Definition of Mpls vpn
BGP/MPLS IP VPN networks are generally built by operators, and VPN users purchase VPN services to realize routing transmission and data intercommunication between user networks.
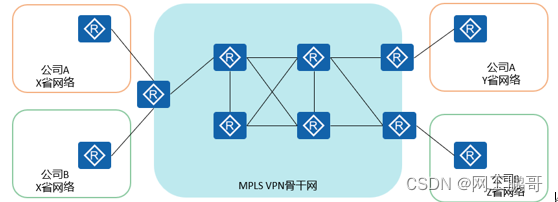
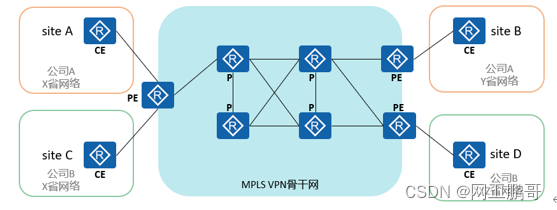
The network architecture of Mpls vpn:
The MPLS VPN network architecture consists of three parts: CE (Customer Edge), PE (Provider Edge) and P (Provider), where PE and P are operator equipment, and CE is MPLS VPN user equipment.
A site is an MPLS VPN user, consisting of CE and other user equipment.
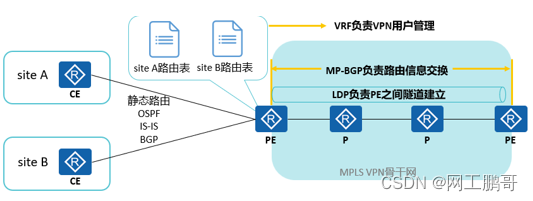
The technical architecture of Mpls vpn:
MPLS VPN is not a single VPN technology, but a comprehensive solution combining multiple technologies, mainly including the following technologies:
MP-BGP: responsible for transferring routing information within a site between PEs.
LDP: Responsible for establishing tunnels between PEs.
VRF: responsible for PE VPN user management.
Static routing, IGP, BGP: responsible for exchanging routing information between PEs and CEs.
Routing delivery of Mpls vpn:
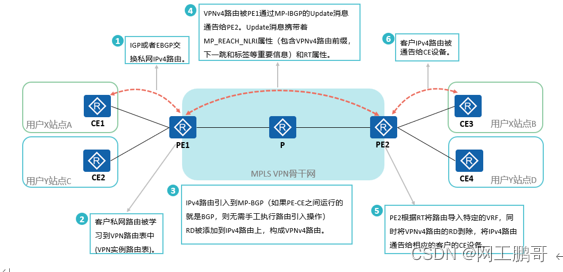
1. Routing information exchange between CE and PE (using ordinary ipv4, ipv6 IGP, BGP, static routing)
The interface connecting the PE device to the CE needs to be assigned to a VPN instance to distinguish user routes.
2. Route transmission from ingress PE to egress PE (using MP-BGP to transmit vpnv4 route)
A VPNv4 address has a total of 12 bytes, including an 8-byte Route Distinguisher (RD) and a 4-byte IPv4 address prefix. In human terms: It is the private network route of CE plus a mark (RD) route transmitted in MP-BGP.
RD value: When the PE receives the same routes in different VRFs sent by the remote PE , it needs to be distinguished by the RD value.
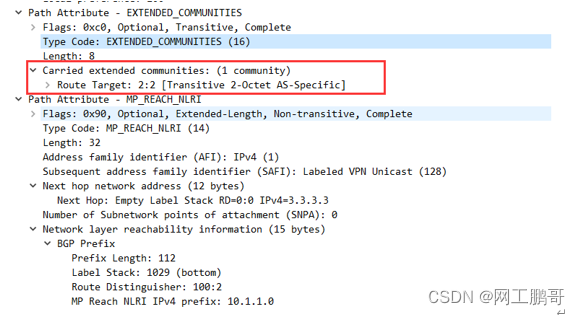
RT value: Indicates the preference of a 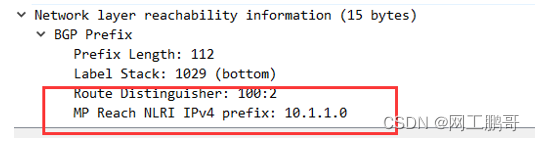 vrf, determines whether the router accepts this route, and which instance's routing table the corresponding route is placed in. The RT value is an extended community attribute. ( When sending VPNV4 routes, the outgoing direction RT will be carried in the extended community attribute )
vrf, determines whether the router accepts this route, and which instance's routing table the corresponding route is placed in. The RT value is an extended community attribute. ( When sending VPNV4 routes, the outgoing direction RT will be carried in the extended community attribute )
Data forwarding of MPLS VPN:
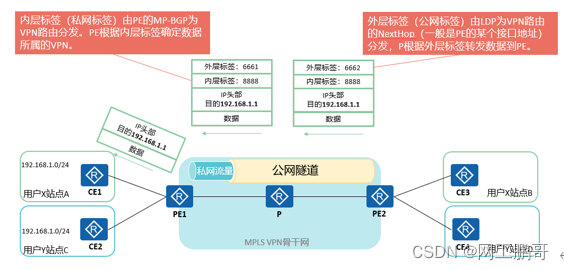
Mpls vpn can advertise the internal route of the site to the corresponding site through MP-bgp (deliver the route of the local CE to the peer CE). This is only the routing interaction completed by the control plane. Network tunnel to realize data communication.
The operator's mpls network P equipment does not have a private network route within the site (CE), so it is impossible to use IP for forwarding, so it is necessary to use the mpls label to forward private network traffic.
Two types of labels are required for data forwarding
The outer label (public network label) is distributed by LDP to NextHop (generally an interface address of PE) for VPN routing, and P forwards data to PE according to the outer label.
The inner label (private network label) is distributed by MP-BGP of the PE for VPN routes. The PE determines the VPN to which the data belongs according to the inner label.
Problems when data forwarding:

Solving problems with tags:
The process of Mpls vpn routing interaction:
Special scenarios and solutions for Mpls vpn:
AS number replacement:
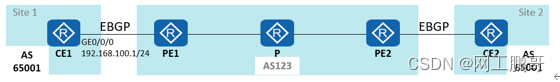
If CE1 sends a private network route to PE1 through EBGP, and then sends it to CE2 through PE2, CE2 will discard this route due to the duplicate AS number, resulting in the incommunication between Site 1 and Site 2 belonging to the same VPN.
You can execute the peer substitute-as command on the PE to enable the AS number substitution function, that is, the PE replaces the AS number of the VPN site where the CE is located in the private network route received by the PE with the local AS number, so that the peer CE will not duplicate the AS number. And discard the routing.
[PE1] bgp 123
[PE1-bgp] ipv4-family vpn-instance vpn1
[PE1-bgp-vpn1] peer 192.168.100.1 substitute-as
SOO:
In CE multi-homing scenarios, if the AS number replacement function of BGP is enabled, routing loops may occur, and the SoO (Site of Origin) feature is required to avoid loops.
CE1 and CE3 are in the same VPN site 1, CE2 is in Site 2, and the AS numbers of Site 1 and Site 2 are both 65001. The EBGP routing protocol runs between the PEs and CEs. To ensure that the routes between Site 1 and Site 2 can be learned normally, the AS number replacement function needs to be configured on PE1 and PE2.
CE1 passes the intra-site route to PE1, and PE1 passes the route to CE3. Because AS number replacement is configured, CE3 will receive the route, which may cause a routing loop.
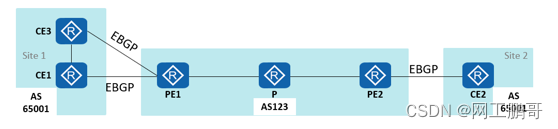
After configuring SoO for BGP neighbors:
When receiving the neighbor's BGP route, it will carry the SoO attribute in the path attribute and advertise it to other BGP neighbors.
When advertising a BGP route to the neighbor, it will check whether the SoO attribute in the route is the same as the configured SoO value, and if they are the same, it will not advertise to avoid loops.
[PE1] bgp 123
[PE1-bgp] ipv4-family vpn-instance vpn1
[PE1-bgp-vpn1] peer 192.168.100.1 soo 200:1
[PE1-bgp-vpn1] peer 192.168.200.1 soo 200:1
Sham link:
Application Scenario
When ospf is running between CE and PE, and there is a backdoor link;
Routes passing through the MPLSVPN super bone are used as inter-area routes, and backdoor links are used as intra-area routes, which will cause VPN traffic to take the backdoor link as the main path.
The peer CE sends LSAI/2/3 to the PE, and at this time sends it to the peer PE—the CE is LSA3
The opposite end CE sends PE is LSA5, at this time to the opposite end PE - CE is LSA5
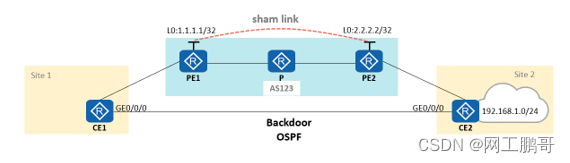
Create an interface for establishing a sham link on the PE
[PE1]interface LoopBack0
[PE1-LoopBack0] ip binding vpn-instance VPNA
[PE1-LoopBack0]ip address 1.1.1.1 32
#Publish in the BGP VPN address family
[PE1-bgp-VPNA]network 1.1.1.1 32
Configure the sham link on the PE node
[PE1-ospf-1]area 0
[PE1-ospf-1-area-0.0.0.0]sham-link 1.1.1.1 2.2.2.2
Adjust the cost value to ensure that the cost of the backdoor link is greater than the cost of the sham link.
[CE1-GigabitEthernet0/0/0]ospf cost 1000
Mpls vpn anti-ring:
DN bit anti-ring:
To prevent Type 3 LSA loops, the OSPF multi-instance process uses an unused bit in the LSA Options field as a flag, called the DN bit. Using the DN bits can prevent Type3 LSA loops.
The OSPF instance process of the PE router ignores Type3 LSAs with the DN bit set when performing SPF calculations.
If the CE device is also configured with a vpn instance, by default, due to the DN loop prevention, the route sent by the PE device will be received and not counted. As a result, the CE cannot receive the route of the peer CE.
The following commands need to be executed on the CE to receive the route sent by the PE:
method one:
Use the dn-bit-set disable summary/ase/nssa command to disable setting the DN bit of an OSPF LSA.
Specifies not to set the DN bit of Summary LSA/AS-external LSA/NSSA LSA
Method 2:
Use the vpn-instance-capability simple command to disable routing loop detection and perform route calculation directly.
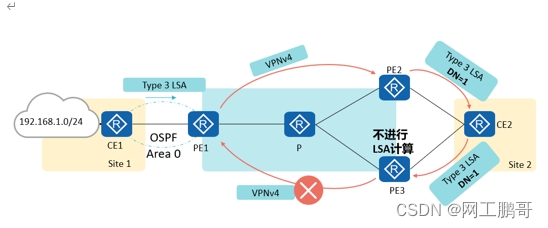
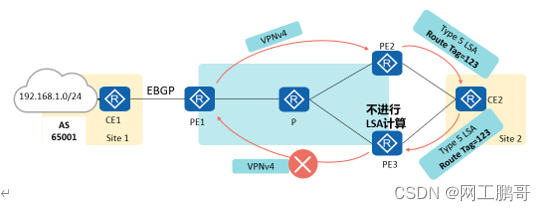
Type5/7 routing loop prevention: VPN Route Tag:
You can use VPN Route Tag (VPN routing tag) to prevent this type 5 or 7 routing loop.
When PEs generate Type 5/7 LSAs based on the received BGP private network routes, they carry VPN route labels. When the PE finds that the VPN routing label of the LSA is the same as that configured locally, it ignores this LSA, so the above loop can be avoided.