This article directory
This article will start with the introduction of NAT and explain the NAT technology itself in detail. Through this article, you can clearly understand the definitions of NAT, SNAT, DNAT, PAT, NAPT, Full NAT, the differences and connections between them . Finally, how to configure a Linux host with multiple network cards into a NAT router will be given in detail.
If you already know the definition of NAT, you can jump directly to here to see how to configure a Linux host into a soft router through NAT table
1. Introduction to NAT
NAT is the abbreviation of Network Address Translation, which refers to the technology of network address translation, that is, the technology of converting one IP address into another IP address. When some hosts on the internal network have been allocated local IP addresses (that is, private IP addresses), but need to communicate with hosts on the Internet (according to the IP protocol and routing protocol, the router will only forward the reports sent by the hosts with public IP addresses). text), can be done through NAT technology.
The scarcity of public network IP addresses makes it impossible to assign a public network IP address to each host that needs to access the Internet, so NAT technology is introduced to allow multiple hosts to share a public network IP address to access the external network, providing A device with such a function is called a NAT router, and the NAT router can convert the destination IP and source IP address of the IP packet of each host in the private network under the management of the router. In addition to buying such a NAT router in the market, a Linux host with multiple network ports can also complete this function.
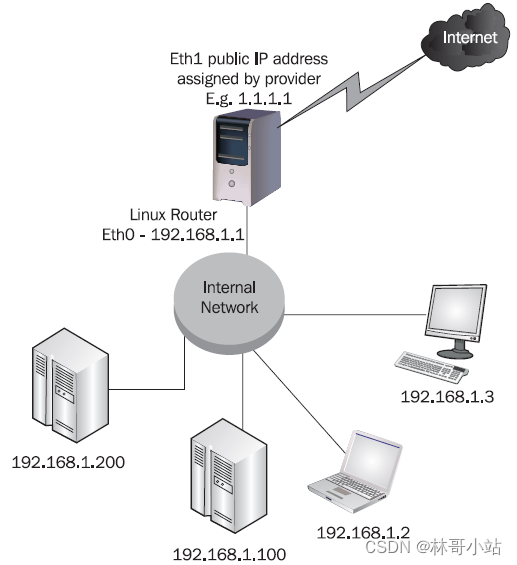
As shown in the figure above, we have a host "Linux Router". This host is connected to the public network through the public network IP address 1.1.1.1, and its other network card is connected to the internal private network 192.168.1.0/24. We all know that 192.168.1.0/24 has a private network segment. All IP addresses under this network segment are private IP addresses. Routers will not forward data packets with private IP addresses, so any host on the public network will It is impossible to access the host in our private network (so using a private IP address also provides network security protection for our host).
In order to enable hosts in the private network to communicate with hosts in the external network, the NAT router (Linux router host) converts the private IP addresses of the hosts in the private network into its own public IP (ie 1.1.1.1). Here, the host on the external network communicates with the public IP address of the Linux router, so it needs to know which packets are for itself and which packets are for other hosts in the private network below it. The host Linux router completes this distinction by maintaining a database of all TCP/IP connections through it. We call this function connection tracking, and the Linux host implements this connection tracking function by creating and maintaining a TCP/UDP connection state table in memory . The state information of all these connections is saved in the /proc/net/ip_conntrack directory. This state table mainly includes: IP address, port number, protocol type, connection state and timeout state. as follows:
tcp 6 262872 ESTABLISHED src=2.2.2.2 dst=1.1.1.1 sport=80 dport=65000 [UNREPLIED] src=192.168.1.2 dst=2.2.2.2 sport=65000 dport=80 use=1
udp 17 174 src=1.1.1.1 dst=1.1.1.11 sport=40997 dport=161 src=1.1.1.11 dst=1.1.1.1 sport=161 dport=40997 [ASSURED] use=1
Through the connection tracking function, Linux router knows that when a response message (used to respond to the request initiated by 192.168.1.2) arrives at 1.1.1.1, this message needs to be forwarded to the laptop computer 192.168.1.2, so it will send the response The destination IP address of the packet is rewritten from 1.1.1.1 to 192.168.1.2, and then forwarded to 192.168.1.2. Note: A firewall based on the connection tracking feature is called a stateful firewall.
NAT functions can be divided into the following categories according to scenarios:
- One-to-one NAT (1:1):
directly convert a private IP address to a public IP address, as shown in the figure above, if there is only one host computer in our private network, then we can use one-to-one NAT. - One-to-many NAT (1:N):
One private IP address is translated into multiple public IP addresses. This means that for each TCP/UDP connection initiated by a host on the private network to a host on the public network, the NAT router must select a public IP from its public IP library, and then convert the private IP to the selected one. public IP. As shown above, if there is only one host computer in our private network, but we have multiple public IPs, then we can choose one-to-many NAT. - Many-to-one NAT (N:1):
As shown in the figure above, there are multiple private IPs, but only one public IP, so the NAT router needs to convert multiple private IPs into the same private IP address (if this public IP belongs to This router, then we call it IP masquerading masquerading). - Many-to-many NAT (N:N):
There are multiple private IPs and multiple public IPs. We need to convert multiple private IPs into specified multiple public IPs. Here we need to use many-to-many NAT.
1.1, SNAT and IP Masquerade (Masquerade)
SNAT (Source Network Address Translation) is the abbreviation of source IP address translation. Because in SNAT, only the source IP address will be translated. The NAT device will convert the source IP address of the IP packets sent by all devices carried by the NAT device into the IP address of the egress device of the NAT device. The source IP address of the data packet will be translated only when access to the external network is required, but it should be noted that the source IP address of the request IP packet initiated from a public network server on the external network will not be converted, nor will the source IP address be converted. Forward to any server in the private network (meaning that all access connections need to be initiated by a host in the private network). This provides access protection for servers in the private network, and also saves a lot of public network IP addresses. SNAT is divided into static SNAT and dynamic SNAT. Static SNAT means that the IP addresses of one or more hosts behind NAT will be converted to the same public IP address. Dynamic SNAT means that the IP addresses of one or more hosts behind NAT The IP address will be converted into a series of public network IP addresses. Under dynamic NAT, the NAT router will select an IP address from the public network IP pool for each connection, so multiple connections to the same host are likely to be converted to different public network source IP addresses. Usually, dynamic SNAT, iptables will select the least used public network IP address for this connection when each connection is initialized. If there are multiple IPs in the IP pool that have never been used, iptables will randomly select one of them. IP masquerading Masquerade (MASQ) works in static SNAT mode, if you cannot specify an IP (for example, the public network interface automatically obtains IP), then the IP masquerading function can automatically use the network card connected to the external network of the NAT router IP address.
注意:SNAT是被iptables在linux内核2.4中由Netfilter引入的,而IP伪装则被iptables保留下来,以支持如PPP接口这一类动态配置
IP地址的接口,它用IP伪装MASQ去代替先找到动态分配的IP再做SNAT这样的过程。
In order to support SNAT or Masquerade, the NAT router must support the connection tracking function, so that it can know which server in the private network initiated the current connection data, and then it can know how to do SNAT and forward the data.
The following figure shows how SNAT, MASQ and connection tracking work:
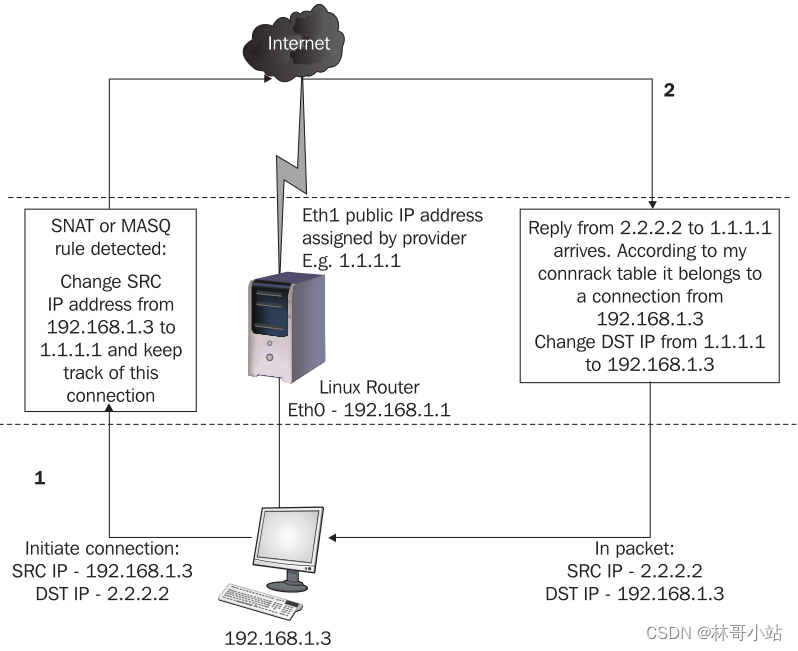
In this figure,
-
The host 192.168.1.3 actively initiates a connection to 2.2.2.2. The data packet of this connection request is sent to the Linux router. At this time, the source IP address of this request data packet is 192.168.1.3, and the destination IP address is 2.2.2.2.
-
If we configure SNAT or Masqueraded for the IP of 192.168.1.3 at this time, Linux router will change the source IP address in the IP header of the request message from 192.168.1.3 to 1.1.1.1, and then send the packet to 2.2 according to the routing protocol .2.2. Also save this connection information to /proc/net/ip_conntrack.
-
When the response message of 2.2.2.2 is received, the source IP of the response message arriving at the Linux router is 2.2.2.2 and the destination IP is 1.1.1.1. Here, the Linux router searches for connection information in /proc/net/ip_conntrack, and then finds the connection established in the previous step.
-
The Linux router will change the target IP address in the IP header of the response message from 1.1.1.1 to 192.168.1.3, and then send the IP message to the 192.168.1.3 host according to the routing rules.
注意:使用SNAT或IP伪装Masquerade时,只有192.168.1.3可以发起到2.2.2.2的连接, 然而2.2.2.2不能发起到192.168.1.3的连接。因为192.168.1.3是一个私网IP地址。
1.2、DNAT
DNAT (Destination Network Address Translations) converts a public IP address into a private IP address. The function of DNAT is opposite to that of SNAT, so if you use SNAT to convert a private network IP address to a public network IP address and DNAT to convert the same public network IP address to the same private network IP address at the same time, then it is A full NAT is formed . DNAT is usually used in the following scenarios. You have multiple servers behind NAT. You map the same public IP address to different private IP addresses according to different ports or protocols. For example, HTTP requests are transferred to HTTP servers, FTP The request goes to the FTP server. So this DNAT is also called port forwarding . As shown in the figure below:
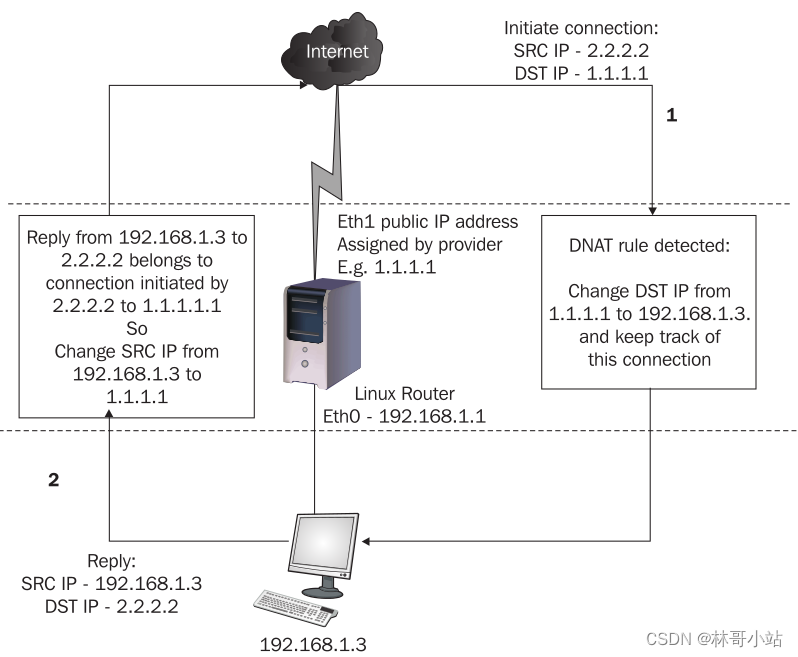
Under normal circumstances, the host 2.2.2.2 cannot actively initiate a connection with the host 192.168.1.3, because 192.168.1.3 is a private network IP address, and the router on the public network will not forward the target address For IP packets with private network addresses. But the 2.2.2.2 host can initiate a connection request with the 1.1.1.1 host.
-
At this point, if we configure the DNAT rule on the 1.1.1.1 host, and the request message commands the DNAT rule, Linux router will change the target IP address in the IP header of the request message from 1.1.1.1 to 192.168.1.3 , and then forward this message to 192.168.1.3, and then record the current connection in its connection tracking database.
-
When 192.168.1.3 sends back a response message, Linux router will query its connection tracking database and find that this response message belongs to the connection initiated by 2.2.2.2 to 1.1.1.1
-
Linux router will change the source IP address in the IP header of the response message from 192.168.1.3 to 1.1.1.1. Then the message is sent to 2.2.2.2.
注意:如果只配置了DNAT,但没有配置SNAT,那么 2.2.2.2可以通过将目标地址设置为1.1.1.1,从而和 192.168.1.3建立连接。但192.168.1.3不能主动发起连接到2.2.2.2。
Digression: Many home SOHO routers call the DNAT function they provide DMZ. In fact, it is not entirely correct to call DNAT a DMZ. DMZ is the abbreviation of Demilitarized Zone, which means an area in your network that does not set any filtering rules. DMZ is essentially a collection of public IPs. Servers using these public network IPs allow any connection (allowing all connections and communications in and out of the two directions). In fact, home SOHO routers make an IP masquerade Masquerade for the LAN, so they use the private server that can receive all the target IPs as the public IP of the WAN port of the router as the DMZ.
1.3, Full NAT (also known as Full Cone NAT)
Full NAT is to completely map one IP address to another IP address. When full NAT is configured, a server with a private IP address behind NAT (for example: 192.168.1.3) will be completely regarded as the public network IP address (for example 1.1.1.1) provided by the NAT router on the public network. This means that the request message sent by 192.168.1.3 is completely equivalent to the message received from 1.1.1.1 (SNAT) in the view of the host on the public network. .All packets sent from other hosts on the public network to 1.1.1.1, the NAT router will change the target IP address to 192.168.1.3 and forward it to the 192.168.1.3 host, even if this message does not belong to any one initiated by the 192.168.1.3 host connection (DNAT).
In other words, full NAT = SNAT+DNAT . When the Linux router receives an IP message from the public network that does not belong to any connection initiated by any private network host, it will be forwarded to 192.168.1.3, so the host 192.168.1.3 is not subject to any connection restrictions because of its private IP address and security protection.
注意:在上一章的DNAT的例子里,1.1.1.1可以是NAT路由器的公网IP地址,也可以是它能收到目标地址为1.1.1.1的报文就可以(其它路由
器会把目标为1.1.1.1的报文转发给NAT路由器)。如果1.1.1.1是NAT路由器的公网IP地址(如上一章图所示), 我产就无法从公网上访问
NAT路由器(比如:我们就无法SSH登录到NAT路由器),因为NAT路由器会把所有发给1.1.1.1的报文都转发给192.168.1.3。
1.4, PAT (also known as NAPT)
PAT is the abbreviation of Port Address Translation, which means port address translation, also known as NAPT, which is the abbreviation of Network Address and Port Translation, which means address and port translation. PAT not only isolates and hides the IP address, but also isolates and hides the port number of a specific server. For example, the company's web server is deployed behind a NAT router, and the IP address of the web server is 192.168.1.100. Then the NAT router has only one IP address of the public network. In the DNS server, we configure the IP address of http://www.ourcompanyname.com to 1.1.1.1. If we want to access this web server from the public network, the NAT router needs to change the destination IP address of all received IP packets sent to 1.1.1.1 with destination port number 80 to 192.168.1.100. In addition, the company also has a dedicated intranet web server 192.168.1.200, which also runs on port 80 (we know that the web server should run on port 80 according to the protocol). When in the office, we can access the intranet web server through the address http://192.168.1.200. But if we want to be able to access the web server of the internal network from the external network, then we need to implement this function through PAT. We can choose a port number (such as port 2143) that is not in use on the NAT router, and then send it to The destination address and port of all IP packets on port 2143 of 1.1.1.1 are changed to 192.168.1.200 and port 80.
With this configuration, on the external network:
- Visit http://www.ourcompanyname.com, that is, the message sent to 1.1.1.1:80 will be sent to 192.168.1.100:80, then you can visit the company's extranet homepage.
- Visit http://www.ourcompanyname.com:2143, that is, the message sent to 1.1.1.1:2143 will be sent to 192.168.1.200:80, then you can visit the company's intranet homepage.
If the company's intranet web server needs to actively access the external network, the NAT server does not need to rewrite the port of the IP packet whose source IP address is 192.168.1.200, and only needs to configure SNAT or Masquerade.
2. How to configure a host with multiple network cards as a NAT router through iptables
to be continued
3. Summary
to be continued