Preface
- First of all, I declare that the host is not a big cow, and there is no great technology. It is just the company's expansion team. Fortunately, as a technical interviewer, my thoughts after interviewing so many people, I hope I can help you a little bit.
1. Background description
This document is based on the compatibility rectification guidance of the change output of the beta1 version of Google Android R. If there are new changes and new features in the subsequent beta version, we will also refresh the relevant chapters of the document, please continue to pay attention to the developer.
2. Storage space limitation
2.1 Background
In order to allow users to better control their files and limit the confusion of files, Android R has modified the method for APP to access files in external storage. The new feature of external storage is called Scoped Storage.
Android R still uses READ_EXTERNAL_STORAGE and WRITE_EXTERNAL_STORAGE as user-oriented storage-related runtime permissions, but now even if these permissions are obtained, access to external storage is also restricted. The scenarios in which the APP requires these runtime permissions have changed, and the visibility of external storage to the APP under various circumstances has also changed.
In the new features of Scoped Storage, the external storage space is divided into two parts:
● Public directories : Downloads, Documents, Pictures, DCIM, Movies, Music, Ringtones, etc.
- The files in the public directory will not be deleted after the APP is uninstalled.
- APP can access the files in it through SAF (System Access Framework) and MediaStore interface.
● App-specific directory
-
After the APP is uninstalled, the data will be cleared.
-
The private directory of the APP, the APP does not need any permissions when accessing its own App-specific directory
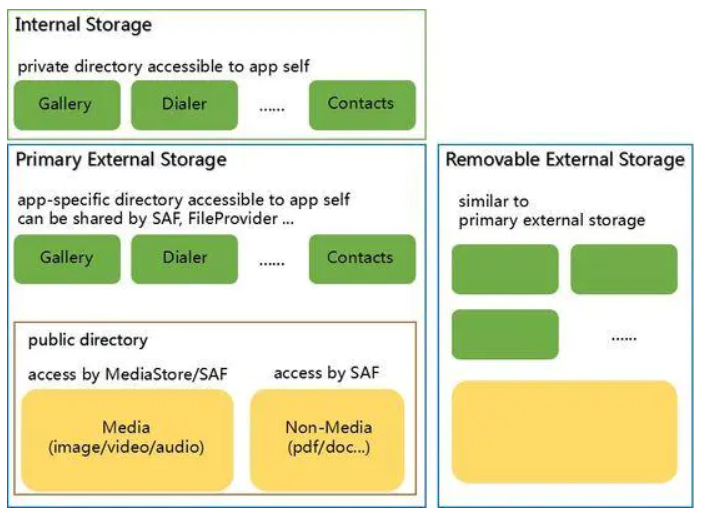
Android R stipulates that APP has two external storage space view modes: Legacy View and Filtered View.
● Filtered View
- App can directly access the App-specific directory, but cannot directly access files outside of the App-specific. Access to public directories or App-specific directories of other apps can only be accessed through MediaStore, SAF, or ContentProvider, FileProvider, etc. provided by other apps.
● Legacy View
- Compatibility mode. As before with Android R, after applying for permission, the App can access external storage and has complete access permissions.
On Android R, apps with a target SDK greater than or equal to 29 are assigned to the Filtered View by default, otherwise, they are assigned to the Legacy View by default. APP may be AndroidManifest.xmlprovided for the new attributes requestLegacyExternalStorageto modify the external memory space view mode, true for the Legacy View, false is Filtered View. You can use Environment.isExternalStorageLegacy()this API to check the operation mode of APP. After APP opens Filtered View, the new features of Scoped Storage will take effect on APP.
In addition to dividing external storage and defining Filtered View, Android R has also made improvements or restrictions on some details of querying and reading and writing files. For example, the geographic location information in image files will no longer be provided by default, and the DATA field obtained by querying MediaProvider will no longer be provided. Reliable, the Pending status of the file has been added, and so on. For details of these details, please refer to the chapter on adaptation schemes.
2.2 Compatibility impact
Scoped Storage has a great impact on APP access to external storage, APP data storage, and data sharing between APPs. Developers should pay attention to the following compatibility issues.
2.2.1 Cannot create a new file
The cause of the problem: directly use a path outside of the App-specific directory to create a new file.
Problem analysis: On Android R, APP only allows files generated by path within its own App-specific directory.
Solution: Please refer to 2.3.1 for the method and file path of new files in the App-specific directory of the APP itself; if you want to create a new file in the public directory, use the MediaStore interface, please refer to 2.3.2; if you want to create a new file in any directory File, SAF is required, see 2.3.3.
2.2.2 Cannot access files on the storage device
Problem reason 1: Use the path directly to access the public directory file.
Problem analysis 1: On Android R, APP can only access the App-specific directory on the external storage device by default.
Solution 1: Refer to 2.3.2 and 2.3.3, use the MediaStore interface to access multimedia files in the public directory, or use SAF to access any file in the public directory. Note: The DATA field queried from the MediaStore interface will be discarded in Android R. It should not be used to access the file or determine whether the file exists; after obtaining the file Uri from the MediaStore interface or SAF, please use Uri to open the FD or input and output Stream instead of converting it into a file path to access.
Problem cause 2: Use the MediaStore interface to access non-multimedia files.
Problem analysis 2: On Android R, using the MediaStore interface can only access multimedia files in the public directory.
Solution 2: Use SAF to apply to users for file or directory read and write permissions, please refer to 2.3.3.
2.2.3 Cannot share files correctly
Problem Cause: When APP will share the App-specific directory of private files to other APP, using a file://type of Uri.
Problem analysis: On Android R, because the files in the App-specific directory are private and protected, other apps cannot access them through the file path.
Solution: See 2.3.4, use FileProvider, will content://share to other types of Uri APP.
2.2.4 Unable to modify the files on the storage device
Problem reason 1: Use the path directly to access the public directory file.
Problem analysis 1: Same as 2.2.2.
Solution 1: Same as 2.2.2, please use the correct public directory file access method.
Problem cause 2: After using the MediaStore interface to obtain the Uri of the multimedia file in the public directory, directly use the Uri to open the OutputStream or file descriptor.
Problem analysis 2: On Android R, to modify the public directory file, user authorization is required.
Solution 2: After obtaining the public directory multimedia file Uri from the MediaStore interface, when opening OutputStream or FD, pay attention to catch RecoverableSecurityException, and then apply to the user for the permission to delete and modify the multimedia file, please refer to 2.3.2.6; use SAF to obtain the file or directory When using Uri, the user has been authorized to read and write and can use it directly, but pay attention to the timeliness of Uri permissions, please refer to 2.3.3.6.
2.2.5 Unexpected deletion of files after application uninstallation
The cause of the problem: Save the files you want to keep in the App-specific directory of the external storage.
**Problem analysis:** On Android R, uninstalling the APP deletes the data in the App-specific directory by default.
Solution: APP should save the files it wants to keep in the public directory through the MediaStore interface, please refer to 2.3.2. By default, the MediaStore interface will save non-media files to the Downloads directory. It is recommended that the APP designate the first level directory as Documents. If the APP wants to retain the data in the App-specific directory when uninstalling, declare android:hasFragileUserData="true" in AndroidManifest.xml, so that when the APP is uninstalled, a pop-up box will prompt the user whether to retain the application data.
2.2.6 Cannot access the geographic location data in the image file
The cause of the problem: parse the geographic location data directly from the image file input stream.
Problem analysis: Because the geographic location information of the picture involves user privacy, the data is not provided to the APP by default on Android R.
Solution: Apply for ACCESS_MEDIA_LOCATION permission and use the MediaStore.setRequireOriginal() interface to update the file Uri, please refer to 2.3.5.1.
2.2.7 Fota upgrade issues
Cause of the problem: After Fota was upgraded, the APP was uninstalled, and the APP data could not be accessed after reinstallation.
Problem analysis: The new features of Scoped Storage are only effective for newly installed apps on Android R. The device is upgraded from the previous version of Android R to Android R, and the installed APP gets the Legacy View view. If these apps save files to external storage directly through the path, such as the root directory of the external storage, then the APP is uninstalled and reinstalled. The new APP gets the Filtered View view, and the old data cannot be accessed directly through the path, resulting in the data Lost.
Solution: APP should modify the way of saving files, no longer use the path to save directly, but use the MediaStore interface to save the files to the corresponding public directory. Before the Fota upgrade, the user history data of the APP can be migrated to the public directory through the MediaStore interface. In addition, the APP should change the way of accessing files outside the App-specific directory, please use the MediaStore interface or SAF.
At last
If you see this and think the article is well written, give it a thumbs up? If you think there is something worth improving, please leave me a message. Will surely inquire carefully and correct deficiencies. Thank you.
Finally put a benefit at the end of the article: GitHub address
PS: I have a lot of high-level Android learning video materials and interview materials in GitHub~
BC%9F%E5%A6%82%E4%BD%95%E9%9D%A2%E8%AF%95%E6%8B%BF%E9%AB%98%E8%96%AA%EF%BC%81.md)**
PS: I have a lot of high-level Android learning video materials and interview materials in GitHub~
Welcome everyone to communicate and discuss together~