1. Add dependence
1 <dependency> 2 <groupId>org.springframework.boot</groupId> 3 <artifactId>spring-boot-starter-web</artifactId> 4 </dependency> 5 <dependency> 6 <groupId>mysql</groupId> 7 <artifactId>mysql-connector-java</artifactId> 8 </dependency> 9 <dependency> 10 <groupId>org.springframework.boot</groupId> 11 <artifactId>spring-boot-starter-test</artifactId> 12 <scope>test</scope> 13 </dependency> 14 <dependency> 15 <groupId>org.apache.shiro</groupId> 16 <artifactId>shiro-spring</artifactId> 17 <version>1.4.0</version> 18 </dependency> 19
2. Shiro authentication and authorization process
2.1 Common API:
// if there is a corresponding role subject.hasRole ( "root" ) // obtain the subject name subject.getPrincipal () // check if there is a corresponding character, no return value judgment directly SecurityManager inside subject.checkRole ( "admin " ) // check if there is a corresponding role subject.hasRole (" ADMIN " ) // Log subject.logout ();
2.2 shiro certification process:
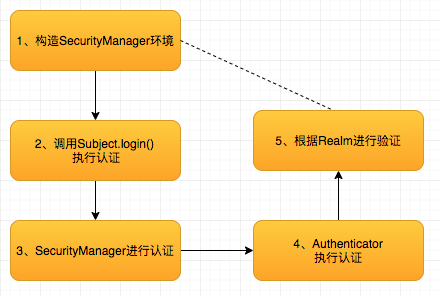
Test code:
. 1 Package net.xdclass.xdclassshiro; 2 . 3 Import org.apache.shiro.SecurityUtils; . 4 Import org.apache.shiro.authc.UsernamePasswordToken; . 5 Import org.apache.shiro.mgt.DefaultSecurityManager; . 6 Import org.apache.shiro .realm.SimpleAccountRealm; . 7 Import org.apache.shiro.subject.Subject; . 8 Import org.junit.Before; . 9 Import org.junit.Test; 10 . 11 / ** 12 is * Shiro authentication process: 13 * 1. configured SecurityManager environmental 14 * 2. call Subject.login () performs the authentication 15 * authentication 3.SecurityManager 16 * performs authentication 4.Authenticator 17 * The realm verify 18 is * / . 19 public class QuicksStratTest { 20 is 21 is / ** 22 is * accountRealm equivalent effect database 23 is * / 24 Private SimpleAccountRealm accountRealm = new new SimpleAccountRealm (); 25 26 is Private DefaultSecurityManager defaultSecurityManager = new new DefaultSecurityManager (); 27 28 @Before 29 public void the init () { 30 //Initialize the data source 31 is accountRealm.addAccount ( "LCH", "123" ); 32 accountRealm.addAccount ( "Jack", "345" ); 33 is // build environment 34 is defaultSecurityManager.setRealm (accountRealm); 35 36 } 37 [ 38 is @ the Test 39 public void testAuthentication () { 40 // set the current context 41 is SecurityUtils.setSecurityManager (defaultSecurityManager); 42 is // set the current subject (application applied User) 43 is the Subject Subject = SecurityUtils.getSubject (); 44 is // simulated user input 45 UsernamePasswordToken usernamePasswordToken = new new UsernamePasswordToken ( "LCH", "123" ); 46 is // actually calls the login method securityManager = this.securityManager.login Subject the Subject (the this, token); 47 subject.login ( usernamePasswordToken); 48 System.out.println ( "authentication result (if authorized):" + subject.isAuthenticated ()); // print to true 49 50 51 is } 52 is }
Above this login method which will be called the authenticator of the user authentication information usernamePasswordToken
2.3 shiro authorization process:
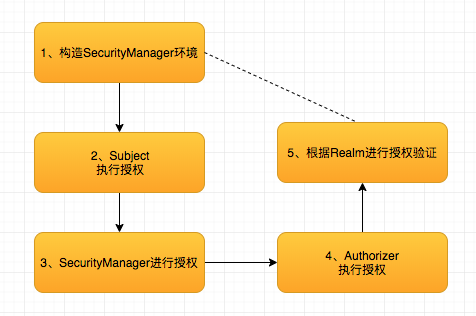
Test code:
. 1 Package net.xdclass.xdclassshiro; 2 . 3 Import org.apache.shiro.SecurityUtils; . 4 Import org.apache.shiro.authc.UsernamePasswordToken; . 5 Import org.apache.shiro.mgt.DefaultSecurityManager; . 6 Import org.apache.shiro .realm.SimpleAccountRealm; . 7 Import org.apache.shiro.subject.Subject; . 8 Import org.junit.Before; . 9 Import org.junit.Test; 10 . 11 / ** 12 is * Shiro authorization process and used the API: 13 is *. 1 tectonic environment SecurityManager 14 * 2.Subject perform authorization 15 * 3.SecurityManager authentication and authorization 16 * 4.Authenticator perform authorization 17 * 5. The authorization verification The realm 18 is * / . 19 public class QuicksStratTest2 { 20 is 21 is / ** 22 is * accountRealm equivalent effect database 23 is * / 24 Private accountRealm = SimpleAccountRealm new new SimpleAccountRealm (); 25 26 is Private DefaultSecurityManager defaultSecurityManager = new new DefaultSecurityManager (); 27 28 @Before 29 public void the init () { 30 // initialize the data source, the user into joining the role 31 is accountRealm.addAccount ( "LCH", "123", "the root", "ADMIN" ); 32 accountRealm.addAccount ( "Jack", "345", "User" ) ; 33 // build environment 34 is defaultSecurityManager.setRealm (accountRealm); 35 } 36 37 [ @Test 38 is public void testAuthentication () { 39 // set the current context 40 SecurityUtils.setSecurityManager (defaultSecurityManager); 41 is // set the current subject (application application the User) 42 is the Subject Subject =SecurityUtils.getSubject (); 43 is // simulate user input 44 is UsernamePasswordToken usernamePasswordToken = new new UsernamePasswordToken ( "LCH", "123" ); 45 // actually calls the login method securityManager Subject subject = this.securityManager.login (this, token ); 46 is subject.login (usernamePasswordToken); 47 48 System.out.println ( "authentication result (if authorized):" + subject.isAuthenticated ()); // results: to true 49 // final call is org. method apache.shiro.authz.ModularRealmAuthorizer.hasRole 50 System.out.println ( "if there is a corresponding character:" + subject.hasRole ( "root" ));// result: to true 51 // get the login account 52 System.out.println ( "getPrincipal ():" + subject.getPrincipal ()); // getPrincipal (): LCH 53 subject.logout (); 54 after System.out.println ( "logout authentication result: "+ subject.isAuthenticated ()); // the logout authentication result: to false 55 56 is 57 is } 58 }
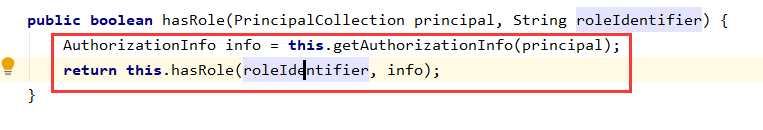
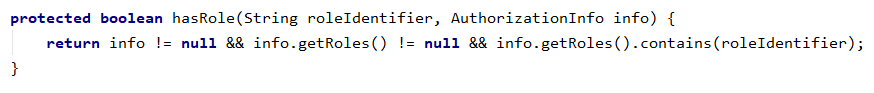
subject.hasRole () method, is actually called SecurityManager method of hasRole permissions check:
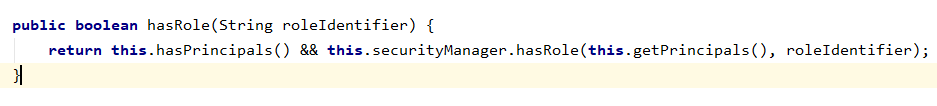
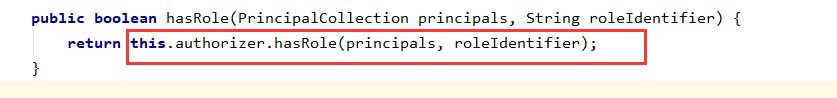
The hasRole SecurityManager method is invoked authorizer of hasRole way to check,
It has achieved three categories:
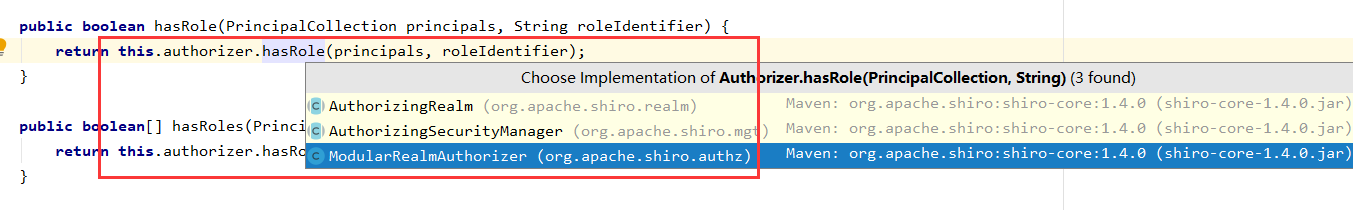
SimpleAccountRealm test code used is inherited from AuthorizingRealm, so here we enter the first class that implements AuthorizingRealm which found its authorization logic is as follows: