Software Architecture Design---Software Architecture Evaluation
Information system evaluation elements include: function, cost, reliability, availability, storage capacity, efficiency, response time, etc. For different applications, the preferred evaluation indicators are different. For example, the banking system should focus on the availability and reliability of the system.
Soft Armor Architecture Design---Software Architecture Evaluation
- The operation log records the activity of the job, the operation process and the problems during the operation, and does not measure the performance of the computer system;
- The job accounting system records the running time of each job, the amount of hardware and software resources used during the running period, and does not measure the performance of the computer system;
- Both hardware monitoring and software monitoring can measure the performance of a computer system, but for a computer system with a high load, software monitoring has a large overhead and will seriously reduce system performance.

Information Monitoring---Intrusion Detection
The Common Intrusion Detection Framework (CIDF) proposed by the US Defense Advanced Research Projects Agency (DARPA) consists of four modules.

- Event generators (Event generators E-Box): Responsible for data collection, converting the collected raw data into events, and providing event-related information to other modules of the system. The information used by intrusion detection generally comes from four aspects:
-
- System and network log files
- Unexpected changes in directories and files
- Unexpected payments during program execution
- Intrusion information in physical form, etc.
- Intrusion detection needs to collect information at several key points in the network (different network segments and different hosts), and compare the information of multiple collection points to determine whether there is any suspicious or intrusive behavior;
- Event Analyzers (Event Analyzers A-boxes): Receive event information and analyze it to determine whether it is an intrusion or abnormal phenomenon. There are three analysis methods:
-
- Pattern Matching: Compare collected information with known network intrusion databases to detect security policy violations
- Statistical analysis: First, establish a normal use profile (Profile) for system objects (such as users, files, directories, and devices), and these feature values will be used to compare with behaviors that occur in the network. When the observed value is outside the normal value range, it is considered that intrusion is likely to occur.
- Data integrity analysis: It mainly focuses on whether the attributes of files or system objects have been modified. This method is often used for post-event audit analysis.
- Event Databases (Event Databases D-boxes): the place where various intermediate results and final data about events are stored, which can be an object-oriented database or a text file;
- Response units (R-box): make various reactions according to the alarm information, the strong reaction is to disconnect, change the file attribute, etc., and the simple reaction is to issue a system prompt to attract the attention of the operator.
Therefore, the composition of the intrusion detection system does not include an early warning unit.

Information Security---Computer Viruses and Trojans:
There are many ways to classify computer viruses. According to the most common method of distinction, that is, according to the way of infection and the nuclear technology used, computer viruses can be divided into file-type viruses, boot-type computer viruses, macro viruses and directory-type computer viruses. ;
- File-type computer viruses that infect executable files (including exe and com files)
- Macro viruses infect text documents, databases, spreadsheets, etc. files created with certain programs
- Directory computer viruses can modify the address of all files stored on the hard disk, if the user uses certain tools (such as scandisk or chkdsk)
- Detecting infected disks will find a large number of file link address errors, which are caused by computer viruses

Information Security---Computer Viruses and Trojans
CIH virus is a vicious virus capable of damaging computer system hardware.
Trojan horse virus is a malicious program that hides secretly and can be controlled through a remote network. The controller can control all actions and resources of the computer that is secretly embedded in the Trojan horse. It is a tool for malicious attackers to steal information.
The "Romeo and Juliet" virus that appeared in 2000 is a very typical worm virus, which has rewritten the history of viruses. The basic characteristics of this virus are the same as those of email viruses. In the text of the e-mail, once the user opens Outlook to send and receive letters for reading, the virus will immediately break out, and the copied new virus will be sent to others by e-mail, which cannot be avoided by computer users.
Melissa virus is a macro virus. When it occurs, it will close the macro virus protection of Word, open the conversion confirmation, and prompt for template saving; make macros and security commands unavailable, and set the security level to the lowest.
Information Security --- Symmetric Encryption and Asymmetric Encryption
The figure shows a digital signature scheme implemented using a public key encryption algorithm. The message P to be sent by the sender A to the receiver B is formed after being signed by A's private key and encrypted by B's public key;

In the Active Directory of Windows Server2003, users are divided into global groups (Global Groups), domain local groups (Domain Local Groups) and universal groups (Universal Groups). Among them, members of the global group come from user accounts and global groups in the same domain, and can access any resources in the domain; members of the domain local group come from user accounts in any domain in the forest, the global combined universal group and the domain local group in the local domain, only Can access resources in the local domain; universal group members come from user accounts in any domain in the forest, and other commuter groups are globally combined, and access rights in multiple domains can be granted;

Information Security---Others
Business flow analysis is a kind of information security threat. It conducts long-term monitoring of the system and uses statistical analysis methods such as communication frequency, communication information flow direction, and changes in the total amount of communication to conduct research and find valuable information. law.
Information Security---Information Digest and Digital Signature:
The basic process of data encryption is to process the original plaintext file or data according to a certain algorithm to make it an unreadable piece of code, usually called "ciphertext", so that it can only be read after entering the corresponding secret key. Display this content, and achieve the purpose of protecting data from illegal theft and reading through such means;
Common encryption algorithms are: DES (Data Encryption Standard), 3DES (Triple DES), RC2 and RC4
IDEA(International Data Encryption Algorithm)、RSA
The message digest algorithm is mainly used in the field of digital signatures as a digest algorithm for plaintext. Famous digest algorithms include RSA's MD5 algorithm and SHA-1 algorithm
Information Security---Network Security Protocol
PGP is an RSA-based email encryption email, which can be used to keep the email confidential to prevent unauthorized persons from reading it, and it can also add a digital signature to the email, so that the recipient can be sure of the sender of the email. The basic principle of PGP is to first encrypt the transmitted information with a symmetric key, and then encrypt the symmetric encryption key with the receiver's public key to form a digital envelope, and hand over the key to an impartial third party for safekeeping; This digital envelope is delivered to the recipient. The receiver must first unpack the digital envelope with its own private key to obtain the symmetric decryption key, and then use the symmetric decryption key to decrypt the real information, taking into account convenience and efficiency.
PKI is a secret key management platform that follows established standards. It can provide services such as encryption and digital signatures for all network applications, as well as the necessary secret key and certificate management systems. The PKI mechanism solves the problem of relying on secret channels when distributing secret keys.
SET secure electronic transaction protocol is mainly used in the B2C mode to ensure the security of payment information. The SET protocol itself is relatively complex, with strict design and high security. It can guarantee the confidentiality, authenticity, integrity and non-repudiation of information transmission. The SET protocol is a typical implementation under the PKI framework, and it is also being continuously upgraded and improved. For example, SET2.0 will support debit card electronic transactions
Kerberos is a network identity authentication protocol based on a trusted third party. It provides a method for identity authentication in an open network. The authentication entity can be a user or a user service. This kind of authentication does not depend on the operating system of the host computer or the IP address of the computer, does not need to ensure the physical security of all computers on the network, and assumes that data packets can be randomly stolen and tampered with during transmission.
Information Security---Network Security Protocol
- Internet Protocol Security (IPSec) is an open standard framework for ensuring confidential and secure communications over Internet Protocol (IP) networks through the use of encrypted security services.
- IPsec (Internet Protocol Security) is the long-term direction of secure networks. It provides proactive protection against private network and Internet attacks through end-to-end security. In communication, only the sender and receiver are the only ones who must understand IPSec to protect computers
- The IPSec protocol is notarized at the third layer of the OSI model, making it suitable for protecting TCP or UDP-based protocols when used alone (such as the secure socket layer SSL cannot protect the communication flow of the UDP layer)
- Similar protocols related to IP security are AH and ESP
-
- The AH protocol is used to provide data integrity and authentication to IP communications, and can provide anti-replay services
- The IP layer encryption provided by ESP guarantees and authenticates the data source to deal with the monitoring on the network. Because AH can protect the communication from tampering, but it does not transform the number, the data is still clear to hackers. In order to effectively protect the security of data transmission, another header ESP in IPv6 further provides data confidentiality and prevents tampering;
- IPSec supports two encapsulation modes: tunnel mode and transport mode
-
- Tunnel (tunnel) mode: The entire IP data packet of the user is used to calculate the AH or ESP header, and the user data encrypted by AH or ESP and ESP is encapsulated in a new IP data packet. Usually, tunnel mode is applied to the communication between two security gateways.
- Transport mode: Only the transport layer data is used to calculate the AH or ESP header, and the AH or ESP header and ESP encrypted user data are placed behind the original IP header. Usually, the transport mode is applied to the communication between two hosts, or the communication between a host and a security gateway. A common format is defined.
Project Management --- Scope Management
Project management is the core means to ensure the success of the project, and plays an important role in the project implementation process. Among them, the project development plan is an important element of project management and the basis of project implementation;
Scope management is to determine which work should be done in the project and which work should not be included in the project;
The schedule management adopts scientific methods to determine the project objectives, and realize the construction period objectives on the basis of the coordination of quality and cost objectives;
Project Management---Time Management:
Project schedule analysis Analysis is the process of organizing related activities in chronological order in order to complete the specific task objectives, under the conditions of obeying the priority relationship, time constraints and resource constraints. Among the various project schedule analysis methods:
- The critical path method is a basic project schedule analysis method: the Gantt chart applies the results of the critical path analysis to the project schedule;
- PERT network analysis is an extension of the critical path method, which introduces changes in the duration of activities during project implementation;
- Prioritized scheduling allows interdependent activities to be partially parallelized;
- The schedule heuristic method is mainly used in the analysis of more complex project plans;

Project Management---Software Quality Management
Component high-quality software is an important goal of project development, and software quality emphasizes three aspects:
- Software requirements are the basis for testing software quality;
- Development standards define a set of guidelines to guide the way software is developed;
- Implicit requirements indirectly define user expectations for certain features
Project Management---Time Management

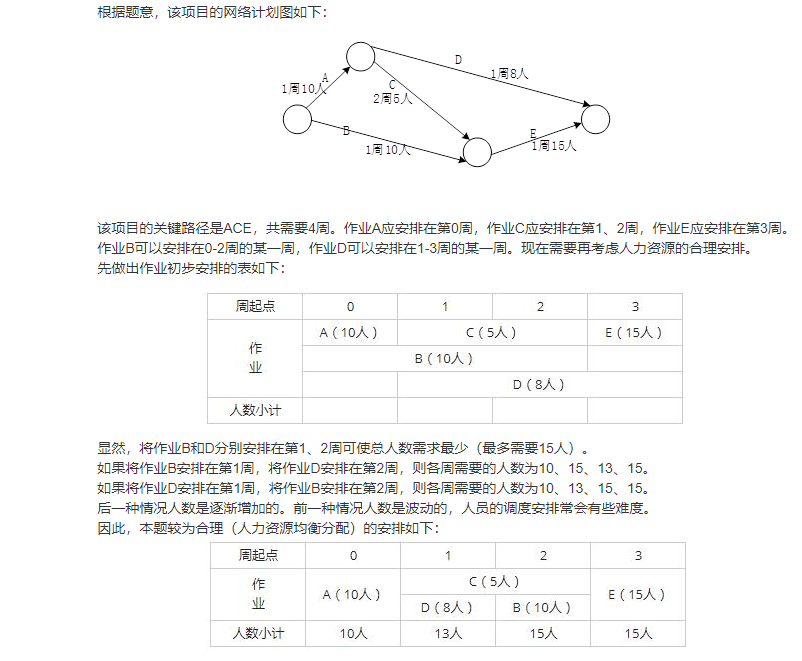
Computer Composition and Architecture---CISC and RISC
RISC and CISC are two common instruction systems:
The characteristics of RISC are: the number of instructions is small, the frequency of use is close, the fixed-length format, most of them are single-cycle instructions, and the operation registers, only Load and Store operate the memory; there are few addressing methods; and general-purpose registers are added; Main; suitable for pipeline;
The characteristics of CISC are: large number of instructions, large difference in frequency of use, variable length format; many addressing methods; microprogram control technology (microcode) is often used and the development cycle is long;