0x00 api interface introduction
Usually in the communication of the website, many API interfaces are called to facilitate the management and invocation of more information, but when using certain APIs, if the developer does not make access policy restrictions or other reinforcements to the API interface, other When users discover APIs, they may obtain sensitive information leakage, or other security issues such as SQL injection. This article introduces the utilization and discovery of three APIs
0x01 WebService class-Wsdl interface test
In the development of WebService, especially when there is an interface with a third party, the SOAP protocol is used, and then there will be a WSDL file (or URL). At this time, related measurements, sensitive information, etc. can be performed on the wsdl file.
wsdl fingerprint detection: "?wsdl"
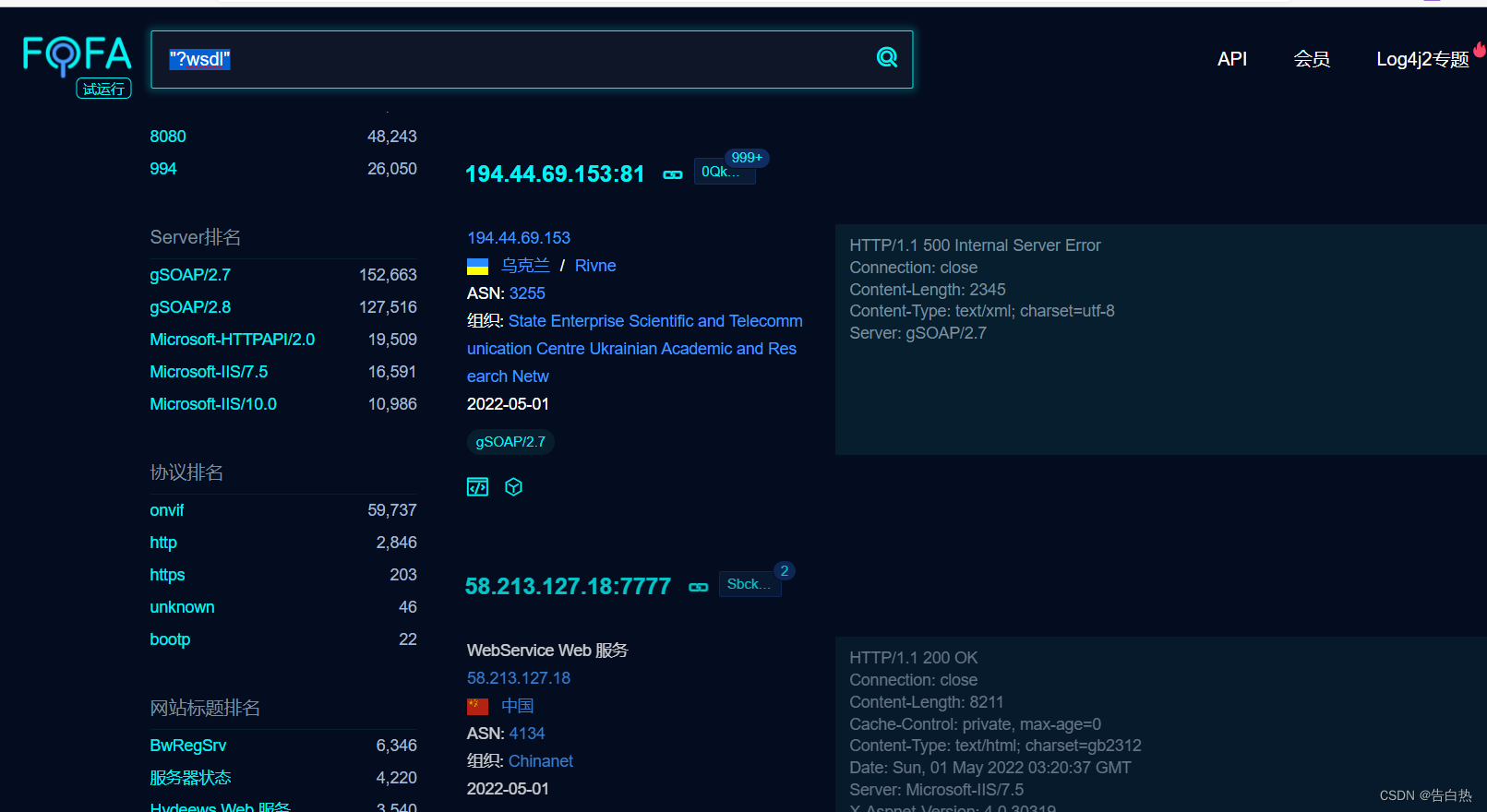
The security issues of this API interface have the following types:
Web 应用安全漏洞:
sql注入
xss攻击
命令执行
越权
LDAP注入
缓冲区溢出
逻辑漏洞
等等
XML 相关的特殊安全漏洞:
XPath注入
XQuery注入
拒绝服务攻击(SOAP 数组溢出、递归的 XML 实体声明、超大消息体)
信息泄漏(XML External Entity File Disclosure)
等等
In the api interface, you can also see some information call queries. Here, there will be a problem of parameter sensitive information leakage. This can usually be found by combining tools and manually testing.
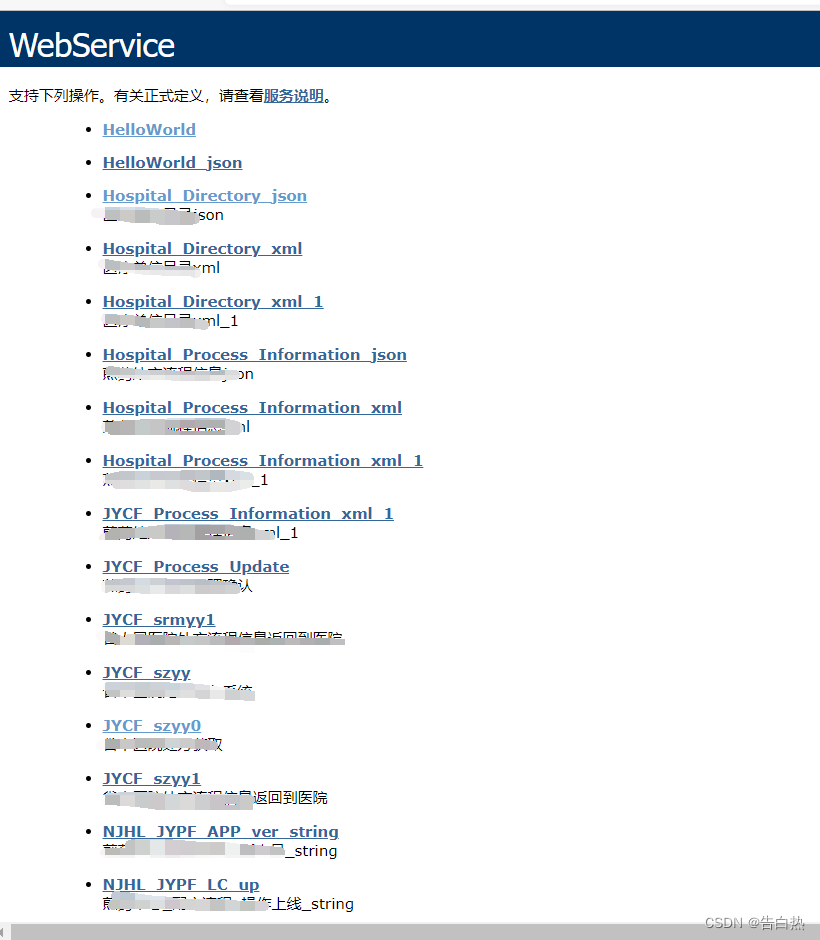
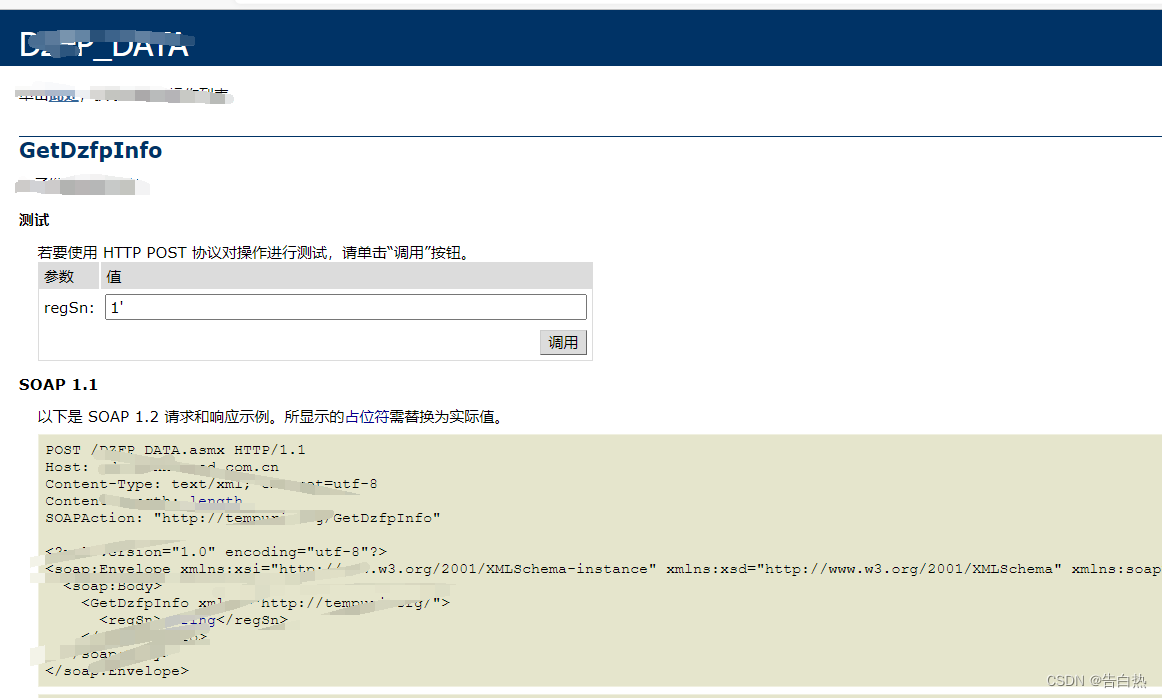
For these places, you can test injection, query information, etc.,
tool test: SoapUI Pro+burp
fingerprint: "?wsdl" && "edu" && country="CN"
A good article can be learned:
https:// cloud.tencent.com/developer/article/1666998
0x02 SOAP class-Swagger interface test
The goal of Swagger is to define a standard and language-independent interface to the REST API, which allows people and computers to have the ability to discover and understand services without access to source code, documentation, or network traffic monitoring. When properly defined through Swagger, users can understand and interact with remote services with minimal implementation logic. Similar to interfaces implemented for low-level programming, Swagger takes the guesswork out of invoking services.
When collecting target information, you can verify whether there is a Swagger interface. The following is the directory fingerprint of the feature:
/swagger/
/api/swagger/
/swagger/ui/
/api/swagger/ui/
/swagger-ui.html
/api/swagger-ui.html
/user/swagger-ui.html
/swagger/ui/
/api/swagger/ui/
/libs/swaggerui/
/api/swaggerui/
/swagger-resources/configuration/ui/
/swagger-resources/configuration/security/
Swagger接口漏洞测试类型
接口越权
接口SQL注入(针对所有查询接口)
接口未授权访问(重点针对管理员模块,如对用户的增删改查)
任意文件上传(针对上传接口进行测试)
测试信息泄露(重点针对用户、订单等信息查询接口,以及一些测试数据等)
There may be a swagger interface for file upload,
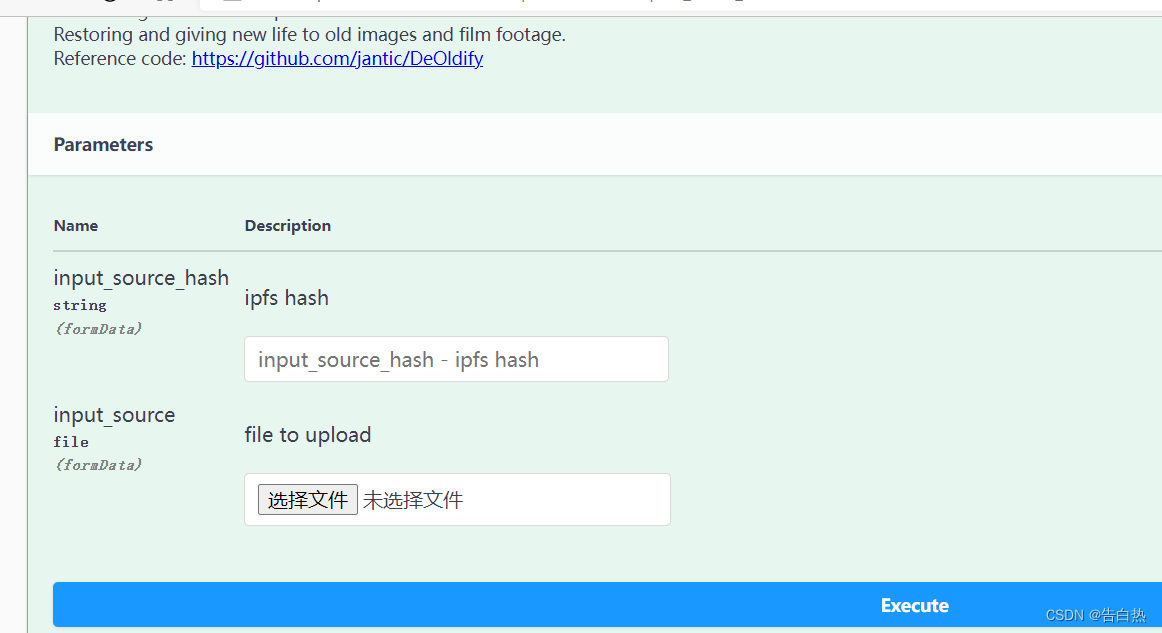
where there is data query, you can also test injection, etc.
Tool test:
https://github.com/lijiejie/swagger-exp
https://github.com/jayus0821/swagger-hack
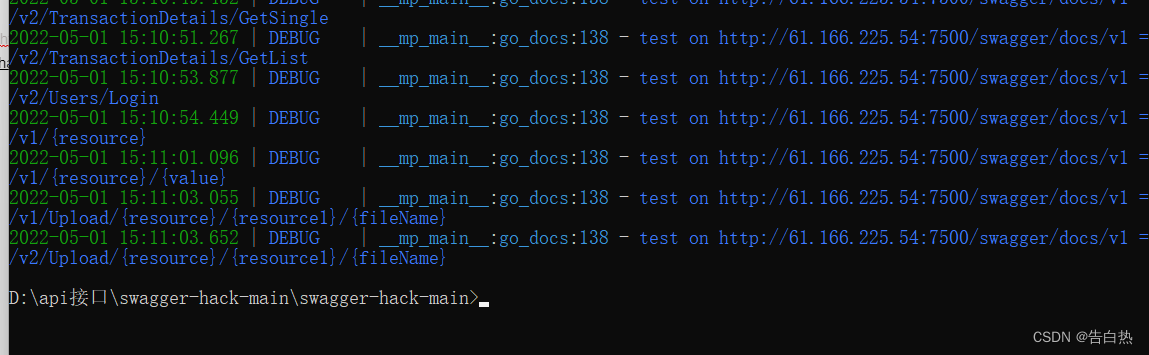
After the test, you can view the test results and return 200, whether there is sensitive information
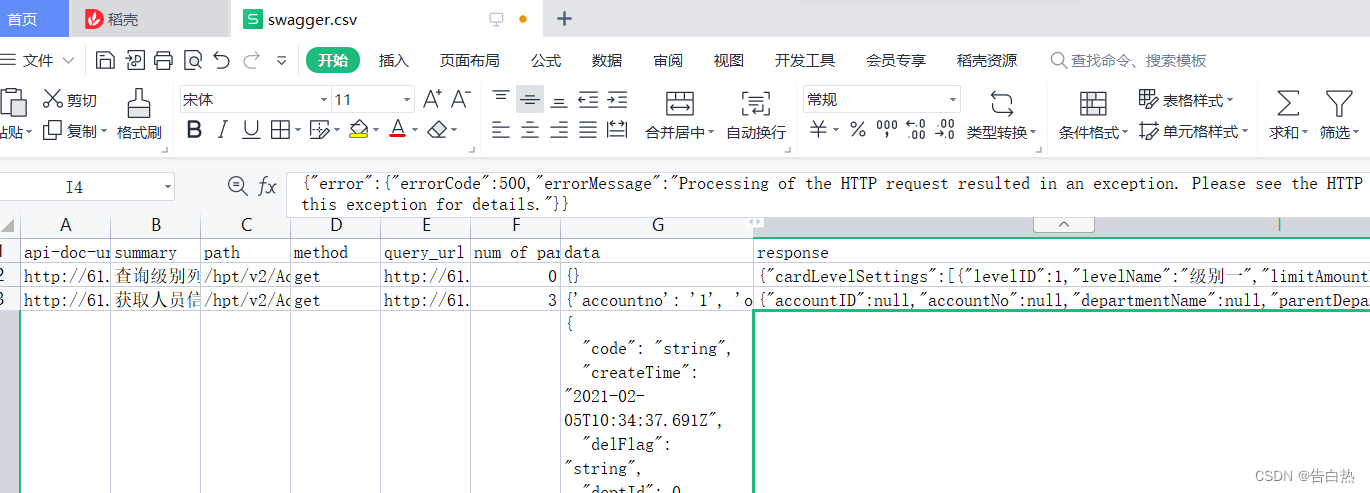
0x03 HTTP class - Webpack test
webpack is a front-end modular packaging (construction) tool.
webpack automatically handles all complicated, repetitive, and mechanical work, and developers only need to focus on the realization of functions. Fingerprint
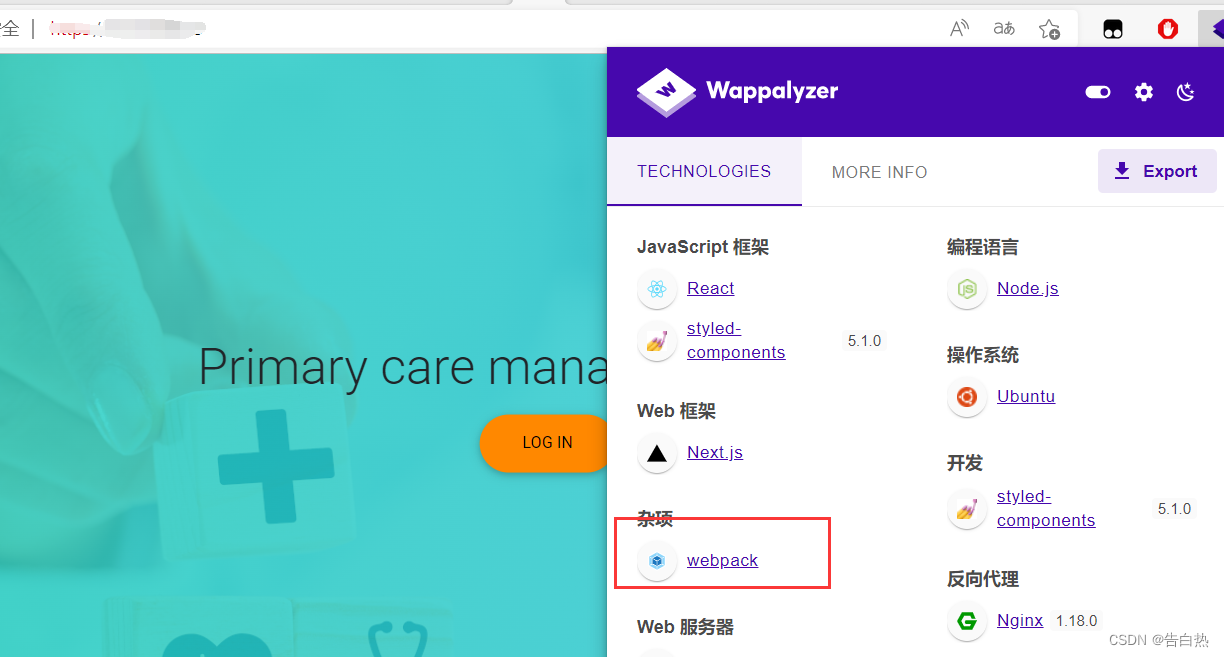
: Use wapplyzer to help identify
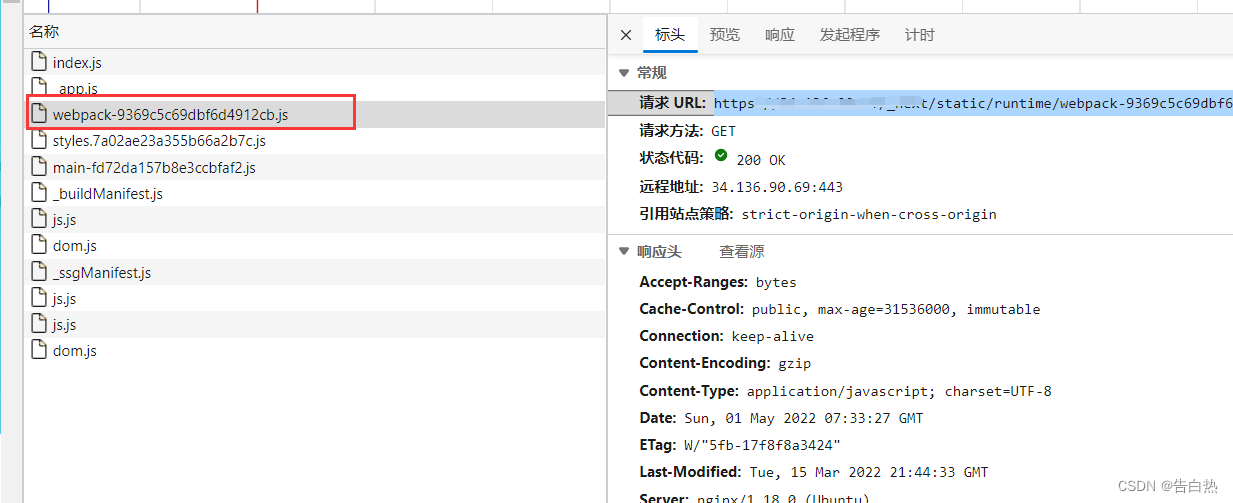
js fingerprints:
Webpack Vulnerability detection,
the tool supports automatic fuzzy extraction of the API corresponding to the target site and the parameter content corresponding to the API, and supports seven major vulnerabilities: unauthorized access, sensitive information disclosure, CORS, SQL injection, horizontal authority violation, weak password, and arbitrary file upload Perform fuzzy and efficient fast detection. After the scan is over, this tool also supports automatic generation of scan reports, and you can choose the HTML version that is easy to analyze and the more formal doc, pdf, and txt versions.
Packer-Fuzzer:https://github.com/rtcatc/Packer-Fuzzer
python3 PackerFuzzer.py -t adv -u http://chargepoint.com