The linux tcpdump command is mainly used in the debugging of network problems. It analyzes and debugs by capturing the data packets of the transmission process. And wireshark is a powerful and easy-to-use packet analysis tool. The combination of tcpdump+wireshark is perfect and perfect, so that network problems have nowhere to hide.
table of Contents
1 Basic introduction to tcpdump and wireshark
2.1.2 Monitor the data packets of the specified network interface
2.1.3 Monitor the data packets of the specified host
2.1.4 Specify the number of captured packets
2.1.5 Simplified display of captured packets
2.1.6 Capture packets according to protocol type
2.1.7 Specify host and port number for packet capture
2.1.8 Capture and save the package
2.2 tcpdump detailed parameters
3 wireshark import data packets for analysis
1 Basic introduction to tcpdump and wireshark
1.1 tcpdump
tcpdump is a command-line packet sniffing tool based on Unix systems, which can capture packets flowing on the network card. By default, tcpdump will not capture the internal communication packets of the machine. According to the provisions of the network protocol stack, for messages, even if the destination is the local machine, it needs to pass through the local network protocol layer, so the local communication must enter the kernel through the API and complete the routing.
Principle of linux packet capture:
Linux packet capture is to register a virtual underlying network protocol to complete the processing power of network messages (to be precise, network devices) messages. When the network card receives a network message, it will traverse all the registered network protocols in the system, such as the Ethernet protocol and x25 protocol processing module, to try to analyze the message, which is similar to the mounting of some file systems , Is to let all the registered file systems in the system try to mount, if one thinks it can handle it, then the mount is completed. When the packet capture module pretends to be a network protocol, the system will give this pseudo protocol a chance when it receives a message, and let it process the message received by the network card. It will take the opportunity to snoop on the message, that is, make a complete copy of the message, pretend it is the message it has received, and report it to the packet capture module.
1.2 wireshark
Wireshark is a data packet analysis tool. In various network applications, such as using Spirent_TestCenter (TC) and Ixia tester to capture interface packets or using the tcpdump monitoring packet capture tool that comes with Linux introduced in this article, After capturing the packet, export the message and import it into the wireshark tool for graphical analysis.
2 tcpdump packet capture
2.1 Common commands
2.1.1 Default startup
tcpdump
Under normal circumstances, directly starting tcpdump will monitor all the data packets flowing on the first network interface. However, due to the problem of the Linux default network card, the following error may occur:
tcpdump: packet printing is not supported for link type NFLOG: use -w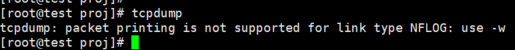
At this point, you can view the network card information through the ifconfig or ip address command, and perform data packet capture through the designated network port

2.1.2 Monitor the data packets of the specified network interface
tcpdump -i ens33

2.1.3 Monitor the data packets of the specified host
Specify the data packet through the network port ens33, and the import and export IP address is 10.193.12.119
tcpdump -i ens33 host 10.193.12.119

Specify the communication between the network port ens33 and the host 10.193.12.12 and the host 10.193.17.4 or 10.193.12.119
tcpdump -i ens33 -n host 10.193.12.12 and \( 10.193.17.4 or 10.193.12.119 \)

Specify the communication between the network port ens33 and the host 10.193.12.12 and the non-host 10.193.17.4
tcpdump -i ens33 -n host 10.193.12.12 and ! 10.193.17.4

Specify all data sent through the network port ens33 and sent by the host 10.193.12.12
tcpdump -i ens33 -n src 10.193.12.12

Specify all data received through the network port ens33 and received by the host 10.193.12.12
tcpdump -i ens33 -n dst 10.193.12.12

2.1.4 Specify the number of captured packets
Specify 5 consecutive data packets received through the network port ens33 and received by the host 10.193.12.12
tcpdump -i ens33 -n dst 10.193.12.12 -c 5
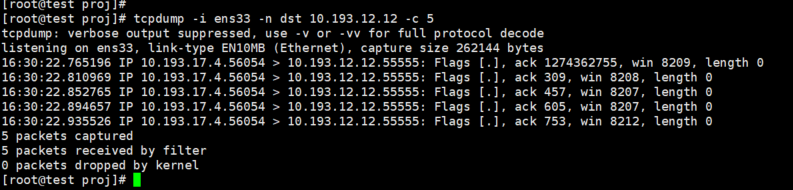
2.1.5 Simplified display of captured packets
tcpdump -i ens33 -n dst 10.193.12.12 -c 5 -q
Specify 5 consecutive data packets received through the network port ens33 and received by the host 10.193.12.12, and use a simplified display, which can be compared with the above picture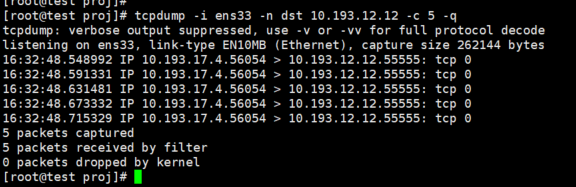
2.1.6 Capture packets according to protocol type
Take ping as an example, we know that the protocol type of ping is icmp, we can specify the icmp protocol type to capture packets
tcpdump -i ens33 -n icmp

2.1.7 Specify host and port number for packet capture
Specify the network card ens33, the port number is 55555 and the ip address is 10.193.12.12 consecutive 10 data packets

2.1.8 Capture and save the package
Capture the package and save the package.cap file, which can be exported and then imported into wireshark for package analysis
tcpdump -i ens33 -n port 55555 and host 10.193.12.12 -c 10 -w package.cap

2.2 tcpdump detailed parameters
- -a Attempt to convert network and broadcast addresses into names.
- -c<number of data packets> After receiving the specified number of data packets, stop dumping operation.
- -d Convert the compiled packet encoding into a readable format and dump it to standard output.
- -dd Convert the compiled packet encoding into C language format and dump it to standard output.
- -ddd Convert the compiled data packet code into a decimal number format and dump it to standard output.
- -e Displays the file header of the connection level on each row of dumping data.
- -f displays the Internet address in numbers.
- -F<Expression file> Specify the file containing the expression.
- -i<Network interface> Send data packets using the specified network section.
- -l Use the buffer for standard output columns.
- -n Does not convert the host's network address to a name.
- -N Does not list domain names.
- -O does not optimize the packet encoding.
- -p Do not let the network interface enter promiscuous mode.
- -q Quick output, only a few transmission protocol information are listed.
- -r<data packet file> Read packet data from the specified file.
- -s<data packet size> Set the size of each packet.
- -S lists the TCP association numbers in absolute rather than relative numbers.
- -t Do not display a time stamp on each row of dumping data.
- -tt Display an unformatted time stamp on each row of dumping data.
- -T<data packet type> Force the data packet specified by the expression mode to be translated into the set data packet type.
- -v displays the instruction execution process in detail.
- -vv displays the instruction execution process in more detail.
- -x List data packet data in hexadecimal code.
- -w<data packet file> Write the packet data to the specified file.
3 wireshark import data packets for analysis
