Before Dokcer was born, application packaging has always been a pain point for most R&D teams. At work, in the face of multiple services, multiple servers, and multiple environments, if you continue to package and deploy in the traditional way, it will waste a lot of time and energy.
After the emergence of Docker, it quickly became popular with six advantages: more efficient use of system resources, more efficient use of system resources, consistent operating environment, continuous delivery and deployment, easier migration, easier maintenance and expansion .
The basic commands of Docker can be called the internal strength of Docker. Only by practicing the internal skills, we will be smoother on the road of Docker learning, and will not lead to "going into the devil".
Next, I will start with the comparison with the virtual machine, in a practical way, to show you a better understanding, and to "play" Docker.
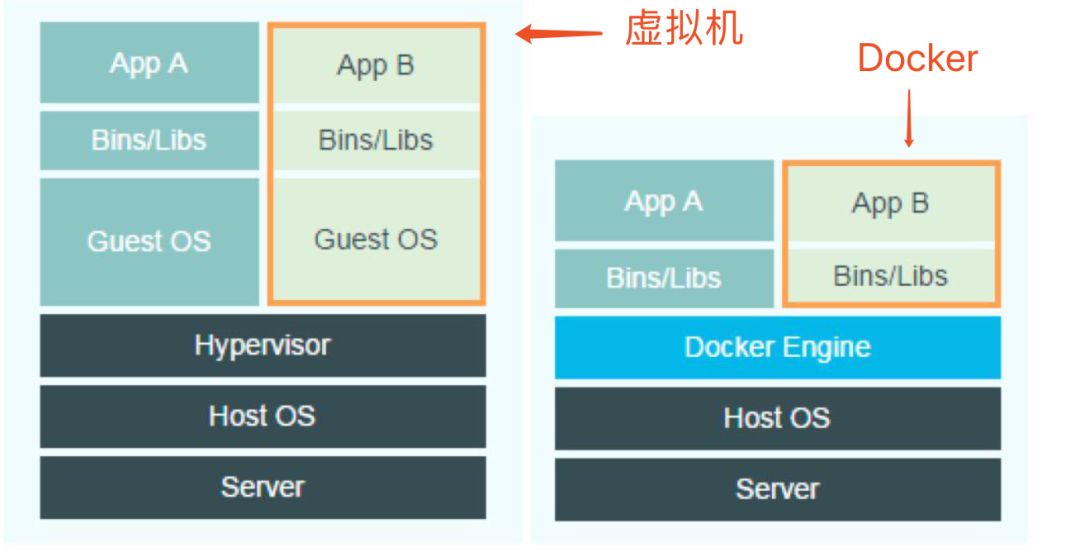
– Virtual machine on the left, docker environment on the right –
Server: physical machine server
Host OS: built operating system
Hypervisor: a virtual machine software, which can be virtualized after installation
Guest OS: virtualized operating system
Bins/Libs : Execute commands, tools
App A: Build software
Docker Engine: Skip the step of virtualizing the kernel and use the host kernel directly
From the picture, we can clearly understand that the virtual machine is more bloated than Docker.
Both virtual machines and containers require a physical machine and an operating system, but virtual machines have a Hypervisor layer and a Guest OS layer. But Docker does not have these two parts, only a layer of Docker Engine.
And each container shares the computer's hardware resources and operating system with the host. Then the resource consumption caused by the hypervisor does not exist on the container side. Therefore, compared with virtual machines, Docker has strong advantages. Of course, there are also certain disadvantages.
Advantage (eliminates the step of virtualizing the kernel)
- Save resources (CPU, memory)
-
- Start in seconds
-
- Lightweight solution (same server can start hundreds of dockers, but not hundreds of virtual machines)
- disadvantage
-
- Isolation and security are weaker than virtual machines (for example, if one of the containers "breaks" the kernel, all containers will not work properly)
-
- In some cases, the server will choose the kernel (eg. compile c++)
and for testers, what kind of convenience does Docker bring us?
- In some cases, the server will choose the kernel (eg. compile c++)
- establish a test environment
-
- Build various basic services
-
- Build a test execution environment (automated test script execution environment)
10. At the beginning, due to network reasons, when we download images, the speed is often very slow. So if you are slow to download images, you can try to configure a domestic accelerator to accelerate image download
- Build a test execution environment (automated test script execution environment)
- Log in to the Ali developer platform:
11. https://dev.aliyun.com/search.html - Click "Create My Container Image"
12.3. After registration/login, enter the Docker image repository and select the accelerator Tab
https://cr.console.aliyun.com/#/imageList - According to personal needs, select the OS running Docker, and modify the Docker configuration file as required.
Proceed as follows:
Modify the configuration file:
add the red part to the
save file . A
good memory is not as good as a bad keyboard. It is not enough to memorize the commands of Docker. You need to type and practice more so that you can master Docker more proficiently and deeply.
Download
the image View the downloaded image
We can see the Jenkins image just downloaded
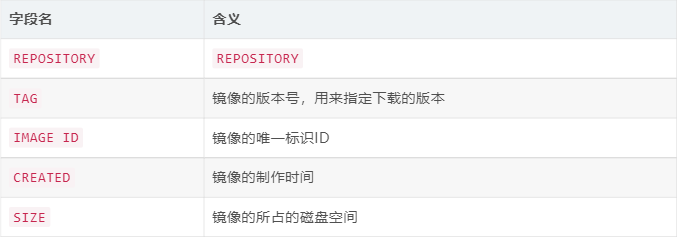
So, what does each of these fields mean?
Delete the mirror
We can see that the Jenkins mirror has been successfully deleted
Download the specified version of the mirror
At this point we can find that the TAG of the mirror is no longer latest but the version number we specified
Pack the mirror into a tar package
Load the packaged image
Add a tag number to the image
After tagging, you will find an image of the 3.6.0 tag version, but the image ID is the same as the original one
Then we deleted the image, found the prompt untagged, and the image was successfully deleted
. Change the name to the image
. Then we can see that there is an additional image called testjenkins, but the image ID is the same as the original.
Push the image to the image warehouse
container Running command parameters
Container management command parameters
Next, we continue to use Jenkins to conduct a practical exercise
docker ps is also a command we commonly use. The following is the startup container information displayed after docker ps, each of which has its own meaning
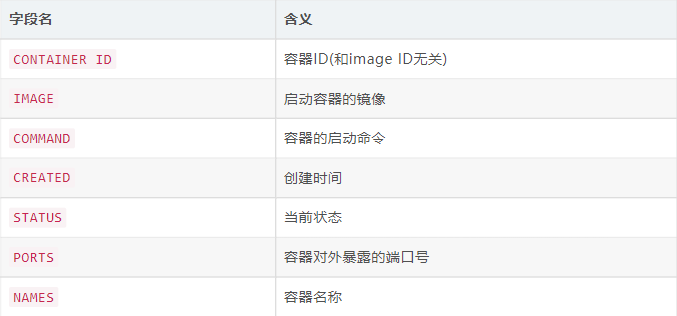
CONTAINER ID: Container ID (not related to image ID)
how to delete this started container? Is it possible to rm directly like the mirror image?
As we can see from the figure, if you delete the running container directly, an error will be reported, you need to stop first and then delete
Or directly
We can see from the picture that although the container is started, it can still be deleted directly using docker rm -f
. When docker ps is executed, we can see that two port numbers are displayed under the PORTS field. What does a port number do?
In fact, these two port numbers are the port numbers that the container deliberately exposes to the outside world. We can make a link between the port number inside the container and a port number of the host through port mapping. In this way, we can access or operate the container through the port number.
How to specify the port number? It is to use the -p parameter
to point the 8080 port of the host to the 8080 port of the container, so that we can access Jenkins on the 8080 port of the host.
During the startup process, we may encounter various problems, we How to locate the problem?
Of course, use the view log method
After learning this, some students may have doubts. If the docker hangs up, what should be done with the data generated in the docker, and how should the data be saved?
Next, we need to understand how docker performs data persistence Woolen cloth?
When we start the container, we add the data mount parameter -v host_path:container_path, and docker can synchronize the data of the container and the host by means of data mounting.
Next, we will use the actual method. , you can see how docker implements this function
1. Start Jenkins, add the -v mount volume parameter
Note: Mount permission: sudo chown -R 1000:1000 /home/docker/jenkins
2. Use docker exec -it myjenkins bash Enter the jenkins container that was just started, and cat /var/jenkins_home/secrets/initialAdminPassword This step is to find the startup password of jenkins
3. Enter the password and enter the Jenkins page to create a job.
4. Delete the container, re-execute the previous command, restart Jenkins, enter the page, and find that the job is not lost because the container was deleted
Note: If the container cannot be successfully started and the log indicates a permission problem, add -u 0 to the startup command
docker exec -it {container name} bash
enters the container, exec means run a command in the container. If using bash and specifying -it will open the container's shell interaction
docker cp {container:name}:{container_path} {host_path} copy a file on the host to the container
When some containers are started, we need to add some initial parameters to them, such as mysql, we need to add some initial accounts and passwords to them. How does docker operate in this situation? Let's move our little hands and practice
- Start the mysql container, pay attention to add -e to pass parameters
-
- Connect to the database through the database connection tool
- The host needs to fill in the ip address of the host machine. Password is what we set at the beginning.
- The port number fills in the port number of the mapped host
- Create a table in the database
- delete the container and restart
-
- Entering the mysql path in the container you just created, you will find the table you just added. This is the data persistence function of the container.
Let's think about another problem next, because the container is isolated.
If the containers are linked to each other in what way?
Here we will introduce another parameter --link. The function of this parameter is to inject the network information of one container into another container. The
old method, we still use testlink to experience this function
. 2. Start mariadb
3. Start tesklink, the information of mariadb is injected into the testlink container
4. Check the log, you can see that the connection to mariadb is successful
- Entering the mysql path in the container you just created, you will find the table you just added. This is the data persistence function of the container.
A thought question, if three containers need to be connected, what method should be used?
The answer is: –env because in docker, –link is configured through environment variables.
Now the architecture of many websites is separated from the front and back ends. In this case, how should we use docker to start the front end and the back end separately and communicate with each other? We can use the following command
--net=container:conan: The container created in this way will not create its own network card and configure its own IP, but share the IP and port range with a specified container.
View docker information
Obtain container/image metadata
Above, we have learned the concept of docker through actual combat, and are familiar with some basic commands of docker. After reading the article, we should be familiar with the practice. Next time, I will take you through 3 practical exercises to monitor selenium, prometheus+grafana, and mysql, and show you how to use docker.
Docker and K8S combat skills are also the focus of BAT test development interviews