This article is my free column "Introduction to Common Tools for Network Attack and Defense".part twoArticles
Each article comes with a full demovideo, welcome to watch!
磨刀不误砍柴工!
在介绍攻防技术时,基础工具的使用很容易忽略,但是对不熟悉的同学来说,这将极大影响学习。 所以本专栏专门介绍网络攻防或CTF竞赛中必备的工具及其使用方式。方便对该领域感兴趣的同学更快入门。为后续学习扫清障碍。
Article directory
This article is accompanied by a demonstration video
Video portal, welcome to like and pay attention
Web security's most intimate comrade-in-arms Burp Suite2--target module experience
1. target module
1.1 Module function introduction
This module contains three sub-modules, namely site map (site map), scope (scope), issue definitions (field, professional vocabulary description)
1.1.1 site map (site map)
This module lists the main content of the website being crawled, which can intuitively reflect the overall overview.
- Domain Name List: Completely lists the paths of different domain names.
- List of data packets under each domain name: classify data packets into their respective domain names for easy viewing and analysis.
- Data packet details: Display the detailed information of request packets and response packets.
- List of suspected problems found by bp tool automatic scanning
- problem details
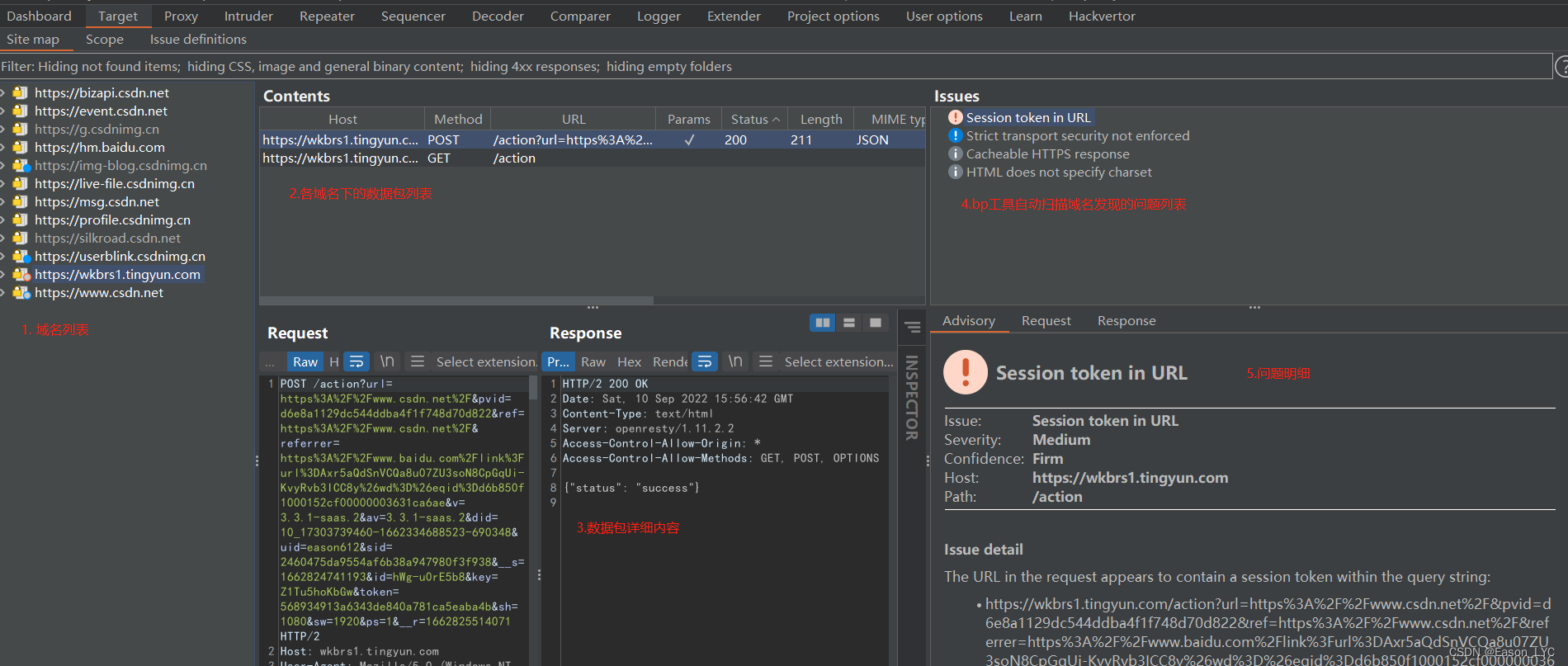
1.1.2 Scope
Set the domain name range for the tool to capture and analyze packets.
Currently, the scope is not set, so the tool intercepts all data packets of the browser, and lists and analyzes all domain names. If one or several domain names are set in the scope, bp will only intercept and analyze the data packets of these domain names.
Operation method, click the domain name mouse mail --> add to scope
1.1.3 issue definitions (fields, professional vocabulary description)
This part summarizes the definitions of a large number of security professional terms. Students who are good at English can actually read the content here. It is very professional and will benefit a lot.
2. Example of using the target module (take the csdn homepage as an example)
The configuration of the software is described above. In this article, let’s take a look at the content of the captured traffic packets and what’s interesting.
特此声明:仅为浏览查看,不做具有攻击性的测试,如有争议,可联系沟通删除文章!
Taking the homepage of csdn as an example, open the website, use the target label of BP software, and find that a large number of domain names related to csdn are automatically obtained.
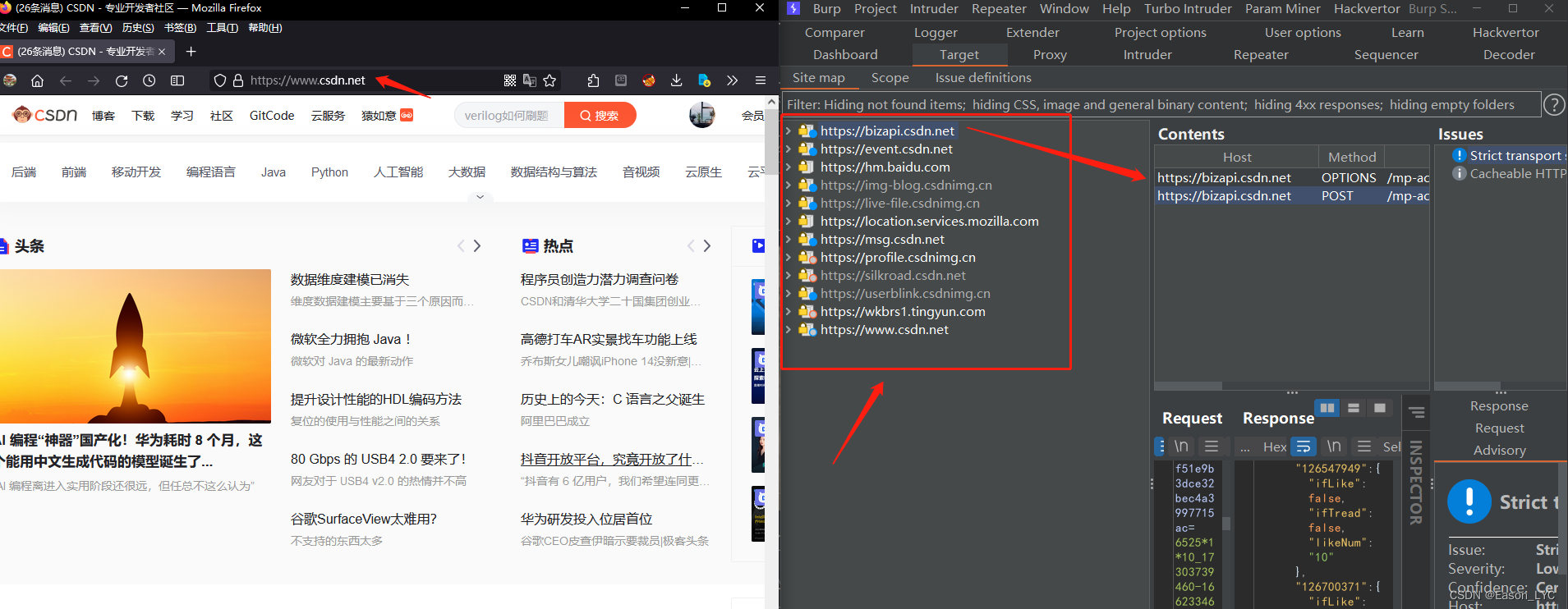
As shown in the figure above, roughly speaking, the 10 domain names related to CSDN are listed as follows:
- https://bizapi.csdn.net
- https://event.csdn.net
- https://img-blog.csdnimg.cn
- https://live-file.csdnimg.cn
- https://msg.csdn.net
- https://profile.csdnimg.cn/
- https://silkroad.csdn.net/
- https://userblink.csdnimg.cn/
- https://wkbrs1.tingyun.com/
- https://www.csdn.net/
Then let's guess what the role of several subdomains is.
2.1 bizapi subdomain analysis
See that there are two data packets under this domain name, one option packet and one post data packet,
2.1.1 Function of option package
I suddenly remembered that in cross-domain access (CORS), it is often to send an option package before the interaction, and the two parties first negotiate which methods can be used to access, verify some preset restrictions, and so on. Look at the content of this package
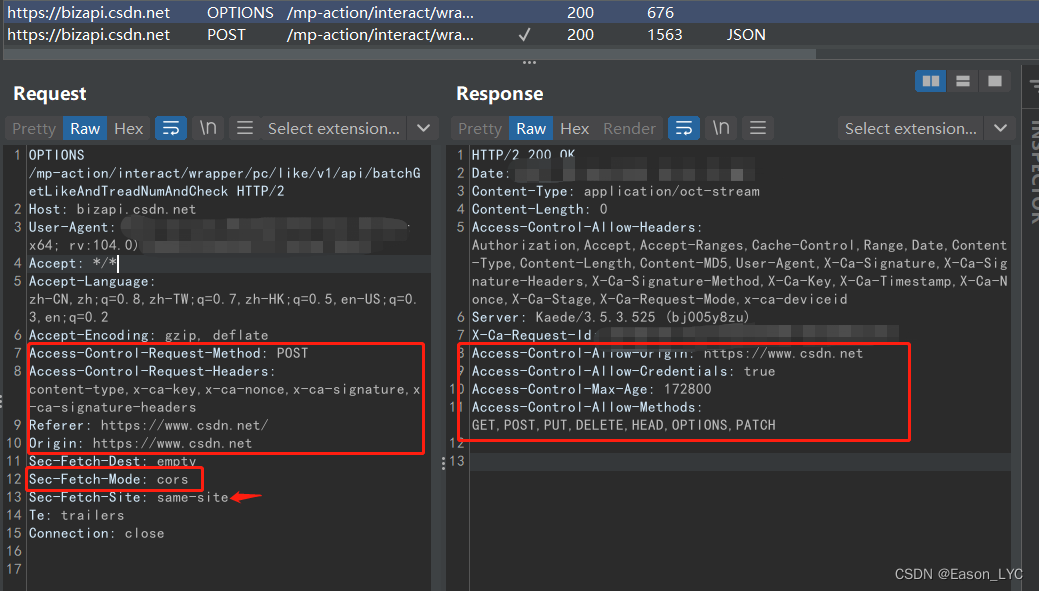
. It’s true. The request package on the left says: I use post to access, and there are many header information such as certificates or signatures in headers for verification. I come from csdn.net, and the mode is CORS same-origin policy.
The response packet replied: I saw that your certificate is True, and it is also satisfied from csdn.net. You can use the following methods to access. After passing, there will be a post package in the follow-up. The original data packet is as follows
Request packet:
OPTIONS /mp-action/interact/wrapper/pc/like/v1/api/batchGetLikeAndTreadNumAndCheck HTTP/2
Host: bizapi.csdn.net
User-Agent:你猜
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Access-Control-Request-Method: POST
Access-Control-Request-Headers: content-type,x-ca-key,x-ca-nonce,x-ca-signature,x-ca-signature-headers
Referer: https://www.csdn.net/
Origin: https://www.csdn.net
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-site
Te: trailers
Response packet:
HTTP/2 200 OK
Date: 你猜
Content-Type: application/oct-stream
Content-Length: 0
Access-Control-Allow-Headers: Authorization,Accept,Accept-Ranges,Cache-Control,Range,Date,Content-Type,Content-Length,Content-MD5,User-Agent,X-Ca-Signature,X-Ca-Signature-Headers,X-Ca-Signature-Method,X-Ca-Key,X-Ca-Timestamp,X-Ca-Nonce,X-Ca-Stage,X-Ca-Request-Mode,x-ca-deviceid
Server: Kaede/3.5.3.525 (bj005nf7p)
X-Ca-Request-Id: 你猜
Access-Control-Allow-Origin: https://www.csdn.net
Access-Control-Allow-Credentials: true
Access-Control-Max-Age: 172800
Access-Control-Allow-Methods: GET,POST,PUT,DELETE,HEAD,OPTIONS,PATCH
2.1.2 The role of the post package
First upload the screenshot of the data package
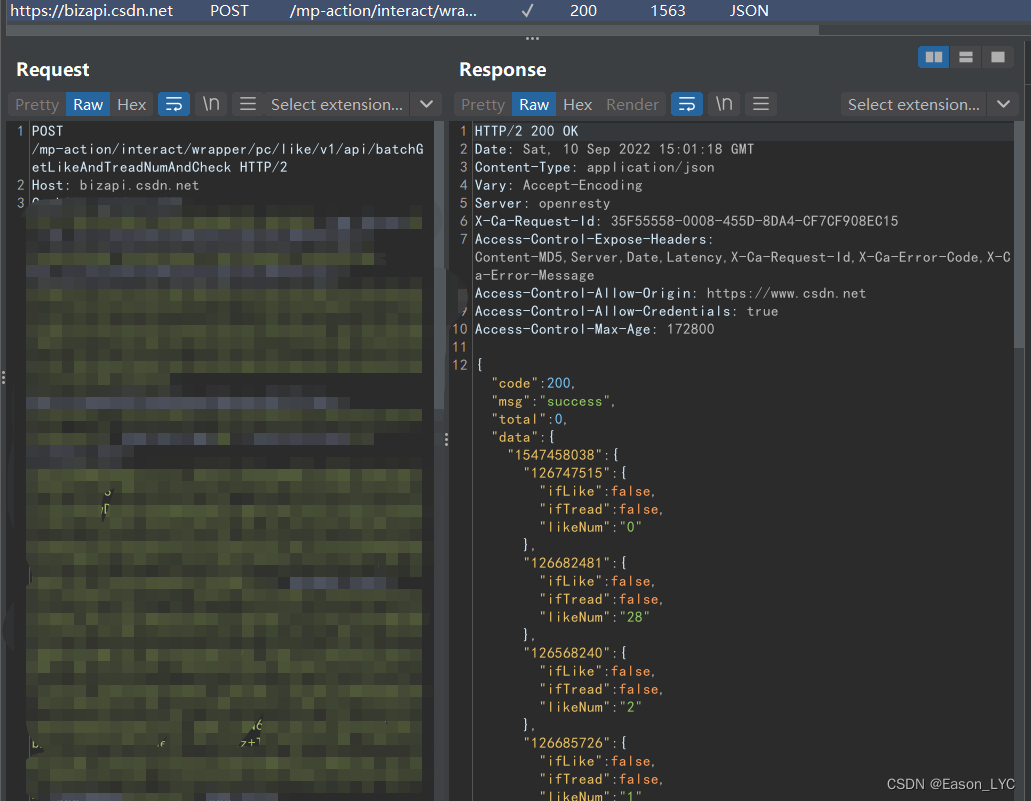
to request the content of the package, I made a mosaic. The main content is to send the personal information and various authentication information of the logged-in user to prove that I am me.
Response packet content: The format of the returned data is json. First let me know that I have passed the verification and returned the data, which is in the json format content below.
What is the content, let's try to guess:
a string of numbers, ifLike, ifThread, likeNum (number of likes?). Seeing this, I got an idea. Could it be the number of likes of the article and other data. Then let's verify it. Compare the contents of the home page.

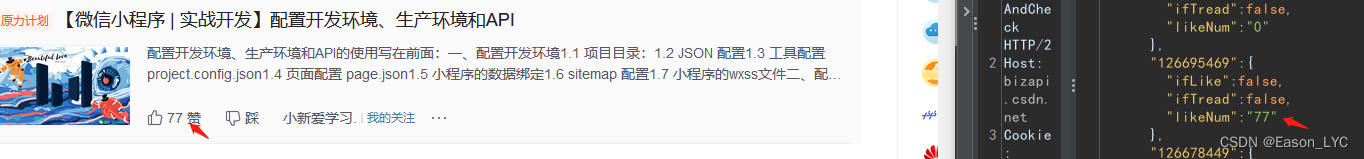 The data can be matched as expected, so the field content is
The data can be matched as expected, so the field content is
- A string of numbers: article id, after clicking on the article, this string of numbers will be automatically added to the url
- ifLike: whether I liked
- ifThread: whether I step on
- likeNum: total number of likes
To sum up: the role of this bizapi domain name is to be responsible for the article recommendation information on the homepage.
2.2 The function of msg subdomain name
Look directly at the corresponding post package
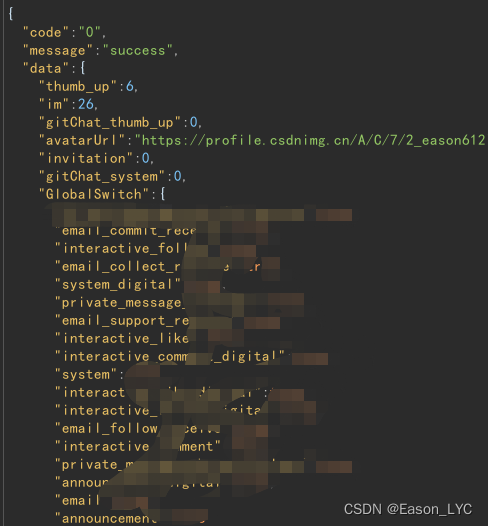
and see the information, which proves that these should be various states and data of the person, but how do the specific fields correspond.
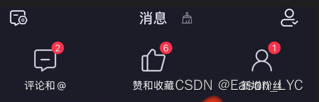
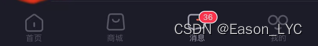
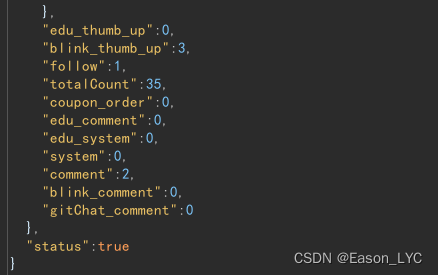
Comparing the two sets of data, you can get the specific field information
- comment: comment and @ unread 2
- thumb_up: likes and favorites unread 6
- follow: New followers unread 1
- im: number of unread messages unread 26
There are a total of 35 messages, but my mobile phone is slow to take screenshots, and there is an extra im. Therefore, 36 items are displayed at the bottom of the screenshot.
To sum up: the function of this msg sub-domain name is to return the information quantity statistics of the logged-in users.
What is the specific content? I guess I click in, and there may be surprises on the next page. As far as the analysis point is concerned, the tool introduction is the main line.
3. Summary
Through the above analysis and interpretation of data packets using the target module of BP software, readers should be able to feel the importance of using packet capture tools for analysis in the field of web security testing, which can be said to be the basis of everything. The more powerful the tool, the better your chances of finding vulnerabilities.
The above is the experience of the target module of Burp Suite. Subsequent articles will introduce the use of other modules. Welcome to like and pay attention!