In recent years, with the rapid development of Internet technology, our dependence on the Internet is also increasing. Using the efficient and convenient tool of the Internet, we can transfer files, share pictures and communicate with others anytime and anywhere. However, the seemingly safe chat window is actually behind the huge Internet computing power to maintain the operation. Every action of ours will leave traces on the Internet. Although major manufacturers have strict confidentiality measures to protect the privacy of customers , but our data still leaks from time to time.
Objectively speaking, our mobile phones and other mobile terminals have limited storage. Photos, video images, etc. all need a specific place to store, and there are many compressed and packaged resources that cannot be stored on mobile phones at all. Many cloud storage software on the market always have defects of one kind or another, either the download speed is too slow or the storage space is limited. Incidents such as private photo leaks and a certain disk overturning are not uncommon.
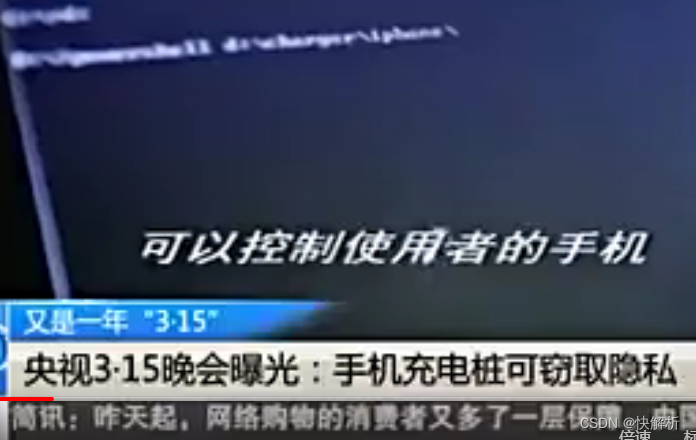
So how did our secret get out?
1. WiFi connection in public places: We usually walk in the streets and alleys with our mobile phones, wandering between major shops, and when we enter some shops with wireless networks, we often come to check their WiFi. You can steal important information of the access terminal by establishing a wireless hotspot, and your privacy may be known to everyone without knowing it.
2. Trojan horses on illegal websites: the Internet is extremely rich, and there are countless websites. In addition to normal websites, there are many illegal websites that take advantage of technical management loopholes. Once we browse the web and enter such a website inadvertently, your computer will be damaged. Or the mobile phone will have a high probability of being implanted with a Trojan horse, and it is possible to control your device through the Trojan horse and even monitor you through the camera.
3. Public charging piles: This incident was also exposed at the 315 party. Hackers can gain access to charging users' mobile phone permissions, penetrate into the user terminal, and steal the user's personal privacy.
4. Software stealing: Now we need to obtain permissions when downloading a lot of software. If we don’t look carefully, many optional permissions will be ignored by us. As everyone knows, after the software obtains permissions, it is very likely to enter your system through permissions to steal secrets , we must carefully analyze and read the installation permission application under the premise of ensuring that the software is official and genuine, so as to protect our privacy and security.
However , in our study and work, we often encounter situations that require file sharing. Some veteran drivers with experience and certain technical means know that they can build a NAS private cloud, which can be easily solved by building an HTTP/FTP/Web server , but for individuals In other words, it is quite a luxury to build a private cloud just for some files used in life or work, and many technical noobs don't know how to build these.
Don't panic, here is an easy-to-use file storage and sharing artifact that can be easily deployed by novices: HFS (Http File Server)
HFS, which is a software for uploading files . The HTTP file system designed for individual users - Http File Server, if you feel that setting up FTP Server is too troublesome, then this software can provide you with a more convenient file transfer system, no need to install after downloading, just execute hfs.exe after decompression , click the right mouse button under the "Virtual File System" pane to add/remove virtual file folders, or directly drag and drop the files you want to add to this window to set up a personal HTTP virtual file server . After double-clicking to run the main program, directly drag and drop the files you want to share to the "Virtual File System" pane, and you can quickly set up an HTTP file server, and other people can quickly access, download and upload files through the IP address, suitable for individuals , project team or file sharing needs in the family.
The operation of Quick Analysis + HFS is extremely convenient. It can realize remote downloading and sharing of HFS in the local intranet in a network environment without a public network IP . So how to achieve this operation?
1. Download the quick analysis client
2. Register a quick analysis account, add a mapping port, and you can get an "external network access address"
According to the above method of using HFS, right-click on the "Virtual File System" pane and select "Add File"; or drag the file here .
In this way, you can remotely access various file resources deployed on the intranet device anytime, anywhere. Quickanalysis uses bank-level data encryption, which can be said to be very good for user data security. It fully uses p2p technology to directly nat Penetration, without port mapping , so that LAN data can be accessed on the external network, with faster and more stable access speed ; HTTPS protocol is constructed by SSL+HTTP protocol, which can be encrypted for transmission to ensure the security of data transmission.
In this way, you no longer have to worry about the security of data transmission.