The half of 2023 is about to pass, let’s ask the soul three times:
- How much has the goal set at the beginning of the year been achieved?
- Has the salary increased?
- Did you find your girlfriend?

Okay, let’s stop pricking everyone’s hearts, and then enter the text.
1. What is the principle of SQL injection?
SQL injection attack is an attack method that inserts maliciously constructed SQL statements into the input parameters of the application, and then parses and executes them on the background SQL server.
2. What is the cause of SQL injection?
In the process of program development, no attention was paid to the standard writing of SQL statements, and input parameters were not filtered.
3. MySQL injection, what conditions are required to write a one-sentence Trojan horse?
Using into outfile to write the Trojan horse into the web directory and get the webshell requires the following conditions:
1. The obtained mysql user has file_priv permission (show global variables like '%secure%' to view)
2. Have write permission to the web directory
3. Know the physical path of the system (requires into outfile ('path'))
4. What is the process of SQL injection?
1. Determine the injection point (by scanner, single quotes, special symbols, etc.)
2. Determine the injection method (character type, number type, error injection, etc.)
3. Determine the database type
4. Explode library name –> table name –> column name –> data in turn
5. Obtain useful data for utilization
5. What are the common web middleware?
1.IIS
2.Apache
3.Nginx
4.Tomcat
5.Jboss
6. What is the difference between MySQL injection above 5.0 and below 5.0?
After Mysql5.0, an information_schema database is added by default. The tables in this database are all read-only, and operations such as deletion, update, and insertion cannot be performed. But it records all important information such as library names, table names, and column names in the database.
information_schema.schemata: stores the library names of all databases in the database
information_schema.tables: stores the table names of all tables in the database
information_schema.colums: stores the column names of all columns in the database
7. What are the types of SQL injection?
1. According to the data type of the injection point:
- digital
- character type
2. According to the data transmission method:
- get type
- post type
- header header injection (UA, COOKIE, etc.)
3. According to the injection method:
- union injection
- Boolean Blind
- time blind
- Error injection
- secondary injection
- wide byte injection
8. What is wide byte injection?
The main use is that when mysql uses GBK encoding, it will artificially consider that two characters are a Chinese character. When escaping single quotes (0x27), if we add the filter escape symbol / (0x5c), we can use GBK encoding in / Add 0xdf or other hexadecimal characters that can form Chinese characters to form a Chinese character (df5c) to escape the single quotation marks.
9. How to defend against wide subsection injection?
1. The database uses utf-8 encoding
2. Using gbk-encoded patch scheme:
- Use mysql_set_charset (GBK) to specify the character set
- Escape with mysql_real_escape_string
Principle: The difference between mysqlmysql_real_escape_string and addslashes is that it will consider the currently set character set, and there will be no problem of splicing df and 5c into a wide byte. The current character set needs to be specified using mysql_set_charset. These two additions are indispensable.
10. What is secondary injection?
Filtering is done when storing in the database, but no filtering is done when fetching data, resulting in an injection method.
11. How to write SQL injection into the shell?
1. Use mysql's into outfile to write to webshell
2. Use the –os-shell method of sqlmap to write to the webshell
12. How to defend against SQL injection?
1. SQL precompilation
2. Strictly limit the parameter type, only numbers
3. Join the black and white list
4. Escape special characters
5. Use WAF
13. How does SQL injection bypass WAF?
1. Case and double writing bypass
2. Replace keywords
3. Use encoding
4. Using annotations
5. Use equivalent functions and commands
6. Use special symbols
7. Filling with junk data
14. What is the principle of XSS?
The attacker embeds a malicious script (usually js code) in the web interface, causing the user to control the operation of the user's browser when browsing the web page
15. What are the classifications of XSS? introduce each
1. Reflective type
generally constructs malicious js in url and sends the link to the target user. When the user visits the link, a GET request will be sent to the server to submit a link with malicious code
2. DOM type
Script programs can dynamically modify page content through DOM.
3. Persistent type
It is common to store malicious code and text in the database of the server on blog message boards, feedback complaints, forum comments, etc., and each user visit will trigger the malicious code.
16. How to write XSS injection statement?
Pop-up <script>alert('xss')</script>
17. What is XSS blind typing and how to use it?
Xss blind typing is an attack scenario, and it is also a storage type. Xss
blind typing means that the feedback effect cannot be directly seen on the front end, only the background can see the input content, and it is impossible to judge whether there is xss from the front end.
In this case, we can store some url links that load malicious scripts, and when the administrator views them, they will obtain information such as keyloggers or cookies
18. How to defend against XSS?
1.HTML Entity Coding
2. Black and white list
3. Set http-only (limit cookie hijacking)
4. CSP Content Security Policy
5.WAF
19. What is the principle of CSRF vulnerability?
Attackers use cross-site requests (using short URLs to induce clicks) to conduct illegal operations as legitimate users. Simply put, they steal your identity information and send malicious requests to third-party websites, including using your identity to send emails, send SMS, transaction transfer, etc.
20. How to defend against CSRF (say three methods)?
1. Verify the HTTP Referer field
2. Add token to the request address and verify
3. Add custom attributes to the HTTP header and verify
21. What is the difference between CSRF and XSS?
First of all, CSRF needs to log in to the website to obtain your cookie before proceeding to the next attack. In principle , XSS does not require
that the browser can directly execute js code, and then the attacker embeds the constructed malicious JS code to let the browser automatically send a request to the server, usually a get request. In principle, csrf uses the principle that all parameters on the server side of the website can be pre-configured, and then the attacker splices the specific request url, which can lure the user (the url is usually shortened so that the user cannot easily see the submitted parameters) and submit the structure well request.
22. What is the harm of SSRF vulnerability?
1. Scan the intranet open services
2. Send payload to any port of any host on the intranet to attack intranet services
3. DOS attack (request for large files, always keep the link keep-alive always)
4. Attack intranet web applications, such as direct SQL injection, xss attacks, etc.
5. Use file, gopher, dict protocols to read local files, execute commands, etc.
23. Which protocols can be used to exploit SSRF vulnerabilities?
- php
http、https、file、gopher、phar、dict、ftp、ssh、telnet
- java
http、https、file、ftp、jar、netdoc、mailto
24. What dangerous functions are involved in SSRF?
The dangerous functions involved in SSRF are mainly network access, which supports pseudo-protocol network reading.
PHP: file_get_contents(), fsockopen(), curl_exec(), etc.
25. How can SSRF vulnerabilities be bypassed when there are defenses?
1. The IP address is converted to other bases or dots are replaced with periods to bypass
2. Short URL bypass
3. Use other protocols to bypass
26. How to judge whether there is an SSRF vulnerability?
In any place where a network request can be initiated externally, use the cause of SSRF for verification.
27. How to defend against SSRF vulnerabilities?
1. Whitelist
2. Filter, intranet ip, add untrusted domain name
3. Disable other protocols
28. In which functions may SSRF vulnerabilities exist?
1. Article sharing
2. Image download or load
3. Request resources from remote services
29. What is the principle of XML injection?
External Entity Injection Attack, which occurs when the program parses the external entity forged by the attacker when parsing the input XML data
30. How to fix the XML injection vulnerability?
1. Use the method provided by the development language to disable external entities
2. Filter the XML data submitted by the user
31. What is the principle of the file upload vulnerability?
Because programmers do not strictly limit the file suffix and file type or processing defects uploaded by users in the implementation code of user file upload function, users can upload executable dynamic script files to the server beyond their own permissions.
32. What are the hazards of file upload vulnerabilities?
1. The website is controlled
2. Add, delete, modify and check files, and execute commands
3. If the server has not been updated for a long time, you can use exp to raise the right
33. What are the common bypass methods for file upload vulnerabilities?
1. Disable js bypass
2. Modify the file type to bypass
3. Upper and lower case, double writing bypass
4. File header bypass
5. Secondary rendering bypass
6. Conditional race bypass
7.00 Truncated Bypass
8. Cooperate with parsing vulnerabilities to bypass
34. Describe the principle of Nginx parsing vulnerabilities
In the lower version of Nginx, there is a key option cgi.fix_pathinfo in the php configuration file that is enabled by default, which causes php to parse forward by default when there are files that do not exist in the url
35. Describe the principle of Apache parsing vulnerabilities
Apache allows files to have multiple suffixes, and will separate the file suffixes according to . If there is an unrecognized suffix, it will continue to parse until it is recognized.
36. Describe the principle of IIS parsing vulnerabilities
1. When creating an .asp file directory, any file in this directory will be parsed by the server into an asp file
2. The server does not parse the content after ";" by default, causing xx.asp;.jpg to be parsed into xx.asp script file
37. How to defend against file upload vulnerabilities?
1. Set the permissions of the directory where the file is uploaded to be non-executable
2. Determine the file type
3. Use random numbers to rewrite the file name and file path.
4. Use security devices such as WAF
38. What is the principle of a file containing a loophole?
Program developers generally write reusable functions into a single file, and call this file directly when they need to use a certain function without writing it again. This process of calling a file is called file inclusion. Flexible, so the included file is set as a variable for dynamic call, so that the client can call a malicious file, resulting in a file containment vulnerability, that is, when a file is imported through a PHP function, because the incoming file name does not have After reasonable verification, unexpected files are manipulated, resulting in file leakage and even malicious code injection.
39. What functions can be used in the file?
- include()
- require()
- include_once()
- require_once()
40. How to use the file contains?
1. Use the file to include upload webshell
2. View sensitive information of the system
41. What are the common command execution functions?
1.system()
2.exec()
3.popen()
4.shell_exec()
5.passthru()
42. What methods can be used to bypass command execution when there is a blacklist?
1. Variable splicing
2. Single quotes and double quotes bypass
3. Encoding bypass
4. Backslash bypass
43. How to defend against command execution?
1. Do not execute external commands
2. Use custom functions or function libraries to replace the functions of external commands
3. Use the escapeshe||arg function to process command parameters.
4. Use safe_mode_exec_dir to specify the path of the executable file.
44. What is an ultra vires loophole?
Privilege violation vulnerability is a very common logical security vulnerability. It is because the server side has too much trust in the data operation request made by the client, ignoring the judgment of the user's operation authority, resulting in modifying the relevant parameters to have the functions of adding, deleting, checking, and modifying other accounts, resulting in an unauthorized loophole
45. How to repair the ultra vires vulnerability?
1. The front and back ends simultaneously verify the user input information, double verification mechanism
2. User identity must be verified before performing key operations to verify whether the user has the authority to operate data
3. Particularly sensitive operations allow users to re-enter passwords or other verification information
4. Obtain the current user id from the user's encrypted authentication cookie to prevent attackers from modifying it, or add unpredictable and unguessable user information to sessions and cookies
5. Encrypted resource IDs directly referenced by objects, preventing attackers from enumerating IDs, and special processing of sensitive data
46. What loopholes usually exist when sending verification codes, and how to defend against them?
When sending verification codes, there are usually logic loopholes (such as SMS bombing, random user registration).
SMS bombing defense methods:
1. Set the time interval
2. Add other authentications. Any
user registration:
1. Limit the verification code verification
2. Shorten the valid time of the verification code
3. Limit the number of verification errors for each verification code
47. What loopholes will be involved in payment?
Logical loopholes, such as:
Modify the payment price of the product
, modify the payment quantity of the product
, modify the coupon (subsidiary value) of the product,
and modify the payment status
48. What are the loopholes in the login function, and how to defend against them?
The login function generally has functions such as user registration, forgetting password, changing password, and verification code.
User registration may generate arbitrary user registration. The login box may also generate SQL injection. Defense methods can include restrictions on verification code verification, authentication before key operations, and SQL pre-compilation.
49. Describe the principle of deserialization vulnerabilities
Serialization is to convert an object into a byte stream, which includes the data and information of the object. Serialization and deserialization are convenient for persistent storage of classes, and are also conducive to network transmission. Deserialization is to restore the data and information of the serialized byte stream into a class. If the byte stream does not have any filtering, the attacker can use malicious construction to make the deserialization generate unexpected classes. Or object, this class or object may bring arbitrary code execution during the generation process.
50. Name five Google Hack grammars
- inurl: Search whether the specified character exists in the url
- link: Search for the specified website and return all urls linked to the specified website
- site: returns all urls related to the specified website
- filetype: Search for files of the specified type
- intitle: Use a character in the title of the web page as the search condition
51. What is the same-origin policy?
The same origin means that "protocol + domain name + port" are the same. If two different domain names point to the same ip address, they are not of the same origin; SOP (Same Origin Policy) is a convention, which is the core of the browser and The most basic security function, if the same-origin policy is missing, the browser is vulnerable to attacks such as XSS and CSRF
52. Introduce session and cookie respectively, and the relationship between the two
Both session and coolie are used to track the identity of the browser user, but the session is stored on the server side, and the cookie is stored on the client side. Cookies are not very safe. You can analyze the cookies stored locally to cheat cookies. The seesion will be saved on the server for a certain period of time. When the number of visits increases, it will take up performance. The limit of a single cookie on the client side is 3K.
53. How to bypass CND to obtain the real IP of the website?
- Query historical DNS records
- Query subdomain
- dark engine search
- foreign ping
54. What tools can be used to collect subdomains?
- oneforall
- ksubdomian
- subdomainbrute
- sublist3r
- rappidns
- google hacker
55. Briefly describe the four modes of the BurpSuite Intrude module
1. sniper (sniper)
comes one by one, the most basic mode, if there are N payloads, execute N times
2. Battering ram (battering ram)
will blast together if two parameters are added.
3.pitchfork (pitchfork mode)
whether to add two payloads symmetrically, for example p1:1,2; p2:3,4. Then the first time is 1,3 and the second time is 2,4
4. Cluster bomb (cluster bomb)
adds two parameters, which will calculate the Cartesian product of the two payloads
56. What are the ways to obtain webshell?
1. Upload webshell directly
2. File upload to get webshell
3. For example, SQL injection to obtain webshell
4. For example, the log writing function obtains webshell
5. Use file inclusion to get webshell
57. How do you do code auditing? How to ensure the comprehensiveness of code audit?
- Backtracking parameter passing process based on sensitive keywords
- Check the controllable variables and track the variable transfer process forward
- Find sensitive function points
- Audit all code
You should understand all the functions currently provided by the application, and obtain all business restriction rules related to these functions, and determine the attack surface from the aspects of context, sensitive data, user roles and access rights, application types, code design, etc., to ensure the accuracy of code audit. Comprehensiveness.
At the end of the article, I also compiled a set of network security interview questions and resume templates for you. If you need it, you can private message me in the background for " interview " to get it. I hope it will be helpful to everyone!
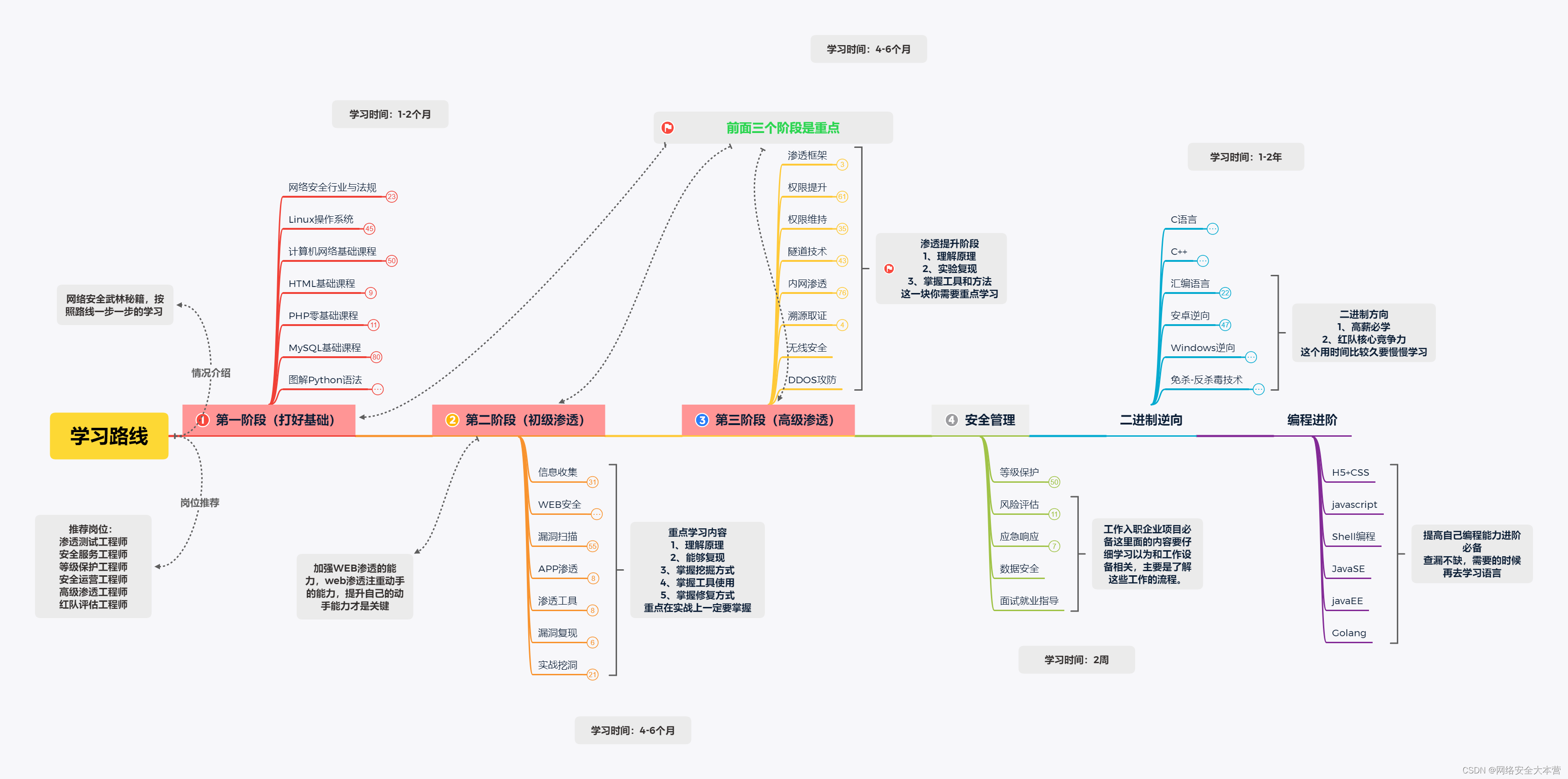
Network Security Zero-Basic Learning Route
For students who have never been exposed to network security, I have prepared a detailed learning and growth roadmap for you. It can be said that it is the most scientific and systematic learning route. It is no problem for everyone to follow this general direction. If you need it, you can tell me in the comment area.