What are packing and unpacking?
Android reverse packing and unpacking are concepts related to Android application security.
- Reverse Engineering with Packing: Reverse engineering refers to increasing the security of the application by adding one or more protection layers or encryption algorithms in a given Android application. Packing tools usually use specific algorithms and techniques to package and protect applications to prevent reverse engineering and malicious attackers from stealing sensitive information and tampering with applications.
The purpose of reverse packing is to increase the anti-reverse engineering performance of the application, making it difficult for reverse analysts to understand and crack the core logic, algorithms and mechanisms of the application. Reverse packing plays an important role in protecting intellectual property, preventing piracy, and reducing malicious code injection.
- Unpacking: Unpacking refers to restoring the packed Android application to its original unpacked state. Unpacking techniques can be used by reverse engineers or malicious attackers to analyze, crack, or modify the code and logic of an application.
Android packer
Android packing is a commonly used application protection technology, which can increase the security of applications and improve the resistance to reverse engineering and malicious attacks. The following are the general practical steps of Android packing:
- Choose the right packer tool: There are many Android packer tools to choose from on the market, such as Bangcle, DexProtector, Qihoo 360, etc. Choose the appropriate packing tool based on your needs and security requirements.
- Prepare the app to be packed: Get the original APK file to be packed and back it up to prevent accidental data loss.
- Pack the application: Use the selected packing tool to pack the application. Packing tools usually provide command line or graphical interface for operation. The specific packing process will involve operations such as encryption algorithms, addition and repair of protection layers, and code relocation.
- Configure packing parameters and settings: Configure relevant parameters and settings of the packing tool as required. These parameters typically include encryption keys, code obfuscation options, resource protection settings, etc.
- Generate a packed application: Use a packer tool to generate a packed application. The resulting application will have hardened features and layers of protection.
- Testing and verification: Test and verify the packed application to ensure its normal operation on different devices and operating system versions, and evaluate its security and performance.
- Publish and distribute packed applications: publish and distribute applications according to requirements. Ensure that the user experience and performance of the packed application is consistent with the original application.
Android shelling
Android unpacking refers to the process of restoring a packed application to its original unpacked state. Unpacking is often used in areas such as reverse engineering, security research, and vulnerability discovery. The following are the general practical steps for Android unpacking:
- Analyze the target application: select the target application that needs to be unpacked, and understand its packing type and packing tool. Common packing tools include Bangcle, DexProtector, Qihoo 360, etc. Conduct research and analysis on the target application to understand its packing mechanism, encryption algorithm and protection layer.
- Get packed application: Get the packed version APK file of the target application. This can be obtained by downloading from an app store or pulling it from a device.
- Select an appropriate unpacking tool: Select an appropriate unpacking tool according to the target application’s packing type and packing tool. Commonly used unpacking tools include Frida, JustTrustMe, APKTool, etc. Some complex packing applications may need to combine multiple tools and techniques for analysis and unpacking.
- Run the unpacking tool: perform the corresponding unpacking operation according to the usage and guidance of the unpacking tool. This may involve injecting code, simulating the operating environment, decrypting files, restoring DEX files, and more.
- Analyze and restore the application: After successful unpacking, analyze the code, resources and logic of the obtained application. Static analysis tools, decompilation tools and debuggers can be used for further reverse analysis and restoration work.
- Verification and testing: Verify and test the unpacked application to ensure its normal operation on different devices and operating system versions, and evaluate its functionality and security.
The above are some simple understandings of Android reverse engineering. Those who have a deeper understanding of reverse engineering can refer to the learning route of packing and unpacking; as follows: For information, refer to "Android Reverse Analysis"
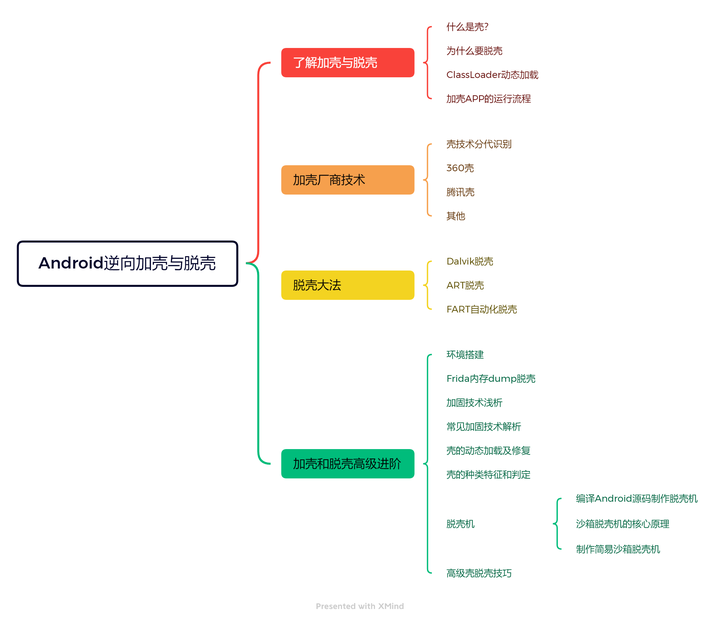
End of article
Android reverse engineering is miscellaneous, so it is almost impossible to get started with zero foundation. Those who are most suitable for learning android reverse engineering are those who have been engaged in android sdk ndk development for a period of time. The characteristics of these people are that they know the operating mechanism of the android system very well and have used CC++ and java for a long time; their advantage in development does not lie in their technical ability. But in the accumulation of experience, what they lack is only reverse methodology and reverse targeted technology.