2023 Guizhou Provincial Vocational Skills Competition "Network Security" project task book
3. Contents of the competition task book
(1) Topology map
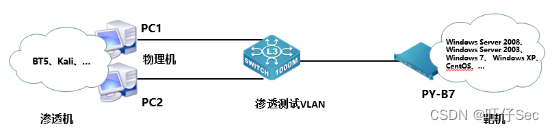
(2) Infrastructure Setting/Security Hardening for Module A (200 points)
1. Project and task description:
Assume that you are a network security engineer of an enterprise. For the server system of the enterprise, ensure the normal operation of each service according to the task requirements, and through the comprehensive use of login and password policies, flow integrity protection policies, event monitoring policies, firewall policies and other security Strategies to enhance the network security defense capabilities of the server system.
2. Description:
1. All screenshots require the screenshot interface and font to be clear, and be pasted at the position required by the corresponding topic;
2. File name naming and saving: network security module A-XX (XX is the station number), save in PDF format;
3. Save the file to the U disk and submit.
3. Server environment description
AServer06 (Windows) system: username administrator password P@ssw0rd
AServer07 (Linux) system: user name root password 123456
A-1: Login Security Hardening (Windows, Linux)
A-1 Task 1 Login Security Hardening (Windows, Linux)
Please set up the server Windows and Linux according to the requirements to improve the security of the server.
1. Password policy (Windows, Linux)
a. The minimum password length is not less than 13 characters;
b. Passwords must meet complexity requirements.
2. User security management (Windows)
a. Set to obtain the ownership of files or other objects, and assign this permission only to the administrators group;
b. Prohibit ordinary users from using the command prompt;
c. Set not to display the last login user name.
A-2: Nginx Security Policy (Linux)
1...Prohibit directory browsing and hide server version and information display;
2. Restrict HTTP request methods, only GET, HEAD, and POST are allowed;
3. Set the client request body read timeout to 10;
4. Set the client request header read timeout to 10;
5. Downgrade the Nginx service and use the www user to start the service.
A-3: Log Monitoring (Windows)
1. The size of the security log file must be at least 128MB. When the maximum log size limit is reached, the log older than 30 days will be overwritten;
2. The size of the application log file is at least 64MB, and when the maximum log size limit is reached, the log older than 15 days will be overwritten;
3. The system log size must be at least 32MB. When the maximum log size limit is reached, events will be overwritten as needed.
A-4: Middleware service hardening (Windows, Linux)
1. SSH service hardening (Linux)
a. Modify the ssh service port to 2222;
b.ssh prohibits the root user from logging in remotely;
c. Set up scheduled tasks for the root user. The ssh service is automatically opened at 7:50 every morning and closed at 22:50; the ssh service is restarted at 7:30 every Saturday;
d. Modify the PID file storage location of SSHD.
2. VSFTPD service hardening (Linux)
a. Set the non-privileged system user running vsftpd to pyftp;
b. Limit the port range of client connections to 50000-60000;
c. Limit the scope of local user login activities to the home directory.
3. IIS Hardening (Windows)
a. Open the log audit record of IIS (the log file save format is W3C, only record date, time, client IP address, user name, method);
b. Turn off the WebDAV function of IIS to enhance the security of the website.
A-5: Local Security Policy (Windows)
1. Anonymous enumeration of SAM accounts is prohibited;
2. Prohibit the system from shutting down without logging in;
3. It is forbidden to store passwords and credentials for network authentication;
4. It is forbidden to apply the Everyone permission to anonymous users;
5. Force logout after the login time is exceeded.
A-6: Firewall Policy (Linux)
1. Set the firewall to allow the machine to forward all data packets except ICMP protocol;
2. To prevent scanning software such as Nmap from detecting key information, set the iptables firewall policy to process traffic on port 80;
3. To defend against denial-of-service attacks, set the iptables firewall policy to filter incoming traffic, limit the incoming traffic to 3 packets per minute, and set the instantaneous traffic to process up to 6 data packets at a time (network data exceeding the upper limit The packet will be discarded and not processed);
4. Only DNS resolution request packets from the 172.16.0.0/24 LAN segment are allowed to be forwarded.
(3) Module B Security Incident Response/Network Security Data Forensics/Application Security (400 points)
B-1: Windows OS Penetration Testing
Task environment description:
Server scenario: Server2105 (close link)
Server scenario operating system: Windows (version unknown)
1. Perform system service and version scanning penetration testing on the server scenario through the penetration testing platform Kali in the local PC, and display the results of the operation Submit the service version information string corresponding to port 445 as the Flag value;
2. Use the penetration testing platform Kali in the local PC to perform a penetration test on the server scenario, and use the DNS information in the network connection information of the scenario as the Flag value (for example:
114.114. 114.114) to submit;
3. Penetration test the server scenario through the penetration testing platform Kali in the local PC, and submit the password of the current highest account administrator in the scenario as the Flag value; 4.
Penetration testing the server through the penetration testing platform Kali in the local PC To conduct a penetration test on the scenario, submit the name of the only file with the suffix .docx in the 111 folder on the desktop of the scenario as the Flag value; 5. Conduct a penetration
test on the server scenario through the penetration testing platform Kali in the local PC, The content of the only
document is submitted as the Flag value
; 6. Penetration test the server scene through the penetration testing platform Kali in the local PC, and the only picture in the 222 folder on the desktop of the scene English words in Chinese
are submitted as Flag values;
B-2: Hidden Information Exploration
Task environment description:
Server scenario: Server2007 (close link)
Server scenario operating system: Unknown
1. Access the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, find the FLAG in the login interface, and submit the FLAG;
2. Access the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, find the FLAG in the background of the login interface, and submit the FLAG; 3. Use the
penetration testing platform Kali in the local PC to access the website in the server scenario Server2007 Visit, log in on the login interface, find FLAG on the successful interface after successful login and submit;
4. Visit the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, and find the moon on the page after successful login , decrypt the information in the moon, and submit the decrypted information as FLAG;
5. Access the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, find the cross star on the page after successful login, and set the cross Download the content of the page in the star, decrypt the downloaded file, and submit the decrypted file content as FLAG;
6. Access the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, and log in in the login interface , after the login fails, find the link in the page to access the connection and download the file, and submit the full name of the hidden file in the file as FLAG; 7. Access the
website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, and in the login interface Login, after login failure, find the link in the page to access the connection and download the file, and submit the content of the hidden information file in the file as FLAG;
8. Access the website in the server scenario Server2007 through the penetration testing platform Kali in the local PC, find the hidden information in each page, merge each information in order, and submit it as FLAG;
B-3: Data Analysis Digital Forensics
Task Description:
Only the IP address of 20221219wire can be obtained.
1. Analyze the Attack.pcapng data packet file under the desktop of 20221219wire, and find out the data packet number of the malicious user’s first access to the HTTP service by analyzing the data packet Attack.pcapng. The number is submitted as the Flag value;
2. Continue to check the data packet file Attack.pcapng, analyze which ports the malicious user has scanned, and use all port numbers from small to large as the Flag value (form: port 1, port 2, port 3 ..., port n) submit;
3. Continue to check the data package file Attack.pcapng, analyze the password used by the malicious user to log in to the background, and submit the background password as the Flag value; 4. Continue to check the
data package file Attack.pcapng, analyze Find out what is the password of the one-sentence Trojan horse written by the malicious user, and submit the one-sentence password as the Flag value;
5. Continue to check the data package file Attack.pcapng, analyze what file the malicious user downloaded, and use the content of the file as the Flag value submit.
B-4: Web Penetration Testing
Task environment description:
only the IP address of 20221219web can be obtained
1. Obtain the version number of Apache and submit it as the Flag value (for example: 5.2.14);
2. Obtain the version number of the Samba server and submit it as the Flag value (for example: 5.0.22);
3. Obtain the kernel version number of the system and submit it as the Flag value (for example: 2.6.18);
4. Submit the picture content under the root path of the website as the Flag value;
5. Find the txt file in the /root directory and use the file content as the Flag value submitted.
B-5: Windows OS Penetration Testing
Task environment description:
only the IP address of 20221219win can be obtained
1. Use the penetration testing platform Kali in the local PC
to perform system service and version scanning penetration testing on the server scenario 20221219win, and use the
service version information corresponding to port 1433 in the operation display results as the Flag Value (for example, 3.1.4500);
2. Use the penetration testing platform Kali in the local PC to perform system service and version scanning penetration testing on the server scenario 20221219win, and submit the fully qualified domain name of the host of the DNS server as the Flag value; 3. Submit the target
server Submit the password of the user with low authority in the SQL-Server database (cannot execute system commands through database instructions) as the Flag value;
4. Submit the password of the user with higher authority in the SQL-Server database in the target server (can execute system commands through database instructions) as Submit the Flag value;
5. Find the file with the suffix .docx in the 266437 folder in the C:\Windows\system32 folder, and submit the content of the document as the Flag value.
B-6: Escalation of Privilege by Infiltration
Task environment description:
Server scenario: Unknown
Server scenario Operating system: Unknown
Username: test Password: 1234564
1. Access the server host, find the administrator name in the host, and submit the administrator name as the flag value;
2. Access the server host, find For the patch information in the host, submit the patch number as the flag value;
3. Access the server host, find the administrator password in the host, and submit the administrator password as the flag value;
4. Access the server host, find the text document under the administrator desktop in the host Information, submit the text document name as the flag value;
5. Visit the server host, find the text document information under the administrator desktop in the host, and submit the information in the text document as the flag value;
6. Visit the server host, find the only one in the recycle bin in the host Information, submit the content in the information as the value of flag6.
( 4 ) Module C CTF Capture the Flag-Attack
(200 points for this module )
1. Project and task description:
Suppose you are a network security penetration test engineer of an enterprise, responsible for the security protection of certain servers of the enterprise, in order to better find various problems and vulnerabilities that may exist in the enterprise network. You try to use various attack methods to attack specific target drones, so as to understand the latest attack methods and technologies, and understand the mentality of network hackers, so as to improve your defense strategy.
Please log in to the answering platform using the Google browser on the client side according to the information provided in the "Competition Parameter Table".
2. Operating system environment description:
Guest OS: Windows 10/Windows7
Target server operating system: Linux/Windows
3. Vulnerability description:
1. Vulnerabilities in the server may be conventional or system vulnerabilities;
2. There may be a command injection vulnerability in the website on the target machine server. Players are required to find the relevant vulnerability of command injection and use this vulnerability to obtain certain permissions;
3. There may be a file upload vulnerability on the website on the target machine server. Players are required to find the relevant vulnerability in file upload and use this vulnerability to obtain certain permissions;
4. There may be loopholes in the files contained in the website on the target machine server. Players are required to find the relevant loopholes contained in the files and combine them with other loopholes to obtain certain permissions and elevate their rights;
5. The service provided by the operating system may contain a remote code execution vulnerability, requiring the user to find the remote code execution service and use this vulnerability to obtain system permissions;
6. The services provided by the operating system may contain buffer overflow vulnerabilities, requiring users to find services with buffer overflow vulnerabilities and use this vulnerability to obtain system privileges;
7. There may be some system backdoors in the operating system. Players can find the backdoors and use the reserved backdoors to directly obtain system permissions.
4. Matters needing attention:
1. The referee server cannot be attacked. If the attack continues after one warning, the team will be ordered to leave the field;
2. The flag value is the unique identifier of each target machine server, and each target machine server has only one;
3. After hacking into the target machine, the contestants are not allowed to close the port, change the password, restart or shut down the target machine, delete or modify the flag, create unnecessary files and other operations on the target machine;
4. After logging in to the automatic scoring system, submit the flag value of the target machine server and specify the IP address of the target machine server;
5. The arena has target drones with different basic points according to the difficulty. For each target server, the first three teams that get the flag value will add points to the basic points. The total score of each team at this stage is The entry stage score, the specific extra points rules refer to the field scoring standards;
6. There will be no additional time for this session.
( 5 ) Module D CTF Capture the Flag - Defense
(200 points for this module)
1. Project and task description:
Assume that each contestant is a network security engineer of a security company, and is responsible for the penetration testing and security protection of several servers. These servers may have various problems and vulnerabilities. You need to penetration test and secure these servers as soon as possible. Each participating team has its own bastion host server, which cannot be accessed by other teams. Contestants detect the security flaws in their bastion servers through scanning, penetration testing and other means, and carry out targeted reinforcement to improve the security defense performance of the system.
Please log in to the answering platform using the Google browser on the client side according to the information provided in the "Competition Parameter Table".
2. Operating system environment description:
Guest OS: Windows 10/Windows7
Bastion server operating system: Linux/Windows
3. Vulnerability description:
1. Vulnerabilities in the bastion server may be conventional or system vulnerabilities;
2. The website on the bastion server may have a loophole of command injection. Players are required to find the loophole related to command injection and use this loophole to obtain certain permissions;
3. The website on the bastion server may have a file upload vulnerability. Players are required to find the relevant vulnerability of file upload and use this vulnerability to obtain certain permissions;
4. The website on the bastion server may contain loopholes in files. Players are required to find the relevant loopholes contained in the files and combine them with other loopholes to obtain certain permissions and escalate their privileges;
5. The service provided by the operating system may contain a remote code execution vulnerability, requiring the user to find the remote code execution service and use this vulnerability to obtain system permissions;
6. The services provided by the operating system may contain buffer overflow vulnerabilities, requiring users to find services with buffer overflow vulnerabilities and use this vulnerability to obtain system privileges;
7. There may be some system backdoors in the operating system. Players can find the backdoors and use the reserved backdoors to directly obtain system permissions.
4. Matters needing attention:
1. Each player needs to take screenshots of the reinforcement points and the reinforcement process, and make a system defense implementation report by himself. The final score is based on the implementation report;
2. When the system is hardened, it is necessary to ensure the availability of external services provided by the bastion server;
3. Do not attack the referee server. If you continue to attack after a warning, the team will be ordered to leave the field;
4. There will be no additional time for this session.
2. Description:
1. All screenshots require screenshot interface and clear fonts;
2. File name and save: network security module D-XX (XX is the station number), save in PDF format;
3. Save the file to the U disk and submit.