Author: Wan Yuxin of Jingdong Industry
I believe that many people have played minesweeper games since they were young. In that era when there were not many computer games, minesweeper became one of the most popular games. Later, I also had the urge to do it once. Through dynamic debugging, reverse engineering and C to write a minesweeper auxiliary tool to improve reverse engineering and coding skills.
Dynamic debugging (analysis)
First, perform dynamic debugging (analysis) of the minesweeper program:
Open OD ( ollydebug tool), drag and drop minesweeper into OD , F9 to run; ctrl+G to input the expression to follow, input rand , click [OK] to jump to the function call, F2 to set a breakpoint, this The second is to find a breakthrough through the API rand function. Click any position in the minefield of the minesweeper window (where 2 appears in the picture ), and then click Restore ([Smiley Face] button - ), as shown in the figure below:

At this time, the OD will break at the breakpoint at the rand just set , as shown in the figure below:
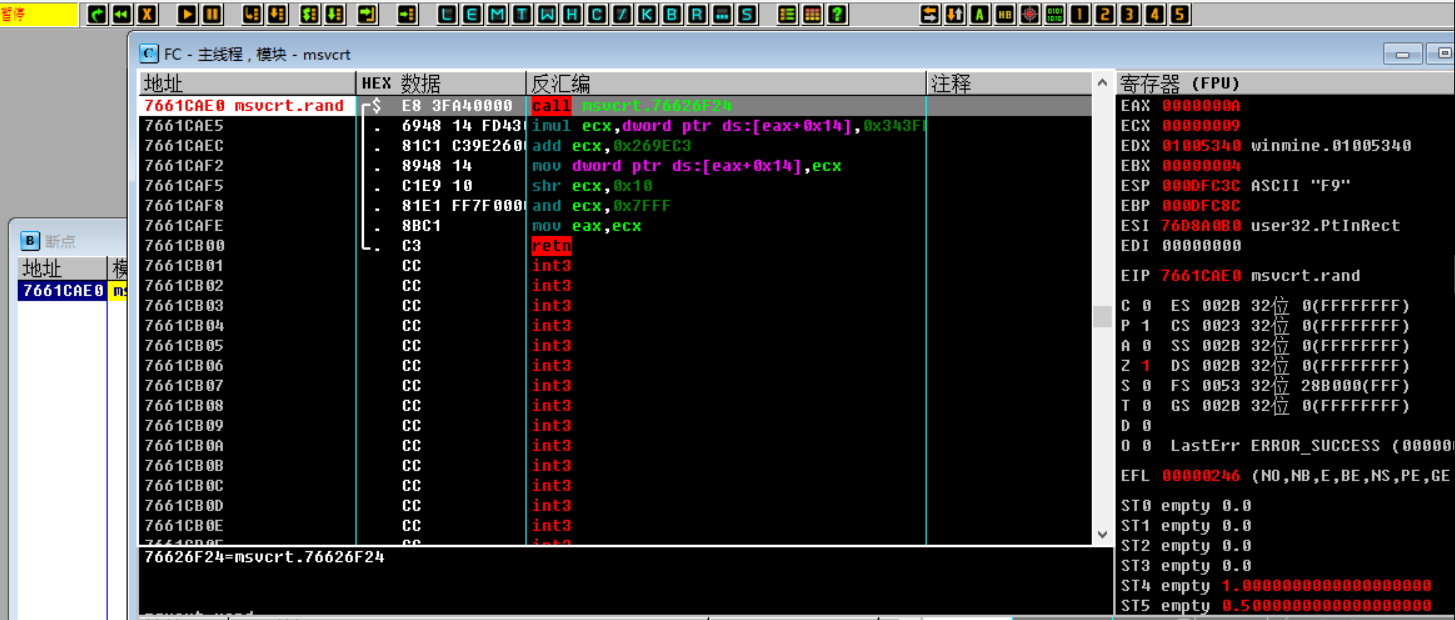
By finding the random function rand , the following stack backtracks, and returns to the upper-level function to find the parameters of push (push into the stack), that is to say, the random generation function ( rand ) is randomly generated height, width, and thunder. Click K (call stack) to pop up the K call stack window, view the stack window information, find the return address, double-click the return address in the K call stack window, and return to the previous layer. This process is called stack backtracking. Carefully observe the stack information 010036D2 (return address) in the figure below .
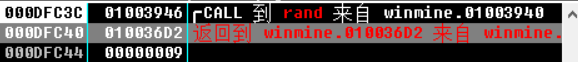
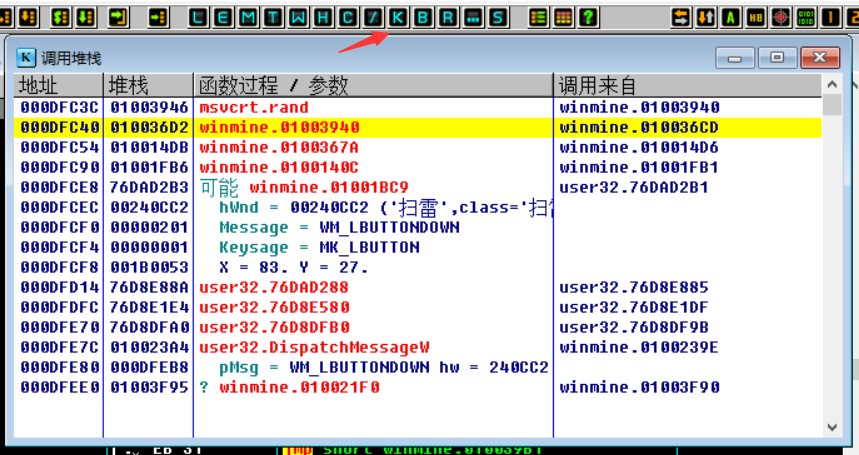
Single-step F8 , observe the register, data window and stack window changes, dword ptr ss:[esp+0x4] or dword ptr ds:[XXX] data window tracking value ( 000DFC44 value is 09 ), as shown below:
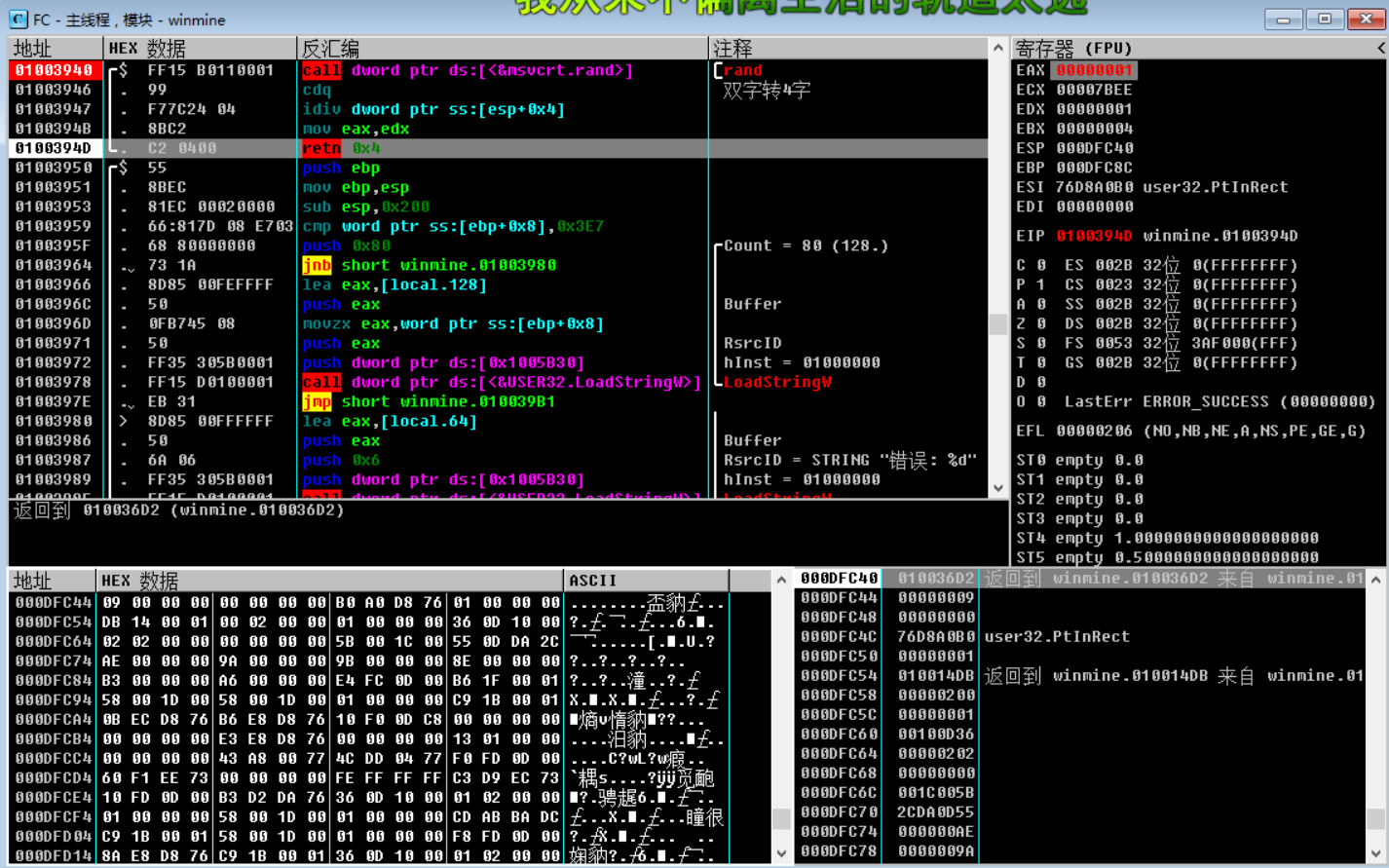
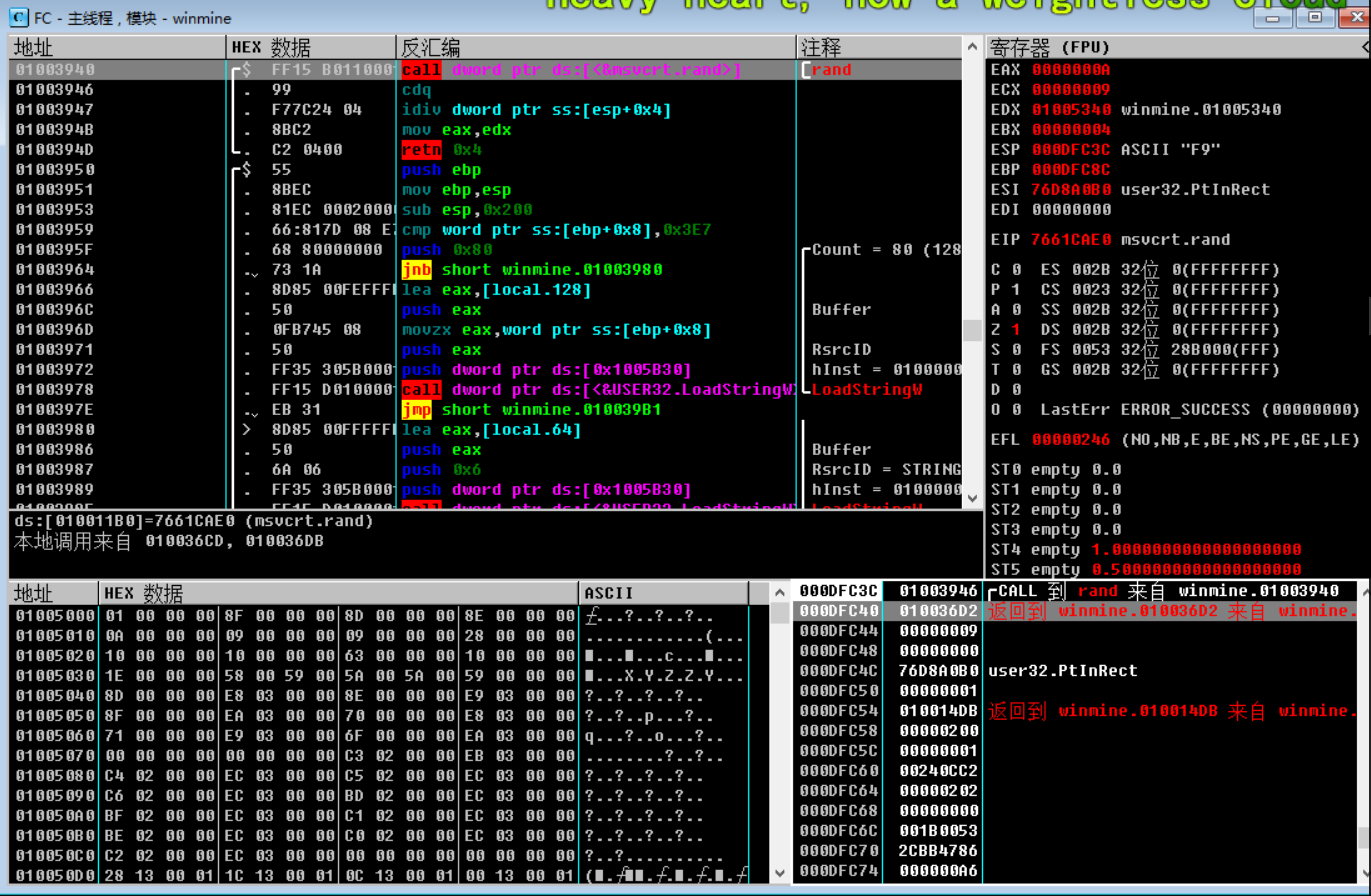
After returning to the upper-level function, analyze the instructions inside, and know the width ( 09 ) generated by random rand just now , as shown in the figure below, pay attention to the address 010036C7 .
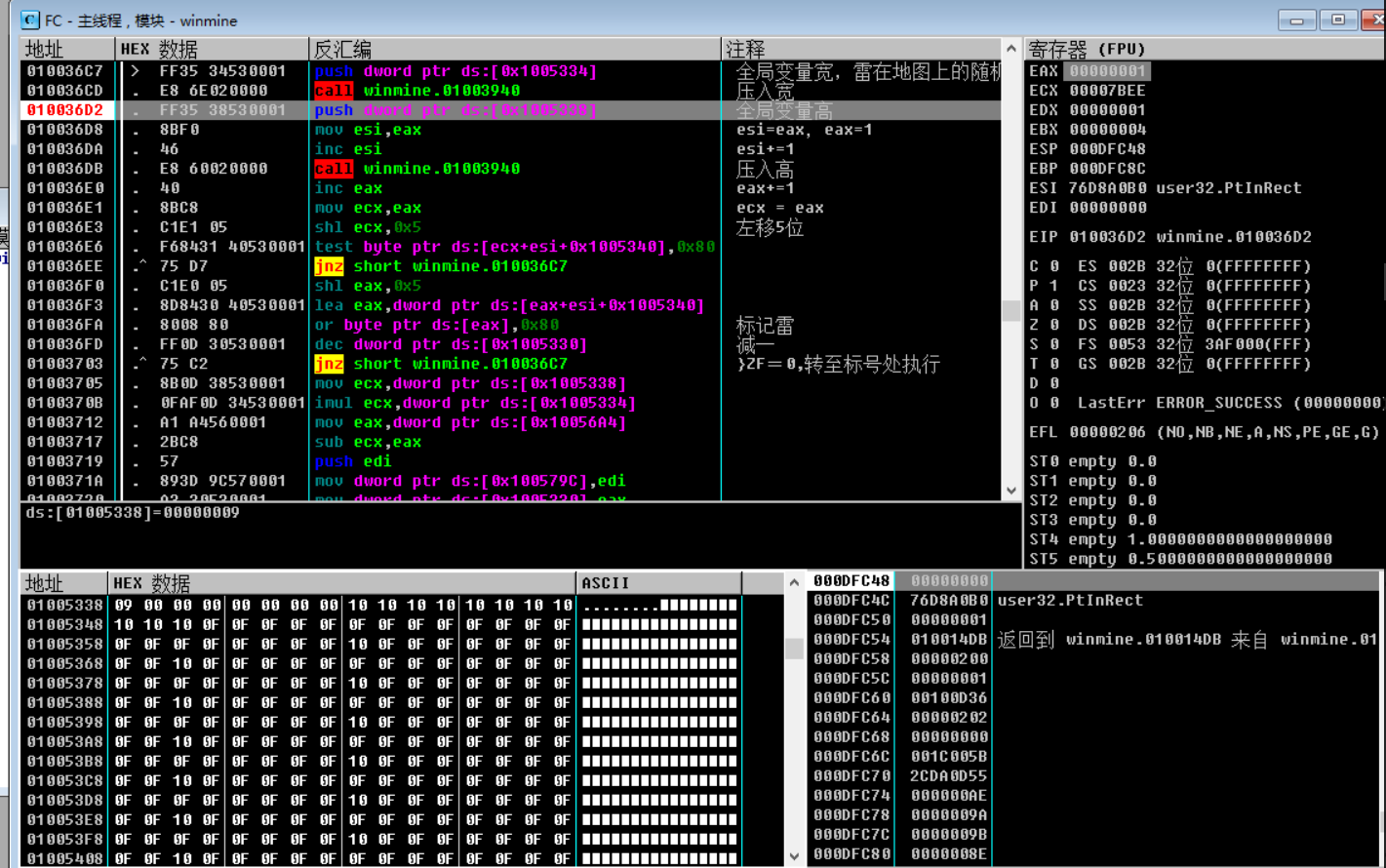
First, analyze eax from the result returned by this function . After a single step, you can see that a number 09 is pushed into the stack (address 010036D2 ) , as shown in the figure below:
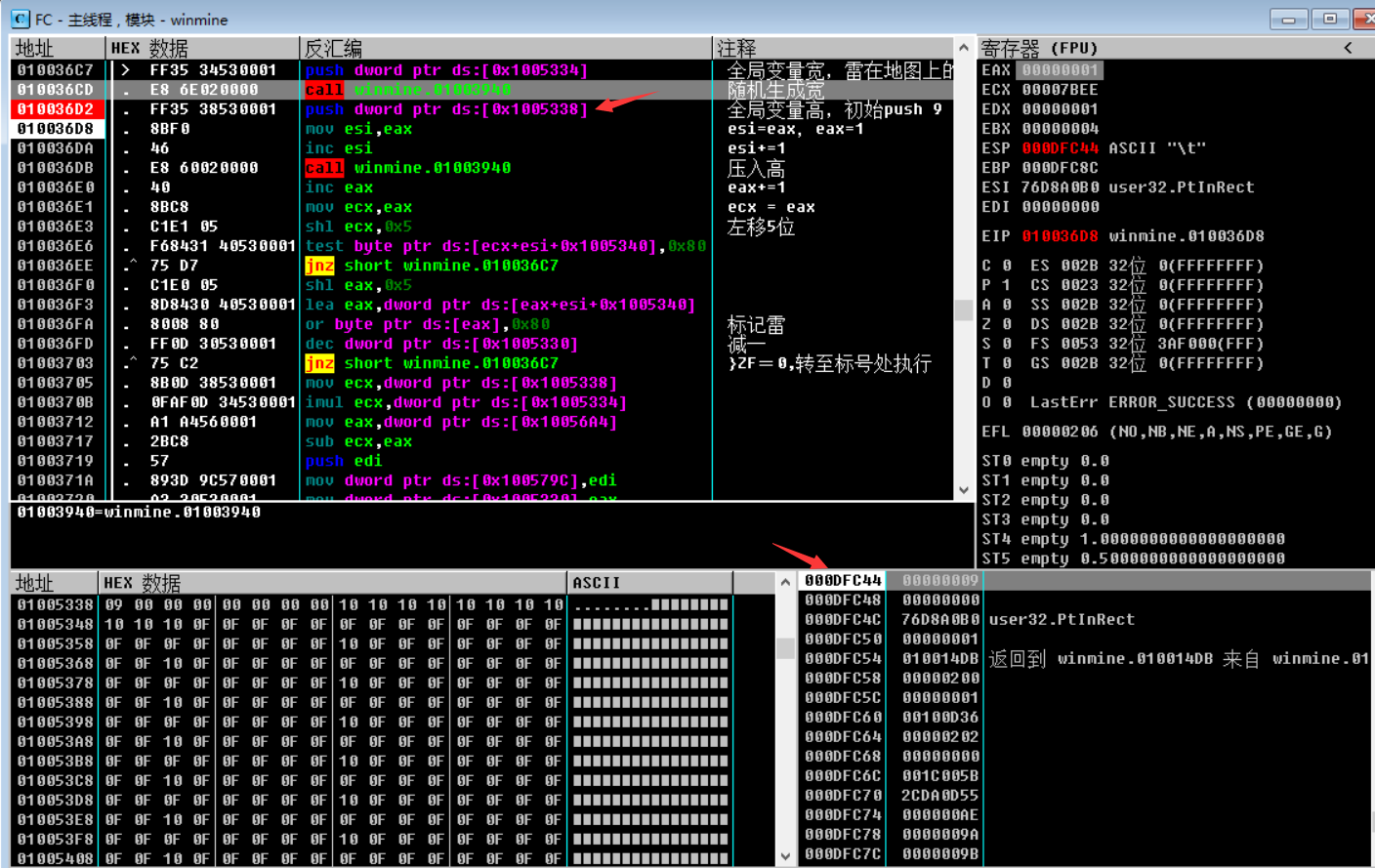
Through the above analysis, it can basically be guessed that the surrounding random function rand generation is high, thunder number. You can try to change the minesweeping settings (custom minefields), as shown in the figure below, to accurately locate the rand function and pass parameters, click [OK], and then click the [Restore (smiley face - )] button.
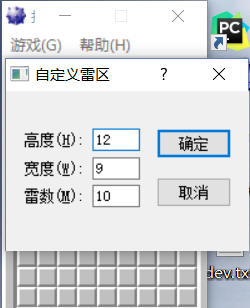
Observe the OD , as shown in the figure below:
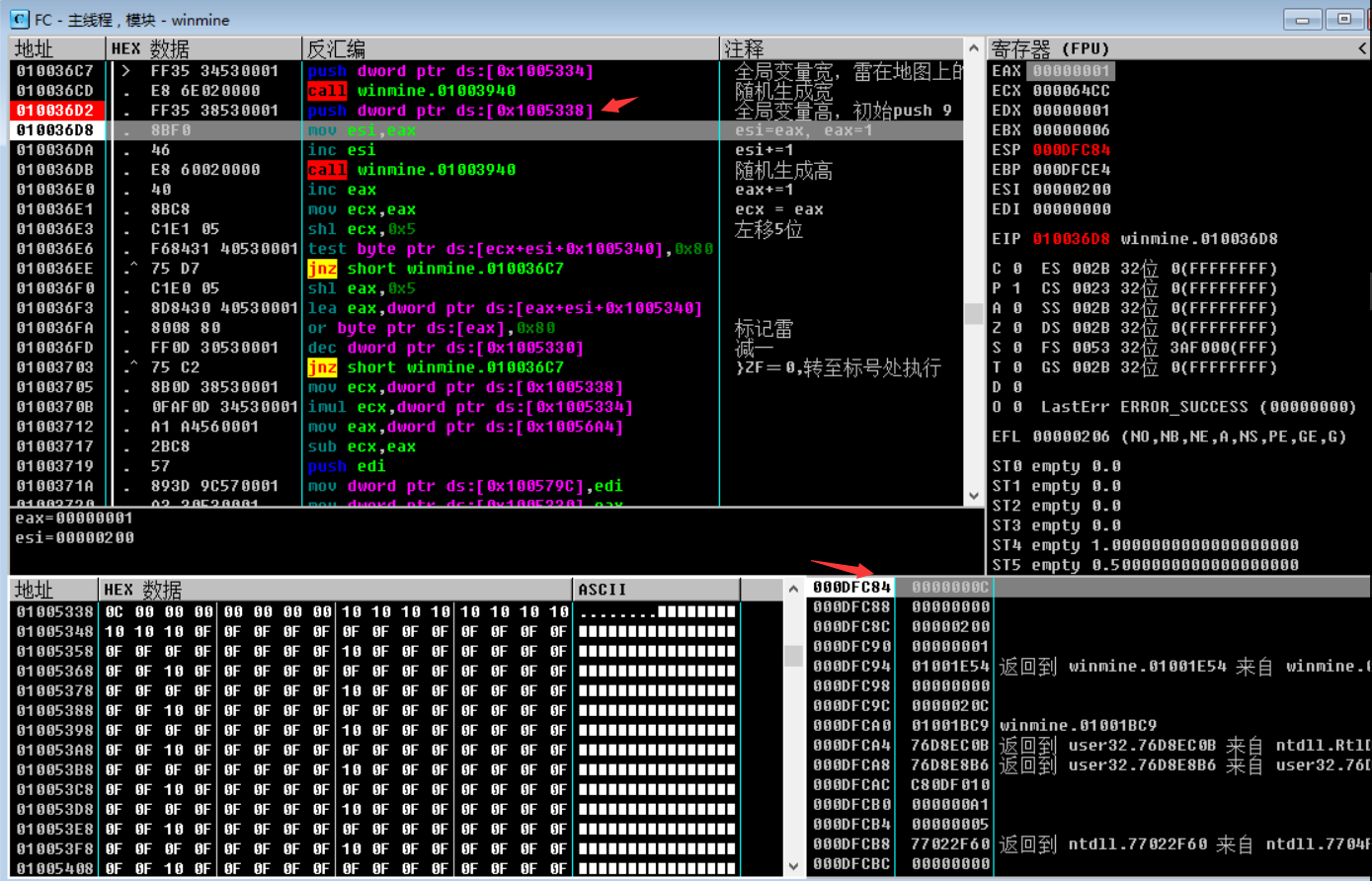
It is found that push 0C ( the value of 000DFC84 is 0C ), it can be determined that the push 0C of this rand function is the height of the minefield. At the same time, you can clearly see a rough minefield graphic in the memory area. Through the above method, you can roughly guess that 0x80 is a minefield. Or analyze together with IDA , through static analysis, you can see the program logic more intuitively. Get the following data: base address, mine number and other information, as shown in the figure below:
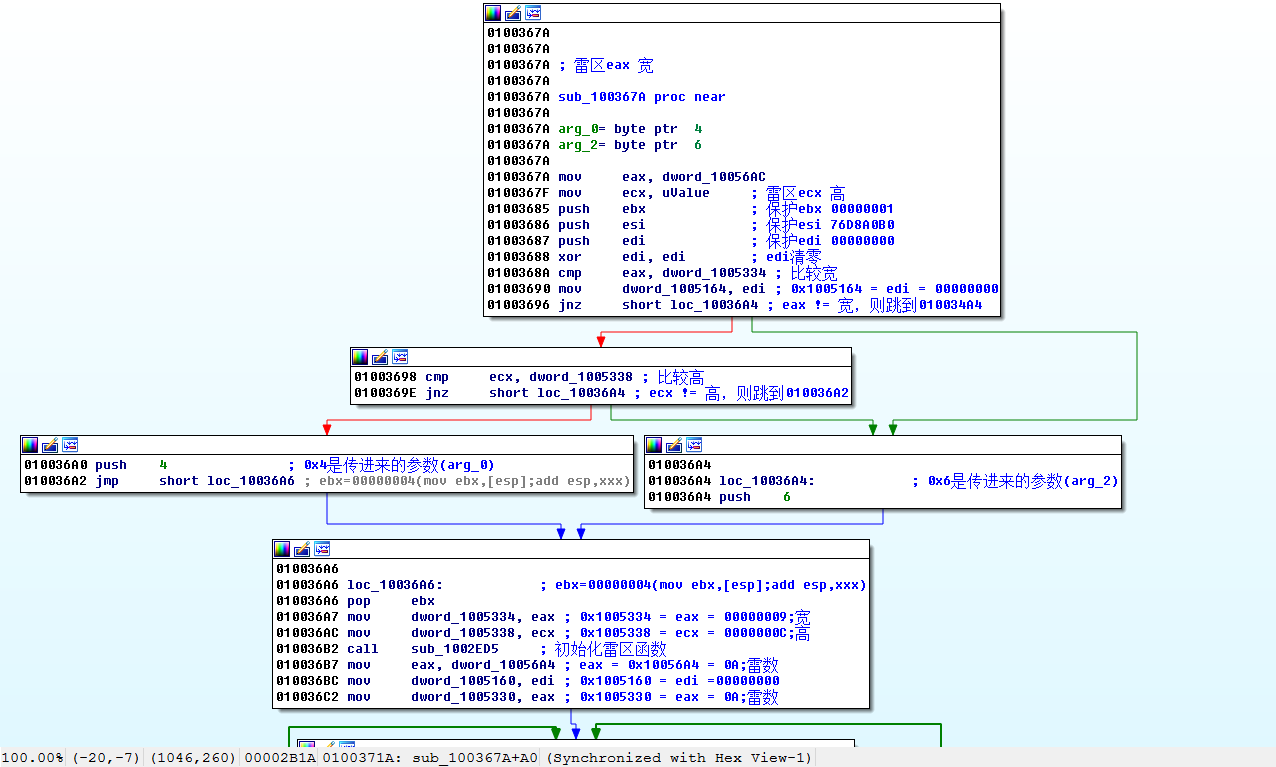
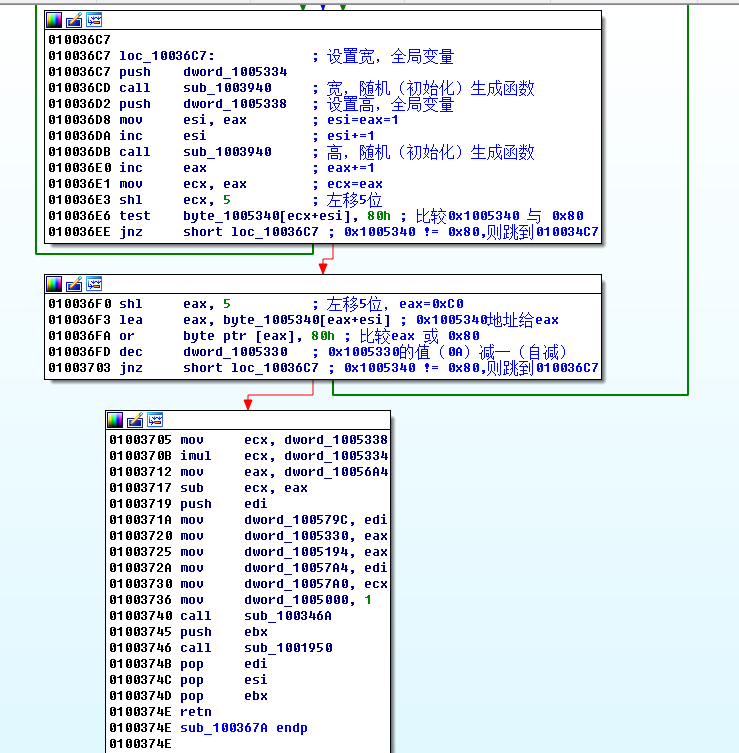
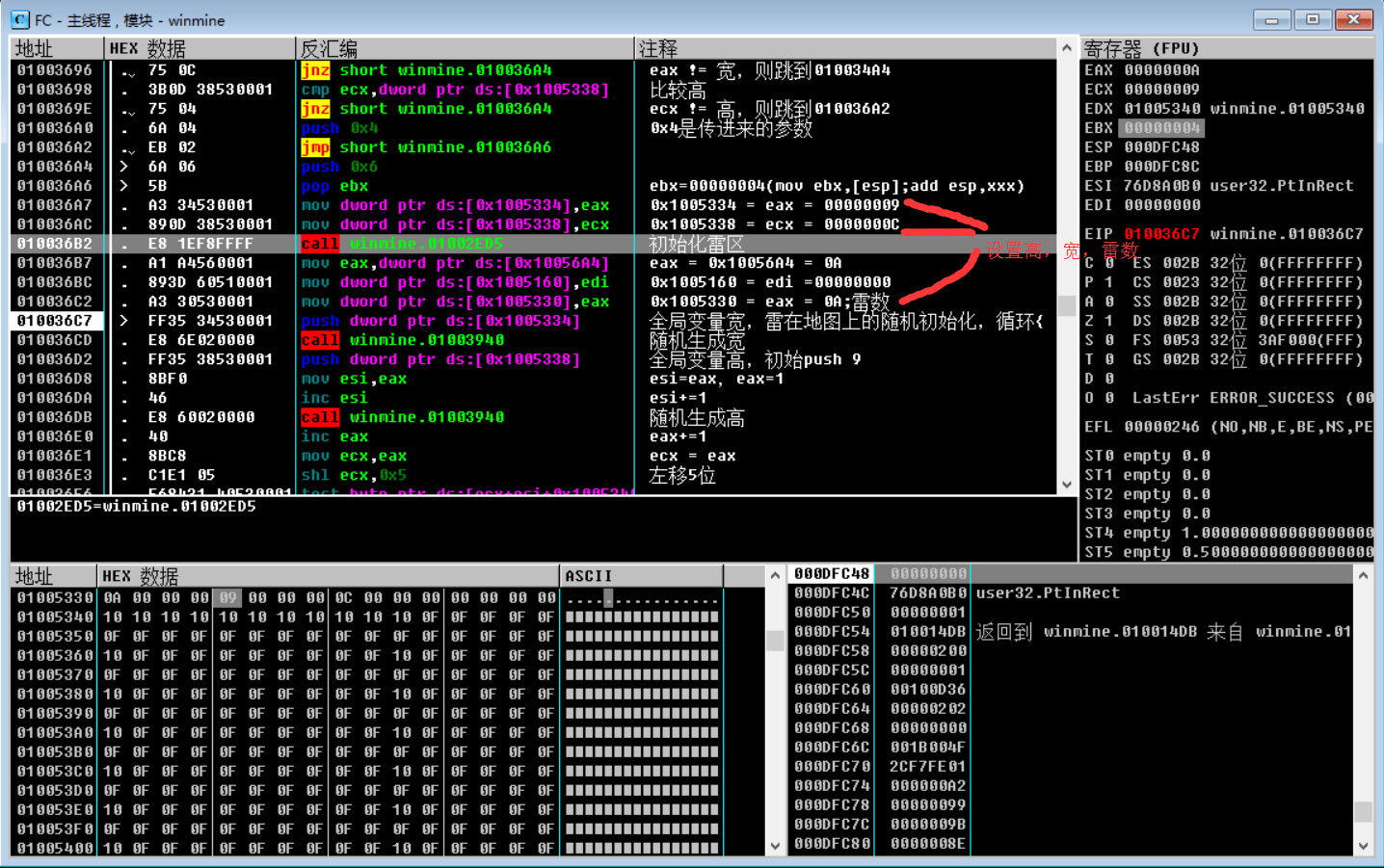
The above code probably means that the variables of global width 0x09 , height 0x0C , and thunder number 0x0A are set first , and the width and height are randomly generated by judging two layers of loops. Get map base address: 0x01005340 . By analyzing the figure below, we know that no mine is 0x0F , mine is 0x8F , and the wall is 0x10 .
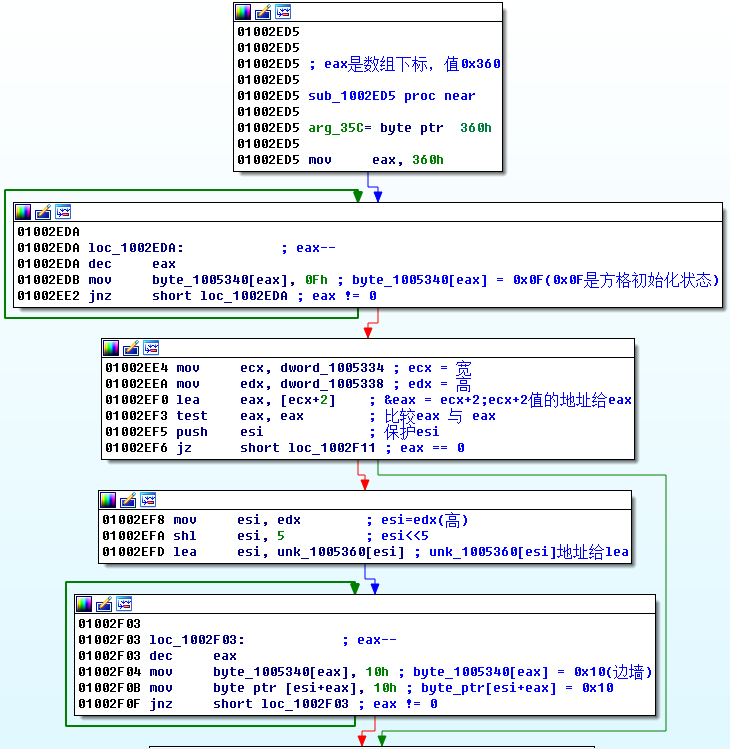
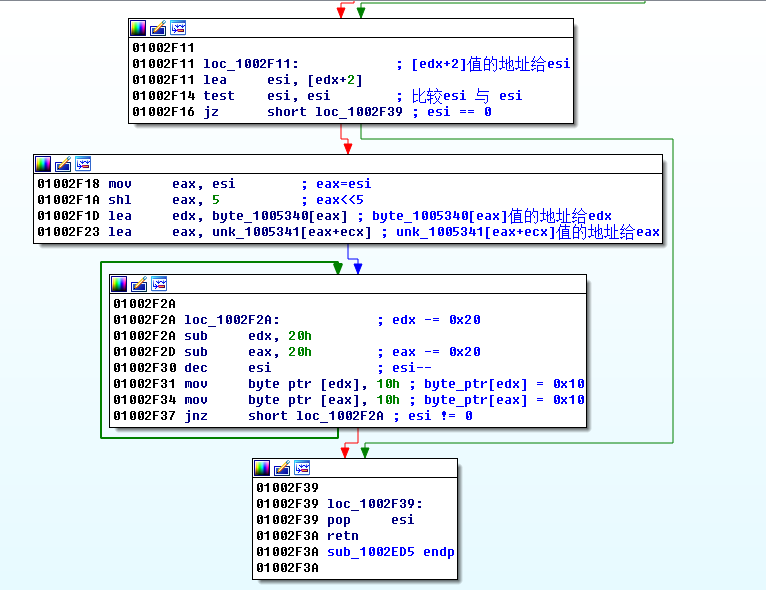
Through the width and height addresses, the minesweeping area and the number of mines are printed, and the side walls and mines can be distinguished more intuitively.
Next, let’s start to figure out how to mark Lei. By assuming that the GetDC function is seen in WinProc (backtracking through the stack to the message callback function) , it is roughly guessed that Bitblt will be used . In OD , enter the expression to be followed by ctrl+g , and enter " BitBlt ”, press F2 to set a breakpoint, click any position in the minesweeping area, and the OD will break at the BitBlt position.
There is also a BitBlt function in BitBlt . The preliminary judgment is that it uses double buffering to draw.
BitBlt(hDestDC,// Destination DC XDest, // Destination x coordinate YDest, // Destination y coordinate 10, // 10, // Height and width of redrawing area hSrcDC, // Source DC 0, 0, SRCCOPY); // Specify the operation method to calculate the coordinates of the mine (click the first mine-sweeping square to view the coordinates), you need to pay attention to the side wall, as shown below:
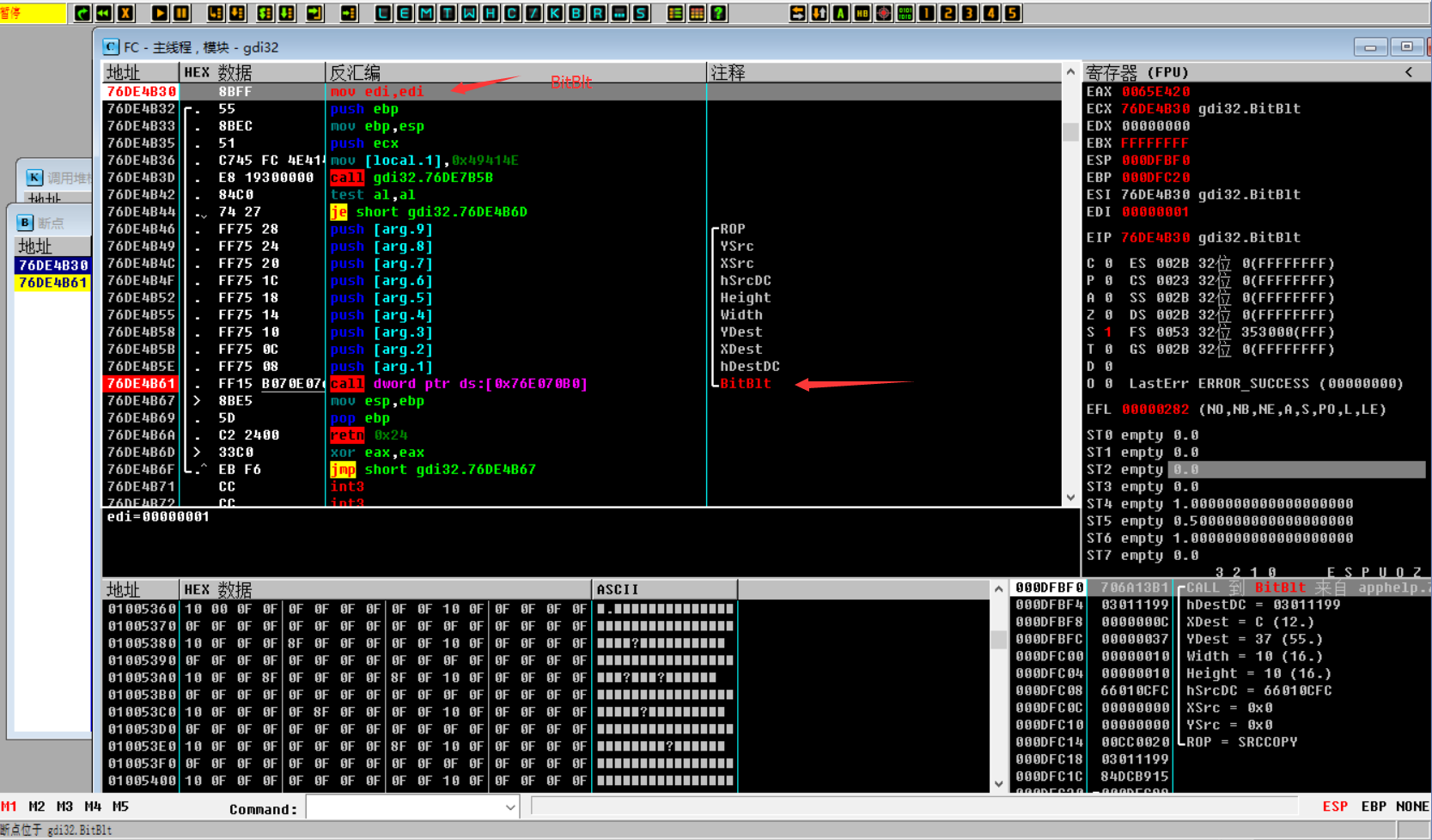
Subtract the value of the side walls:
-0x04=0x0C(12)-0x10(16)
0x27=0x37(55)-0x10(16)
Get the coordinate formula: x ( XDest:12 ) =1*0x10(16)-0x04(4) , y ( YDest:55 ) =1*0x10(16)+0x27(39).
code writing
Through the above rough analysis, the code can be written,
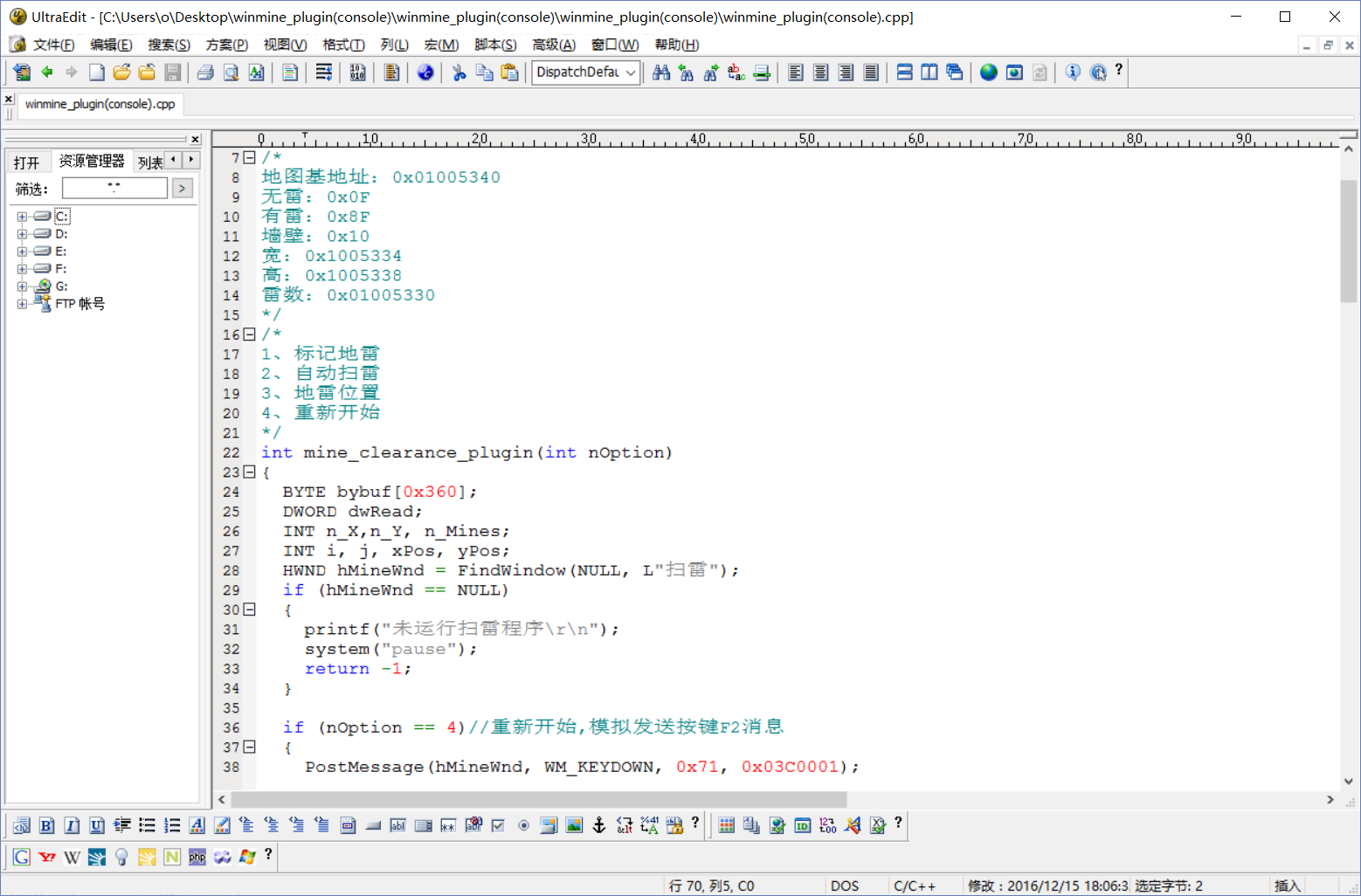
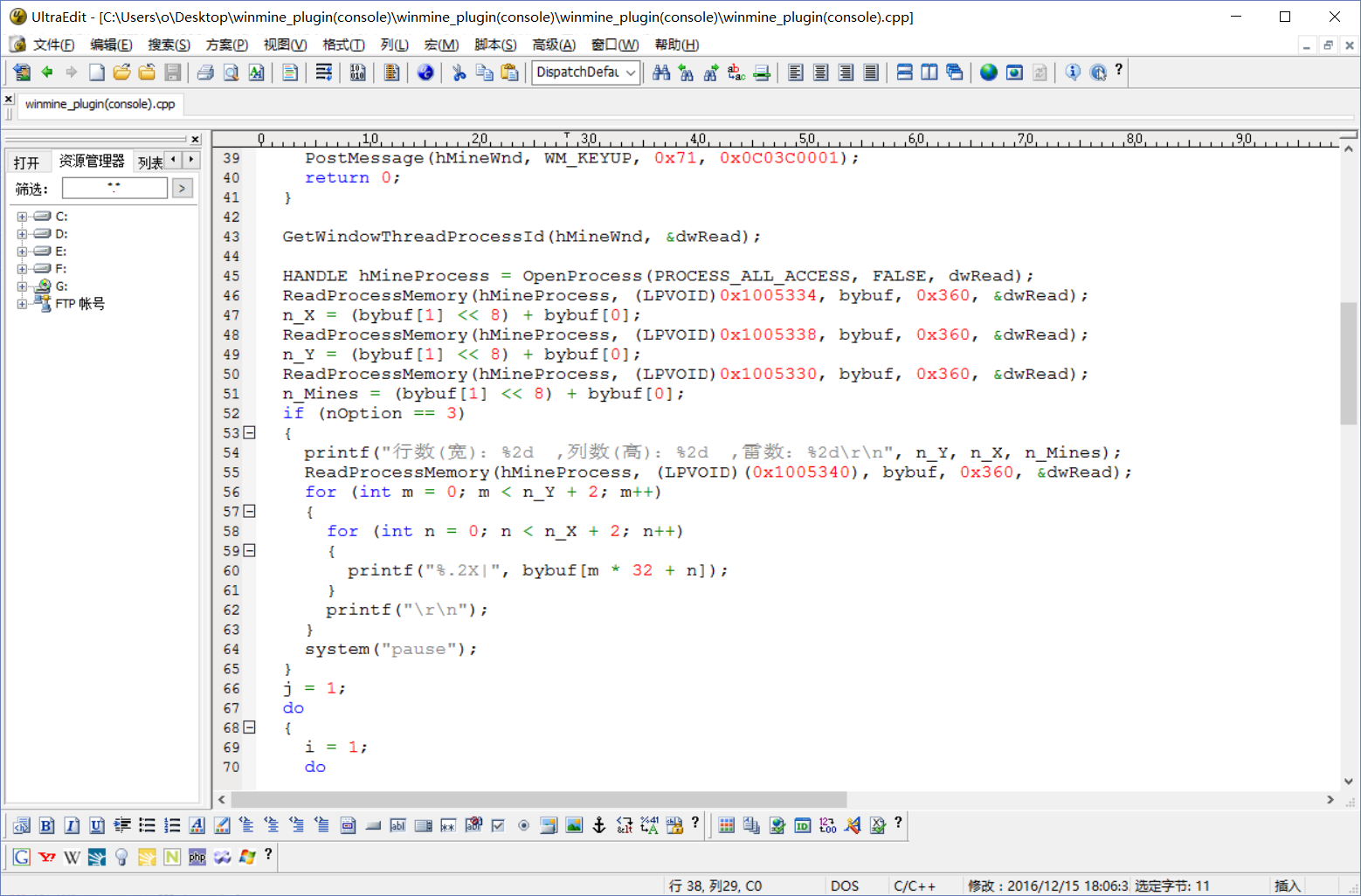
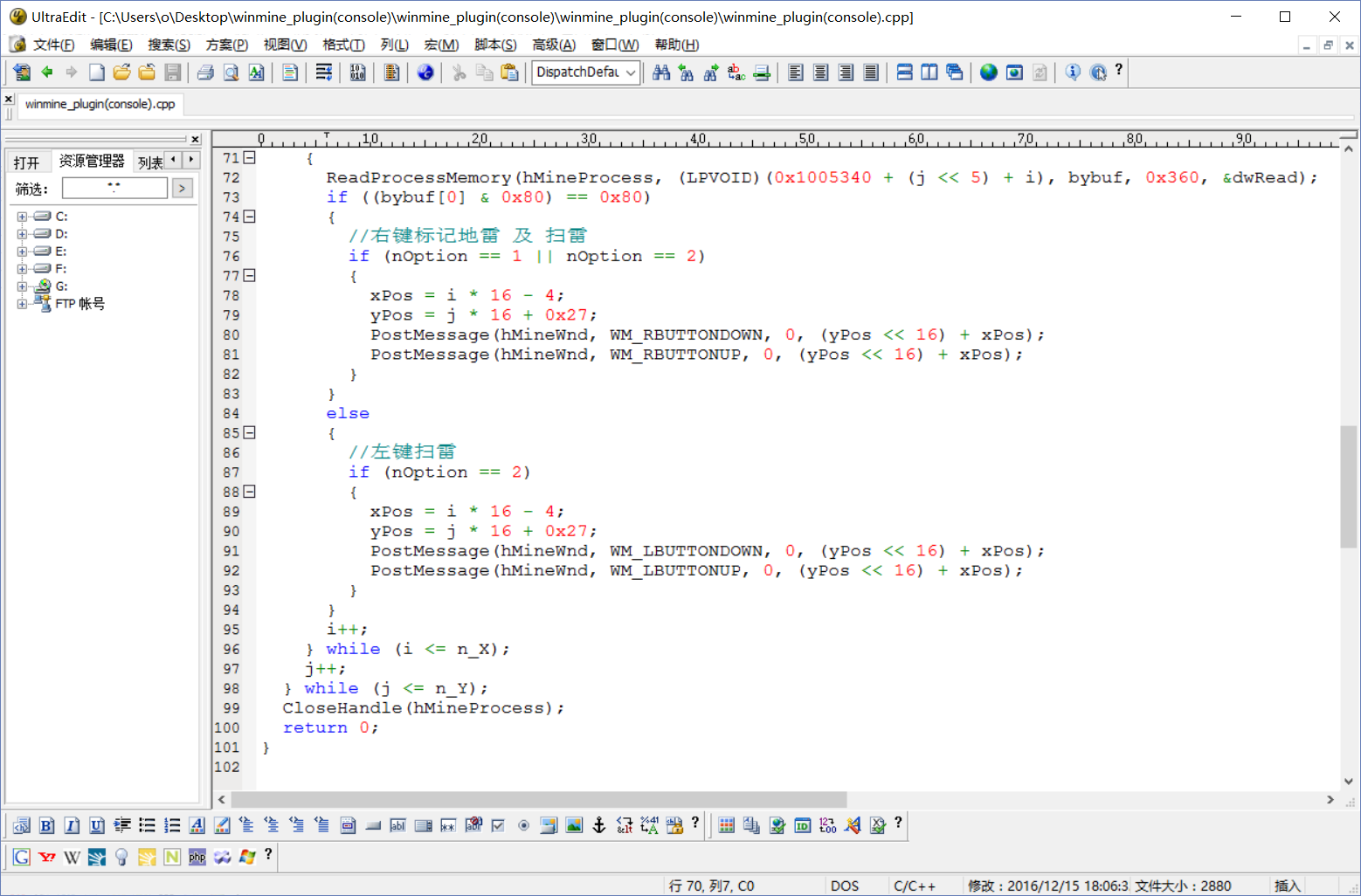
achievement
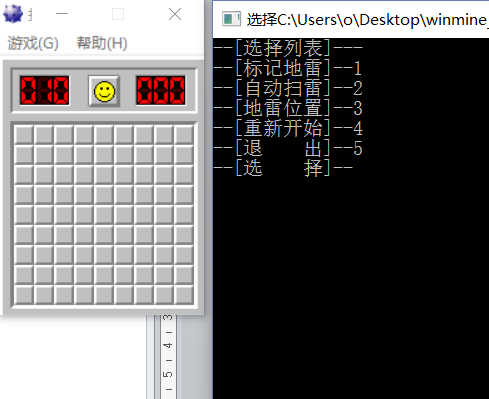
Enter 3 landmine locations to get landmine ( 10 walls, 8F landmine, 0F no mine)
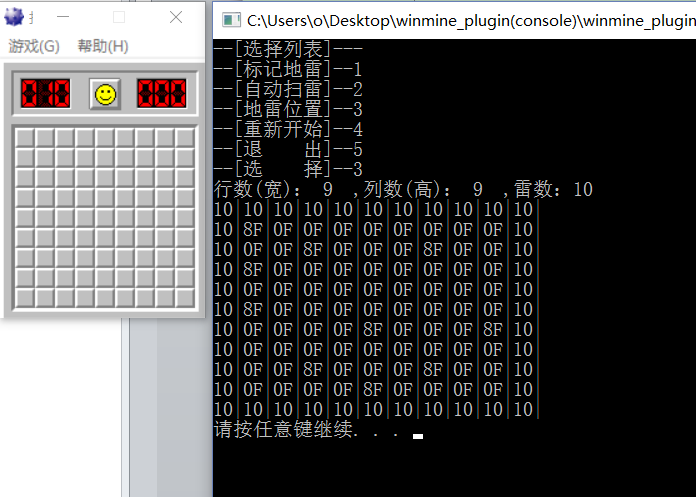
Enter 2 to automatically clear mines, mark mines and open the map
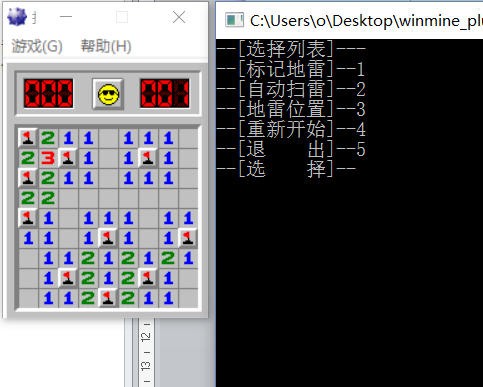
Through this small project, first of all, a kind of reverse thinking about the software has been strengthened, such as: seeing this kind of panel, I probably guessed that it is implemented with an array, and secondly, the layout of mine is randomly generated, and then through dynamic debugging, we can understand The implementation method (an implementation idea of the developer), can find the key base address, several states (no thunder, thunder, wall), the last coding stage can understand the operation of the memory, several important APIs, FindWindow to obtain the handle , OpenProcess opens the handle, ReadProcessMemory reads memory information, PostMessage asynchronous message mode, CloseHandle closes the handle. Some of the analysis is wrong or not in place, please shoot for bricks. More reverse, analyzing the code is very helpful, not only can you broaden your thinking and level of programming and testing, but also discover, develop and exploit loopholes in the program or patch the program, etc. I hope that my friends will work hard and encourage each other on this long and arduous journey.