20155305 "Network Confrontation" Information Collection and Vulnerability Scanning
experiment procedure
Information collection
- whois
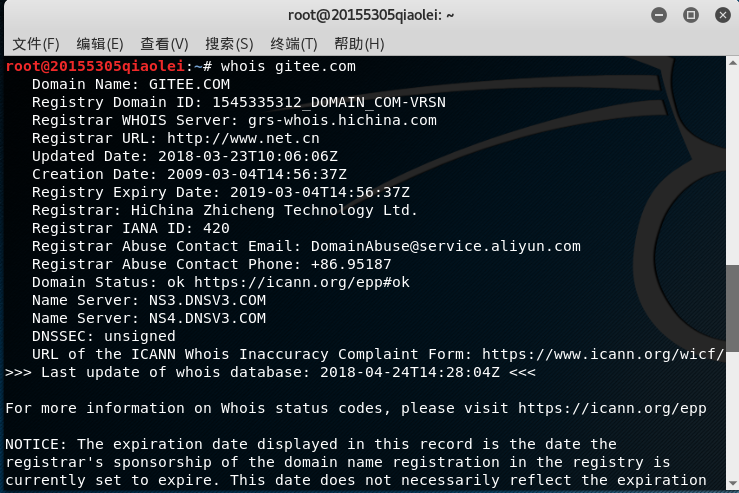
Enter in the kali terminal whois 网址to view the registered company, service, registered province, fax, telephone and other information.
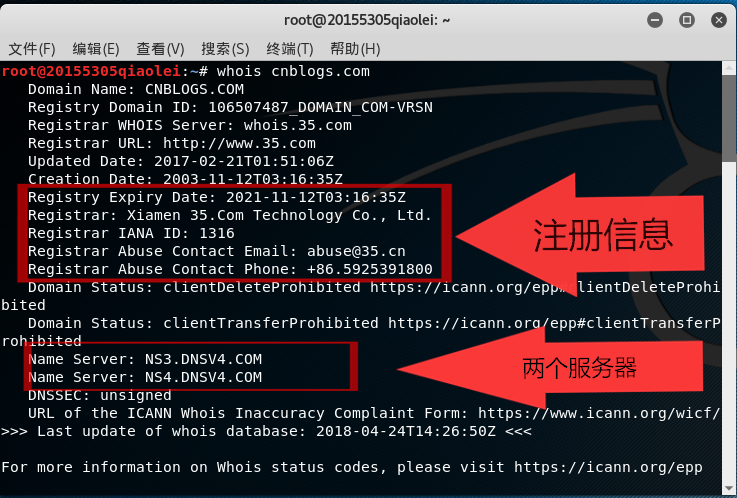
The following is the same
- dig 或 nslookup
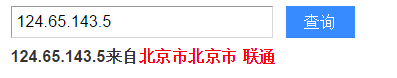
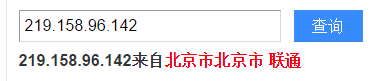
dig 网址Enter or in the kali terminal nslookup 网址to view the IP address corresponding to the URL.
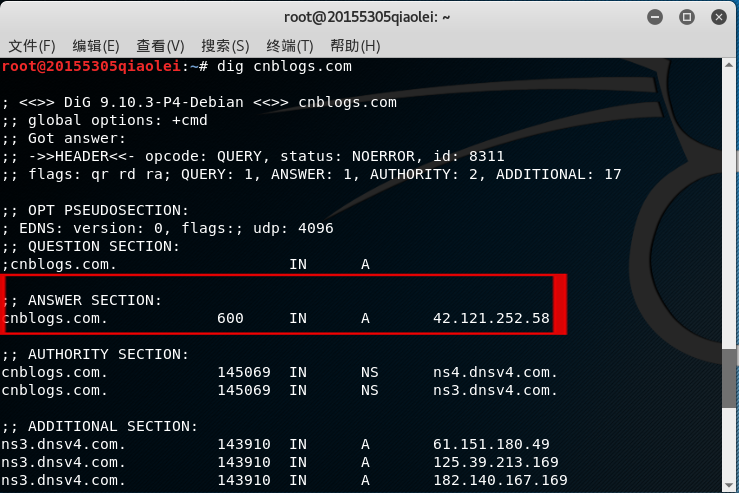
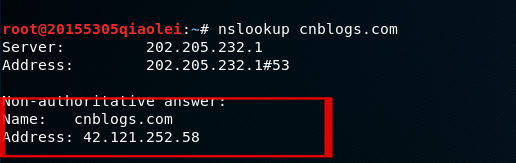
Then you can search for the specific geographic location of the IP address in Baidu.
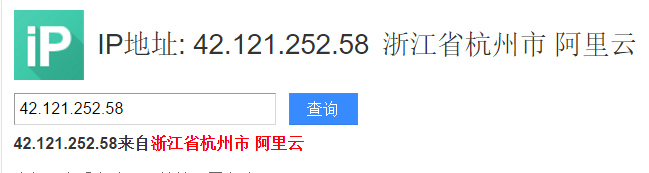
- Tracert Routing Probe
The tracert command will display the ip that the data packet passes through, and you can query these routes or the geographic location of the machine through ip.
Entering the Tracert IP address under my host Windows 10 shows several ip's that have been walked through.
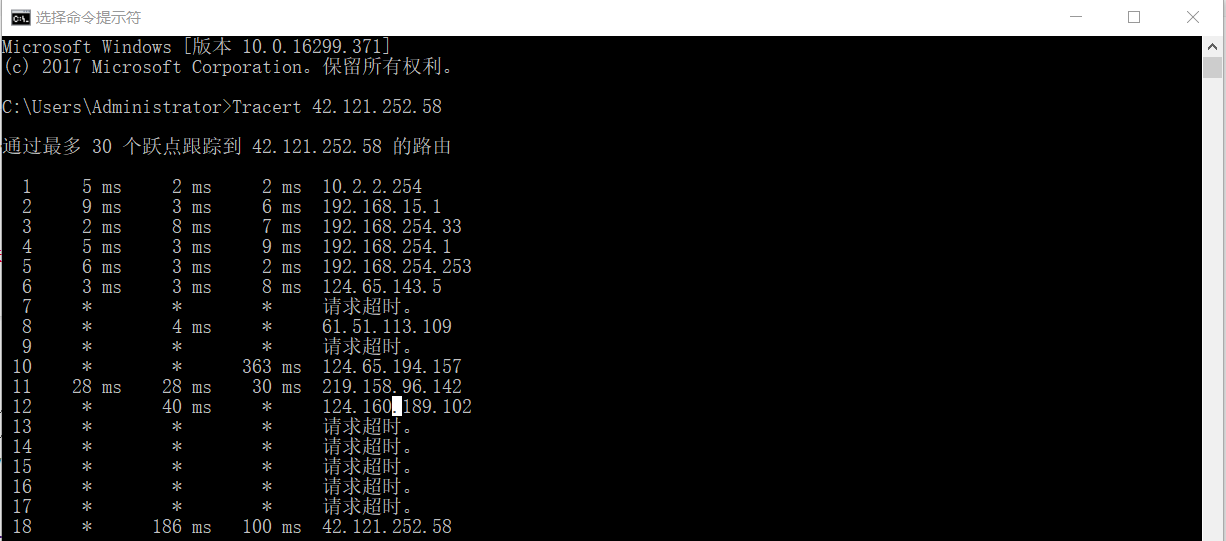
The routes or geographic locations corresponding to these IPs can be queried on the network.
But under Kali, traceroute IP地址there is only one gateway
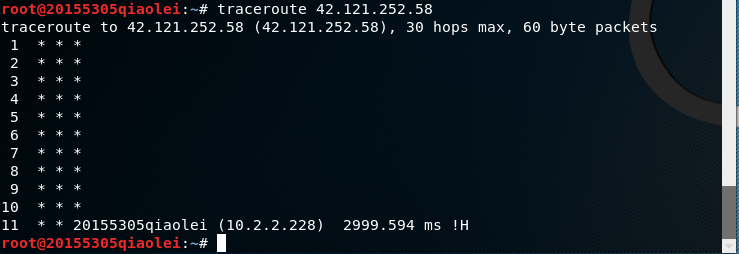
After I understand it, I feel that the reason is that the message returned by the virtual machine network traceroute cannot be mapped to the source IP address, source port, destination IP address, destination port and protocol, so the message cannot be routed back in reverse.
- search engine query
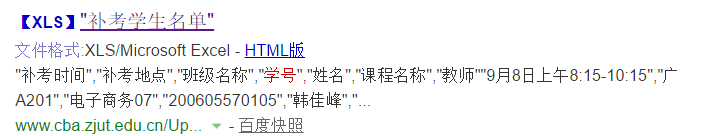
Enter in Baidu's search bar filetype:xls 关键字 site:edu.cnto search for URLs with xls format files including keywords.
nmap scan
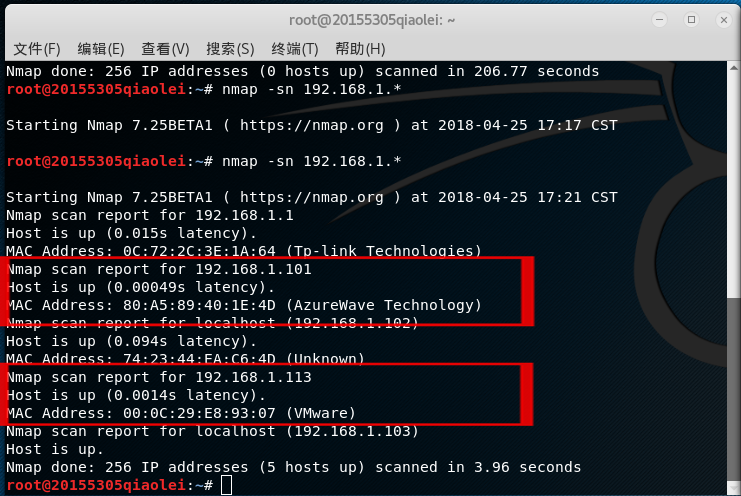
Enter scan surviving hosts under the Kali terminal
nmap -sn IP地址, you can scan a host or a whole network segment of hosts, I scanned an entire network segment including my Win 10 host and xp virtual machine, and got The following results:
Scan to my win 10 host and vm virtual machine win xp
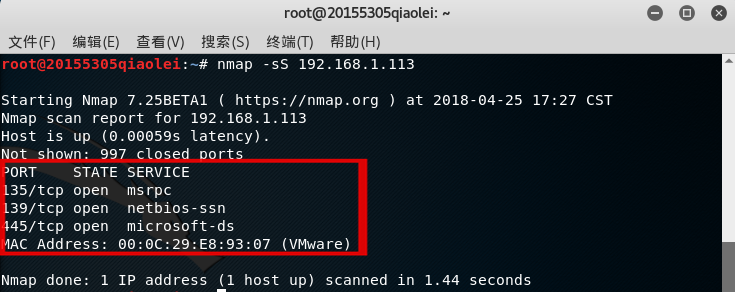
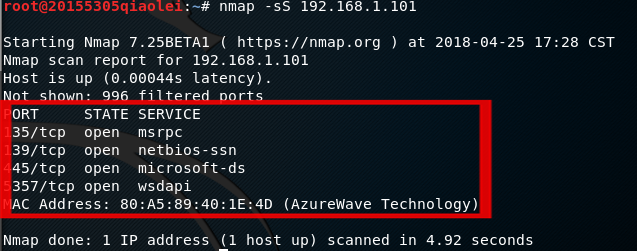
- In the Kali terminal, enter
nmap -sS IP地址the open tcp port that can scan the target host,-sSindicating that it belongs to tcp syn scanning.
Scanned the virtual machine xp system and the host win 10 system respectively, and found the status of different tcp ports and the services provided
- Enter under the Kali terminal to scan UDP ports, which
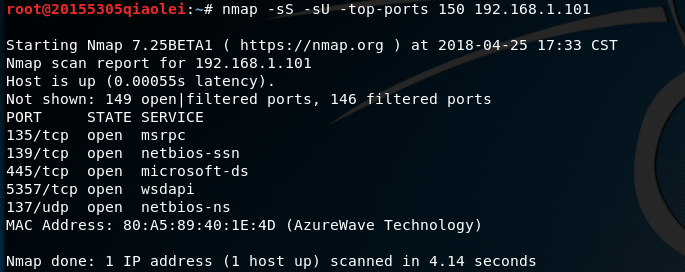
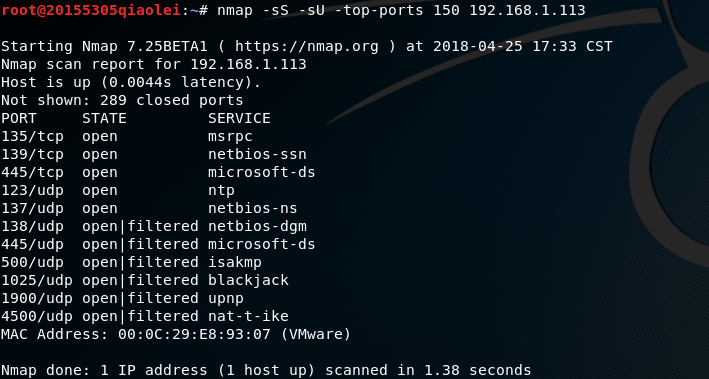
nmap -sS -sU -top-ports 150 IP地址means to scan the 150 most likely open ports for tcp and udp respectively.-sU-top-ports 150
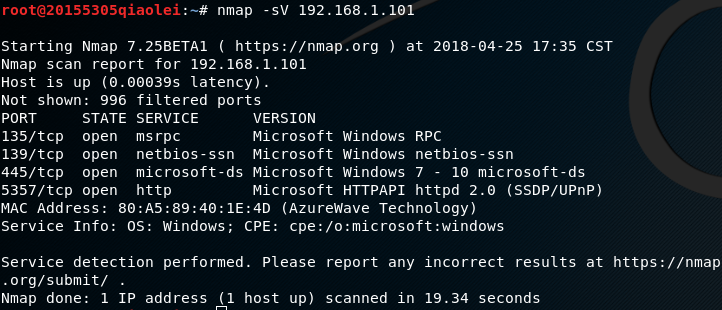
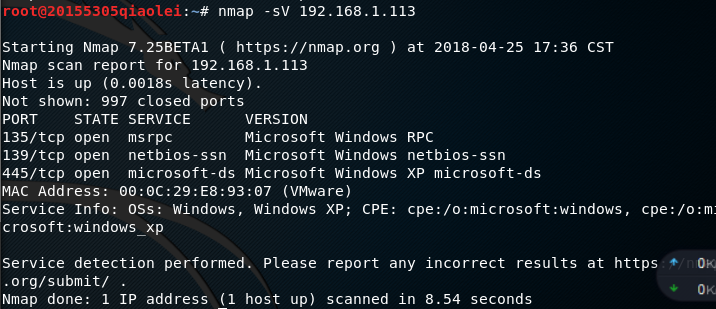
nmap -sV IP地址Enter the service version of the detection target host under the Kali terminal .
It can be seen that the service version of the win 10 host and the win xp virtual machine is very different. It can be speculated on the system and system version used.
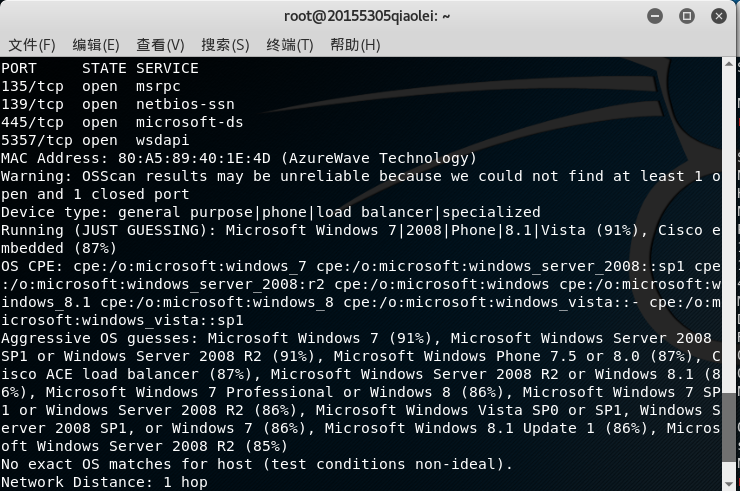
nmap -O IP地址Enter the operating system of the detection target host under the Kali terminal .
The operating system of win xp is scanned very well
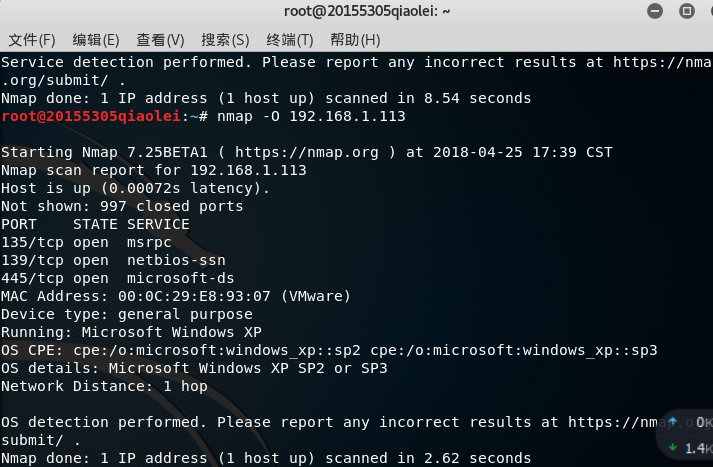
Win 10 is not so easy
Vulnerability Scan
- openvas configuration (re-enable the kali virtual machine given by the teacher)
Enter in Kali openvas-check-setupto view the installation status of openvas:
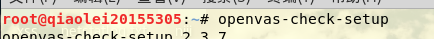
Check and find an error:
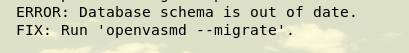
We can solve the error by entering the command according to the prompt
openvas-check-setup
openvasmd --migrate
openvas-manage-certs -a
openvas-manage-certs -a -f
openvasmd
openvas-check-setupEnter openvas-check-setupthe command again, and you can see that the openvas installation is successful.
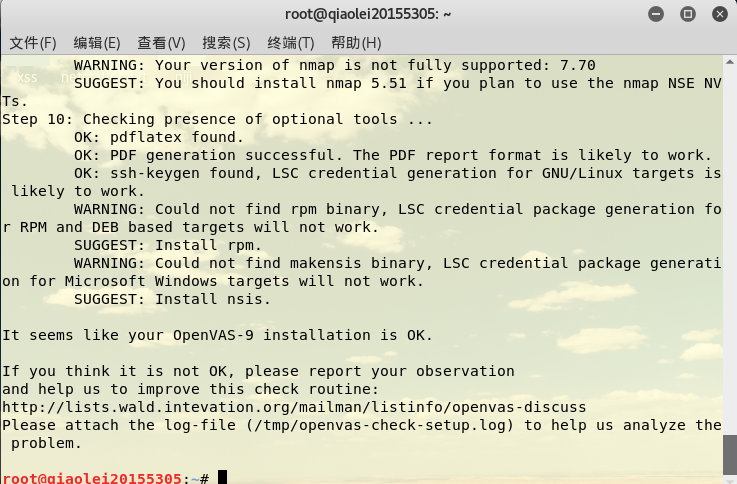
Enter openvasmd --user=admin --new-password=20155305the command to add a user account and password.

Enter to openvas-startopen openvas. will automatically jump to the pagehttps://127.0.0.1:9392
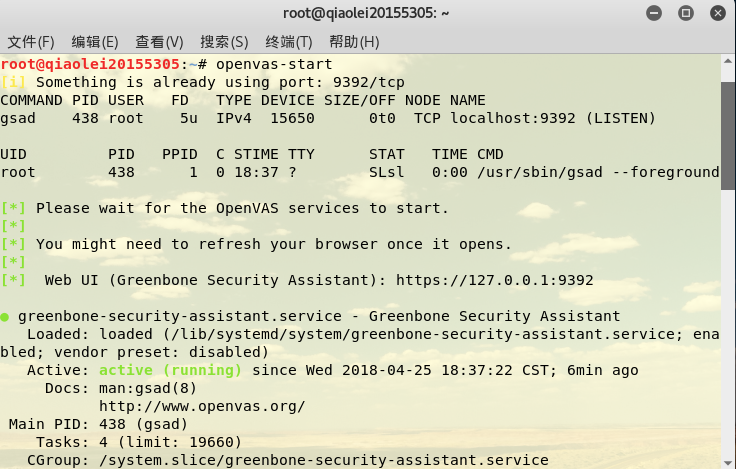
When opening the home page for the first time, an error such as the link is not safe, you need to open Advanced, click the lower left corner, and set https://127.0.0.1:9392 as a trusted site, and you can open it normally.

- Scan target hosts
The login interface has automatically displayed the account we just added, enter the password, click login to jump to the interface with many scanning tasks.
Select Tasks under the scan menu, you can see the following results
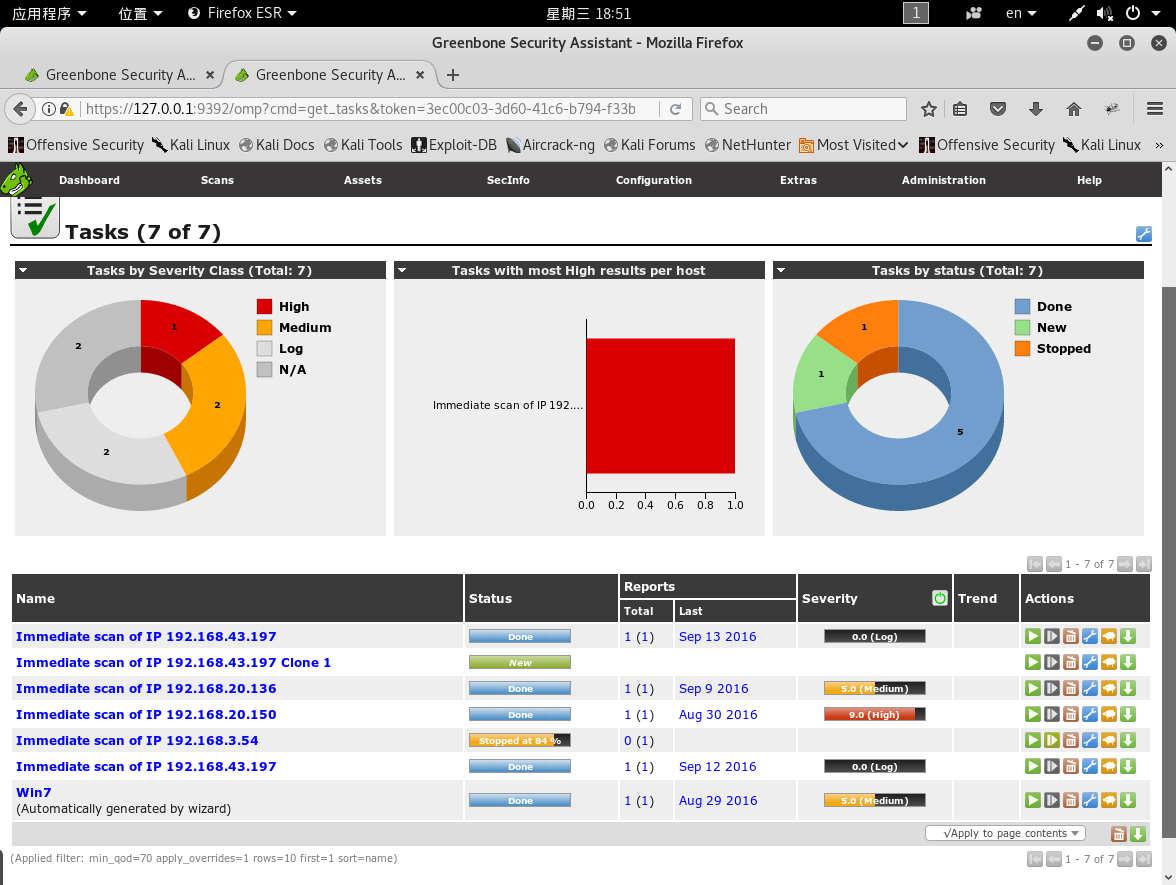
Select task wizard under the Wizard (a purple icon) menu, enter the IP of the target host in the scan bar, and start scanning the target host.
First look at my win 10 host is medium after scan is complete
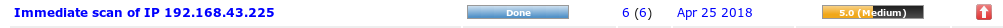
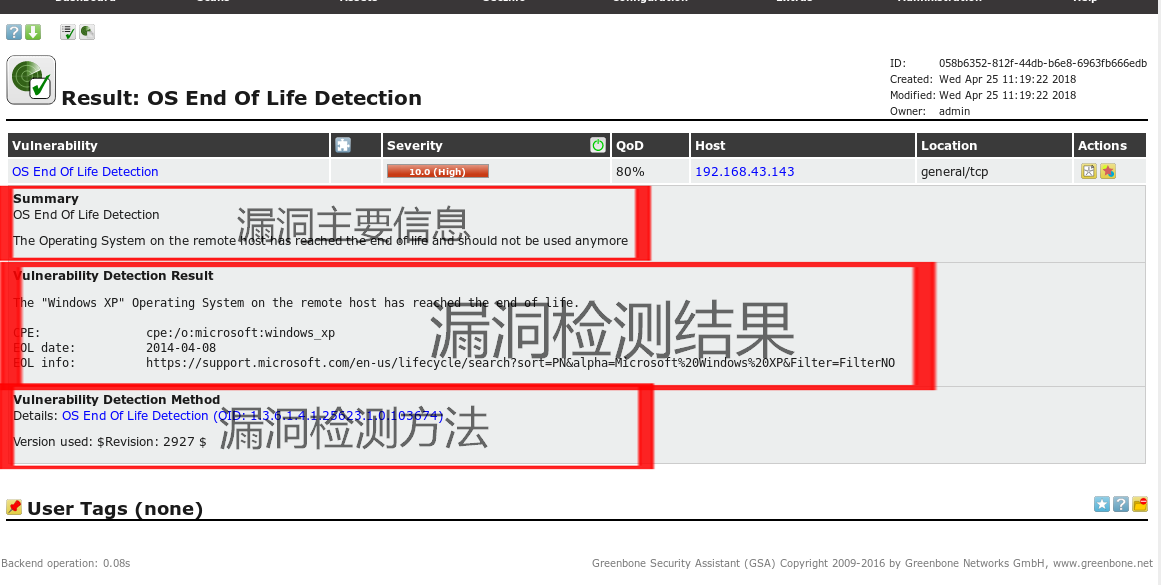
When the scan is completed, the severity of the win xp vulnerability used in the last experiment is already the highest level of 10.0 (it is indeed a lot of vulnerabilities and it is easy to be broken haha)

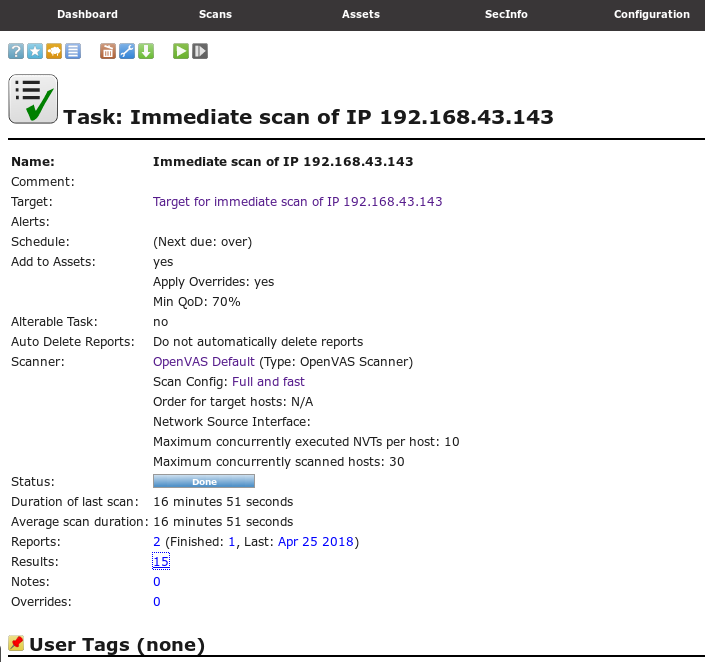
At this time, we click on our scan results to open the result
You can view an advanced vulnerability of the scanned target host. And you can see the relevant ports of all vulnerabilities (the port of this advanced vulnerability is general/tcp)
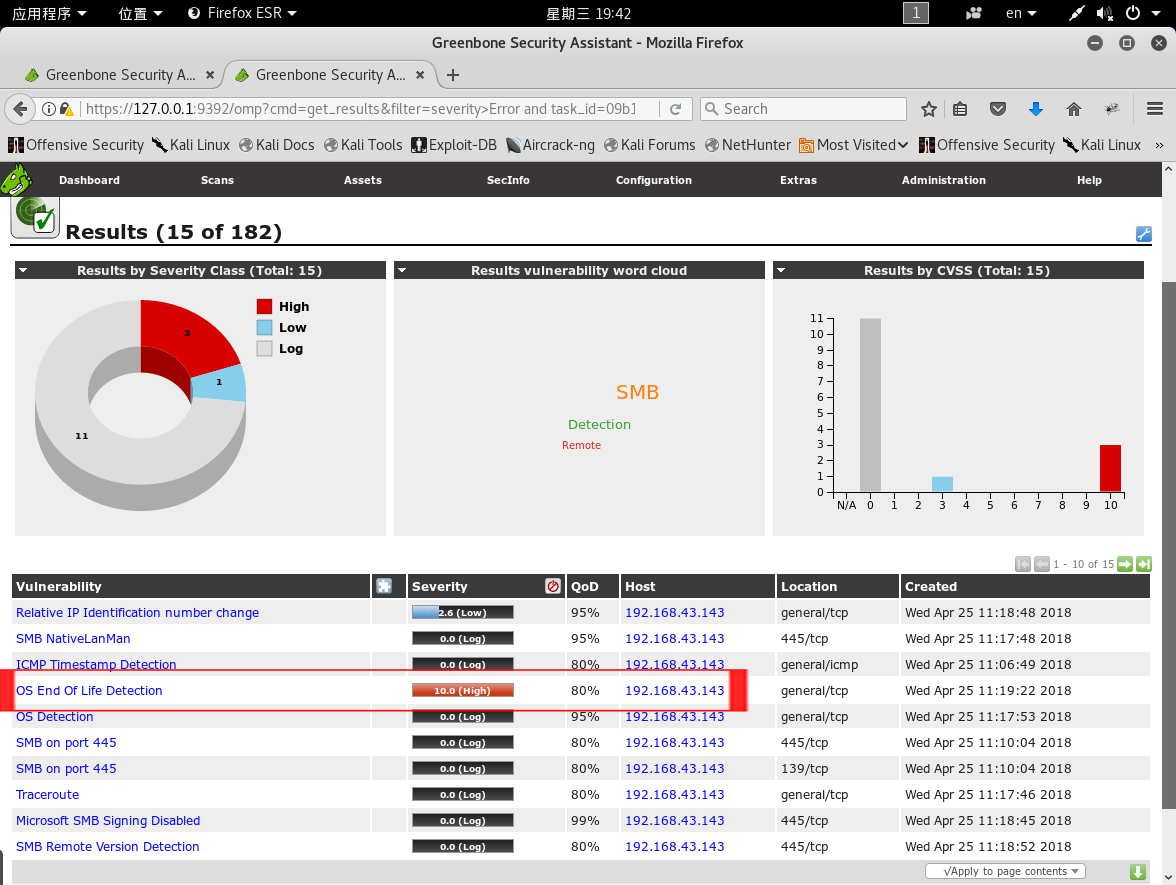
Click the vulnerability name to see the specific information of the vulnerability.
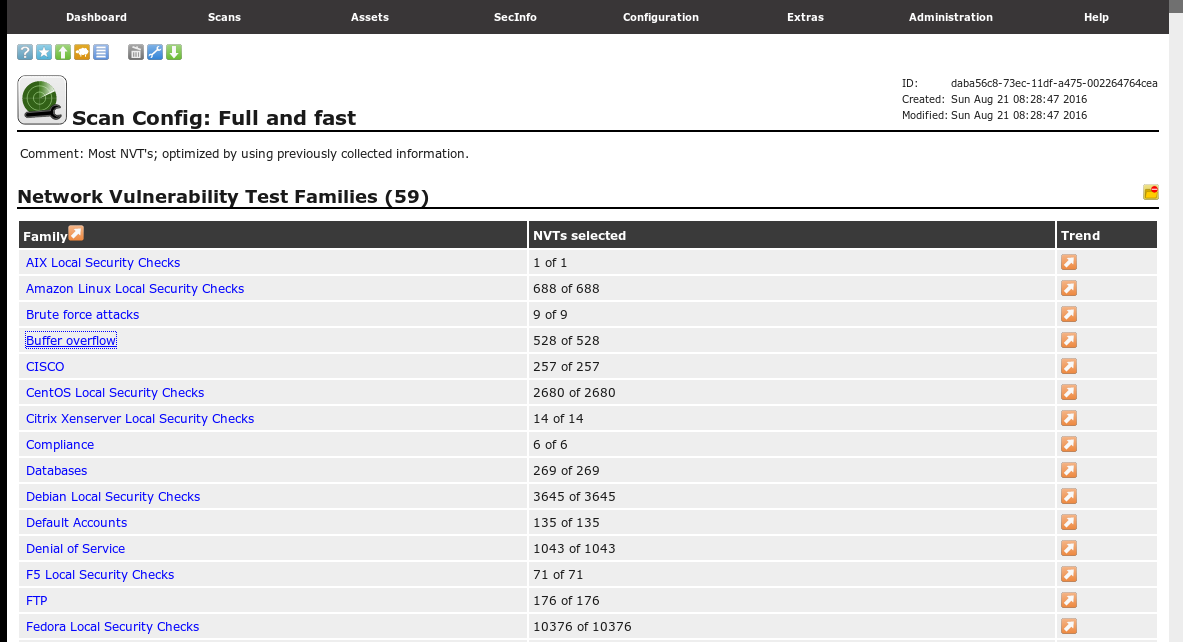
full and fastOr click to view when entering the target machine scan information
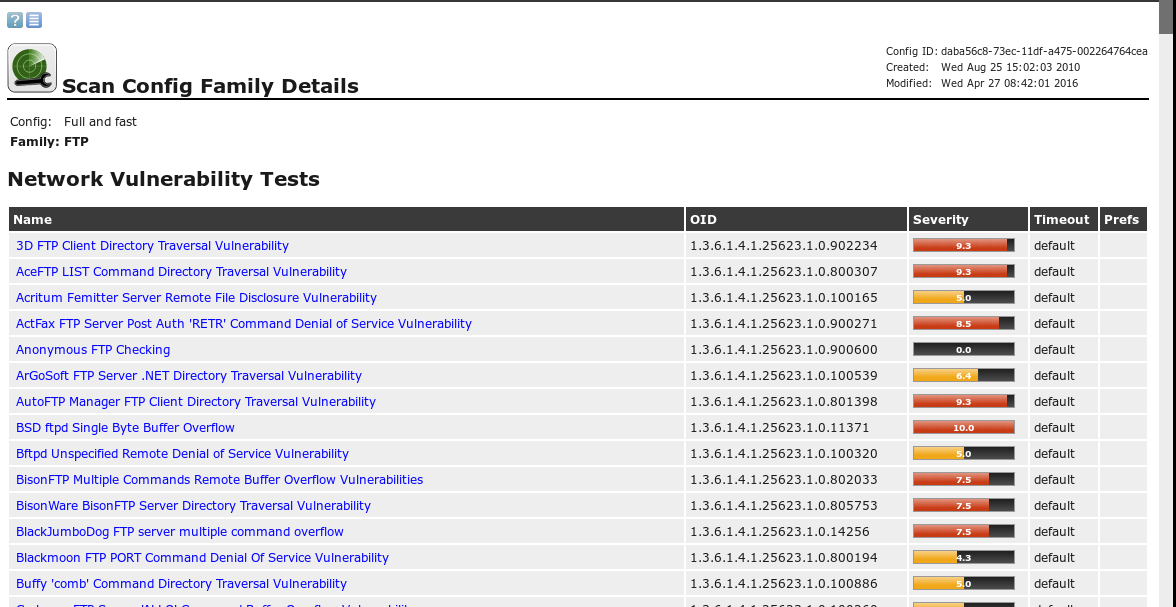
Select FTP to go in to view detailed information
- Close openvas.
Experiment summary and experience
This time, the experiment is relatively easy to follow the steps, and there are no special problems, except that the teacher's kali has to be changed when the vulnerability scanning needs to be installed. Rest assured, the focus of this experiment is to learn to use various scanning techniques. For us, it is not only to learn how to scan, but also to learn how to analyze the results of scanning. From the scan results, English is really super important, otherwise I can't understand all kinds of things. My level can only look up word translations while doing experiments. Finally, happy labor day haha