STS mode authorization of OSS
The authority management system provided by a cloud mainly includes two parts, RAM (Resource Access Management) and STS (Security Authentication Service), to meet the needs of securely authorizing others to access without exposing the main account AK\SK . STS provides A temporary access grant. Temporary AK\SK and STSToken can be returned through STS, and these information can be directly sent to temporary users to access OSS.
Discovery of OSS functions
Open the website (https://xxx.cn/) plug-in prompts that there is a key credential
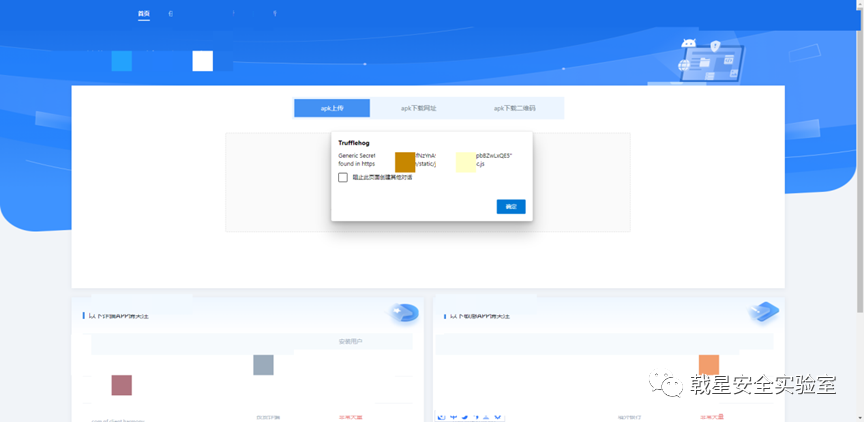
Visit the corresponding js view, use the cloud REACT frontend upload function
https://xxx.cn/static/js/main.68c9e34c.js

Format analysis, unable to obtain detailed information about buckets


Breakpoint js file to get ak, sk
The accesskeyid keyword was discovered by the asynchronous js traffic scanning tool

The corresponding file view is obviously a bucket function

Browser f12 to find the source code location, found that it is Alibaba Cloud oss, breakpoint code, use the web page upload function to trigger

Get ak, sk core ststoken information
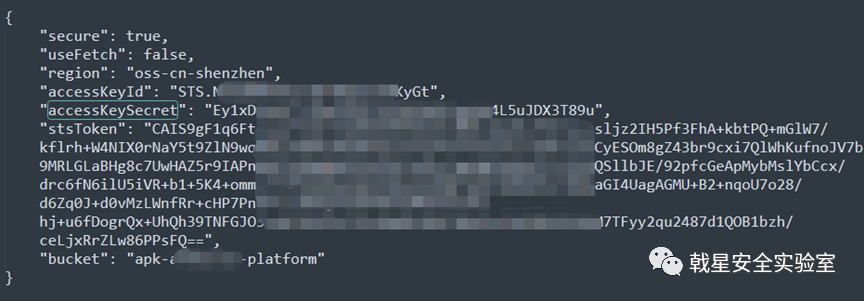

STS mode access

Although accessKeyId, accessKeySecret and stsToken will change in STS mode, we can still take over the corresponding storage bucket within the validity period (about 3~5 minutes)

Root path browsing, you can see cloud storage mainly for Guangzhou, Hangzhou and Shenzhen

Access to multiple subfolders is successful, the website deployment system is still quite large
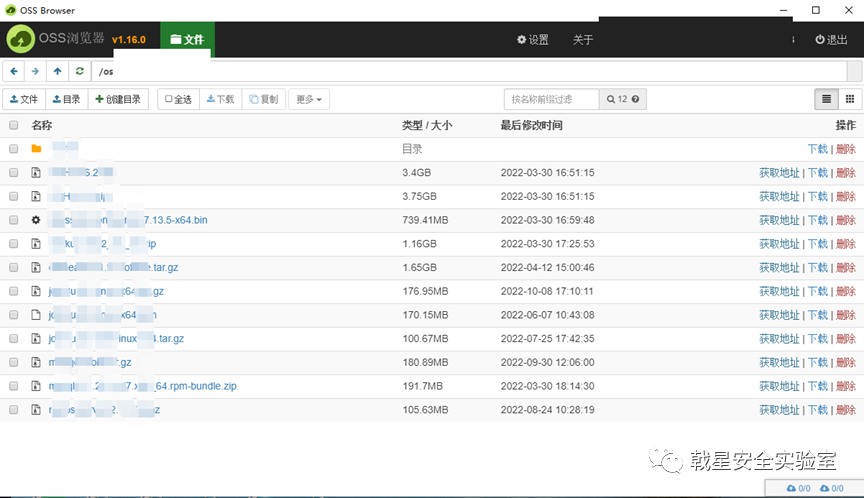
Test download, success

Finally, I tried to scan the cloud host, and there was nothing.
Because it is an STS mode access, stop here.
repair suggestion
Precisely authorize roles in STS mode such as "oss-admin", and only allow access to the upload path