1. Terminology
ACL (Access Control List)-Access Control List
step - step size
wildcard - wildcard
inbound - inbound
outbound - outbound
2. Overview of ACL technology
background
With the rapid development of the network, the problems of network security and network service quality QoS (Quality of Service) are becoming more and more prominent.
1) Important server resources in the park are accessed at will, and confidential information in the park is easily leaked, causing security risks.
2) Internet viruses wantonly invade the intranet of the park, and the security of the intranet environment is worrying.
3) The network bandwidth is randomly occupied by various services, and the bandwidth of voice and video services that require the highest service quality cannot be guaranteed, resulting in poor user experience.
Therefore, it is imminent to improve network security and service quality, and we need to control the network. For example, a tool is needed to help filter some traffic.
overview
An ACL is a series of sequential rules composed of permit or deny statements; it classifies packets by matching relevant fields of the packets.
ACL is a basic tool that can match the source IP address, destination IP address, protocol type, source and destination port and other elements in an IP data packet; Accurate identification and control of network access, to control network access behavior, prevent network attacks and improve network bandwidth utilization, so as to effectively guarantee the security of the network environment and the reliability of network service quality.
3. The basic concept and working principle of ACL
The composition of ACL

ACL number: When configuring an ACL on a network device, each ACL needs to be assigned a number called an ACL number, which is used to identify the ACL. Different categories have different ACL number ranges, which will be described in detail later.
Rules: As mentioned earlier, an ACL usually consists of several "permit/deny" statements, and each statement is a rule of the ACL.
Rule number: Each rule has a corresponding number, called the rule number, which is used to identify the ACL rule. It can be customized or assigned automatically by the system. The number range of ACL rules is 0 to 4294967294, and all rules are sorted by rule number from small to large.
Action: permit or deny in each rule is the processing action corresponding to this rule. permit means "permit" and deny means "deny". However, ACL is generally used in combination with other technologies. Different scenarios have different meanings of processing actions.
For example: if ACL is used in combination with traffic filtering technology (that is, ACL is called in traffic filtering), permit means "allowing passage", and deny means "denying passage".
Matching items: ACL defines extremely rich matching items. For the source address shown in the example, ACL also supports many other rule matching items. For example, Layer 2 Ethernet frame header information (such as source MAC, destination MAC, Ethernet frame protocol type), Layer 3 message information (such as destination address, protocol type), and Layer 4 message information (such as TCP/UDP port number) wait.
Classification and identification of ACL
Classification based on ACL rule definition
Classification |
number range |
Rule definition description |
Basic ACL |
2000~2999 |
Only use the source IP address of the packet, fragmentation information, and effective time period information to define the rule. |
Advanced ACL |
3000~3999 |
Rules can be defined by using the source IP address, destination IP address, IP protocol type, ICMP type, TCP source/destination port number, UDP source/destination port number, effective time period, etc. of IPv4 packets. |
Layer 2 ACL |
4000~4999 |
Use the Ethernet frame header information of the packet to define rules, such as based on the source MAC address, destination MAC address, and Layer 2 protocol type. |
User-defined ACL |
5000~5999 |
Define rules using headers, offsets, string masks, and user-defined strings. |
User ACL |
6000~6999 |
The source IP address or source UCL (User Control List) group of the IPv4 message can be used, as well as the destination IP address or destination UCL group, IP protocol type, ICMP type, TCP source port/destination port, UDP source port/destination port number etc. to define the rules. |
Classification based on ACL identification method
Classification |
Rule definition description |
Digital ACL |
Traditional ACL identification method. When creating an ACL, specify a unique number to identify the ACL. |
Named ACL |
ACLs are identified by name instead of number. |
ACL matching mechanism
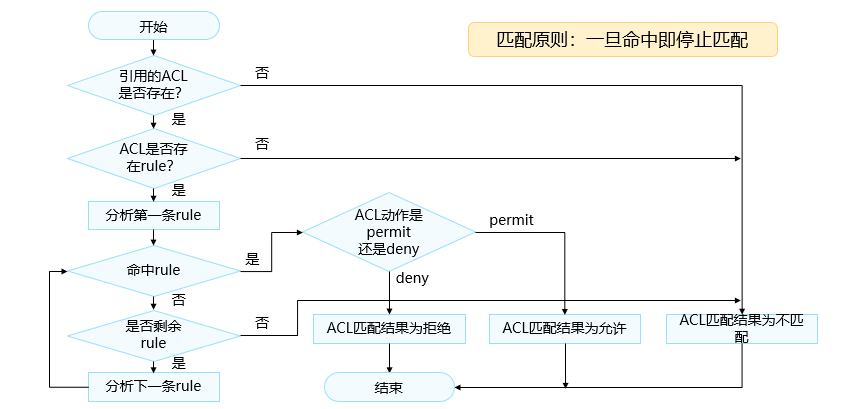
ACL matching order
Huawei devices support two matching orders: automatic ordering (auto mode) and configuration order (config mode). The default ACL matching order is config mode.
自动排序,是指系统使用“深度优先”的原则,将规则按照精确度从高到低进行排序,并按照精确度从高到低的顺序进行报文匹配。
配置顺序,系统按照ACL规则编号从小到大的顺序进行报文匹配,规则编号越小越容易被匹配如果后面又添加了一条规则,则这条规则会被加入到相应的位置,报文仍然会按照从小到大的顺序进行匹配。
注意:ACL技术总是与其他技术结合在一起使用的,因此,所结合的技术不同,“允许 (permit)”及“拒绝 (deny)”的内涵和作用也会不同。例如,当ACL技术与流量过滤技术结合使用时,permit就是“允许通行”的意思,deny就是“拒绝通行”的意思。
ACL的配置位置

入站方向:
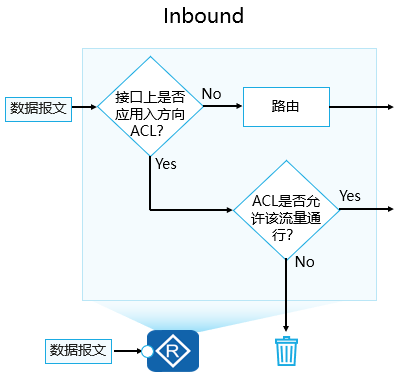
出站方向

四、ACL的基础配置及应用
基本ACL的基础配置命令
1. 创建基本ACL
[Huawei] acl [ number ] acl-number [ match-order config ]
使用编号(2000~2999)创建一个数字型的基本ACL, 并进入基本ACL视图。
[Huawei] acl name acl-name { basic| acl-number} [ match-orderconfig ]
使用名称创建一个命名型的基本ACL,并进入基本ACL视图。
2.配置基本ACL的规则
[Huawei-acl-basic-2000] rule [ rule-id] { deny | permit } [ source { source-address source-wildcard | any } |
time-range time-name ]
在基本ACL视图下,通过此命令来配置基本ACL的规则。
高级ACL的基础配置命令
1.创建高级ACL
[Huawei] acl [ number ] acl-number [ match-order config ]
使用编号(3000~3999)创建一个数字型的高级ACL,并进入高级ACL视图。
[Huawei] acl name acl-name { advance | acl-number } [ match-orderconfig]
使用名称创建一个命名型的高级ACL,进入高级ACL视图。
2.配置基本ACL的规则
根据IP承载的协议类型不同,在设备上配置不同的高级ACL规则。对于不同的协议类型,有不同的参数组合。
当参数protocol为IP时,高级ACL的命令格式为
rule [ rule-id] { deny | permit } ip [ destination {destination-address destination-wildcard| any } | source { source-
addresssource-wildcard | any } | time-rangetime-name | [ dscp dscp |[ tos tos| precedenceprecedence] ]]
在高级ACL视图下,通过此命令来配置高级ACL的规则。
当参数protocol为TCP时,高级ACL的命令格式为
rule [ rule-id] { deny | permit }{ protocol-number| tcp} [ destination { destination-addressdestination-wildcard| any }
| destination-port { eg ,port | gt port | ltport | range port-start port-end }| source { source-address source-wildcard|
any} | source-port {eqport | gt port |It port | range port-startport-end } I tcp-flag { ack | fin | syn}* | time-range
time-name]★
在高级ACL视图下,通过此命令来配置高级ACL的规则。
配置实例
案例1:使用基本ACL过滤数据流量
需求:
在Router上部署基本ACL后,ACL将试图穿越Router的源地址为192.168.1.0/24网段的数据包过滤掉,并放行其他流量,从而禁止192.168.1.0/24网段的用户访问Router右侧的服务器网络
拓扑图:
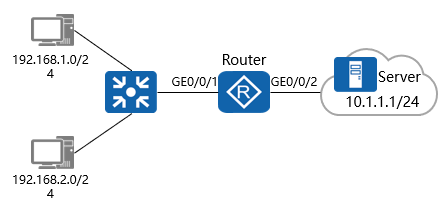
配置步骤:
如图完成路由器的IP地址和路由相关配置。
创建基本ACL 2000并配置ACL规则,拒绝192.168.1.0/24网段的报文通过,允许其他网段的报文通过。
[Router] acl 2000
[Router-acl-basic-2000] rule deny source 192.168.1.0 0.0.0.255
[Router-acl-basic-2000] rule permit source any
3. 配置流量过滤
[Router] interface GigabitEthernet 0/0/1
[Router-GigabitEthernet0/0/1] traffic-filter inbound acl 2000
案例2:使用高级ACL限制不同网段的用户互访
需求:
某公司通过Router实现各部门之间的互连。为方便管理网络,管理员为公司的研发部和市场部规划了两个网段的IP地址。
现要求Router能够限制两个网段之间互访,防止公司机密泄露
拓扑图:
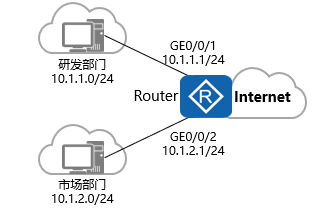
配置步骤:
如图完成路由器的IP地址和路由的相关配置。
创建高级ACL 3001并配置ACL规则,拒绝研发部访问市场部的报文通过。
[Router] acl 3001
[Router-acl-adv-3001] rule deny ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
创建高级ACL 3002并配置ACL规则,拒绝市场部访问研发部的报文通过。
[Router] acl 3002
[Router-acl-adv-3002] rule deny ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255