foreword

With the arrival of China's largest safety product performance test and the challenge of human physical fitness limits, all the big shots are showing their talents. At the same time, a large number of 0days have been made public. Excluding those who have been refuted, there are still many loopholes worth learning. Zhiyuan This is a combined vulnerability. First, any administrator logs in, and then getshell in the background. Because the foreground vulnerability is relatively more harmful, here we focus on analyzing the foreground vulnerability.
Detailed analysis
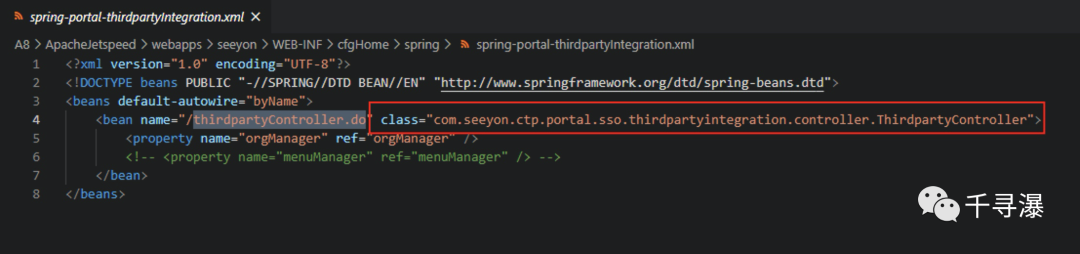
thirdpartyController.doZhiyuan oa uses the automatic assembly of spring, and can quickly locate the vulnerability class by searching the vulnerability URL in the xml file .
Find the problematic method according to exp.
After finding this method, you can basically see the vulnerability point at a glance. At the bottom of the method, the memberId here is controllable.
First, obtain the encoded L, M, and T parameters through the enc parameter.

Here LightWeightEncoder.decodeStringis a base64 encoding implemented by Zhiyuan itself, and the implementation method is very simple. It is to encode the plaintext into base64 first, and then add one to each encoded char. For example, the string encoded by base64 is abcd, which corresponds to bcde.
After the enc is obtained, the string will be split, first use & to split, then use = to split, and store it in the map object.
The linkType and timeStamp here are obtained from enc. timeStamp is a timestamp, we can directly use 2099 when constructing exp.
L is the connection address, the author of the vulnerability provides the message.link.doc.folder.open
same type message.link.doc.open.index, message.link.news.openetc.
M is the user id. The author of the vulnerability provides that -7273032013234748168
this value is the default id when the system is installed, and there are 4 default ids during installation, corresponding to different permissions.
"5725175934914479521" "集团管理员"
"-7273032013234748168" "系统管理员"
"-7273032013234748798" "系统监控"
"-4401606663639775639" "审计管理员"

Finally, get user information according to id through getMemberById

Finally, the poc is generated and sent, and the cookie for administrator login can be obtained