overview
A hash function is a mathematical function that outputs a hash value based on the input. The input to a hash function is of arbitrary length, but the output is always of fixed length.

Hash Algorithm Design
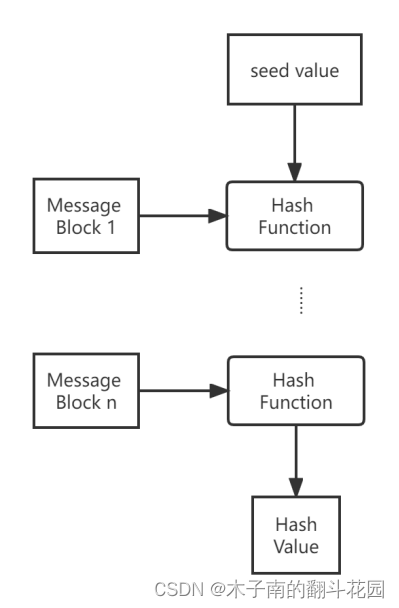
The core of the hash algorithm is a mathematical function, which constitutes a part of the hash algorithm, operates according to the input data block, and obtains the result as the hash value. Hashing algorithms involve multiple rounds of the hash function, each round accepting an input of a fixed size. This process is repeated for as many rounds as possible to hash the entire message.
The hash value of the first message block becomes the input of the second hash algorithm whose output changes the result of the third operation, and so on. This effect is called the avalanche effect of hashing. The avalanche effect can cause the hash values of two pieces of data to be very different. A change of even one data bit can make a big difference.
Application Scenarios of Hash Functions
1. Digital signature:
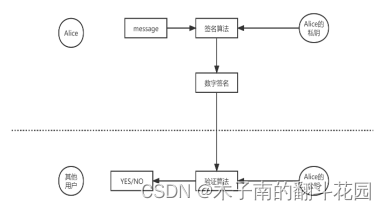
Digital signatures are used to verify the authenticity of digital messages or documents, and to ensure that the content of the information has not been tampered with by third parties. If the prerequisites are met, the recipient of the information can confirm the identity of the sender of the information through a digital signature to ensure that the information is sent by the corresponding sender (authenticity), and the content of the communication information is generated by a digital signature As a result of the important factor, once the content changes, the digital signature will change a lot, and it can verify whether the content of the information has changed (integrity).
The digital signature is encrypted with the user's private key and decrypted with the public key. The user uses his own key to generate a digital signature through a signature algorithm. The verification process of the public key is to verify the identity of the digital signature through the verification algorithm.
2. Data Integrity
According to the one-way and collision-avoiding characteristics of the hash function, the mapping of the input file can be generated without exposing the content of the file. If a good hash algorithm is selected, we can fully trust the accuracy of the hash function to generate the digest. If the hash value of the file is different before and after sending, it can indicate that the file has been tampered with.
——————————————————————————————————————————
update record