1 User account
① What do the system do when we log in to Linux?
- First check /etc/password to see if there is an input account, if so, find the corresponding UID (user ID) GID (group ID), and read the main folder of the account together with the corresponding shell settings
- Check the password table; then Linux goes into /etc/shadow to find the corresponding UID and then checks whether the password just entered is the same as the password of this file;
- All OK, enter the shell control stage
- (If you want to back up the Linux system account, be sure to back up these two files /etc/password /etc/shadow )
②
/etc/password
file structure
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
Each line represents a user; : Divide a line into 7 segments, they represent
1. Account name such as root
2 Password The early UNIX system password is placed in this field, but the special effect of this file is that all programs can read it, which will cause the password to be easily stolen, because the password field is placed in the
/etc/shadow
, so X is filled in by default here
3.UID user identifier
UID=0
means system administrator; multiple system administrators can be set but this is not recommended;
1~499 (system account)
This range is the ID reserved for the system;
This range will have /nologin, so what does nologin mean?
The shell of the system account uses /sbin/nologin, and you cannot log in to the system at this time, even if a password is given.
The so-called "unable to log in" only means that the user cannot use bash or other shells to log in to the system, it does not mean that the account cannot use system resources. For example, in each system account, the print job is managed by the lp account, and the www server is managed by the apache account. They can all work on the system program, but they cannot log in to the host.
Sometimes some services, such as mail services, are mostly used to receive mail from the host, and do not require login. If an account tries to connect to my host to get a shell, we can deny it.
In addition, if I want to let a user with /sbin/nologin know that when they cannot log in to the host, they can create a new file /etc/nologin.txt and write the reason why they cannot log in in the file. When the user logs in, The contents of this file will appear on the screen.
Subdivision 1~99: System accounts created by distributions themselves
100~499: If the user needs a system account, the account UID that can be used
More than 500 (can log in to the account) for general users
4.GID (GroupID group ID)
/etc/group
file is similar to /etc/passwd, that is to make the group name correspond to this GID;
5. The basic information of the user is listed, and there is no special explanation for the meaning of this account.
6. The home folder, for example, the root account is /root; the user login will go to this folder by default; if you want to modify the home folder, you can modify this field; the default user home folder is /home/yourIDname
7.Shell ; the shell used by default
③
/etc/shadow
file structure
We know that the operation of many programs is related to permissions, and permissions are related to UDI/GID, so each program needs to read /etc/passwd to understand the permissions of different accounts; then the permissions of this file are set to -rw-r-- r--; the password is very insecure in the second field of passwd; it will be obtained by others; so it was developed to move the password to /etc/shadow;
: The division has 9 fields;
1. Account name
2. The password is encrypted; although it is encrypted, it may still be cracked, so this file can only be read by root;
3. Date of last password change
4. Number of days the password cannot be changed (compared to the third)
5. The number of days the password needs to be re-changed
6. The number of warning days when the password needs to be changed
7. Account grace time in the background of password expiration
8. Account Expiration Date
9. Reserved fields
What should I do if I forget the root password?
④/etc/group /etc/gshadow (省略)
2 Account Management
2.1 Add and delete users: useradd, related configuration files, passwd, usermod, userdel
1. Add user
adduser username
; this will create a user group with the same username by default;
adduser -u 700 -g users test3
-u custom UID
-g custom user group
-r
creates a system account; will not actively create a home folder
When we use the adduser username; we will create and modify many files by default; where do these default data come from?
Use the command
useradd -D
to view the default value

The above data is found in the file /etc/default/useradd;
(skip)
- set password passwd username
passwd [-l] [-u] [-S]
[-l] lock lock user password is added in front of the password field in /etc/shadow!
[-u] unlock user
[-S] View password-related parameters; for example, just -l; test LK 2017-01-04 0 99999 7 -1 (Password locked.)
shows that it is locked;
The command to view the detailed parameters of the password is also
chage -l username
Root users pay attention to passwd. When modifying someone else's password, you must add the user name, otherwise it will modify the root password.
- Modify some user parameters usermod [-cdegGlsuLU] username
usermod -L username lock user == passwd -l username
usermod -U username unlock user == passwd -u username
usermod -c username Modify user description information /etc/passwd fifth column information
-g : followed by the initial user group;
-G : followed by secondary user group
-l: modify account name
- userdel delete user
userdel -r username deletes the home folder as well
5 id Query user-related ID information
2.2 Adding and deleting user groups
id View user information
1.
groupadd [-g gid] [-r] User group name
-g specifies the GID
-r Create a new system user group.
2.
groupmod [-g gid] [-n group_name] user group
-g Modify GID -n Modify user group name
It is best not to change the GID at will
3.
groupdel [groupname]
4.gpasswd: user group administrator function
The function is to allow a user group to have an administrator. After this use, the administrator can manage which accounts can join/remove the user group.
example:
groupadd testgroup
create a new user group
gpasswd testgroup
gives the user group a password
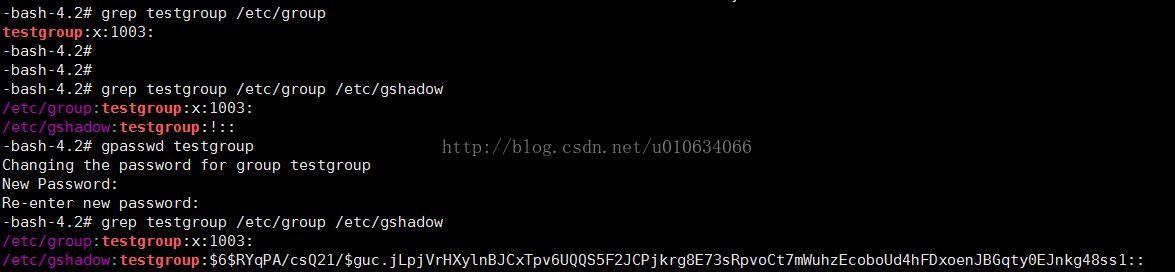
gpasswd -A test testgroup
sets the administrator of the user group to test
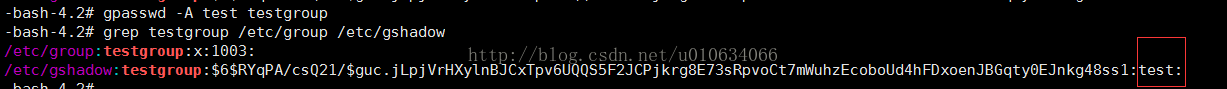
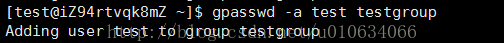
gpasswd -a test testgroup
log in to the test user; add test or other users to the testgroup group
Log in to the src user and execute this statement, prompting no permission
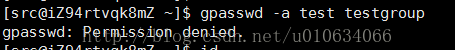
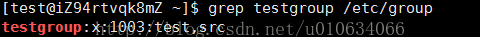
gpasswd [-A user1, ....] [-M user3, ...] groupname
The following is the
root
user has permission to execute
If no argument is given to give groupname a password in /etc/gshadow
-A Give the master control of groupname to the following user to manage (the administrator of the user group)
-M add some accounts to this user group
-r remove the password for this group
-R disable password
The following is the user group administrator has permission to execute
-a add a user to this group
-d remove a user from the user group groupname
5
newgrp [groupname]
In the above test, we also added the user test to the newly created testgroup1
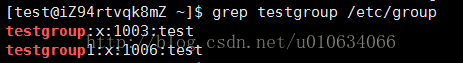
There are 2 groups in test; we can use newgrp to switch the current group; to get the permissions of the corresponding group
newgrp testgroup1
If the switch is successful, we use id to see
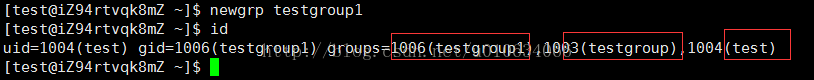
The first one that appears is the current group; you can see that there is a group name test; that is because centos adduser will create a user group with the same user name by default
example: