Article Directory
Preface
In daily work, the remote connection server is often used to operate. There are many commonly used software in remote connection software, but most of them use the ssh protocol.
1. SSH protocol definition and configuration steps
definition
The full name of the SSH protocol is Secure shell, which is a secure channel protocol used to implement remote login, copy, and other operations on a character interface.

The client often uses xshell CRT Putty
. The server often uses openSSH. The
openssh service name is sshd. The main program is /usr/sbin/sshd. The configuration file is /etc/ssh/sshd_config.
In centos7, the system installs openssh related software packages by default. And the service is automatically opened. The port number is 22. You can execute systemctl start sshd to start the sshd service.
Both ssh_config and sshd_config are configuration files of the ssh server. The difference between the two is that ssh_config is a configuration file for the client, and sshd_config is a configuration file for the server.
Configure openSSH server
Modify the ssh configuration file of the
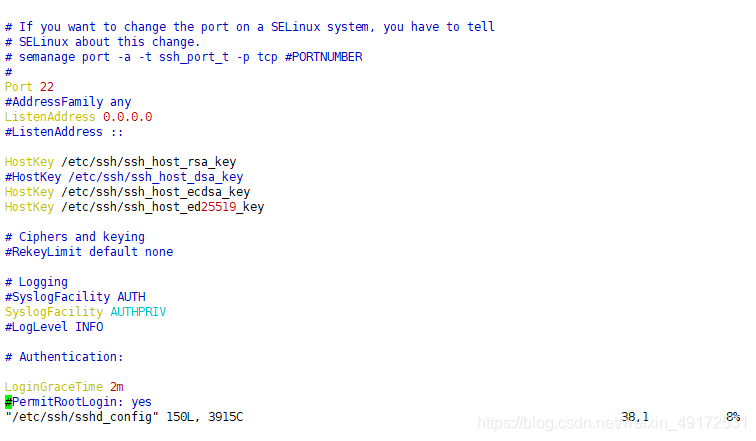
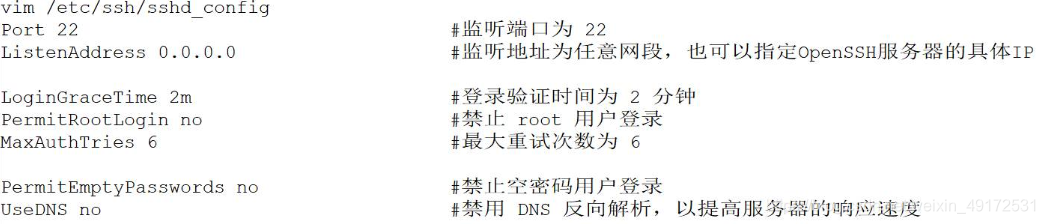
server. If the configuration file is configured, you only need to comment out the configuration you need. The above are common parameters.
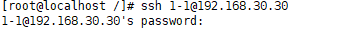
Log in to the ssh server
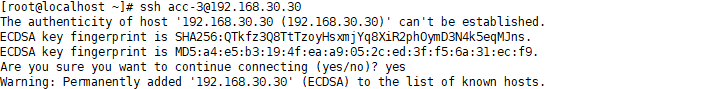
Use IP to log in to the ssh address. The sshd service defaults to port 22-P can specify a non-default port if it defaults to port 22 by default. When logging in for the first time, you must accept the ECDSA key yes sent by the server as consent. After the key verification is successful, you can log in to the server environment.
 You can also set up multiple users to log in to ssh, restrict users to log in ip, etc.
You can also set up multiple users to log in to ssh, restrict users to log in ip, etc.
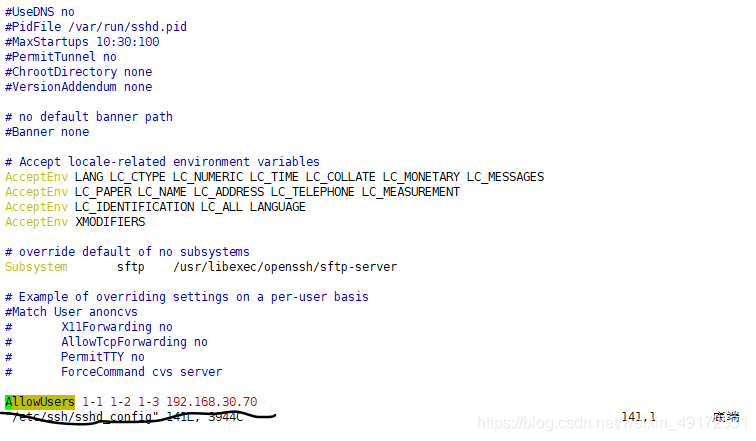
Definition list 1-1 1-2 can log in directly 1-3 can only log in from 192.168.30.70.
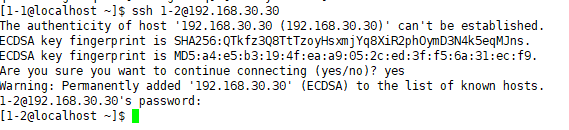
1-1 1-2 You can log in directly,

but you can't log in. You can
prevent a user from logging in as DenyUsers, but be careful not to use it with AllowUsers at the same time.
Copy files remotely
When connecting to a remote desktop, you can upload and download some files to the server and host. You
can use the scp command, but note that you need to use the -r option when copying and uploading a directory
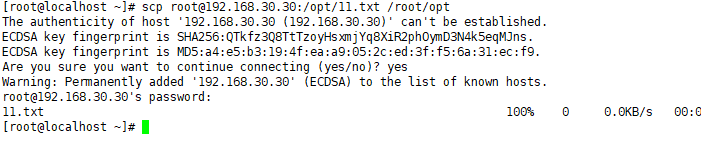
. Upload a file
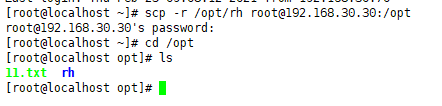
-r copy the entire directory and
it will appear when scp is copied There is no permission issue, please pay attention to the account privilege escalation in the main server, which has been discussed in the previous blog.
SFTP and transfer
The difference between SFTP and FTP sftp uses encryption technology, so the transmission efficiency is higher than stp, but the security is higher, and the configuration is the same as ftp.
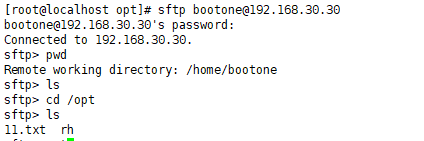
get for download and put for upload
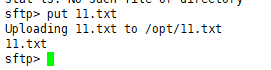
Ways of identifying
There are two authentication modes in the ssh server: password authentication and key pair authentication.
Password verification is simple and convenient to verify the login name and password of the local system user in the server, but it will be brute force cracked.
The key requires matching key information to pass the verification. Usually, a pair of key files (public key and private key) are created in the client first, and then the public key file is placed on the server at the specified location. When logging in remotely, the system The public key and private key will be used for encryption/decryption association, which can increase security and enable interactive login.
When the key pair and password are both enabled, the server preferentially starts the key pair verification according to the actual situation.
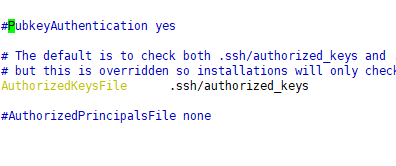
The cursor is to enable key pair verification, and the
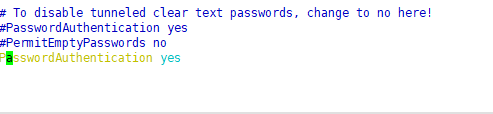
cursor is to enable password verification
Configure key pair verification
Create a key file for the current user through the ssh-keygen tool. The available encryption algorithms are RSA, ECDSA and DSA RSA are the most commonly used algorithms.
In the 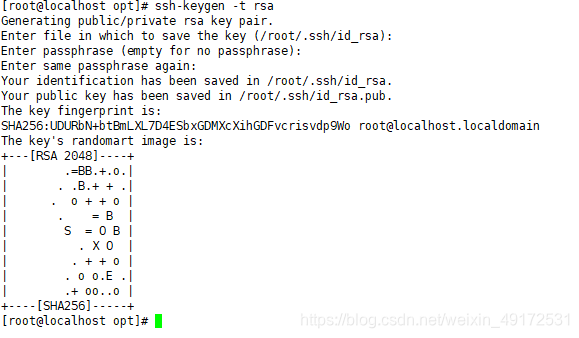
save key file in the default directory.
Upload the public key file to the server. You can upload it to the server or specify it directly.
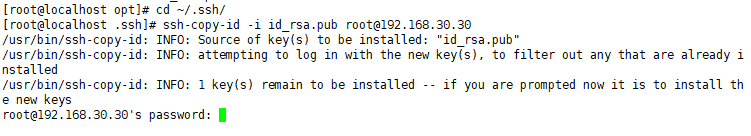
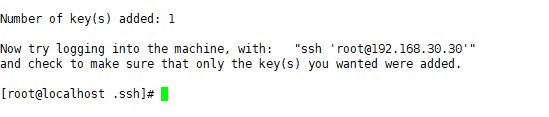
Enter the private key file to log in to the ssh server.
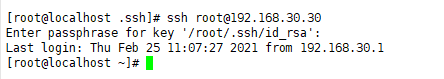
Configure the agent to log in to ssh. You can log in without the interaction of the password account.
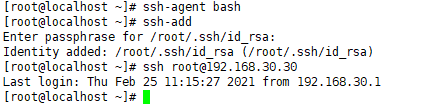
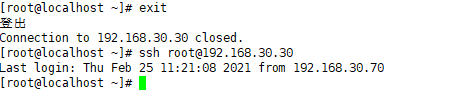
Log in again to log in without interaction.
Two, TCP Wrappers access control
1. Definition
TCP Wrappers wraps up the TCP service and listens to the port of the tcp service program on behalf of it. A security detection process is added. External connection requests must pass this layer of security detection and can only access the service program after obtaining permission. Most Linux distributions now provide TCP Wrappers service by default.
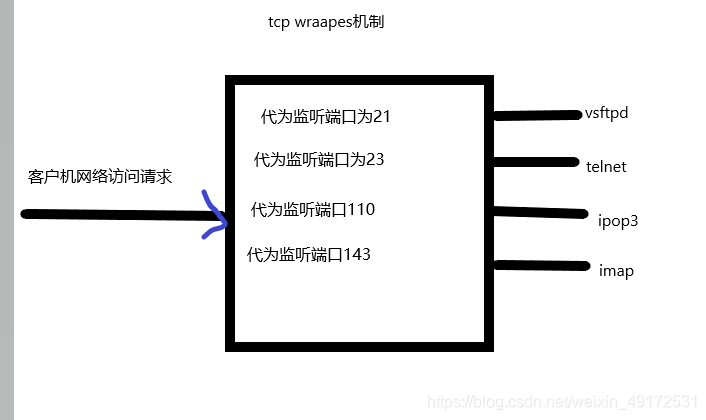
2 Implementation
There are two types:
1 Directly use the tcpd program to protect other services, and you need to run the tcpd program.
2 There are other network service programs that call the libwrap.so.* link library, and there is no need to run the tcpd program. This method is used more and is more efficient.
You can use the command to view the link library
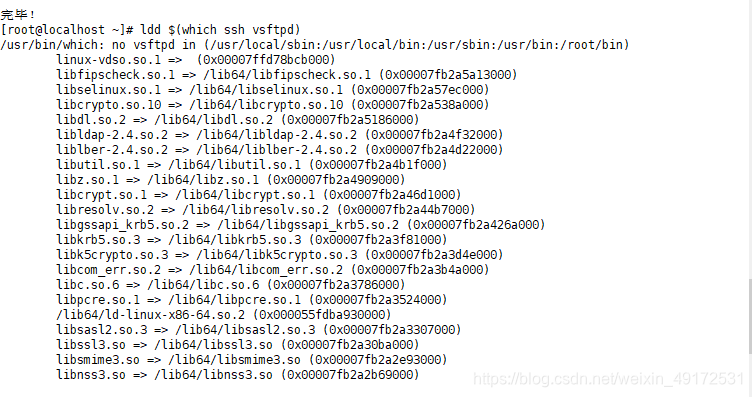
3 Access strategy
The protection programs of the TCP Wrappers mechanism are various network service programs, which perform access control on the clients that access the service. There are two configuration files to perform access control
/ etc/hosts.allow and /etc/hosts.deny. Use them respectively To set the allow and deny policy.
The format is a list of service programs: client address list. The
service control list ALL represents all services, and a single service is represented by the service name vsftpd. If there are multiple services, it can be written as a list of multiple service programs, separated by service names.
The client address list
ALL represents any client address.
LOCAL: represents the local address to each address separated by.
Can be used in combination with wildcards. * Means any length character? Indicates that only one character is represented.
The network segment address can be represented by a specific network segment, such as 192.168.30. or 192.168.30.0/255.255.255.0. The
area address uses .sinla.com to match all hosts in this domain name
4. Access rules
When accessing, the main service will check the visitor's permission, that is, access the two configuration files /etc/hosts/allow and /etc/hosts/den files. When the
visitor matches the policy of the allow file, it can be accessed
without a match. Continue to match the deny policy, deny access if any.
If the two policies are not accessed, it is allowed to pass
, the so-called black and white list.
Allow all access and only deny individual as long as you add a policy in deny.
Allow individual deny of all in addition to configuring the allow policy, but also configure the all: all policy in deny.
For example, only hosts on the 192.168.30.70 network segment and hosts on the 192.168.30.0 network segment are allowed to access other addresses, and hosts on
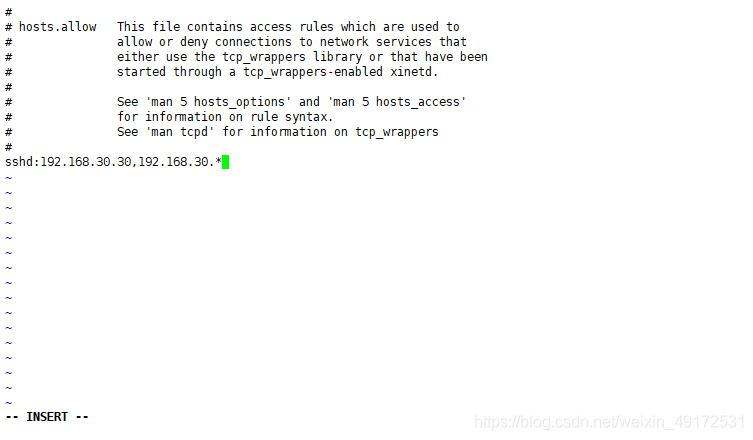
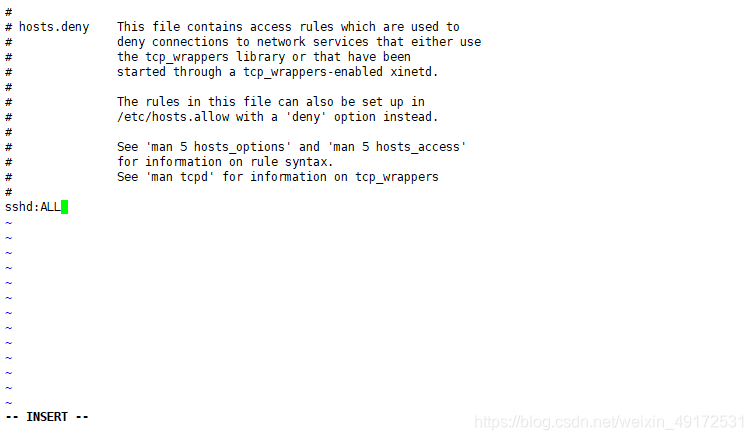
192.168.30.30 can be denied access.