According to a Bloomberg report yesterday , security researchers from Kaspersky Lab confirmed that the Pinduoduo app contained malicious code after Google removed it from its official app store, the Play Store.
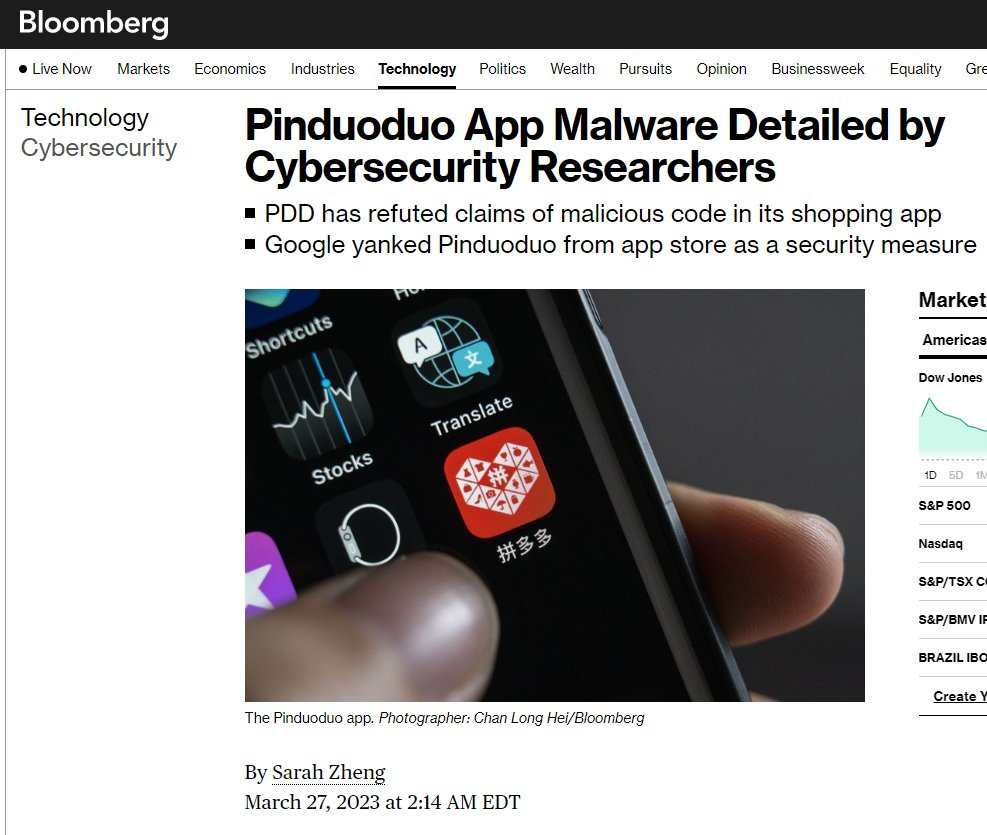
In one of the first public reports of the malicious code, Kaspersky explained how the app elevates itself to compromise user privacy and data security . It tested versions of the app distributed through China's local app stores -- including those from Huawei, Tencent and Xiaomi.
The findings, which Kaspersky shared with Bloomberg, are among the clearest explanations from the independent security team for triggering Google's actions and malware warnings last week. The cybersecurity firm, which has been instrumental in uncovering some of the biggest cyberattacks in history, said it found evidence of early versions of Pinduoduo exploiting system software vulnerabilities to install backdoors and gain unauthorized access to user data and notifications .
Those conclusions are largely in line with those posted online by other researchers over the past few weeks, though Bloomberg News has yet to confirm the veracity of earlier reports.
At present, discussions on this matter on Weibo have been on the hot search list.
Cybersecurity expert @sunwear also had this to say on the matter:
In addition to Kaspersky Lab, an analysis of the non-Google Play version of the Pinduoduo app by researchers from another security company, Lookout, also confirmed the allegations made by the independent security research organization DarkNavy . Preliminary analysis shows that at least two non-Play versions of the Pinduoduo app exploit the vulnerability CVE-2023-20963.
The vulnerability was disclosed by Google on March 6. Using this vulnerability can escalate privileges, and the entire process does not require user interaction. The fix was only made available to end users two weeks ago.
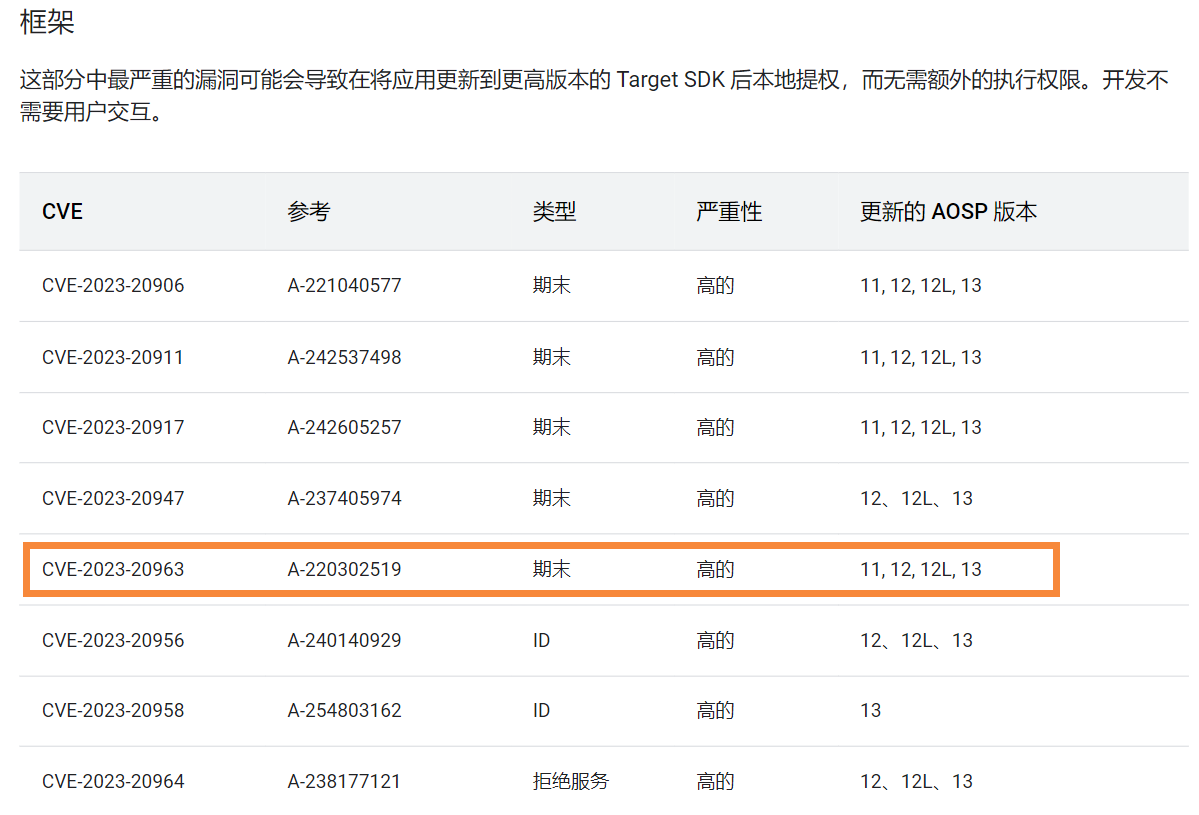
Researchers at Lookout analyzed two versions of Pinduoduo released before March 5, both of which contained code to exploit CVE-2023-20963. Both versions were signed with the same key as the Pinduoduo Google Play version.
There is currently no evidence that the versions on the Play Store and Apple's App Store contain malicious code, and the Pinduoduo apps downloaded through Google and Apple's official stores are safe. But Android users who downloaded through third-party markets are not so lucky. Given that Pinduoduo has hundreds of millions of users, the number of affected users may be very staggering.
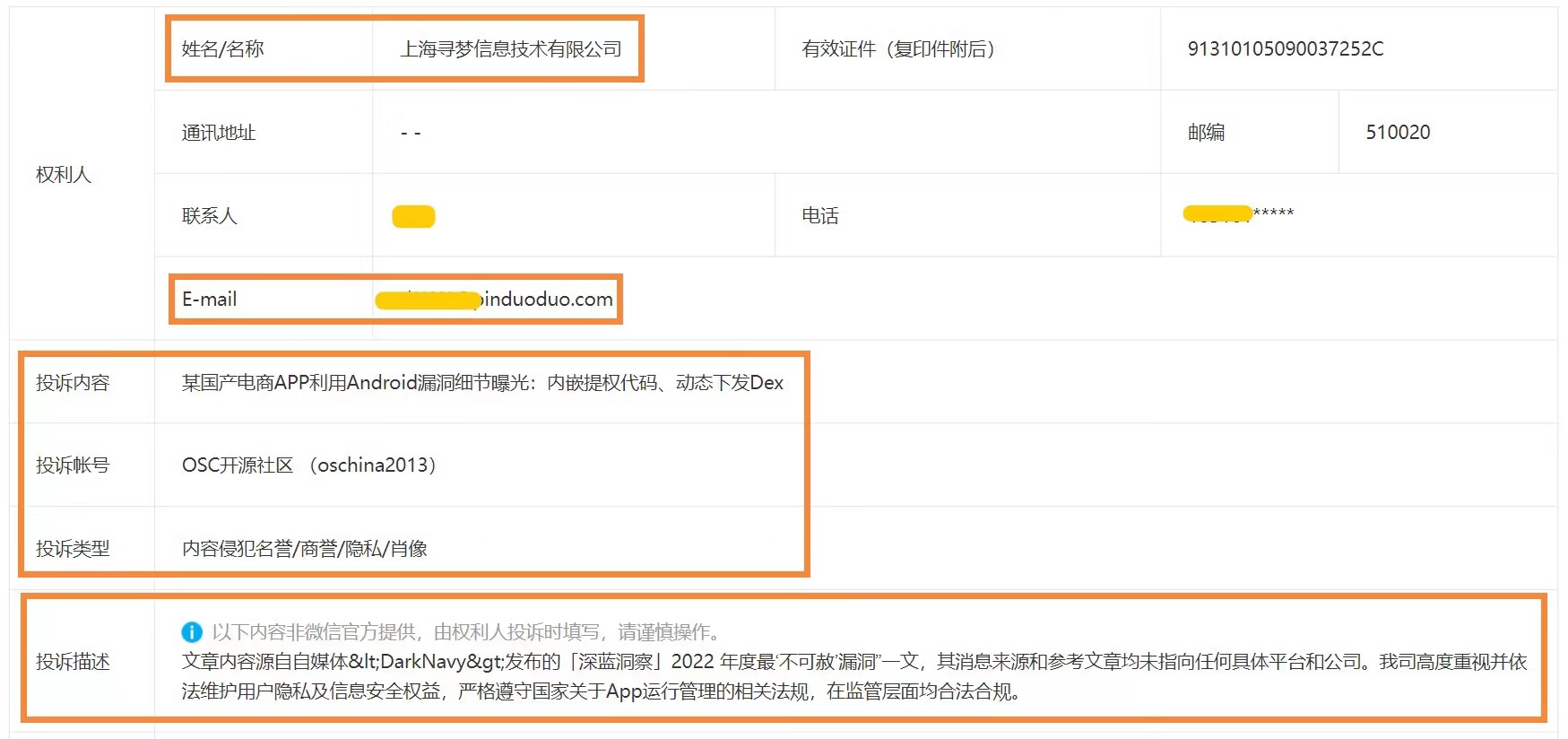
Yesterday, the related article previously reported by the OSCHINA WeChat official account "A domestic e-commerce APP exploits the details of Android vulnerabilities: embedded privilege escalation code, dynamic distribution of Dex" received a complaint from the main company of Pinduoduo, the complaint type is " content infringement Reputation/Goodwill/Privacy/Likeness ". However, the article did not name which company or which APP it was from the beginning to the end.
further reading
- The details of a domestic e-commerce APP exploiting Android vulnerabilities are exposed: embedded privilege escalation code, dynamic delivery of Dex
- Pinduoduo Malicious Behavior Analysis Report
- Pinduoduo apk embedded privilege escalation code, and dynamic dex analysis
update:
On March 28, China Business News asked Kaspersky about the fact that the Pinduoduo app contained malicious code.
Kaspersky responded to CBN by saying: It has received comments from security researcher Igor Golovin that some versions of the Pinduoduo APP contain malicious code, exploit known Android vulnerabilities to escalate privileges, download and execute additional malicious modules, some of which Also gained access to user notifications and files. Our products detect these versions as HEUR:Backdoor.AndroidOS.Pinduo.a. Infected versions of the app are distributed through a local app store.
Kaspersky also said that as background information, we did not find this malicious version, we only detected it. In other words, the version containing the malicious code was not the first that Kaspersky discovered. But Kaspersky did detect malicious code in this version .
Source: https://finance.sina.com.cn/tech/roll/2023-03-28/doc-imynkyaa1518200.shtml