Table of contents
Iptables command configuration
Firewalld two configuration methods
firewall-cmd command line basic configuration
firewall-config graphical configuration
Basic Concepts of Firewall
The firewall is to control the entry and exit of data packets according to the rules set by the system administrator, mainly to protect the security of the intranet
At present, there are two main types of firewalls in the Linux system: iptables and firewalld
Iptables - Static Firewall
In the early Linux system, the iptables firewall was used by default, and the configuration file was in /etc/sysconfig/iptables
Works mainly at the network layer
Using chain rules, only Internet data packets can be filtered, but data packets from intranet to intranet cannot be filtered
Iptables can only be configured via the command line
Iptables allows all by default, and needs to be restricted by denying
Iptables must be refreshed after modifying the rules to take effect, and the connection will be lost (cannot daemon process)
Firewalld - dynamic firewall
Replaced the previous iptables firewall, the configuration files are in /usr/lib/firewalld and /etc/fiewalld
Works mainly at the network layer
Added the concept of region, which can not only filter Internet data packets, but also filter intranet data packets
Firewalld can be configured not only through the command line, but also through the graphical interface
Firewalld defaults to deny all, and needs to be allowed to release
Firewalld can dynamically modify a single rule and dynamically manage a rule set (allows to update rules without breaking existing sessions and connections, and can be a daemon process)
Precautions
Both iptables and firewalldl are just the management programs of the Linux firewall. The real firewall executor is netfilter in the kernel, but the results and usage methods of firwalld and iptables are different
When configuring the firewall, it is not recommended to use the two configuration methods in combination (it is recommended to use only one of them)
Iptables Explained
Iptables configuration firewall relies on four parts: table, rule chain, rule (matching condition), control type composition
Iptables table
The processing priority is from high to low, and the tables are independent from each other
raw table
Whether to track the state of a data packet (including two rule chains of OUTPUT and PREAUTING)
mangle table
Modify the content of the data packet; you can do traffic shaping and mark the data packet (including all rule chains)
nat table
Responsible for the address translation function; modify the source and destination IP addresses or ports in the data packet (including three rule chains of IN, OU, PR, and PO)
filter table
Responsible for filtering data packets; allowing or disallowing data packets (including three rule chains of IN, OU, and FO)
Iptables rule chain
What is a rule chain
Many rules form a rule chain
Data packets are matched from top to bottom, and the matching ends when the matching is successful, and the corresponding control type is executed (it is recommended to put precise policies on it)
rule chain type
INPUT processes inbound data packets (processing data packets whose target is the local machine)
OUTPUT processes outbound data packets (the processing source is local data packets, generally do not make rules on this chain)
PREROUTING processes data packets before routing (generally used as NAT Server)
POSTROUTING processes packets after routing (generally used for source NAT)
FORWARD processes forwarded data packets (processes data packets passing through the machine)
Iptables control type
ACCEPT allows the packet to pass through
DROP discards data packets (do not respond to the other party, use this in general work)
REJCET refuses to pass the data packet (it will respond to the other party, and the other party knows that it is rejected)
SNAT modifies the source address of the packet
DNAT modifies the destination address of the packet
MASQUERADE pretends to be a non-fixed public IP address
LOG records log information in the /var/log/messages file, and then passes the packet to the next rule
The data packet arrives at the firewall for matching according to the following figure
The data processing of iptables is concerned with four tables and five links and the flow in and out
Iptables command configuration
When configuring the iptables firewall, you need to enable the firewall service
systemctl start firewalld to open the firewall
systemctl status firewalld View firewall status
Iptables command to view firewall
iptables -nL -t nat View the rule chain of the nat table
-n Display output in numeric form (eg by IP address)
-L View the policies of the current firewall
-t specifies which table to view in iptables (the default is the filter table)
Iptables command to configure firewall
iptables -P INPUT DROP changes the default traffic for the INPUT rule chain to deny
-P set/modify default policy
iptables -t filter -I INPUT -s 192.168.10.0/24 -j ACCEPT Configure rules in the INPUT rule chain under the filter table
-I num insert rules (uppercase i, add rules at the beginning of the chain by default, you can specify the serial number)
-i Incoming data from this network card
-o The data flowing from this network card
-s source address (plus! means negation)
-d destination address
-j limit action
iptables -A INPUT -p tcp --dport 1000:1024 -j REJECT rejects packets with tcp port numbers 1000~1024
-A Add rules at the end of the chain
-p specifies the protocol type
--sport source port
--dport destination port
iptables -D INPUT 1 deletes the first rule of the INPUT rule chain
-D num delete rule chain
-R modify rules
iptables -F clears existing policies
iptables-save to save firewall policies
Precautions
When the content of the created rule is consistent with the existing rule, the original rule will not be overwritten, and it will be directly added to the existing rule chain (that is, there are two identical rules under this rule chain at this time, but the order is different)
The above configuration of the firewall is in runtime mode, that is, it will take effect immediately after the configuration is successful, but it will become invalid after restarting (the configuration needs to be saved, and it will not become invalid after restarting)
firewalld explained
firewalld is the service name, firewall-cmd and firewall-config are configuration tool names
firewall-cmd based on command line configuration
firewall-config is configured based on a graphical interface (these two configuration methods are synchronized in real time)
Firewalld zone concept
By default, all network cards are public areas, and network cards can be set to different areas as needed
Trust trust zone
Allow all traffic (all network connections are acceptable)
Public public area
Only accept ssh, dhcpv6-client service connections (default zone)
External _
Only accept ssh service connections (IPv4 traffic forwarded through this area will be masqueraded by default)
HomeFamily area
Only accept ssh, msdns, ipp-client, samba-client, dhcpv6-client service network connections
Internal area
same home area
Work area
Only accept ssh, ipp-client, dhcpv6-client service connections
Dmz quarantine area (demilitarized area)
Receive only ssh service connections
Block restricted area
Deny all incoming traffic (with responses)
Drop drop area
drop all incoming traffic (no response)
Packet Arrival Firewall Matching Rules
Firewall only cares about the area for data processing
- Match according to the source IP address of the data packet, and match according to the area rules of the bound area of the source address (if there is no bound area, match the rules of the default area)
- According to the incoming network interface match, the rules of the area bound to this interface are matched (if there is no bound area, the rules of the default area are matched)
Area rules for binding source address > area rules for network card binding > rules for the default area
Firewalld two configuration methods
Temporary configuration (runtime current effective table)
Effective immediately, invalid after reboot
No interruption of existing connections
Unable to modify service configuration
Permanent configuration (permanent permanent effective table)
Does not take effect immediately, takes effect after restarting, or takes effect immediately after synchronization
will terminate the existing connection
Can modify service configuration
firewall-cmd command line basic configuration
How to achieve permanent configuration
--permanent means that this configuration is added to take effect permanently (the default is temporary)
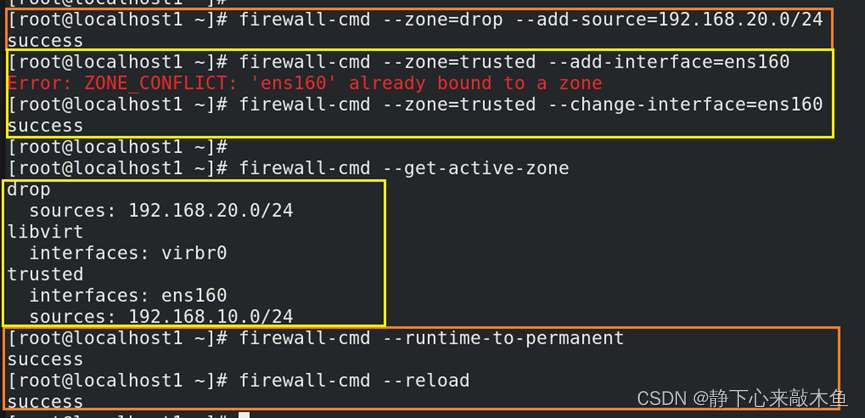
Or execute this command after the configuration firewall-cmd --runtime-to-permanent will temporarily change to permanent
After the permanent configuration is completed, you need to synchronize firewall-cmd --reload to immediately synchronize the permanent configuration
Review the default regions and make changes
firewall-cmd --get-zones query available areas
firewall-cmd --get-default-zone query the name of the default zone
firewall-cmd --get-active-zone displays the area and network card name currently in use
firewall-cmd --set-default-zone=trusted Set the default zone to the trusted zone
Bind the network card/subnet to the zone (allow/deny this subnet through)
firewall-cmd --zone=drop --add-source=192.168.20.0/24 Bind this subnet to the drop zone (reject traffic from this subnet)
firewall-cmd --zone=trusted--add-interface=ens160 Bind this network card to the trusted zone (allow traffic from this network card)
--remove-source remove subnet bound to zone
--change-source change binding of subnet to zone
Configure the protocols/port numbers allowed/denied by the zone
firewall-cmd --list-all displays the port number, network card, service and other information of the current area
--list-all-zones show all zone's
firewall-cmd --get-services lists all currently allowed protocols
firewall-cmd --zone=public --add-service http configuration public zone allows HTTP protocol
--remove-service ssh refuse to pass the ssh protocol
--add-port=123/tcp Allow port 123 through tcp
--remove-port=123/tcp reject port 123 through tcp
The protocol type and port number saved by cat /etc/services
Configuring Protocol Port Translation (Port Mapping)
firewall-cmd --permanent --zone=public --add-forward-port=port=888:proto=tcp:toport=22:toaddr=192.168.10.1
Convert the tcp 22 port number of the 192.168.10.1 host to the 888 port number (the public area receives ssh)
--remove-forward-port remove this port mapping
other configuration
--panic-on emergency mode, cut off all network connections (use in special cases)
--panic-off restore all network connections
Configure rich rules (more complex and detailed firewall policy configuration)
Highest priority (higher than the default rules, the two do not conflict)
Ability to restrict users based on source and destination addresses and port numbers
firewall-cmd --zone=public --list-rich-rule displays the rich rules already configured in the public area
firewall-cmd --permanent --zone=public --add-rich-rule="rule family="ipv4" source address="192.168.100.1/24" service name="ssh" accept" allow from 192.168.100.1 The host accesses port 22
--add-rich-rule add a rich rule
--remove-ruch-rule remove a rich rule
reject Deny access
firewall-config graphical configuration
Install firewall-config
Configure Yum source (software warehouse) Linux
package installation%22blog%22%2C%22rType%22%3A%22article%22%2C%22rId%22%3A%22129150924%22%2C%22source%22%3A%22m0_49864110%22%7D
Install the software dnf install firewall-config
System interface explanation
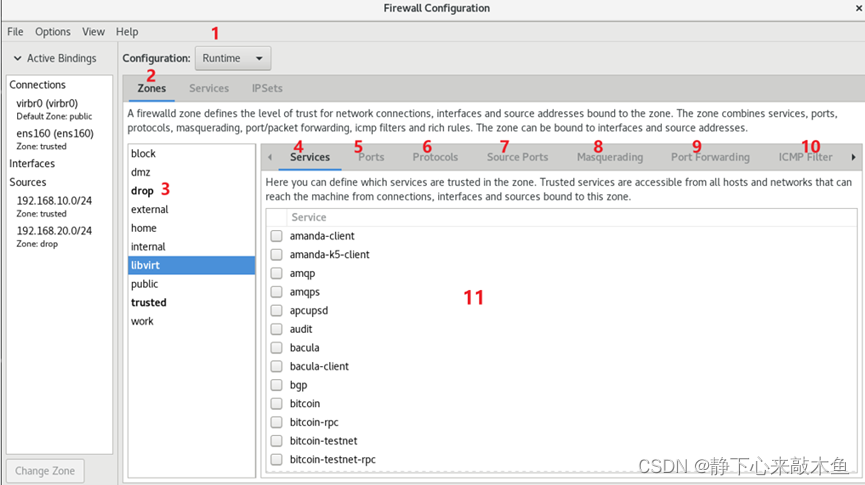
1: Select runtime (Runtime) or permanent (Permanent) mode configuration
2: Select an area
3: The area currently in use (black bold)
4: Manage services in the currently selected area
5: Manage ports in the currently selected area
6: Set the protocols that are allowed to be accessed
7: Set the ports that are allowed to be accessed
8: Turn on or off SNAT (Source Network Address Translation) technology
9: Set port forwarding policy
10: Control the traffic requesting icmp service
11: For the service in the selected area, if the check box in front of the corresponding service is checked, it means that the traffic related to it is allowed
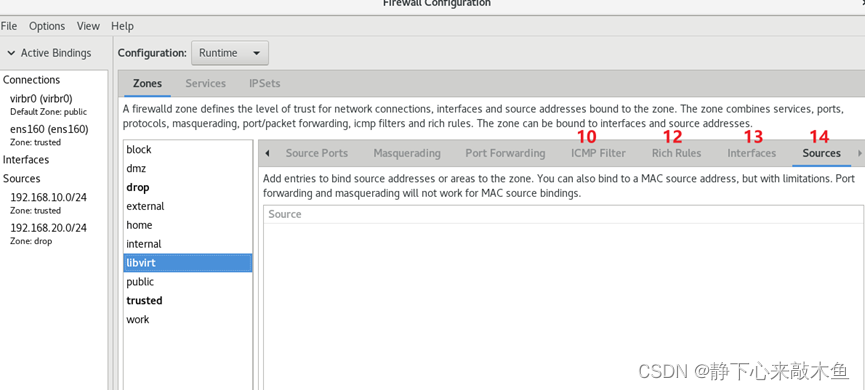
12: Rich rules for managing firewalls
13: Network card information (network card and region binding information)
14: Subnet information (subnet and region binding information)
15: View the list of commonly used service agreements
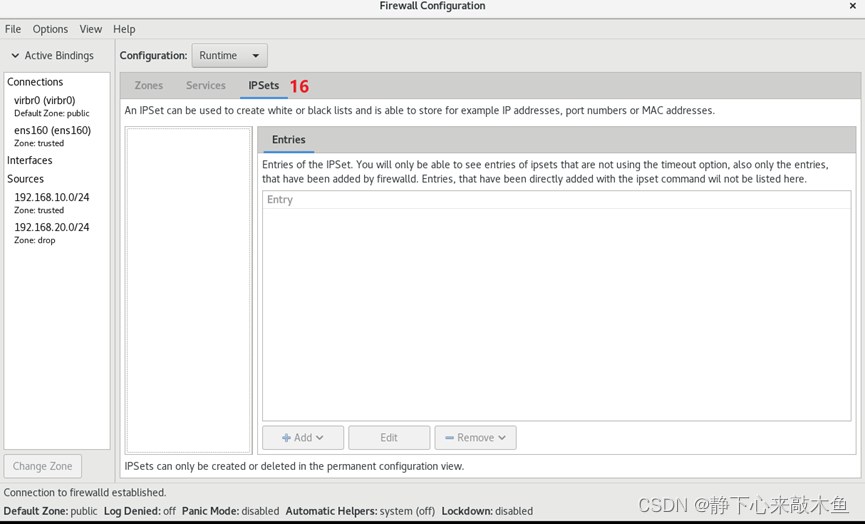
16: Black and white list of host addresses