Table of contents
Detailed explanation of UserDetailsService
Detailed Explanation of PasswordEncoder Password Parser
Introduction to built-in parsers
Introduction to BCryptPasswordEncoder
-
Detailed explanation of UserDetailsService
- When nothing is configured, the account and password are generated by the Spring Security definition
- In the actual project, the account number and password are all queried from the database.
- So we need to control the authentication logic through custom logic
- If you need custom logic, you only need to implement the UserDetailsService interface
- The interface is defined as follows:
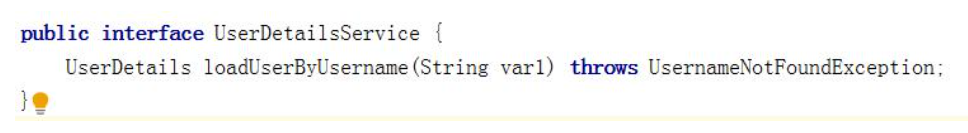
-
return value
- The return value UserDetails is an interface defined as follows:
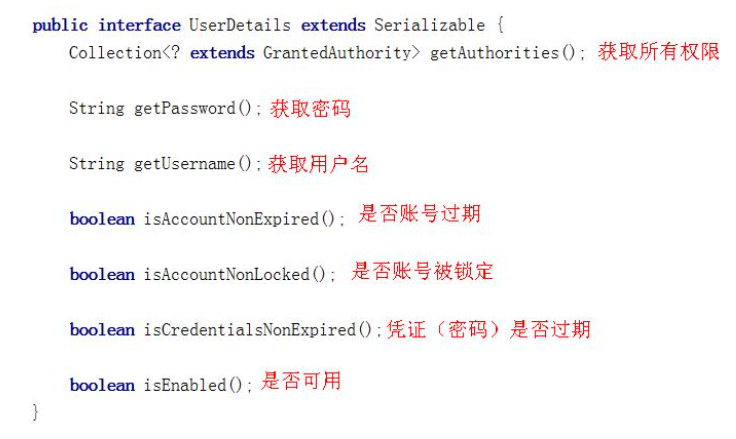
- If you want to return an instance of UserDetails, you can only return the implementation class of the interface
- The following examples are provided in Spring Security
- We only need to use the User class inside
- Note that the fully qualified path of User is:
- org.springframework.security.core.userdetails.User
- This is often confused with the User class developed by myself in the system
- Many methods and properties are provided in the User class

- There are two construction methods, and calling any one of them can instantiate an instance of the UserDetails implementation class User
- The construction method with three parameters actually calls the construction method with seven parameters.

- username: username
- password: password
- authorities: the permissions the user has; null is not allowed here
- The username here should be the username passed by the client
- And the password should be the password queried from the database
- Spring Security will compare the password in User with the password passed by the client
- If they are the same, the authentication is passed; if they are not the same, the authentication fails
- The permissions in the authorities are necessary for learning authorization. All the contents included are the permissions that this user has. If there is a certain permission that is not included in it, and a certain permission must be included when doing something, 403 will appear.
- Authorities collection objects are usually created through AuthorityUtils.commaSeparatedStringToAuthorityList("")
- The parameter is a string, and multiple permissions are separated by commas
-
method parameters
- The method parameter represents the username
- This value is the data passed by the client form
- By default, it must be called username, otherwise it cannot be received
-
abnormal
- UsernameNotFoundException Username not found exception
- In loadUserByUsername, you need to get values from the database through your own logic
- If the corresponding data is not queried through the user name, UsernameNotFoundException should be thrown, and the system knows that the user name has not been queried
-
Detailed Explanation of PasswordEncoder Password Parser
- Spring Security requires a PasswordEncoder instance in the container
- Therefore, when customizing the login logic, it is required to inject the bean object of PasswordEncoder into the container
-
Interface introduction
- encode(): parse the parameters according to specific parsing rules
- matches(): Verify that the encoded password obtained from storage matches the original password submitted after encoding
- Returns true if the passwords match
- Returns false if there is no match
- The first parameter indicates the password to be parsed; the second parameter indicates the stored password
- upgradeEncoding(): Returns true if the parsed password can be parsed again and achieves a more secure result, otherwise returns false; default returns false

-
Introduction to built-in parsers
- There are many resolvers built into Spring Security
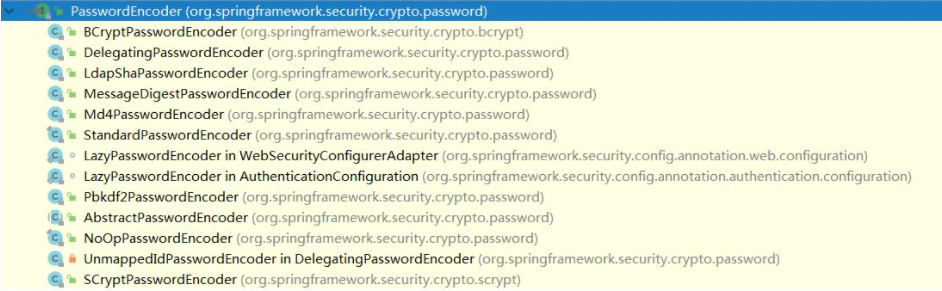
-
Introduction to BCryptPasswordEncoder
- BCryptPasswordEncoder is the official password parser recommended by Spring Security
- BCryptPasswordEncoder is a concrete implementation of the bcrypt strong hash method
- It is a one-way encryption based on Hash algorithm
- The encryption strength can be controlled by strength, the default is 10
-
code demo
- Create a new com.msb.MyTest under the project src/test/java to test the usage of BCryptPasswordEncoder

-
custom login logic
- The UserDetailsService and PasswordEncoder explained earlier need to be used when customizing the login logic
- However, Spring Security requires that there must be a PasswordEncoder instance in the container when performing custom login logic
- So you can't directly new object
-
Write configuration class
- Create a new class com.msb.config.SecurityConfig and write the following content

-
custom logic
- Implementing UserDetailService in Spring Security means serving user details
- Write user authentication logic in this class
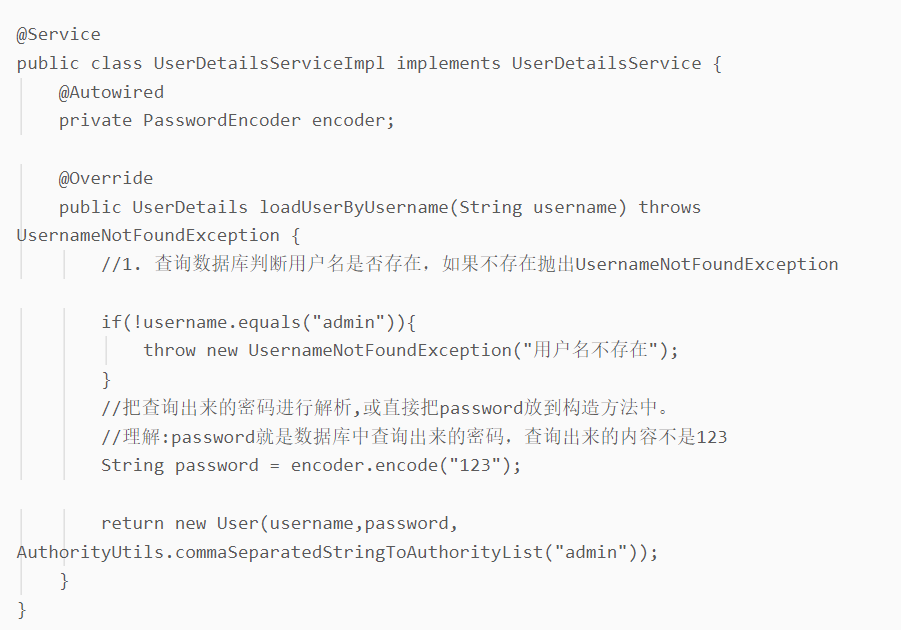
- After restarting the project, enter the account number: admin, password: 123 in the browser, and then you can enter the login.html page correctly