1. HTTP protocol and HTTPS
We all know that when the client and the server need to communicate, they need to communicate according to a set of protocols.
The whole HTTP is the Hypertext Transfer Protocol (Hyper Text Transfer Protocol , HTTP) is a simple request-response protocol, which usually runs on top of TCP . It specifies what kind of messages the client may send to the server and what kind of responses it may get.
We all know that to use a browser to access a website page, we need to know the domain name of the website. In the address bar of the browser, we will see a string of URLs, as shown in the figure

The URL of the website will be divided into two parts: the communication protocol and the domain name address.
The domain name address is easy to understand. Different domain name addresses represent different pages in the website, and the communication protocol is simply the language for communication between the browser and the server. The communication protocols in the website are generally the HTTP protocol and the HTTPS protocol. What are the two and what is the difference?
HTTP protocol
The HTTP protocol, also known as Hypertext Transfer Protocol, is a network protocol that uses plaintext data transmission. The HTTP protocol has always been the most mainstream web protocol. The HTTP protocol is used to transmit information between web browsers and web servers. It sends content in plain text and does not provide any data encryption. If an attacker intercepts web browsing You can directly read the information in the transmission message between the browser and the website server.
With the development of the Internet today, the plaintext transmission of the HTTP protocol will cause users to have very large security risks. Just imagine, if you are shopping on a website with HTTP protocol, you need to enter your bank card number and password on the page, and then you submit the data to the server to make the purchase. If this link is a little careless, your transmission data is intercepted by a third party. Due to the HTTP plaintext data transmission, your bank card number and password will be obtained by the interceptor. Do you still dare to shop on an HTTP website now? Would you still leave your personal information on an HTTP website?
HTTPS protocol
In order to solve this defect of the HTTP protocol, another protocol needs to be used: the Secure Socket Layer Hypertext Transfer Protocol HTTPS. For the security of data transmission, HTTPS adds the SSL/TLS protocol on the basis of HTTP. SSL/TLS relies on Certificate to verify the identity of the server and to encrypt the communication between the browser and the server. The HTTPS protocol can be understood as an upgrade of the HTTP protocol, which adds data encryption on the basis of HTTP. Before the data is transmitted, the data is encrypted before being sent to the server. In this way, even if the data is intercepted by a third party, your personal information is still safe because the data is encrypted. This is the biggest difference between HTTP and HTTPS.

2. The difference between HTTP and HTTPS

1. Different security
The https:// prefix indicates that it is encrypted with SSL (Secure Sockets) or TSL, and the information transmission between your computer and the server will be more secure. When you use a browser to visit an HTTP website, you will find that the browser will display a "not safe" security warning for the HTTP website, prompting the user that the website currently visited may be at risk
2. The website application process is different
The HTTPS protocol needs to apply for a certificate from a CA. Generally, there are few free certificates and you need to pay a fee. To enable SSL on a web server, you need to obtain a server certificate and bind the certificate to the server to use SSL.
3. The default port is different
http and https use completely different connection methods, and also use different ports. http uses port 80, and https uses port 443. In the network model, HTTP works at the application layer, while HTTPS works at the transport layer.
3. Encryption algorithm
General encryption algorithms are divided into two types: symmetric encryption and asymmetric encryption.
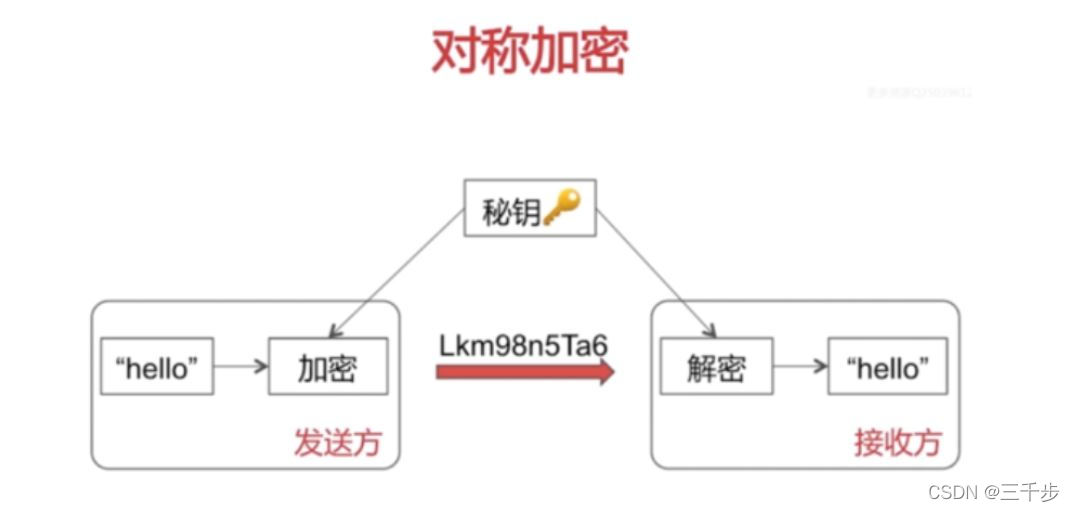
Symmetric encryption
The same key is used for encryption and decryption. The key is shorter and difficult to decipher. In addition to the Data Encryption Standard (DES), another symmetric key encryption system is the International Data Encryption Algorithm (IDEA), which is more encrypted than DES. Well, and the computer performance requirements are not so high.
 advantage:
advantage:
Open algorithm, small amount of calculation, fast encryption speed and high encryption efficiency
shortcoming:
Before the data is transmitted, the sender and the receiver must agree on a secret key, and then both parties can keep the secret key. Secondly, if one party's secret key is leaked, then the encrypted information is not safe. In addition, every time a pair of users uses a symmetric encryption algorithm, they need to use a unique secret key unknown to others, which will cause a huge number of keys owned by both the receiving and sending parties, and key management will become a burden for both parties.
Common symmetric encryption algorithms are : DES, 3DES, Blowfish, IDEA, RC4, RC5, RC6 and AES
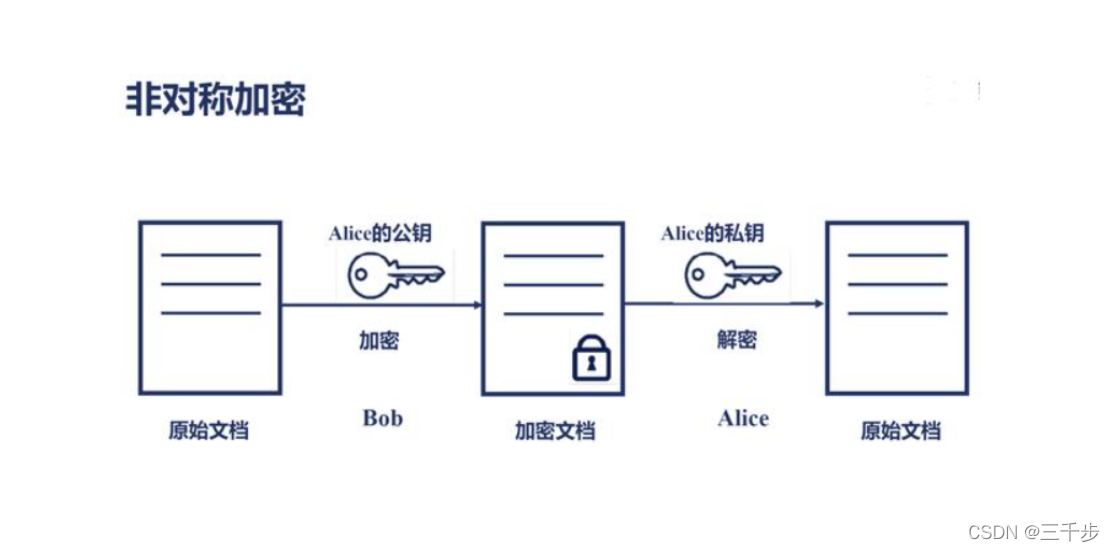
asymmetric encryption
Unlike symmetric encryption algorithms, asymmetric encryption algorithms require two keys: a public key (publickey) and a private key (privatekey). The public key and the private key are a pair. If the data is encrypted with the public key, only the corresponding private key can be used to decrypt it; if the data is encrypted with the private key, only the corresponding public key can be used to decrypt the data. decrypt. Because encryption and decryption use two different keys, this algorithm is called an asymmetric encryption algorithm.
The basic process of asymmetric encryption algorithm to realize the exchange of confidential information is: Party A generates a pair of keys and discloses one of them as a public key to other parties; Encrypted and then sent to Party A; Party A then uses another private key saved by itself to decrypt the encrypted information. Party A can only use its private key to decrypt any information encrypted by its public key.
advantage:
Security, even if the ciphertext is intercepted and the public key is obtained, but the private key cannot be obtained, the ciphertext cannot be deciphered. As the recipient, be sure to keep your own key safe.
shortcoming:
The encryption algorithm is very complicated, the security depends on the algorithm and the key, and the encryption and decryption efficiency is very low.
Common asymmetric encryption algorithms are : RSA, ECC (for mobile devices), Diffie-Hellman, El Gamal, DSA (for digital signatures)
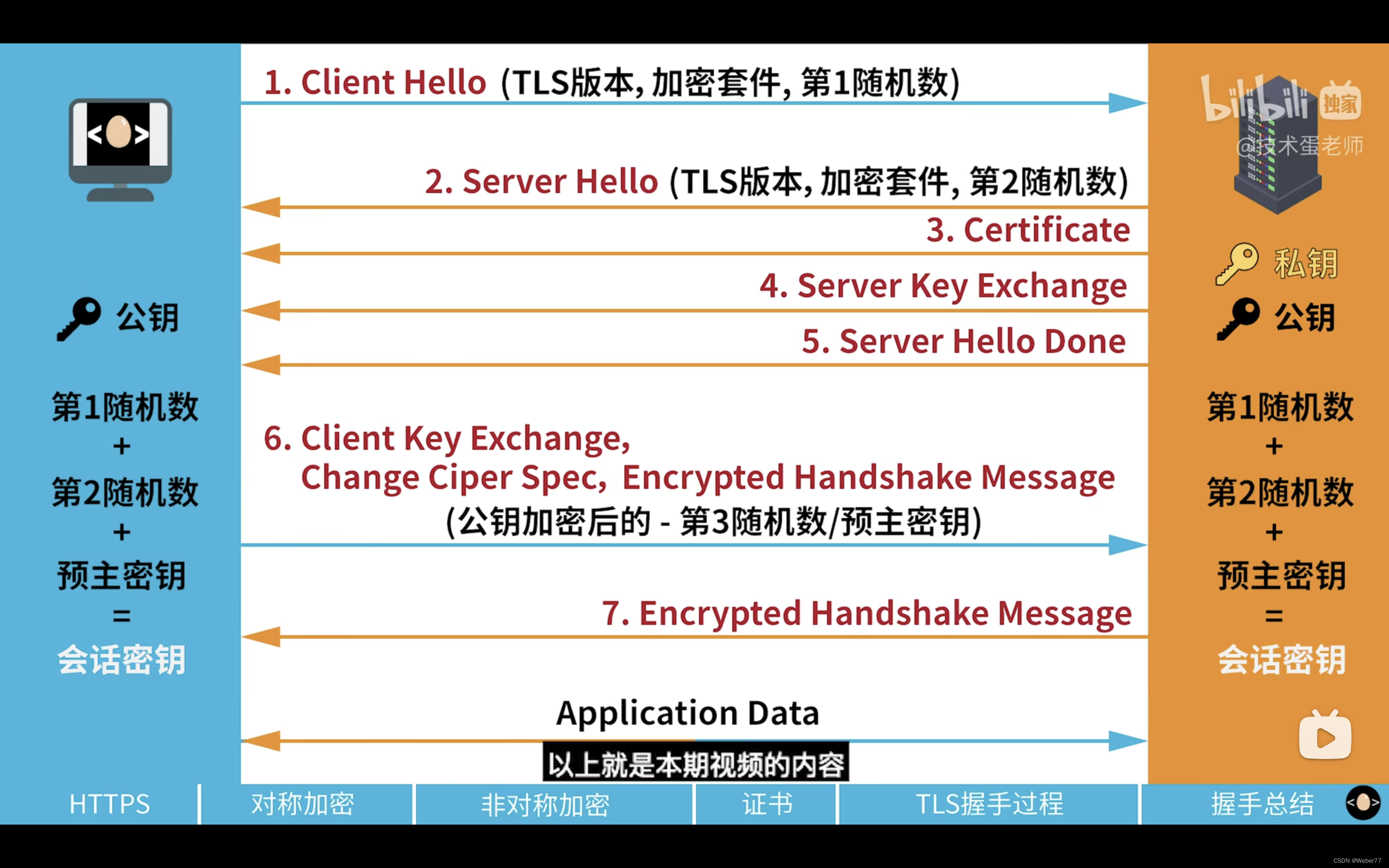
4. TLS handshake process
1. First, the client sends its supported TLS version, optional encryption algorithm, and a random number to the server
2. After receiving the message, the server sends its own TLS version, the selected set of encryption algorithms, and the second random number to the client
3. The server sends its own CA certificate to the client to ensure that the website the client wants to visit is correct
4. The server sends its own public key to the client and tells the client that the call is over
5. The client generates the third random number (pre-master key), encrypts the pre-master key with the public key, and sends it to the server
6. The server receives the encrypted pre-master key and decrypts it with its own private key, so that only the server and client know the pre-master key
7. The server and client use the first and second random numbers and the pre-master key to calculate and obtain the session key
8. Afterwards, the server and client can use the session key for symmetric encryption to speed up communication efficiency