20155206 Experiment 4 Malicious code analysis
System operation monitoring
1.Schtasks
, Create a netstat20155206.txt file, enter in the file
date /t >> c:\netstat20155206.txt time /t >> c:\netstat20155206.txt netstat -bn >> c:\netstat20155206.txt
, Change the file name to netstat20155206.bat
, create another netstat20155206.txt
, and cut these two files to the C drive directory
method
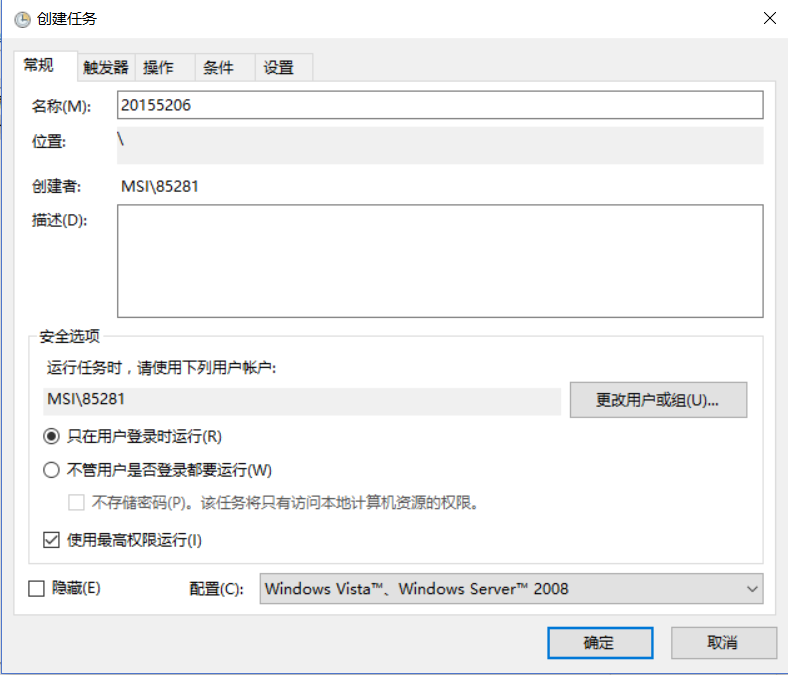
, open the control panel and search for scheduled tasks
, select Create task, set the name to 20155206, and select to run with the highest privilege
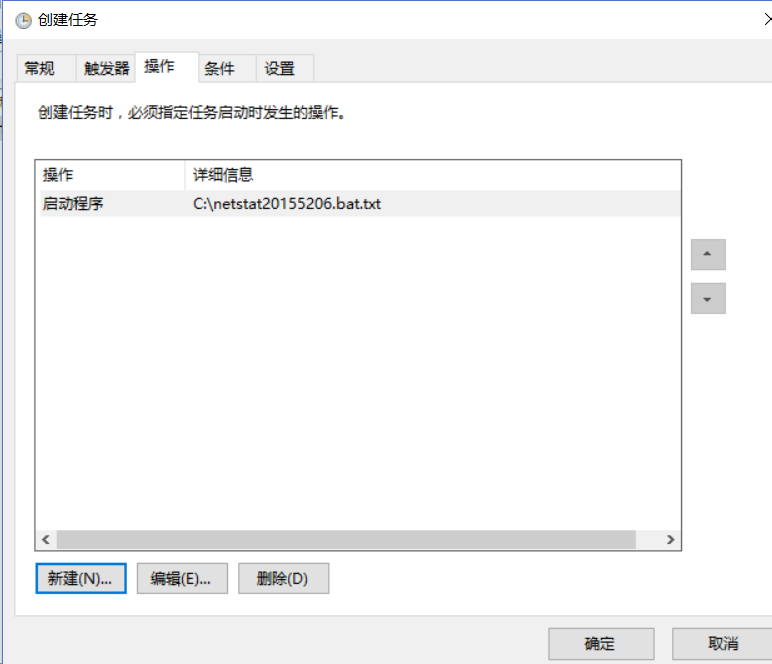
, open 20155206.txt, and get the picture as shown in the figure
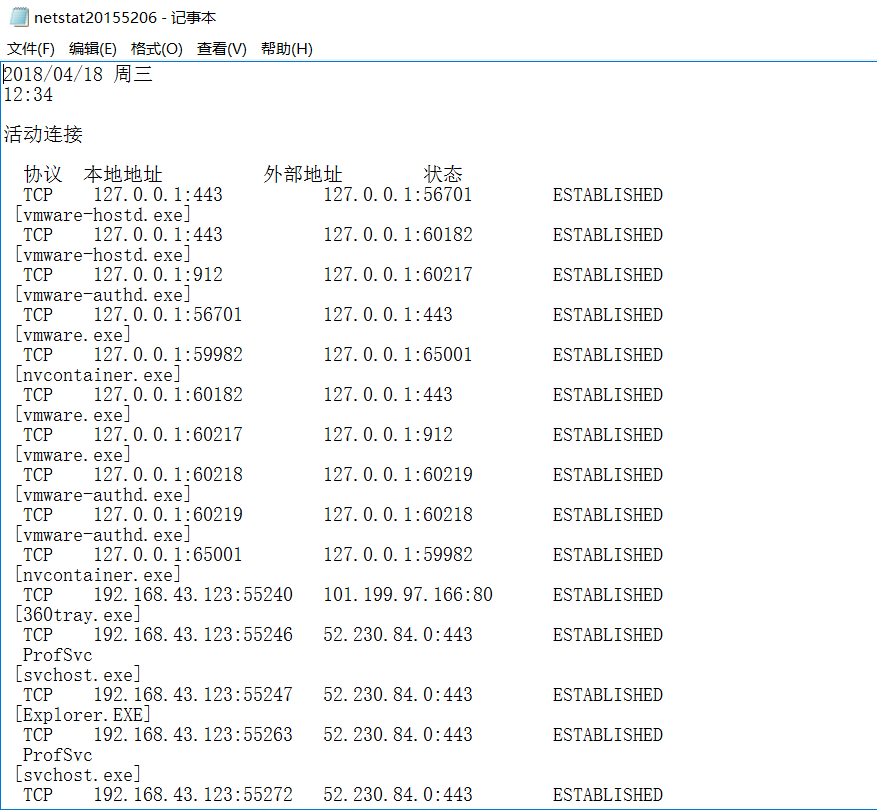
Sysinternals toolset
2.1Sysmon
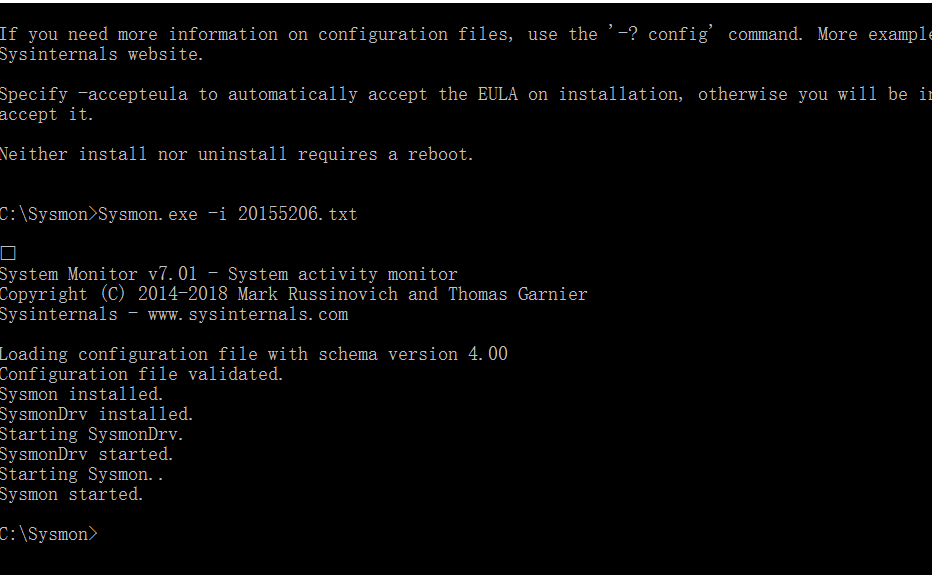
, Download sysmon
, decompress it, create a 20155206.txt file on the C drive, and enter
`
、 以管理员身份运行命令行,输入Sysmon.exe -i 20155210.txt`
, Open the control panel, search for event viewing, open the event viewer, the sysmon log is there, under the application and service log/Microsoft/Windows/Sysmon/Operational
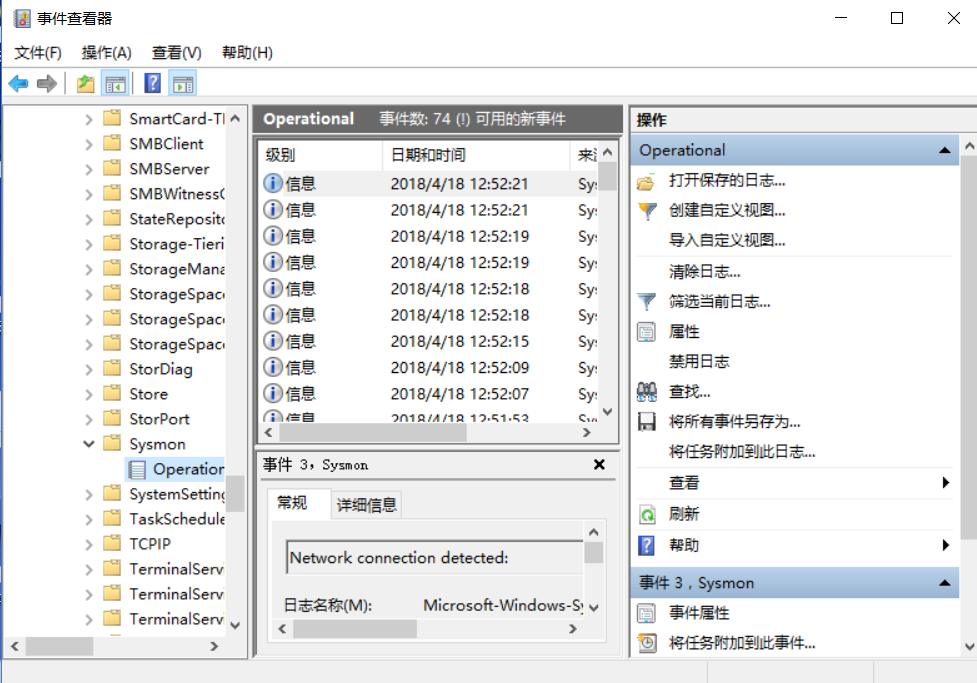
, View the log
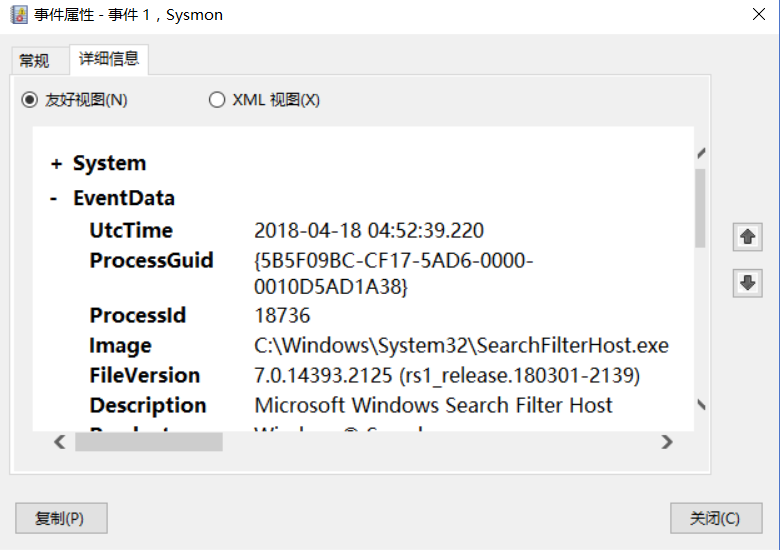
, searchfilterhost creation program
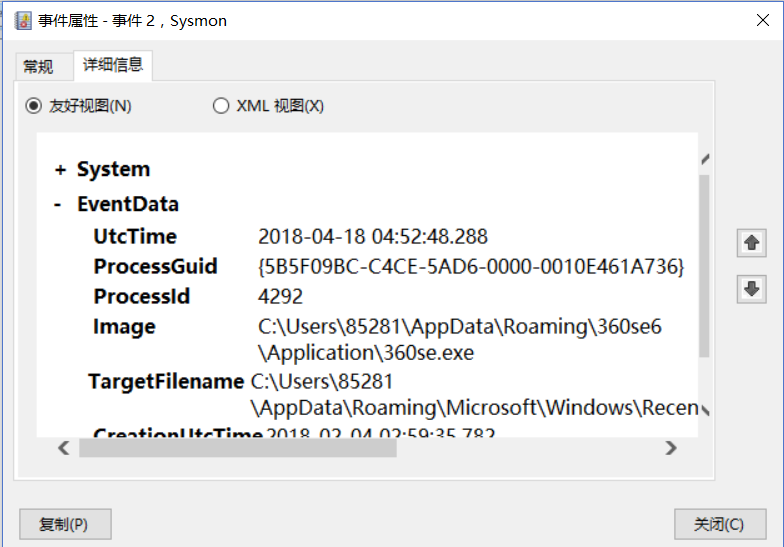
, Run the 360 browser
, Next, we mainly monitor ports 80 and 443
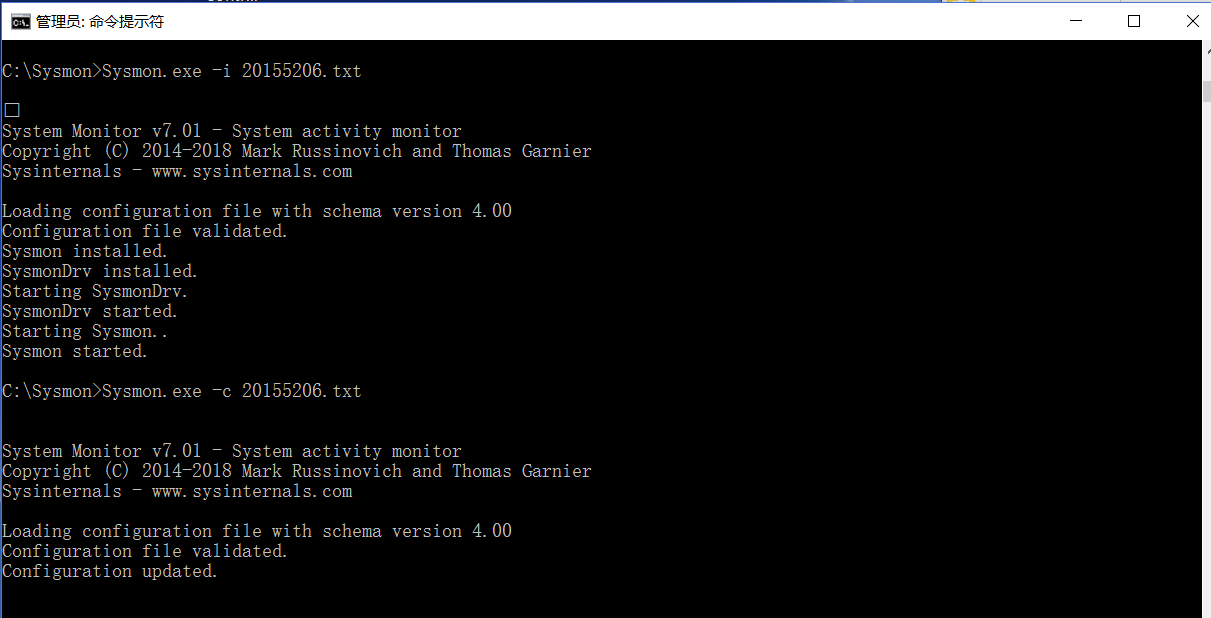
, use the following code to make changes to 20155206.txt, and then use sysmon.exe -c 20155206.txt to update.
`
`
, as shown
, view event viewer
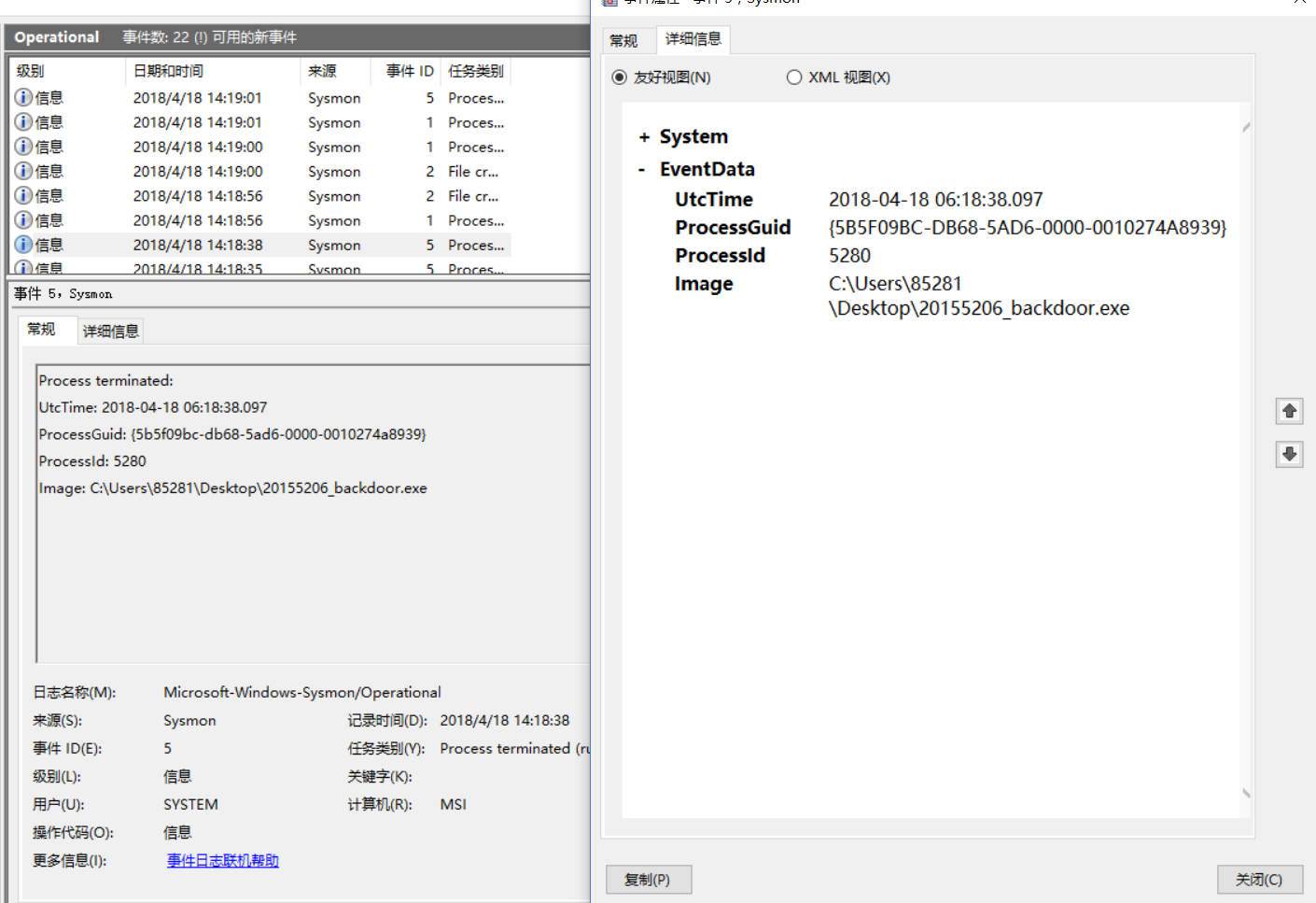
, 20155206_backdoor.exe runs
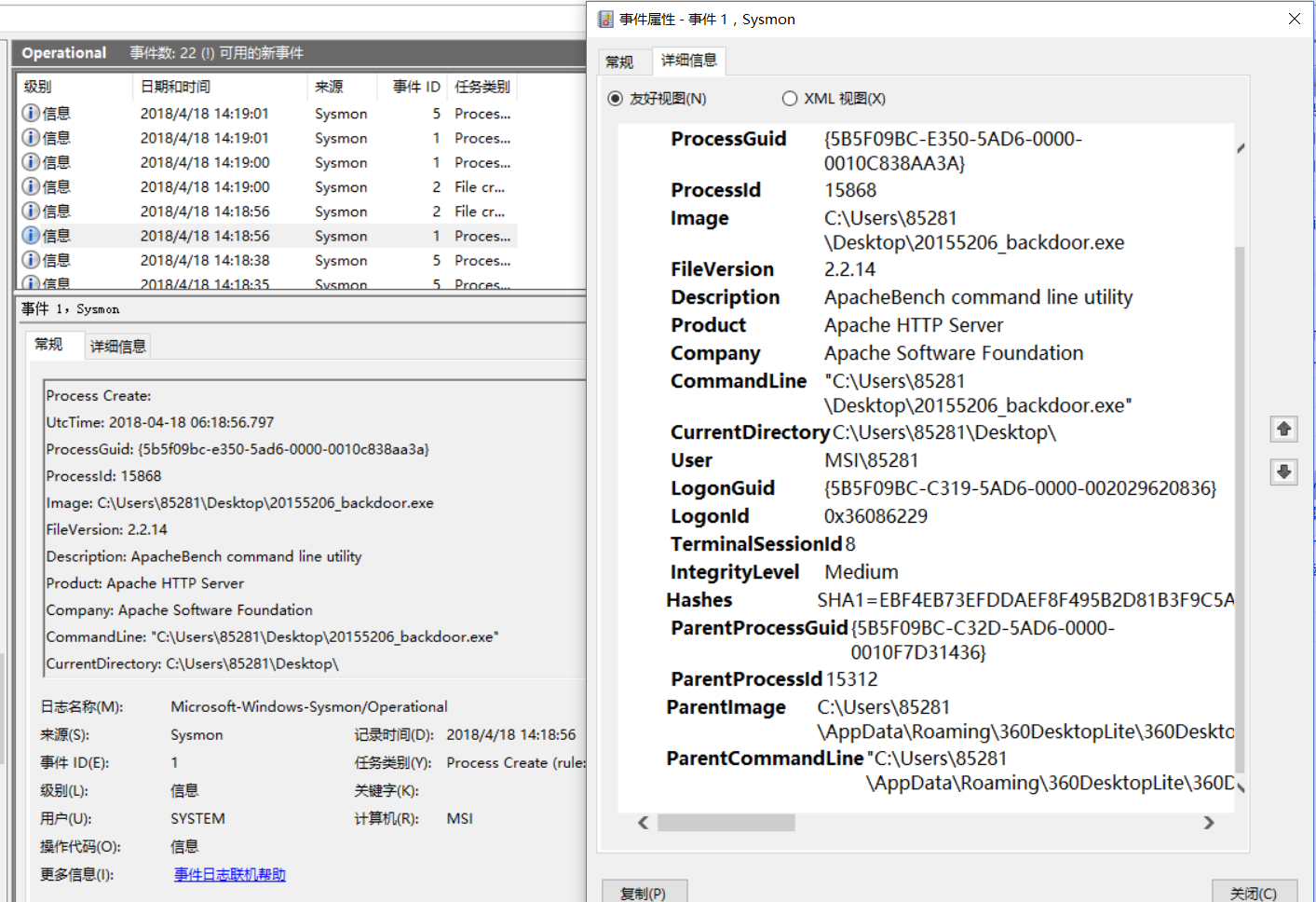
, ** 20155206_backdoor.exe is successfully connected back, but there is no destination port number and resource port number.
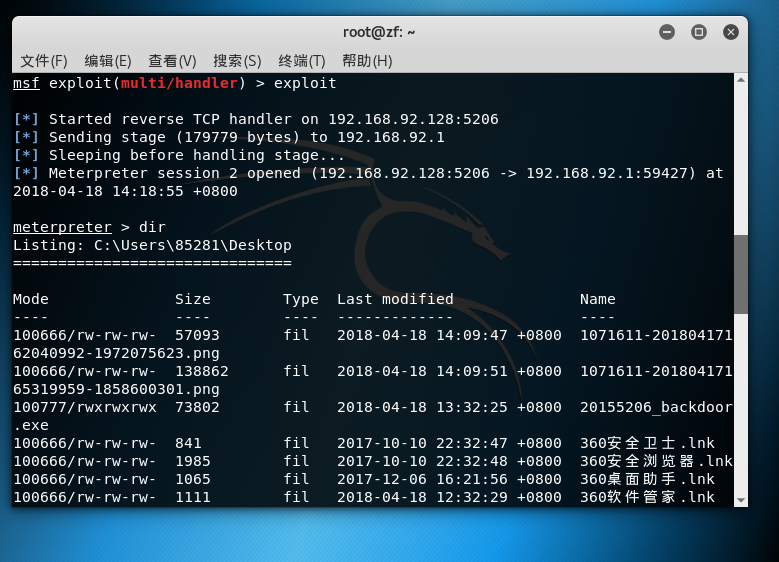
, The above picture is a screenshot after the dir operation is performed after the kali connection is successful**
2.2TCPview
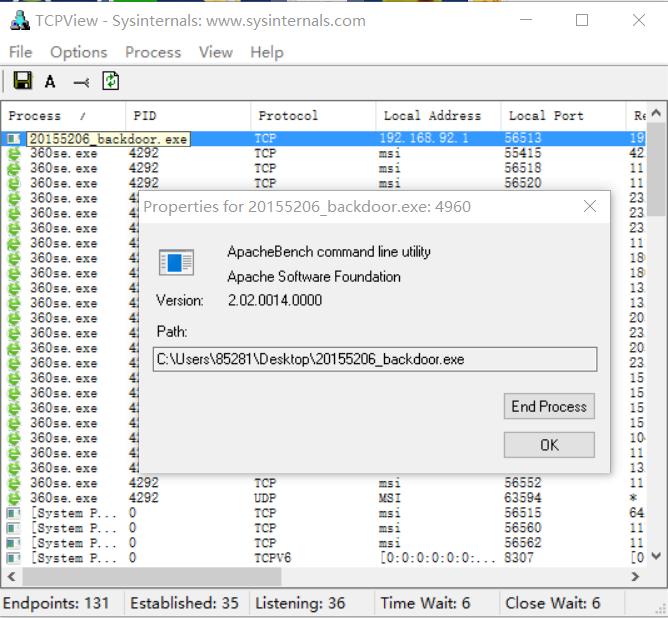
, Accessing information General localport is a backdoor for cifs, cifs is a newly proposed protocol that enables programs to access files on remote Internet computers and ask this computer to provide services. Obviously, if there is a program's LocalPort displayed as cifs, you should pay attention
Malware Analysis
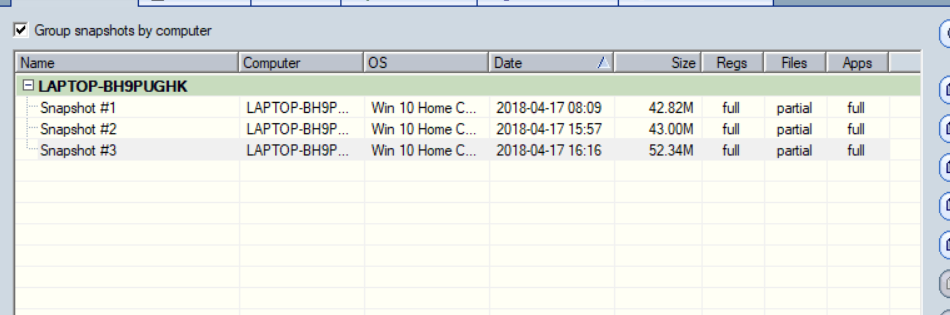
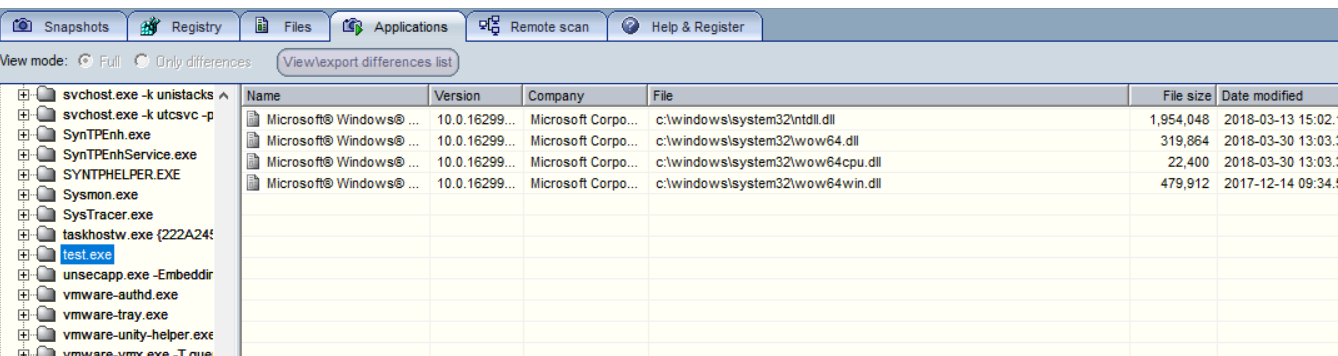
, first we download Systracer, install
it, then take a snapshot