Rating
1 safety protection level
According to the relevant management documents of grade protection, the safety protection level of grade protection objects is divided into the following five levels:
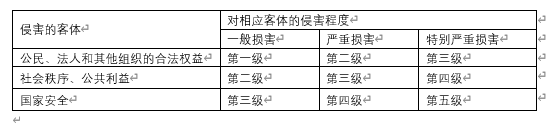
At the first level, if the objects of hierarchical protection are damaged, they will damage the lawful rights and interests of citizens, legal persons and other organizations, but will not damage national security, social order and public interests.
At the second level, if the objects of hierarchical protection are damaged, it will cause serious damage to the legitimate rights and interests of citizens, legal persons and other organizations, or cause damage to social order and public interests, but does not harm national security
The third level, after the damage of the hierarchical protection object, it will cause particularly serious damage to the lawful rights and interests of citizens, legal persons and other organizations, or cause serious damage to social order and public interests, or cause damage to national security
The fourth level, after the hierarchical protection object is damaged, it will cause particularly serious damage to social order and public interests, or cause serious damage to national security
The fifth level, the damage to the object of level protection will cause particularly serious damage to national security
2. Grading elements:
The level of the hierarchical protection object is determined by two grading elements:
Victimized object
Degree of infringement on the object
Violated objects:
the legitimate rights and interests of citizens, legal persons and other organizations,
social order, public interest,
national security
Infringement of the legitimate rights and interests of citizens, legal persons, and other organizations means that certain social rights and interests enjoyed by citizens, legal persons, and other organizations that are confirmed by the law and protected by the law are damaged.
Matters that violate social order include the following: affecting the work order of state agencies’ social management and public services; affecting the order of various types of economic activities; affecting the order of scientific research and production in various industries; affecting the normalcy of the public under legal constraints and ethics Life order, etc.; other matters affecting social order.
Matters that infringe on the public interest include the following aspects: affecting members of society to use public facilities; affecting members of society to obtain public information resources; affecting members of society to receive public services, etc.; other matters affecting public interests.
Infringements on national security include the following aspects: affecting the stability of national power and national defense strength; affecting national unity, national unity and social stability; affecting the political and economic interests of the country in foreign activities; affecting important national security work; affecting national economic competition Power and scientific and technological strength; other matters affecting national security.
The degree of infringement on the subject
caused general damage
caused serious damage
caused particularly serious damage
The description of the three levels of infringement is as follows:
General damage: job functions are partially affected, business capabilities are reduced but the performance of the main functions is not affected, minor legal issues occur, lower property losses, and limited social adverse effects. Other organizations and individuals cause lower damage;
Serious damage: work functions are severely affected, business capabilities are significantly reduced and the performance of main functions is severely affected, serious legal problems occur, high property losses, large-scale social adverse effects, and serious damage to other organizations and individuals ;
Particularly severe damage: work functions are particularly severely affected or incapacitated, business capabilities are severely reduced and or functions cannot be performed, extremely serious legal problems occur, extremely high property losses, large-scale social adverse effects, and other organizations and individuals Caused very serious damage.
3. The relationship between grading elements and safety protection level
The degree of infringement of the infringed object on the corresponding object
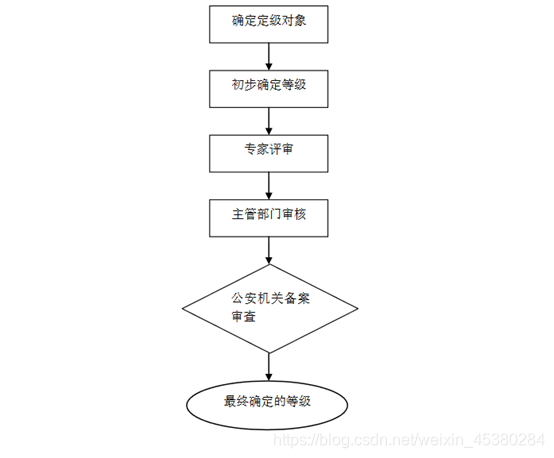
4. Grading process
The general process of the grading work of the grading protection object is shown in Figure 1.
5. Rating object
1. Basic information network
For basic information networks such as telecommunications networks, radio and television transmission networks, and the Internet, they should be classified into different grading objects according to factors such as service types, service areas, and security responsibility subjects. The inter-provincial national business private network can be rated as a whole object, or it can be divided into several rated objects by region.
2. Information System
- Industrial control system The
industrial control system is mainly composed of the production management layer, the field equipment layer, the field control layer and the process monitoring layer, among which: see 5 for the principle of determining the grading objects of the production management layer. The field equipment layer, field control layer and process monitoring layer shall be rated as a whole object, and the elements of each level shall not be rated separately. Determining the rating objects Preliminary determination of the rating The expert review authority reviews the final determination of the public security organ’s filing review. For large industrial control systems, it can be divided into multiple rating objects based on factors such as system functions, control objects, and manufacturers.
2. Cloud computing platform
In a cloud computing environment, the cloud computing platform on the cloud service side should be rated separately as the grading object, and the grading protection object on the cloud tenant side should also be rated as a separate grading object. For large-scale cloud computing platforms, cloud computing infrastructure and related auxiliary service systems should be divided into different grading objects.
3. Internet
of Things The Internet of Things should be rated as a whole object, which mainly includes elements such as the perception layer, network transmission layer, and processing application layer.
4. Information systems
using mobile internet technology The level of protection objects using mobile internet technology should be rated as a whole object, which mainly includes mobile terminals, mobile applications, wireless networks, and related application systems.
5. Other information systems
Other information systems that are the objects of the rating should have the following basic characteristics:
1. Have a definite main security responsibility unit. The information system that is the object of grading should be able to clarify its main security responsibility unit;
2. Carry relatively independent business applications. The information system as the grading object should carry relatively independent business applications, and multiple information systems that accomplish different business goals or support the functions of different units or different departments should be divided into different grading objects;
3. Have the basic elements of an information system. The information system that is the target of the rating should be a multi-resource collection composed of related and supporting equipment and facilities in accordance with certain application goals and rules. A single device (such as servers, terminals, network equipment, etc.) is not rated separately.
3. Big data Big data
with a unified security responsibility unit should be rated as a whole object, or the same related support platform as the responsible subject should be uniformly rated.
6. Grading method:
1. Overview
The security of grading objects mainly includes business information security and system service security. The infringed objects and the degree of infringement on the objects may be different. Therefore, the security protection level should also be divided into business information security and system service security. Aspects are determined. The security protection level of the rated object reflected from the perspective of business information security is called the business information security protection level; the security protection level of the rated object reflected from the perspective of system service security is called the system service security protection level.
The grading method is as follows:
The first step is to
determine the object infringed when it is damaged
1. Determine the object infringed when the business information is damaged
2. Determine the object infringed when the system service is infringed.
The second step is to
determine the degree of infringement on the object
1. According to different infringed objects, comprehensively evaluate the degree of infringement of the business information security from multiple aspects
. 2. According to different infringed objects, comprehensively evaluate the system from multiple aspects The degree of infringement of the service security on the object
The third step is to
determine the security protection level
1. Determine the business information security protection level
2. Determine the system service security protection level
3. Preliminarily determine the higher of the business information security protection level and the system service security protection level as the security protection of the rated object grade
For grading objects such as big data, factors such as data scale and data value should be considered comprehensively, based on their importance in national security, economic construction, and social life, and their impact on national security, social order, and public security after data resources are destroyed. Benefits and factors such as the degree of harm to the legitimate rights and interests of citizens, legal persons and other organizations determine the level of security protection. In principle, the big data security protection level is above the third level.
For grading objects such as basic information networks and cloud computing platforms, the security protection level should be determined according to the importance of the level protection objects that they carry or will be carried, and in principle should not be lower than the security protection level of the level protection objects they carry.
The security protection level of the national critical information infrastructure should not be lower than the third level.
2. Determining the infringed objects The
objects infringed when the grading objects are destroyed include national security, social order, public interest, and the legitimate rights and interests of citizens, legal persons, and other organizations.
When determining the infringed object, it is necessary to first determine whether it violates national security, then whether it violates social order or public interests, and finally whether it violates the legitimate rights and interests of citizens, legal persons, and other organizations.
3. Determine the degree of infringement on the object
- The objective aspect of the infringement is
in the objective aspect. The infringement of the object is manifested as the destruction of the rated object, and the harm mode is manifested as the destruction of the business information security and the destruction of the information system service. The business information security refers to ensuring the information The confidentiality, integrity, and availability of information in the system. System service security refers to ensuring that the grading objects can provide services in a timely and effective manner to complete the predetermined business goals. As the business information security and system service security are damaged, the objects infringed and the degree of infringement on the objects may be different. In the process of grading, it is necessary to deal with these two types of harm separately.
After business information security and system service security are disrupted, the following harmful consequences may occur:
affect the performance of work functions; cause decline in business capabilities; cause legal disputes; cause property losses; cause adverse social effects; cause losses to other organizations and individuals; other impacts .
- Comprehensive determination of the degree of
infringement The degree of infringement is a comprehensive manifestation of different external manifestations in objective aspects. Therefore, the degree of harm should be determined first according to different infringed objects and different consequences of harm. The methods and perspectives taken to determine the degree of harm for different harm consequences may be different. For example, the degree to which the system service security is destroyed and the business capability declines can be different from the area covered by the grading target service, the number of users or the volume of business, etc. It is confirmed that the property losses caused by the destruction of business information security can be determined in terms of direct capital losses and indirect information recovery costs.
When judging the degree of infringement for different infringed objects, the following different criteria should be followed:
If the infringed object is the legitimate rights and interests of citizens, legal persons or other organizations, the overall interests of the person or the unit shall be used as the judgment of the degree of infringement. the benchmark;
if the object of the violation of social order, public security or national interests should be to the overall interests of the industry or the country as a benchmark to determine the extent of damage.
The degree of infringement on the object after business information security and system service security is destroyed is obtained by comprehensively assessing the degree of harm of different harm results. Since the types of information and system service characteristics handled by the grading objects of each industry are different, the damage results and the calculation methods of the damage degree concerned after business information security and system service security are damaged may be different. Each industry can be based on the industry information Features and system service characteristics, formulate a comprehensive assessment method of the degree of harm, and give specific definitions of general damage, serious damage, and particularly serious damage caused by infringement of different objects.
4. Determine the level of security protection
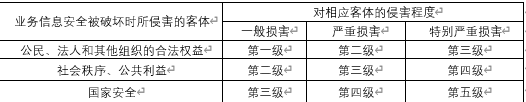
According to the object infringed when the business information security is destroyed and the degree of infringement on the corresponding object, according to the business information security protection level matrix table, the business information security protection level can be obtained.
Business information security protection level matrix:
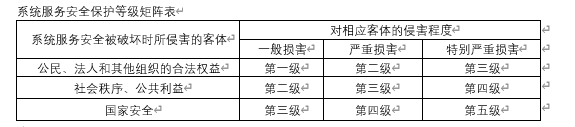
According to the object infringed when the system service security is destroyed and the degree of infringement on the corresponding object, according to Table 3, the system service security protection level matrix table, you can get the system service security protection level
System service security protection level matrix table
The security protection level of the grading object is determined by the higher of the business information security protection level and the system service security protection level.
7. Expert review
The operation and user unit of the grading object shall organize information security experts and business experts to review the rationality of the preliminary grading results and issue expert review opinions.
8 Competent authority review
The operation and user unit of the grading object should report the preliminary grading result to the competent authority of the industry or the superior competent authority for review
9. Record review by public security organs
The operation and user unit of the rated object shall submit the preliminary classification result to the public security organ for filing and review in accordance with relevant management regulations. If the review fails, the operation and user unit shall organize a re-rating; after the review is passed, the safety of the rated object shall be finalized. Protection level.
10. Level change
When the information, business status, and system service scope handled by the hierarchical protection objects change, which may lead to major changes in the business information security or system service security, the infringed objects and the degree of infringement on the objects should be based on this The standard requires re-determination of the grading objects and safety protection levels.