Introduction to Spring Security
Spring Security is a highly customizable security framework . Utilizing the functions of Spring IoC/DI and AOP, the system provides a declarative security access control function, which reduces the work of writing a large number of repetitive codes for system security. The two main areas with regard to security are " authentication " and " authorization " (or access control). These two points are also important core functions of Spring Security. In layman's terms, "authentication" means whether the system believes that the user can log in. Generally speaking, "authorization" means that the system judges whether the user has permission to do certain things.
The first step of preparation:
We first need to build a simple SpringBoot project, and then add security dependencies to the pom dependencies:
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
After introducing the security dependency, if we try to access the previous interface, we will automatically jump to a Spring Security default login page. The default username is user, and the password will be output on the console. You must log in to access the interface.
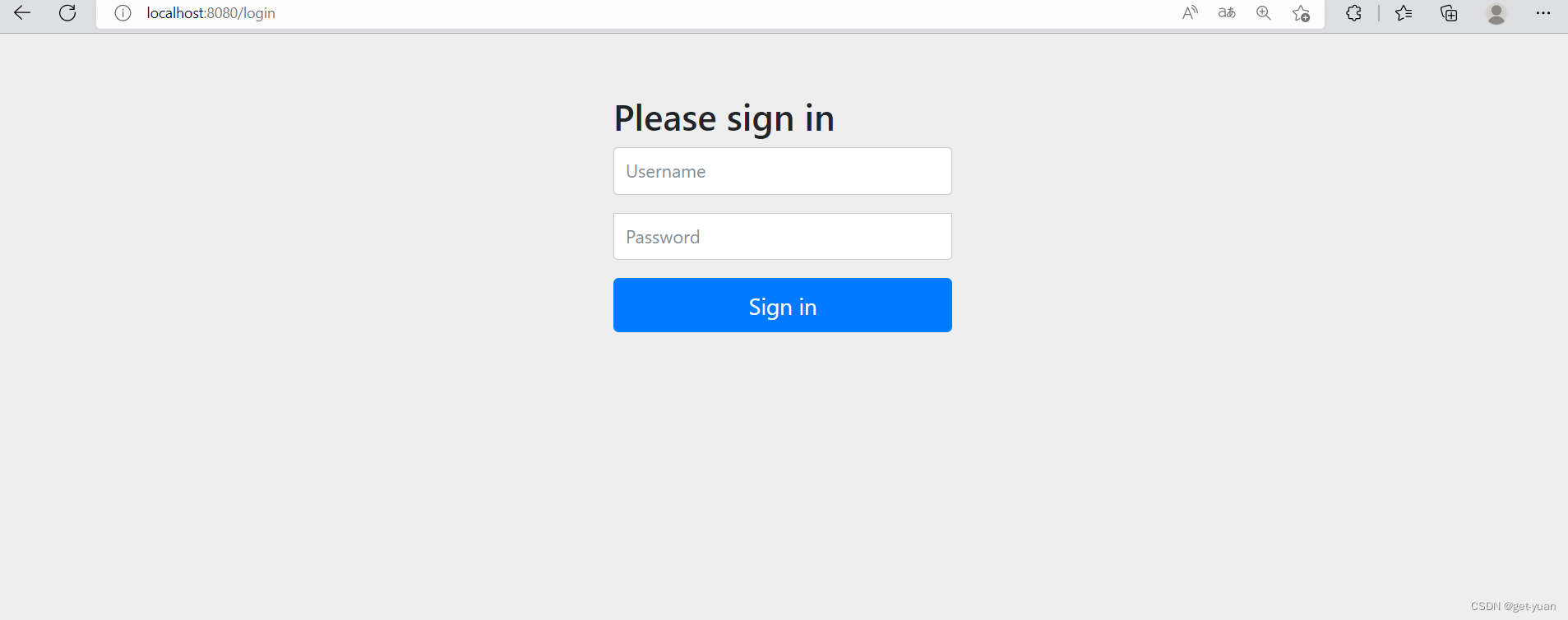
 Of course, in actual development, it is impossible for us to use the login interface that comes with the security framework, and we will encapsulate our own login interface later.
Of course, in actual development, it is impossible for us to use the login interface that comes with the security framework, and we will encapsulate our own login interface later.
The second step of the authentication principle flow chart and the detailed diagram of the authentication process
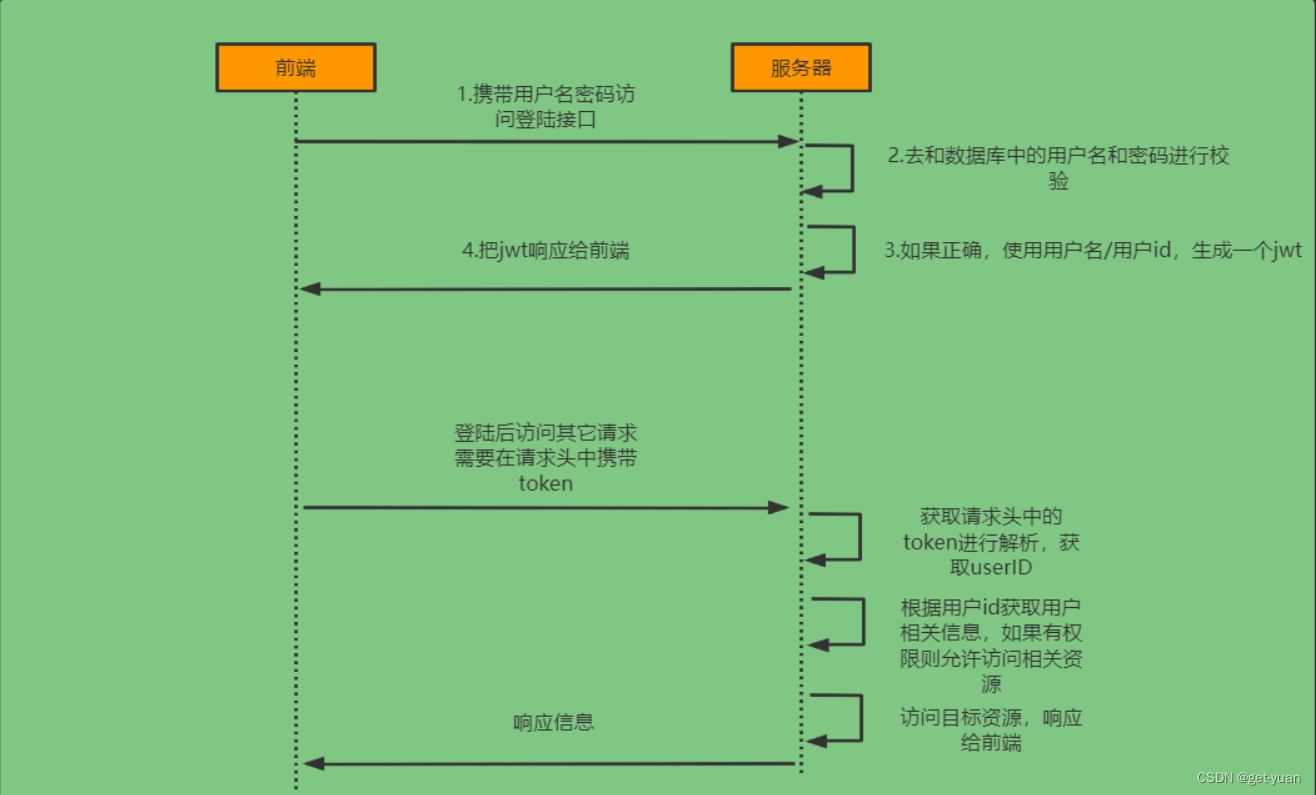
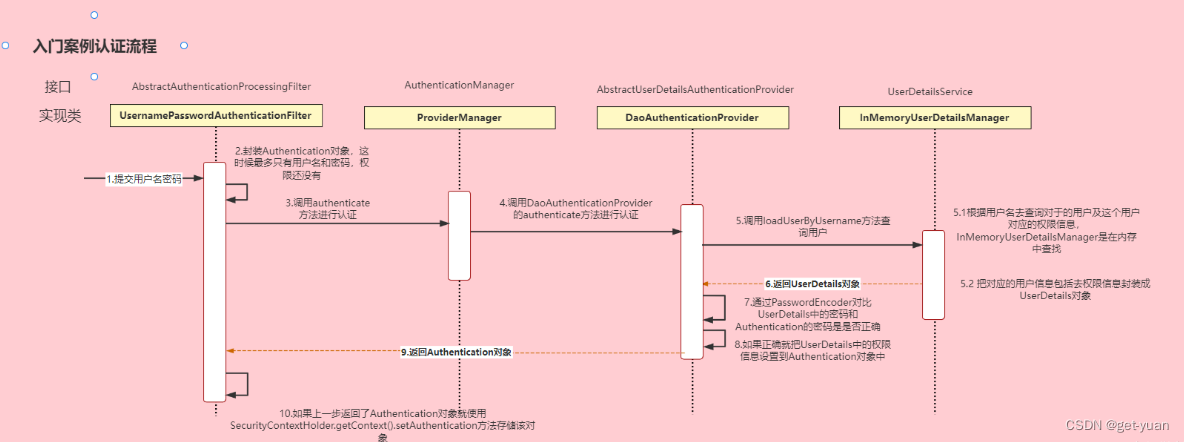
Interface explanation
Authentication interface: Its implementation class represents the user currently accessing the system and encapsulates user-related information.
AuthenticationManager interface: defines the authentication authentication method
UserDetailsService interface: the core interface for loading user-specific data. It defines a method to query user information based on username.
UserDetails interface: Provides core user information. The user information obtained and processed through the UserDetailsService according to the username should be encapsulated into a UserDetails object and returned. Then encapsulate this information into the Authentication object.
Idea summary
- Log in
①Custom login interface: Call the ProviderManager method for authentication. If the authentication passes and generate jwt, store the user information in redis.
②Custom UserDetailsService: Query the database in this implementation class
- check:
① Define Jwt authentication filter
- Get token
①Analyze the token to get the userid in it, get the user information from redis, and store it in the SecurityContextHolder
The fourth step is to integrate the practice into springboot
1. Add the necessary dependencies
<!--redis依赖-->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-data-redis</artifactId>
</dependency>
<!--fastjson依赖-->
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>fastjson</artifactId>
<version>1.2.33</version>
</dependency>
<!--jwt依赖-->
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt</artifactId>
<version>0.9.0</version>
</dependency>
2. Add Redis and its related configuration
Add tool classes FastJsonRedisSerializer, RedisCache, R, JwtUtil, WebUtils and configuration class RedisConfig
Package structure directory:
FastJsonRedisSerializer class (Redis uses FastJson serialization):
package com.hu.publicsecurity.utils;
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.ParserConfig;
import com.alibaba.fastjson.serializer.SerializerFeature;
import com.fasterxml.jackson.databind.JavaType;
import com.fasterxml.jackson.databind.type.TypeFactory;
import org.springframework.data.redis.serializer.RedisSerializer;
import org.springframework.data.redis.serializer.SerializationException;
import java.nio.charset.Charset;
/**
* Redis使用FastJson序列化
*
* @author sg
*/
public class FastJsonRedisSerializer<T> implements RedisSerializer<T>
{
public static final Charset DEFAULT_CHARSET = Charset.forName("UTF-8");
private Class<T> clazz;
static
{
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);
}
public FastJsonRedisSerializer(Class<T> clazz)
{
super();
this.clazz = clazz;
}
@Override
public byte[] serialize(T t) throws SerializationException
{
if (t == null)
{
return new byte[0];
}
return JSON.toJSONString(t, SerializerFeature.WriteClassName).getBytes(DEFAULT_CHARSET);
}
@Override
public T deserialize(byte[] bytes) throws SerializationException
{
if (bytes == null || bytes.length <= 0)
{
return null;
}
String str = new String(bytes, DEFAULT_CHARSET);
return JSON.parseObject(str, clazz);
}
protected JavaType getJavaType(Class<?> clazz)
{
return TypeFactory.defaultInstance().constructType(clazz);
}
}
RedisCache class (cache basic objects, Integer, String, entity classes, etc., or not encapsulated, but you have to be able to use the basic storage and acquisition statements of redis):
package com.hu.publicsecurity.utils;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.data.redis.core.BoundSetOperations;
import org.springframework.data.redis.core.HashOperations;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.data.redis.core.ValueOperations;
import org.springframework.stereotype.Component;
import java.util.*;
import java.util.concurrent.TimeUnit;
@SuppressWarnings(value = { "unchecked", "rawtypes" })
@Component
public class RedisCache
{
@Autowired
public RedisTemplate redisTemplate;
/**
* 缓存基本的对象,Integer、String、实体类等
*
* @param key 缓存的键值
* @param value 缓存的值
*/
public <T> void setCacheObject(final String key, final T value)
{
redisTemplate.opsForValue().set(key, value);
}
/**
* 缓存基本的对象,Integer、String、实体类等
*
* @param key 缓存的键值
* @param value 缓存的值
* @param timeout 时间
* @param timeUnit 时间颗粒度
*/
public <T> void setCacheObject(final String key, final T value, final Integer timeout, final TimeUnit timeUnit)
{
redisTemplate.opsForValue().set(key, value, timeout, timeUnit);
}
/**
* 设置有效时间
*
* @param key Redis键
* @param timeout 超时时间
* @return true=设置成功;false=设置失败
*/
public boolean expire(final String key, final long timeout)
{
return expire(key, timeout, TimeUnit.SECONDS);
}
/**
* 设置有效时间
*
* @param key Redis键
* @param timeout 超时时间
* @param unit 时间单位
* @return true=设置成功;false=设置失败
*/
public boolean expire(final String key, final long timeout, final TimeUnit unit)
{
return redisTemplate.expire(key, timeout, unit);
}
/**
* 获得缓存的基本对象。
*
* @param key 缓存键值
* @return 缓存键值对应的数据
*/
public <T> T getCacheObject(final String key)
{
ValueOperations<String, T> operation = redisTemplate.opsForValue();
return operation.get(key);
}
/**
* 删除单个对象
*
* @param key
*/
public boolean deleteObject(final String key)
{
return redisTemplate.delete(key);
}
/**
* 删除集合对象
*
* @param collection 多个对象
* @return
*/
public long deleteObject(final Collection collection)
{
return redisTemplate.delete(collection);
}
/**
* 缓存List数据
*
* @param key 缓存的键值
* @param dataList 待缓存的List数据
* @return 缓存的对象
*/
public <T> long setCacheList(final String key, final List<T> dataList)
{
Long count = redisTemplate.opsForList().rightPushAll(key, dataList);
return count == null ? 0 : count;
}
/**
* 获得缓存的list对象
*
* @param key 缓存的键值
* @return 缓存键值对应的数据
*/
public <T> List<T> getCacheList(final String key)
{
return redisTemplate.opsForList().range(key, 0, -1);
}
/**
* 缓存Set
*
* @param key 缓存键值
* @param dataSet 缓存的数据
* @return 缓存数据的对象
*/
public <T> BoundSetOperations<String, T> setCacheSet(final String key, final Set<T> dataSet)
{
BoundSetOperations<String, T> setOperation = redisTemplate.boundSetOps(key);
Iterator<T> it = dataSet.iterator();
while (it.hasNext())
{
setOperation.add(it.next());
}
return setOperation;
}
/**
* 获得缓存的set
*
* @param key
* @return
*/
public <T> Set<T> getCacheSet(final String key)
{
return redisTemplate.opsForSet().members(key);
}
/**
* 缓存Map
*
* @param key
* @param dataMap
*/
public <T> void setCacheMap(final String key, final Map<String, T> dataMap)
{
if (dataMap != null) {
redisTemplate.opsForHash().putAll(key, dataMap);
}
}
/**
* 获得缓存的Map
*
* @param key
* @return
*/
public <T> Map<String, T> getCacheMap(final String key)
{
return redisTemplate.opsForHash().entries(key);
}
/**
* 往Hash中存入数据
*
* @param key Redis键
* @param hKey Hash键
* @param value 值
*/
public <T> void setCacheMapValue(final String key, final String hKey, final T value)
{
redisTemplate.opsForHash().put(key, hKey, value);
}
/**
* 获取Hash中的数据
*
* @param key Redis键
* @param hKey Hash键
* @return Hash中的对象
*/
public <T> T getCacheMapValue(final String key, final String hKey)
{
HashOperations<String, String, T> opsForHash = redisTemplate.opsForHash();
return opsForHash.get(key, hKey);
}
/**
* 删除Hash中的数据
*
* @param key
* @param hkey
*/
public void delCacheMapValue(final String key, final String hkey)
{
HashOperations hashOperations = redisTemplate.opsForHash();
hashOperations.delete(key, hkey);
}
/**
* 获取多个Hash中的数据
*
* @param key Redis键
* @param hKeys Hash键集合
* @return Hash对象集合
*/
public <T> List<T> getMultiCacheMapValue(final String key, final Collection<Object> hKeys)
{
return redisTemplate.opsForHash().multiGet(key, hKeys);
}
/**
* 获得缓存的基本对象列表
*
* @param pattern 字符串前缀
* @return 对象列表
*/
public Collection<String> keys(final String pattern)
{
return redisTemplate.keys(pattern);
}
}
R class and ResultCode interface (unified return result set):
package com.hu.publicsecurity.utils.commonResult;
import io.swagger.annotations.ApiModelProperty;
import lombok.Data;
import java.util.HashMap;
import java.util.Map;
/**
* 同一返回结果的类
*/
@Data
public class R {
@ApiModelProperty(value = "是否成功")
private Boolean success;
@ApiModelProperty(value = "返回码")
private Integer code;
@ApiModelProperty(value = "返回消息")
private String message;
@ApiModelProperty(value = "返回数据")
private Map<String,Object> data= new HashMap<>();
private R(){}//构造方法私有化,表示这个构造方法只能被这个类的内部所使用
/**
* 成功静态方法
* @return
*/
public static R ok(){
R r = new R();
r.setSuccess(true);
r.setCode(ResultCode.SUCCESS);
r.setMessage("成功");
return r;
}
/**
* 成功静态方法
* @return
*/
public static R error(){
R r = new R();
r.setSuccess(false);
r.setCode(ResultCode.ERROR);
r.setMessage("失败");
return r;
}
//实现链式编程
public R success(Boolean success){
this.setSuccess(success);
return this;
}
public R message(String message){
this.setMessage(message);
return this;
}
public R code(Integer code){
this.setCode(code);
return this;
}
public R data(String key,Object value){
this.data.put(key, value);
return this;
}
public R data(Map<String,Object> map){
this.setData(map);
return this;
}
}
package com.hu.publicsecurity.utils.commonResult;
public interface ResultCode {
public static Integer SUCCESS=20000;//成功
public static Integer ERROR=20001;//失败
public static Integer EMPTY=40000;//为空
}
JwtUtil class:
package com.hu.publicsecurity.utils;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.JwtBuilder;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
import java.util.Date;
import java.util.UUID;
/**
* JWT工具类
*/
public class JwtUtil {
//有效期为
public static final Long JWT_TTL = 60 * 60 *1000L;// 60 * 60 *1000 一个小时
//设置秘钥明文
public static final String JWT_KEY = "huyannan";
public static String getUUID(){
String token = UUID.randomUUID().toString().replaceAll("-", "");
return token;
}
/**
* 生成jtw
* @param subject token中要存放的数据(json格式)
* @return
*/
public static String createJWT(String subject) {
JwtBuilder builder = getJwtBuilder(subject, null, getUUID());// 设置过期时间
return builder.compact();
}
/**
* 生成jtw
* @param subject token中要存放的数据(json格式)
* @param ttlMillis token超时时间
* @return
*/
public static String createJWT(String subject, Long ttlMillis) {
JwtBuilder builder = getJwtBuilder(subject, ttlMillis, getUUID());// 设置过期时间
return builder.compact();
}
private static JwtBuilder getJwtBuilder(String subject, Long ttlMillis, String uuid) {
SignatureAlgorithm signatureAlgorithm = SignatureAlgorithm.HS256;
SecretKey secretKey = generalKey();
long nowMillis = System.currentTimeMillis();
Date now = new Date(nowMillis);
if(ttlMillis==null){
ttlMillis=JwtUtil.JWT_TTL;
}
long expMillis = nowMillis + ttlMillis;
Date expDate = new Date(expMillis);
return Jwts.builder()
.setId(uuid) //唯一的ID
.setSubject(subject) // 主题 可以是JSON数据
.setIssuer("huyannan") // 签发者
.setIssuedAt(now) // 签发时间
.signWith(signatureAlgorithm, secretKey) //使用HS256对称加密算法签名, 第二个参数为秘钥
.setExpiration(expDate);
}
/**
* 创建token
* @param id
* @param subject
* @param ttlMillis
* @return
*/
public static String createJWT(String id, String subject, Long ttlMillis) {
JwtBuilder builder = getJwtBuilder(subject, ttlMillis, id);// 设置过期时间
return builder.compact();
}
/**
* 生成加密后的秘钥 secretKey
* @return
*/
public static SecretKey generalKey() {
byte[] encodedKey = Base64.getDecoder().decode(JwtUtil.JWT_KEY);
SecretKey key = new SecretKeySpec(encodedKey, 0, encodedKey.length, "AES");
return key;
}
/**
* 解析
*
* @param jwt
* @return
* @throws Exception
*/
public static Claims parseJWT(String jwt) throws Exception {
SecretKey secretKey = generalKey();
return Jwts.parser()
.setSigningKey(secretKey)
.parseClaimsJws(jwt)
.getBody();
}
}
WebUtils class:
package com.hu.publicsecurity.utils;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
public class WebUtils
{
/**
* 将字符串渲染到客户端
*
* @param response 渲染对象
* @param string 待渲染的字符串
* @return null
*/
public static String renderString(HttpServletResponse response, String string) {
try
{
response.setStatus(200);
response.setContentType("application/json");
response.setCharacterEncoding("utf-8");
response.getWriter().print(string);
}
catch (IOException e)
{
e.printStackTrace();
}
return null;
}
}
Configuration class RedisConfig:
package com.hu.publicsecurity.config;
import com.hu.publicsecurity.utils.FastJsonRedisSerializer;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.data.redis.connection.RedisConnectionFactory;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.data.redis.serializer.StringRedisSerializer;
@Configuration
public class RedisConfig {
@Bean
@SuppressWarnings(value = { "unchecked", "rawtypes" })
public RedisTemplate<Object, Object> redisTemplate(RedisConnectionFactory connectionFactory)
{
RedisTemplate<Object, Object> template = new RedisTemplate<>();
template.setConnectionFactory(connectionFactory);
FastJsonRedisSerializer serializer = new FastJsonRedisSerializer(Object.class);
// 使用StringRedisSerializer来序列化和反序列化redis的key值
template.setKeySerializer(new StringRedisSerializer());
template.setValueSerializer(serializer);
// Hash的key也采用StringRedisSerializer的序列化方式
template.setHashKeySerializer(new StringRedisSerializer());
template.setHashValueSerializer(serializer);
template.afterPropertiesSet();
return template;
}
}
3. Write a User entity class that corresponds to your own database table:
package com.hu.publicsecurity.pojo;
import com.baomidou.mybatisplus.annotation.*;
import java.util.Date;
import java.io.Serializable;
import io.swagger.annotations.ApiModel;
import io.swagger.annotations.ApiModelProperty;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.EqualsAndHashCode;
import lombok.NoArgsConstructor;
/**
* <p>
*
* </p>
*
* @author 胡雁南
* @since 2022-07-05
*/
@Data
@AllArgsConstructor
@NoArgsConstructor
@EqualsAndHashCode(callSuper = false)
@ApiModel(value="User对象", description="")
public class User implements Serializable {
private static final long serialVersionUID = 1L;
@ApiModelProperty(value = "用户id")
@TableId(value = "id", type = IdType.AUTO)
private Long id;
@ApiModelProperty(value = "用户账号")
private String username;
@ApiModelProperty(value = "用户密码")
private String password;
@ApiModelProperty(value = "用户姓名")
private String nickName;
@ApiModelProperty(value = "用户头像")
private String avatar;
@ApiModelProperty(value = "账号状态")
@TableField(fill = FieldFill.INSERT)
private Boolean status;
@ApiModelProperty(value = "版本号(乐观锁)")
@Version
private Integer version;
@ApiModelProperty(value = "逻辑删除")
@TableField(fill = FieldFill.INSERT)
@TableLogic
private Boolean isDeleted;
@ApiModelProperty(value = "创建时间")
@TableField(fill = FieldFill.INSERT)
private Date createTime;
@ApiModelProperty(value = "更新时间")
@TableField(fill = FieldFill.INSERT_UPDATE)
private Date updateTime;
}
4. Create a class that implements the UserDetailsService interface
Override the methods in it. The main implementation is to query user information from the database through the username username for verification:
package com.hu.publicsecurity.service.impl;
import com.baomidou.mybatisplus.core.conditions.query.QueryWrapper;
import com.hu.publicsecurity.handler.CustomException;
import com.hu.publicsecurity.mapper.UserMapper;
import com.hu.publicsecurity.pojo.User;
import com.hu.publicsecurity.pojo.vo.LoginUser;
import com.hu.publicsecurity.utils.commonResult.ResultCode;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import java.util.Objects;
@Service
public class UserDetailsServiceImpl implements UserDetailsService {
@Autowired
private UserMapper userMapper;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
//根据用户名查询用户信息
QueryWrapper<User> wrapper = new QueryWrapper<>();
wrapper.eq("username", username);
User user = userMapper.selectOne(wrapper);
//如果查询不到数据就通过抛出异常来给出提示
if (Objects.isNull(user)) {
throw new CustomException(ResultCode.ERROR, "用户名或者密码错误");
}
//TODO 可以根据用户信息查询权限信息 添加到LoginUser中
//因为返回的类型必须是UserDetails,所以必须定义一个类来实现
LoginUser loginUser = new LoginUser(user);
return loginUser;
}
}
Because the return value of the UserDetailsService method is the UserDetails type, you need to define a class LoginUser
, implement this interface, and encapsulate user information in it.
package com.hu.publicsecurity.pojo.vo;
import com.hu.publicsecurity.pojo.User;
import lombok.AllArgsConstructor;
import lombok.Data;
import lombok.NoArgsConstructor;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.Collection;
@Data
@AllArgsConstructor
@NoArgsConstructor
public class LoginUser implements UserDetails {
private User user;
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
return null;
}
@Override
public String getPassword() {
return user.getPassword();
}
@Override
public String getUsername() {
return user.getUsername();
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return true;
}
}
5. Use the BCryptPasswordEncoder method provided by SpringSecurity for password encryption:
We can define a SecurityConfig configuration class, which SpringSecurity requires to inherit from WebSecurityConfigurerAdapter.
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Bean
public PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
}
Six, custom login interface
Customize the login interface, let SpringSecurity release this interface, and allow users to access this interface without logging in. In the interface, we use the authenticate method of AuthenticationManager to perform user authentication, so we need to configure in SecurityConfig to inject AuthenticationManager into the container. If the authentication is successful, a jwt should be generated and returned in the response. And in order to allow the user to identify the specific user through jwt when the user requests next time, we need to store the user information in redis, and the user id can be used as the key.
login controller layer
package com.hu.publicsecurity.controller;
import com.hu.publicsecurity.pojo.User;
import com.hu.publicsecurity.service.LoginService;
import com.hu.publicsecurity.utils.commonResult.R;
import io.swagger.annotations.Api;
import io.swagger.annotations.ApiOperation;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.web.bind.annotation.*;
@Api(tags = "登录和注销接口")
@RestController
@CrossOrigin
public class LoginController {
@Autowired
private LoginService loginService;
@ApiOperation("通过账号和密码进行登录获得token")
@PostMapping("/user/login")
public R login(@RequestBody User user) {
String jwt = loginService.login(user);
return R.ok().data("token",jwt);
}
SecurityConfig configuration class:
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Bean
public PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http
//关闭csrf
.csrf().disable()
//不通过Session获取SecurityContext
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS)
.and()
.authorizeRequests()
// 对于登录接口 允许匿名访问
.antMatchers("/user/login").anonymous()
// 除上面外的所有请求全部需要鉴权认证
.anyRequest().authenticated();
}
@Bean
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
}
login service implementation class
package com.hu.publicsecurity.service.impl;
import com.hu.publicsecurity.handler.CustomException;
import com.hu.publicsecurity.pojo.User;
import com.hu.publicsecurity.pojo.vo.LoginUser;
import com.hu.publicsecurity.service.LoginService;
import com.hu.publicsecurity.utils.JwtUtil;
import com.hu.publicsecurity.utils.RedisCache;
import com.hu.publicsecurity.utils.commonResult.ResultCode;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.stereotype.Service;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Autowired
private AuthenticationManager authenticationManager;
@Autowired
private RedisCache redisCache;
@Override
public String login(User user) {
//把登陆时用户的账户和密码封装成一个authentication对象
UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(user.getUsername(), user.getPassword());
//AuthenticationManager authentication进行用户登录认证,会把
Authentication authenticate = authenticationManager.authenticate(authenticationToken);
//如果认证没通过,给出对应的提示
if (Objects.isNull(authenticate)) {
throw new CustomException(ResultCode.ERROR,"登录失败");
}
//如果认证通过,使用userid生成一个jwt jwt存入返回结果集返回,
// 1、先获得LoginUser对象,
LoginUser loginUser = (LoginUser) authenticate.getPrincipal();
// 2、再从LoginUser对象中取得userid
String userid = loginUser.getUser().getId().toString();
// 3、生成token(jwt)
//需要导入jaxb-api依赖,否者会报错
String jwt = JwtUtil.createJWT(userid);
/*System.out.println(jwt);*/
//把完整的用户信息存入redis中作为key
redisCache.setCacheObject("login:"+userid,loginUser);
return jwt;
}Here, when generating jwt, that is, when String jwt = JwtUtil.createJWT(userid);, an error may be reported: javax.xml.bind.DatatypeConverter, mainly because the jdk version is too high, and the following needs to be imported if jdk1.8 or above rely.
<!--解决Handler dispatch failed;nested exception is java.lang.NoClassDefFoundError: javax/xml/bind/DatatypeConverter-->
<!--以下javax.xml.bind依赖是因为jdk版本不同需要导入的依赖-->
<dependency>
<groupId>javax.xml.bind</groupId>
<artifactId>jaxb-api</artifactId>
<version>2.3.0</version>
</dependency>
<dependency>
<groupId>com.sun.xml.bind</groupId>
<artifactId>jaxb-impl</artifactId>
<version>2.3.0</version>
</dependency>
<dependency>
<groupId>com.sun.xml.bind</groupId>
<artifactId>jaxb-core</artifactId>
<version>2.3.0</version>
</dependency>
<dependency>
<groupId>javax.activation</groupId>
<artifactId>activation</artifactId>
<version>1.1.1</version>
</dependency>Seven, custom jwt filter:
We need to customize a filter, which will get the token in the request header, parse the token and extract the userid from it. Use userid to get the corresponding LoginUser object in redis. Then encapsulate the Authentication object and store it in SecurityContextHolder.
package com.hu.publicsecurity.utils;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.JwtBuilder;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
import java.util.Date;
import java.util.UUID;
/**
* JWT工具类
*/
public class JwtUtil {
//有效期为
public static final Long JWT_TTL = 60 * 60 *1000L;// 60 * 60 *1000 一个小时
//设置秘钥明文
public static final String JWT_KEY = "huyannan";
public static String getUUID(){
String token = UUID.randomUUID().toString().replaceAll("-", "");
return token;
}
/**
* 生成jtw
* @param subject token中要存放的数据(json格式)
* @return
*/
public static String createJWT(String subject) {
JwtBuilder builder = getJwtBuilder(subject, null, getUUID());// 设置过期时间
return builder.compact();
}
/**
* 生成jtw
* @param subject token中要存放的数据(json格式)
* @param ttlMillis token超时时间
* @return
*/
public static String createJWT(String subject, Long ttlMillis) {
JwtBuilder builder = getJwtBuilder(subject, ttlMillis, getUUID());// 设置过期时间
return builder.compact();
}
private static JwtBuilder getJwtBuilder(String subject, Long ttlMillis, String uuid) {
SignatureAlgorithm signatureAlgorithm = SignatureAlgorithm.HS256;
SecretKey secretKey = generalKey();
long nowMillis = System.currentTimeMillis();
Date now = new Date(nowMillis);
if(ttlMillis==null){
ttlMillis=JwtUtil.JWT_TTL;
}
long expMillis = nowMillis + ttlMillis;
Date expDate = new Date(expMillis);
return Jwts.builder()
.setId(uuid) //唯一的ID
.setSubject(subject) // 主题 可以是JSON数据
.setIssuer("huyannan") // 签发者
.setIssuedAt(now) // 签发时间
.signWith(signatureAlgorithm, secretKey) //使用HS256对称加密算法签名, 第二个参数为秘钥
.setExpiration(expDate);
}
/**
* 创建token
* @param id
* @param subject
* @param ttlMillis
* @return
*/
public static String createJWT(String id, String subject, Long ttlMillis) {
JwtBuilder builder = getJwtBuilder(subject, ttlMillis, id);// 设置过期时间
return builder.compact();
}
/**
* 生成加密后的秘钥 secretKey
* @return
*/
public static SecretKey generalKey() {
byte[] encodedKey = Base64.getDecoder().decode(JwtUtil.JWT_KEY);
SecretKey key = new SecretKeySpec(encodedKey, 0, encodedKey.length, "AES");
return key;
}
/**
* 解析
*
* @param jwt
* @return
* @throws Exception
*/
public static Claims parseJWT(String jwt) throws Exception {
SecretKey secretKey = generalKey();
return Jwts.parser()
.setSigningKey(secretKey)
.parseClaimsJws(jwt)
.getBody();
}
}
Set the execution sequence of the jwt filter in the SecurityConfig configuration class.
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Bean
public PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Autowired
JwtAuthenticationTokenFilter jwtAuthenticationTokenFilter;
@Override
protected void configure(HttpSecurity http) throws Exception {
http
//关闭csrf
.csrf().disable()
//不通过Session获取SecurityContext
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS)
.and()
.authorizeRequests()
// 对于登录接口 允许匿名访问
.antMatchers("/user/login").anonymous()
// 除上面外的所有请求全部需要鉴权认证
.anyRequest().authenticated();
//把token校验过滤器添加到过滤器链中
http.addFilterBefore(jwtAuthenticationTokenFilter, UsernamePasswordAuthenticationFilter.class);
}
@Bean
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
}
Eight, custom logout
You only need to define a logout interface, then obtain the authentication information in SecurityContextHolder, and delete the corresponding data in redis. Add a logout interface to the Controller layer of login. There is a pit here. In the user authentication of Spring Security, the user logout function is customized. The interface access path is /logout. The blogger used swagger2 and postman to test and found that the logout was still not successful, and the 403 error was always reported. Later, I debugged the entire authentication process, and found that when the logout interface path is /logout, the system will automatically redirect to the logout interface that comes with security, so the logout interface function defined by myself cannot be implemented correctly. So you must change the logout interface path defined by yourself (cannot be /logout), I changed it to /user/logout.
Controller layer:
package com.hu.publicsecurity.controller;
import com.hu.publicsecurity.pojo.User;
import com.hu.publicsecurity.service.LoginService;
import com.hu.publicsecurity.utils.commonResult.R;
import io.swagger.annotations.Api;
import io.swagger.annotations.ApiOperation;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.web.bind.annotation.*;
@Api(tags = "登录和注销接口")
@RestController
@CrossOrigin
public class LoginController {
@Autowired
private LoginService loginService;
@ApiOperation("通过账号和密码进行登录获得token")
@PostMapping("/user/login")
public R login(@RequestBody User user) {
String jwt = loginService.login(user);
return R.ok().data("token",jwt);
}
//访问路径名字绝对不能设置成/logout
@ApiOperation("退出")
@GetMapping("/user/logout")
public R logout(){
Boolean aBoolean = loginService.logout();
if (aBoolean){
return R.ok().message("注销成功");
}
return R.error().message("注销失败");
}
}
Service implementation class:
package com.hu.publicsecurity.service.impl;
import com.hu.publicsecurity.handler.CustomException;
import com.hu.publicsecurity.pojo.User;
import com.hu.publicsecurity.pojo.vo.LoginUser;
import com.hu.publicsecurity.service.LoginService;
import com.hu.publicsecurity.utils.JwtUtil;
import com.hu.publicsecurity.utils.RedisCache;
import com.hu.publicsecurity.utils.commonResult.ResultCode;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.stereotype.Service;
import java.util.Objects;
@Service
public class LoginServiceImpl implements LoginService {
@Autowired
private AuthenticationManager authenticationManager;
@Autowired
private RedisCache redisCache;
@Override
public String login(User user) {
//把登陆时用户的账户和密码封装成一个authentication对象
UsernamePasswordAuthenticationToken authenticationToken = new UsernamePasswordAuthenticationToken(user.getUsername(), user.getPassword());
//AuthenticationManager authentication进行用户登录认证,会把
Authentication authenticate = authenticationManager.authenticate(authenticationToken);
//如果认证没通过,给出对应的提示
if (Objects.isNull(authenticate)) {
throw new CustomException(ResultCode.ERROR,"登录失败");
}
//如果认证通过,使用userid生成一个jwt jwt存入返回结果集返回,
// 1、先获得LoginUser对象,
LoginUser loginUser = (LoginUser) authenticate.getPrincipal();
// 2、再从LoginUser对象中取得userid
String userid = loginUser.getUser().getId().toString();
// 3、生成token(jwt)
//需要导入jaxb-api依赖,否者会报错
String jwt = JwtUtil.createJWT(userid);
/*System.out.println(jwt);*/
//把完整的用户信息存入redis中作为key
redisCache.setCacheObject("login:"+userid,loginUser);
return jwt;
}
@Override
public Boolean logout() {
//获取SecurityContextHolder中的用户id
UsernamePasswordAuthenticationToken authentication = (UsernamePasswordAuthenticationToken) SecurityContextHolder.getContext().getAuthentication();
LoginUser loginUser = (LoginUser) authentication.getPrincipal();
String userid = loginUser.getUser().getId().toString();
String redisKey = "login:" + userid;
//删除redis中的值
boolean aBoolean = redisCache.deleteObject(redisKey);
return aBoolean;
}
}
The fifth step can also customize failure and authorization processing
In Spring Security, if we have an exception during the authentication or authorization process, it will be caught by ExceptionTranslationFilter. In ExceptionTranslationFilter, it will be judged whether the authentication failed or the authorization failed. If an exception occurs during the authentication process, it will be encapsulated into AuthenticationException and then the method of the AuthenticationEntryPoint object will be called to handle the exception. If an exception occurs during the authorization process, it will be encapsulated into AccessDeniedException and then the method of the AccessDeniedHandler object will be called to handle the exception. So if we need to customize exception handling, we only need to customize AuthenticationEntryPoint and AccessDeniedHandler and configure them to SpringSecurity.
AuthenticationEntryPoint (authentication failure processing exception class):
package com.hu.publicsecurity.handler;
import com.alibaba.fastjson.JSON;
import com.hu.publicsecurity.utils.WebUtils;
import com.hu.publicsecurity.utils.commonResult.R;
import com.hu.publicsecurity.utils.commonResult.ResultCode;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.stereotype.Component;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
@Component
public class AuthenticationEntryPointImpl implements AuthenticationEntryPoint {
@Override
public void commence(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, AuthenticationException e) throws IOException, ServletException {
//处理异常
String json = JSON.toJSONString(R.error().code(ResultCode.ERROR).message("认证失败请重新登录"));
WebUtils.renderString(httpServletResponse, json);
}
}
AccessDeniedHandler (permission handling exception class):
package com.hu.publicsecurity.handler;
import com.alibaba.fastjson.JSON;
import com.hu.publicsecurity.utils.WebUtils;
import com.hu.publicsecurity.utils.commonResult.R;
import com.hu.publicsecurity.utils.commonResult.ResultCode;
import org.springframework.security.access.AccessDeniedException;
import org.springframework.security.web.access.AccessDeniedHandler;
import org.springframework.stereotype.Component;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
@Component
public class AccessDeniedHandlerImpl implements AccessDeniedHandler {
@Override
public void handle(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, AccessDeniedException e) throws IOException, ServletException {
//处理异常
String json = JSON.toJSONString(R.error().code(ResultCode.ERROR).message("权限不足"));
WebUtils.renderString(httpServletResponse, json);
}
}
After the class is implemented, it needs to be configured in the SecurityConfig configuration class. If you want to use swagger for subsequent interface testing, you also need to release swagger on the premise that you have configured the swagger environment. The blogger and the notes are ready.
package com.hu.publicsecurity.config;
import com.hu.publicsecurity.filter.JwtAuthenticationTokenFilter;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.security.web.access.AccessDeniedHandler;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private JwtAuthenticationTokenFilter jwtAuthenticationTokenFilter;
@Autowired
private AuthenticationEntryPoint authenticationEntryPoint;
@Autowired
private AccessDeniedHandler accessDeniedHandler;
//创建BCryptPasswordEncoder注入容器
@Bean
public PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
//放行
@Override
protected void configure(HttpSecurity http) throws Exception {
http
//关闭csrf
.csrf().disable()
//不通过Session获取SecurityContext
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS)
.and()
.authorizeRequests()
// 对于登录接口 允许匿名访问
.antMatchers("/user/login","/registerUser").anonymous()
//下面是放行swagger
.antMatchers("/swagger-ui.html").permitAll()
.antMatchers("/webjars/**").permitAll()
.antMatchers("/v2/**").permitAll()
.antMatchers("/swagger-resources/**").permitAll()
// 除上面外的所有请求全部需要鉴权认证
.anyRequest().authenticated();
//让自己定义的过滤器在security的过滤器之前执行
http.addFilterBefore(jwtAuthenticationTokenFilter, UsernamePasswordAuthenticationFilter.class);
//配置异常处理器
http.exceptionHandling()
//配置认证失败处理器
.authenticationEntryPoint(authenticationEntryPoint)
//配置授权失败处理器
.accessDeniedHandler(accessDeniedHandler);
}
//配置把AuthenticationManager注入容器。
@Bean
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
}
The sixth step, cross-domain issues
The same-origin policy requires the same source to communicate normally, that is, the protocol, domain name, and port number are all exactly the same. Separation of front-end and back-end projects, front-end projects and back-end projects are generally not of the same origin, so there will definitely be problems with cross-domain requests. So we have to deal with it so that the front end can make cross-domain requests.
Just need to create a CorsConfig configuration class:
package com.hu.publicsecurity.config;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.servlet.config.annotation.CorsRegistry;
import org.springframework.web.servlet.config.annotation.WebMvcConfigurer;
@Configuration
public class CorsConfig implements WebMvcConfigurer {
@Override
public void addCorsMappings(CorsRegistry registry) {
// 设置允许跨域的路径
registry.addMapping("/**")
// 设置允许跨域请求的域名
.allowedOriginPatterns("*")
// 是否允许cookie
.allowCredentials(true)
// 设置允许的请求方式
.allowedMethods("GET", "POST", "DELETE", "PUT")
// 设置允许的header属性
.allowedHeaders("*")
// 跨域允许时间
.maxAge(3600);
}
}
Then open SpringSecurity's cross-domain access and configure http.cors() in the SecurityConfig configuration class;
package com.hu.publicsecurity.config;
import com.hu.publicsecurity.filter.JwtAuthenticationTokenFilter;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.config.http.SessionCreationPolicy;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.security.web.access.AccessDeniedHandler;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private JwtAuthenticationTokenFilter jwtAuthenticationTokenFilter;
@Autowired
private AuthenticationEntryPoint authenticationEntryPoint;
@Autowired
private AccessDeniedHandler accessDeniedHandler;
//创建BCryptPasswordEncoder注入容器
@Bean
public PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
//放行
@Override
protected void configure(HttpSecurity http) throws Exception {
http
//关闭csrf
.csrf().disable()
//不通过Session获取SecurityContext
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS)
.and()
.authorizeRequests()
// 对于登录接口 允许匿名访问
.antMatchers("/user/login","/registerUser").anonymous()
//下面是放行swagger
.antMatchers("/swagger-ui.html").permitAll()
.antMatchers("/webjars/**").permitAll()
.antMatchers("/v2/**").permitAll()
.antMatchers("/swagger-resources/**").permitAll()
// 除上面外的所有请求全部需要鉴权认证
.anyRequest().authenticated();
//让自己定义的过滤器在security的过滤器之前执行
http.addFilterBefore(jwtAuthenticationTokenFilter, UsernamePasswordAuthenticationFilter.class);
//配置异常处理器
http.exceptionHandling()
//配置认证失败处理器
.authenticationEntryPoint(authenticationEntryPoint)
//配置授权失败处理器
.accessDeniedHandler(accessDeniedHandler);
//允许跨域
http.cors();
}
//配置把AuthenticationManager注入容器。
@Bean
@Override
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
}