Mind map of this article:
Article directory
foreword
This article specifically explains the differences between different users and permission issues under Linux.
1. Classification of users under Linux
There are two types of users under Linux: super user (root) and ordinary user.
Super users: can do anything under the linux system without restrictions.
Ordinary users: do limited things under linux.
The command prompt of a super user is "#", and the command prompt of a normal user is "$".
Command: su [username] Function: Switch users. For example, to switch from the root user to the normal user user, use su user.
To switch from a normal user to a root user, use su root (root can be omitted), and the system will prompt you to enter the password of the root user.
are
If you directly enter su, the user is forced to switch to the root user by default (no need to log in), and you need to enter the password of the root user at this time.
are -
If you enter su - directly, you will switch to the root user by default (need to log in again), and you need to enter the password of the root user at this time.
If you want to switch to other ordinary users under the root account, directly enter:
su username
Switching from the root user to any other common user does not require entering the common user password.
If switching between ordinary users, enter:
su username
To switch between ordinary users, you need to enter the password of the corresponding user that needs to log in
After switching users, you can press ctrl + d to return to the original user.
sudo command
sudo + arbitrary command
Function: Temporarily extract permission for this command
1.1 Classification of file visitors (people)
The owner of the file and file directory: u—User (Chinese civilian legal issues)
The user of the group that the owner of the file and file directory belongs to: g—Group (not much to say)
Other users: o—Others (foreigners)
2. File type and access rights (thing properties)
We see that when we list detailed files/directories under a directory, there will be 10 characters in front.
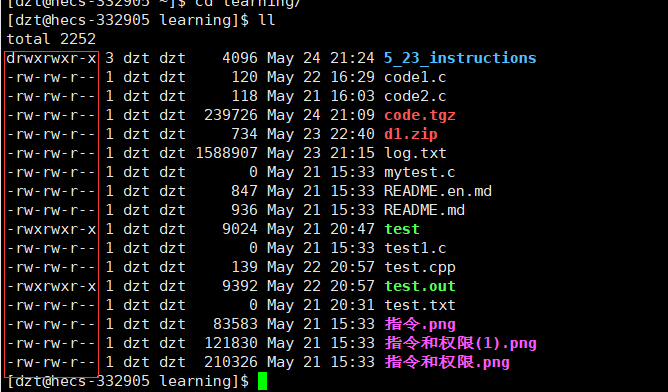
The first character is the file type we will discuss below.
2.1 File types under Linux
File types under Linux include:
–: Ordinary files, including text, executable programs, library files, etc. are ordinary files
d: Directory files
b: Block device files, including disk files
c: Character device files, including keyboard, display files, etc.
p: Pipeline files, used to communicate
Among them, what we need to know is - and d, which are ordinary files and directory files respectively.
Why do you say that the file suffix has no direct meaning?
The system under Linux does not distinguish files by file name suffix, and an executable file can be executed with or without the file suffix. (Note that it is Linux, not other software)
For example:
First create a new .c file, then compile and generate an a.out file
mv a.out a.exe
This also works.
But when the .c compiler (called gcc) compiles, it will recognize the .c suffix, and other suffixes may not be compiled. This is other software running on Linux, not Linux itself.
Summary: Linux distinguishes files/directories by the first letter in front. If it is -, it is an ordinary file, and if it is d, it is a directory file.
2.2 File permission attribute (role/identity)

The first character is finished above, and then the following 9 characters are said:
r: readable
w: writable
x: executable
-: corresponding permission location, no permission
Note: The permissions corresponding to each location are always the same, and there is no possibility of out-of-order problems!
Note: The permissions corresponding to each location are always the same, and there is no possibility of out-of-order problems!
Note: The permissions corresponding to each location are always the same, and there is no possibility of out-of-order problems!
The first three positions correspond to the permissions of the owner, the middle three correspond to the permissions of the group to which it belongs, and the last three correspond to the permissions of other people.
Every three characters for a role are:
owner, group, others
Let me talk about the difference between the owner and other people. For a file or project, someone must have created it. The person who created it is called the owner. The owner can view and change his own project at will, but can other people view/ Changes to this item require the owner's consent.
That is, others cannot freely view the item
As for the group it belongs to , if there is a person/group of people who are colleagues of the owner, then the owner can pull these people into his group to give them the same permissions.
Let's talk about the content of the frame corresponding to the above picture:
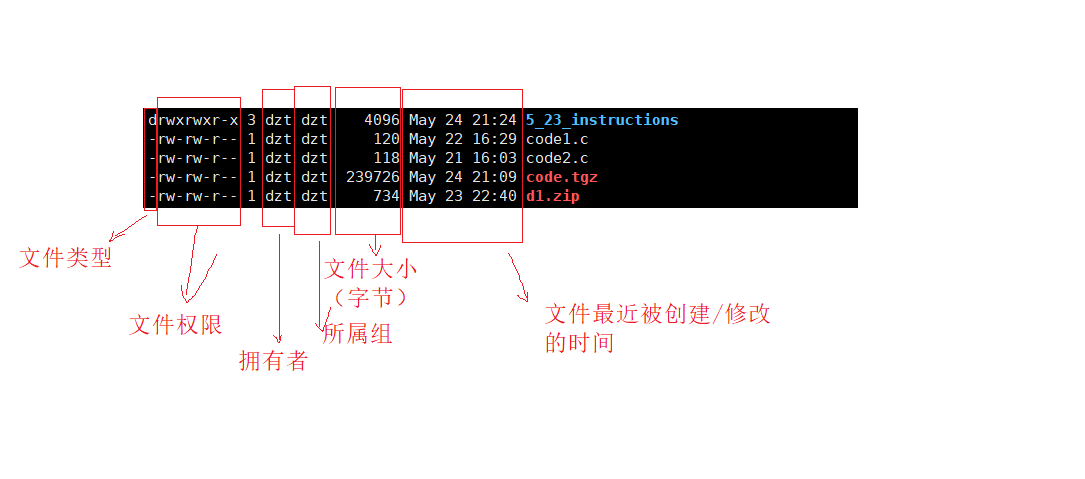
for the numbers in the middle column, we will talk about it later.
There is a detail: the above file/directory only has two identities of the owner and the group to which it belongs, so what about others?
In fact, if a person is neither the owner of the file/directory nor the group he belongs to, then he is other.
Therefore, the identity of other is not displayed under Linux.
Summarize:
Two representation methods of permission value under Linux:

Modification of chmod command and chown command/permission
method 1:
instruction:
chmod : change mode, modify mode/permission
for example:
chmod u-rwx test.c
subtracts his r, w, x permissions to the test.c file from the owner.
chmod u-rwx, g-rwx, x-rwx test.c
deletes the r, w, and x permissions of the test.c file for the owner, the group it belongs to, and others
chmod u+rwx, g+rwx, x+rwx test.c
increase the owner, group, and other people's r, w, x permissions to the test.c file
Method 2:
Since the permissions corresponding to each location are either available or not, it can be expressed in binary form
. For example:
chmod 000 test.c
modify the owner’s permission to the test.c file to—, the group’s permission to—, and the others’ permission to—
chmod 777 test.c
modify the owner's permissions on the test.c file to be readable, writable and executable, the permissions of the group to which it belongs are readable, writable and executable, and the permissions of other people are readable, writable and executable
because 7 corresponds to The binary number is 111, and the positions corresponding to each 1 are: readable, writable, and executablechmod 776 test.c
modify the owner's permissions on the test.c file to be readable, writable and executable, the permissions of the group to which it belongs are readable, writable and executable, and the permissions of other people are readable and writable, but not executable because
6 The corresponding binary is 110, and other has permission for the file to be readable and writable but not executable.
tips: some things that the owner and the group can do
For a file, if the owner and the group belong to the same person, then when the system authenticates this person, it starts from the owner first. If the authentication is successful, even if the group belongs to this person, the system will not look at the group again .
That is to say, when the system performs authentication, a person can only correspond to one identity.
2. For the owner, even if he owns the file, if his permission to the file is read-only but not writable, he cannot write.
Just because you only own the file doesn't mean you can write to it.
for example:
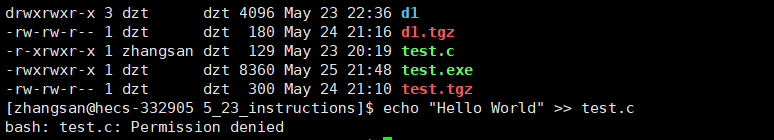
The owner of the test.c file is zhangsan, whose permission to the file is read-only and execute-only, and has no write permission, so the write operation cannot be completed.
3. If the group and owner of a file are different, then if the person in the group has write permission, he can write to the file.
For example:
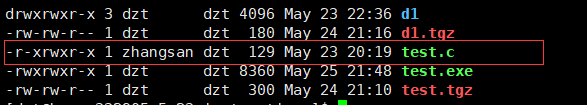
in the test.c file, the owner is zhangsan, and the group it belongs to is dzt. At this time, the identity of the owner is zhangsan, but the group dzt belongs to can have rwx permission on the file.
The relationship between the umask command and the permission value
Under Linux,
The default permission value of the created ordinary file is: 666
The default permission value of the directory file is: 777
However, after some special calculation in Linux, the ordinary file becomes: 665, and the directory file becomes: 775.
The reason for all this is the umask, which is called the permission mask.
Permission mask: Any permissions that appear in the umask will not appear in the final file permissions!
for example:
The default umask is: 0002
, that is:
000 000 010
If you create an ordinary file, the default permission value is 666, that is:
110 110 110
Then after calculation:
the final permission value of the ordinary file is:
110 110 100
So:
final permissions = starting permissions & (~umask)
How to change umask:
umask + corresponding permission mask
such as: umask 0001
or umask 0555
rwx functions for ordinary files and directory files
For normal files:
r: whether the file can be read
w: whether the file can be written
x: whether the file can be executed
For directory files:
r: whether to allow us to view the contents of the directory
w: whether to allow us to create, change, delete in the current directory
x: whether to allow us to enter the corresponding directory
Summary: For ordinary files, the reason why the default permission value is 666 is that there are only a few executable files. If you want the file to become executable, you can add it manually.
For directory files, you must have executable permissions, that is, you must enter the directory, otherwise it is meaningless.
3. What exactly is a sticky bit?
We know that in life we will have the need to share files.
We can set a file to be readable, writable and executable by others, so that other people can enter the shared file and operate it.
But what if someone else deletes the shared file? Because he has write permission, he can delete the file naturally. In order to avoid such a situation,
The first method: The owner removes the write permission of others!
But a new problem arises. If the write permission of other people is removed, the shared file/directory cannot achieve a good sharing effect, because other people also need to write information to the file.
So the first method is not advisable.
sticky bit
We know that whether a file can be deleted is not determined by the file itself, but by the directory where the file is located.
So the sticky bit must be set under the directory.
The sticky bit is a special executable permission. Its function is to allow others to read, write and execute the shared directory/file normally, but it cannot be deleted. Only the owner/root of the file is allowed to delete the sticky bit operation
method :chmod o+t directory name
or chmod +t directory name
Do not write other people's permissions, and the sticky bit also takes effect on the executable permissions of other people in the corresponding directory by default.
In general, the sticky bit is generated to prevent other users from deleting shared files/directories, but it also ensures that other people can normally operate on shared directories/files.
Summarize
This article mainly describes the management of permissions under Linux, the differences between different users, permission masks, sticky bits and other issues.