1. The basic concepts of HTTP and HTTPS
HTTP (HyperText Transfer Protocol: HyperText Transfer Protocol): It is the most widely used network protocol on the Internet. It is a standard for client and server requests and responses (TCP), used to transfer hypertext from the Web server to the local The browser's transmission protocol , which can make the browser more efficient and reduce network transmission.
HTTPS (HyperText Transfer Protocol Secure: HyperText Transfer Protocol Secure): An HTTP channel with security as the goal, that is, an SSL layer is added to HTTP. The security foundation of HTTPS is SSL, so SSL is required for the details of encryption. The main purpose of HTTPS development is to provide identity authentication for website servers and protect the privacy and integrity of exchanged data.
Second, the difference between HTTP and HTTPS
1. The HTTPS protocol requires a CA (Certificate Authority) to apply for a certificate. Generally, there are fewer free certificates, so a certain fee is required.
2. HTTP is a hypertext transmission protocol, information is transmitted in plain text, and data is not encrypted, while HTTPS is a secure SSL encrypted transmission protocol.
3. HTTP and HTTPS use completely different connection methods, and the ports used are different. HTTP is port 80 and HTTPS is port 443.
4. The HTTP connection is very simple and stateless . The HTTPS protocol is a network protocol constructed by the SSL+HTTP protocol that can be used for encrypted transmission and identity authentication. It is safer than the HTTP protocol.
Three, the working principle of HTTP
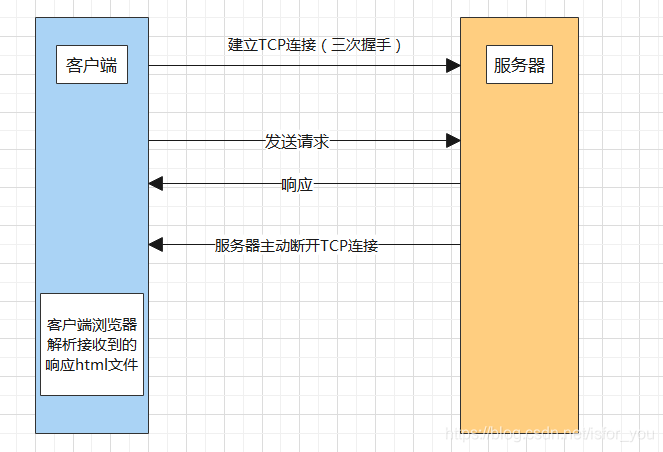
1. The client establishes a TCP connection with the server (three-way handshake)
2. After the connection is successful, the client sends a request to the server
3. The server responds after receiving the request sent by the client, and sends the response information to the client
4. The server After sending the response information, the TCP connection will be disconnected, so HTTP is stateless, and the next visit will not know the process of the previous visit.
5. The client receives the response information, the browser parses it, and parses the html file After rendering a web page on the browser
Fourth, the working principle of HTTPS
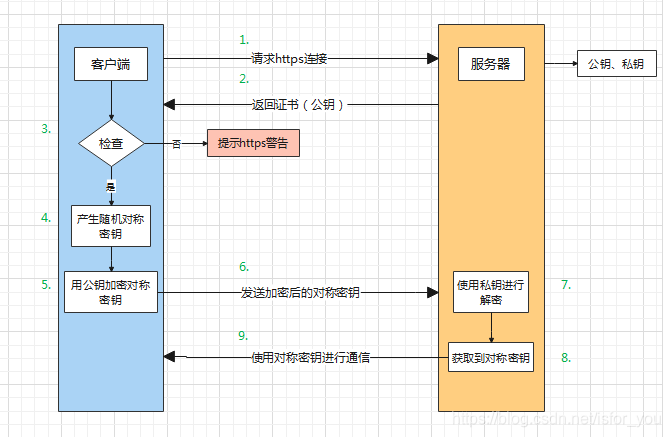
1. The client initiates an HTTPS request
The user enters an https website in the browser, and then connects to port 443 of the server.
2. Send the certificate
The server using the HTTPS protocol must have a set of digital certificates. This set of certificates is actually a pair of public and private keys. The public key is like a lock, and the private key is a key. Only this private key can open the public key. If other people can’t open it, they won’t be able to see the content inside.
The server sends the certificate to the client. This certificate is actually a public key, which just contains a lot of information, such as the issuing authority of the certificate, expiration time, and so on.
3. The client resolves the certificate
This part of the work is done by the TLS of the client. First, it will verify whether the public key is valid. If an abnormality is found, a warning box will pop up, indicating that there is a problem with the certificate.
4. Generate a random key
If there is no problem with the certificate, then generate a random symmetric key
5. Encrypt the symmetric key
The public key encrypts the symmetric key, as mentioned above, the random value is locked with a lock, so that unless there is a key, the locked content cannot be seen.
6. Transmit encrypted information
The purpose of sending the encrypted symmetric key to the server is to let the server obtain the symmetric key, and then the communication between the client and the server can be encrypted and decrypted by this symmetric key.
7. The server decrypts the information
After decrypting with the private key, the server obtains the symmetric key passed by the client, and then encrypts the content symmetrically through the key. The so-called symmetric encryption is to mix the information with the symmetric key through a certain algorithm. Unless you know the symmetric key, you can't get the content, and both the client and the server know this key, so as long as the encryption algorithm is strong enough and the symmetric key is complex enough, the data is safe enough.
8. Transmission of encrypted information
This part of the information is the information encrypted by the server with the symmetric key and can be restored on the client.
9. The client decrypts the information
The client uses the previously generated symmetric key to decrypt the information transmitted from the service segment, and then obtains the decrypted content. Even if the third party listens to the data during the whole process, it is helpless.
Five, the advantages and disadvantages of HTTPS
1. Advantages:
(1) Use the HTTPS protocol to authenticate users and servers to ensure that data is sent to the correct client and server;
(2) The HTTPS protocol is a network protocol constructed by the SSL+HTTP protocol for encrypted transmission and identity authentication. It is safer than the http protocol. It can prevent data from being stolen or changed during transmission and ensure the integrity of the data.
(3) HTTPS is the most secure solution under the current architecture. Although it is not absolutely secure, it greatly increases the cost of man-in-the-middle attacks.
(4) Google adjusted its search engine algorithm in August 2014, and stated that “compared to the same HTTP website, a website that uses HTTPS encryption will rank higher in search results”.
2. Disadvantages:
(1) The HTTPS protocol handshake phase is relatively time-consuming, which will extend the page load time by nearly 50% and increase the power consumption by 10% to 20%;
(2) HTTPS connection caching is not as efficient as HTTP, which will increase data overhead and power consumption, and even existing security measures will be affected as a result;
(3) SSL certificates require money. The more powerful the certificate, the higher the cost. Personal websites and small websites are not necessary and generally won’t be used.
(4) SSL certificates usually need to be bound to an IP, and multiple domain names cannot be bound to the same IP. IPv4 resources cannot support this consumption.
(5) The encryption scope of the HTTPS protocol is also relatively limited, and it has little effect on hacker attacks, denial of service attacks, server hijacking, etc. The most important thing is that the credit chain system of SSL certificates is not secure, especially when some countries can control CA root certificates, man-in-the-middle attacks are equally feasible.