Article Directory
MAC address
MAC (Media Access Control Address) address: Each device in the network has a unique network identifier.
1. Composition
The MAC address is 48 bits (6 bytes)
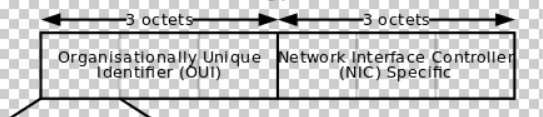
The first 24bit is the code used to represent the manufacturer by applying to IETF and other institutions, and the last 24bit is the only value assigned to the product by the manufacturer.
2. Classification
- Physical MAC address: The 8th bit of the MAC address is 0, which uniquely identifies a terminal on the Ethernet and is the only hardware address in the world
- Broadcast address: MAC address with all 1s, used to identify all terminals on the LAN (ffff:ffff:ffff)
- Multicast MAC address: The 8th bit of the MAC address is 1, which identifies a group of terminals on the LAN
3. Three processing behaviors of data frames by the switch
- Flooding: Data frames are received from one interface of the switch and sent from all interfaces (broadcast frames, multicast frames, unknown unicast frames)
- Forwarding: Receive data frames from one interface of the switch and send them from other specific interfaces (known unicast frames)
- Discard: Data frames received from an interface of the switch are directly discarded
- Receive a data frame from an interface, and then send out from that interface
- The length of the received data frame is less than 64Bit
- The tail checksum error of the data link layer encapsulation of the received data frame
- The received data frame matches the black hole entry
3. Common MAC addresses
| address | usefulness |
|---|---|
| 01-00-5E-0X-XX-XX | ipv4 multicast |
| 01-80-C2-00-00-00 | STP message destination |
| 33-33-XX-XX-XX-XX | IPV6 multicast |
4. MAC address table
Instruct the switch to forward data:
- If the MAC address table contains an entry corresponding to the destination MAC address of the packet, the packet will be forwarded directly through the outbound interface in the entry
- If the MAC address table does not contain an entry corresponding to the destination MAC address of the message, the device will broadcast the message on all interfaces in the VLAN to which it belongs except the receiving interface.
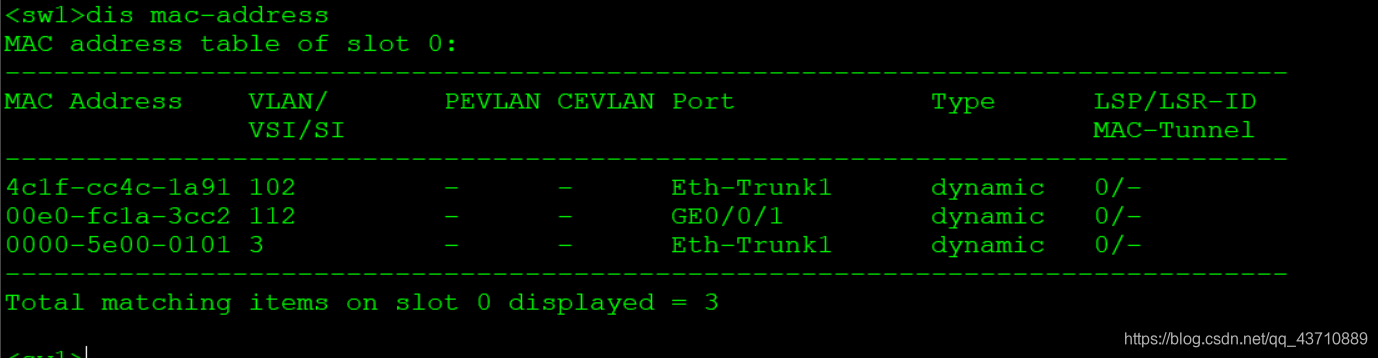
MAC address table classification
(1) Dynamic entries (dynamic)
- Obtained by the interface through the source MAC address in the message, the entry can be aged, and the default aging time is 300 seconds .
- Dynamic entries will be lost after system reset, interface board hot swap or interface board reset
Modify the aging time
[Huawei]mac-address aging-time ?
<0,10-1000000> Aging-time seconds, 0 means that MAC aging function does not
work
(2) Static entries (static)
- It is manually configured by the user and delivered to each interface board. The entries cannot be aged.
- After the system is reset, the interface board is hot-plugged, or the interface board is reset, the saved entries will not be lost.
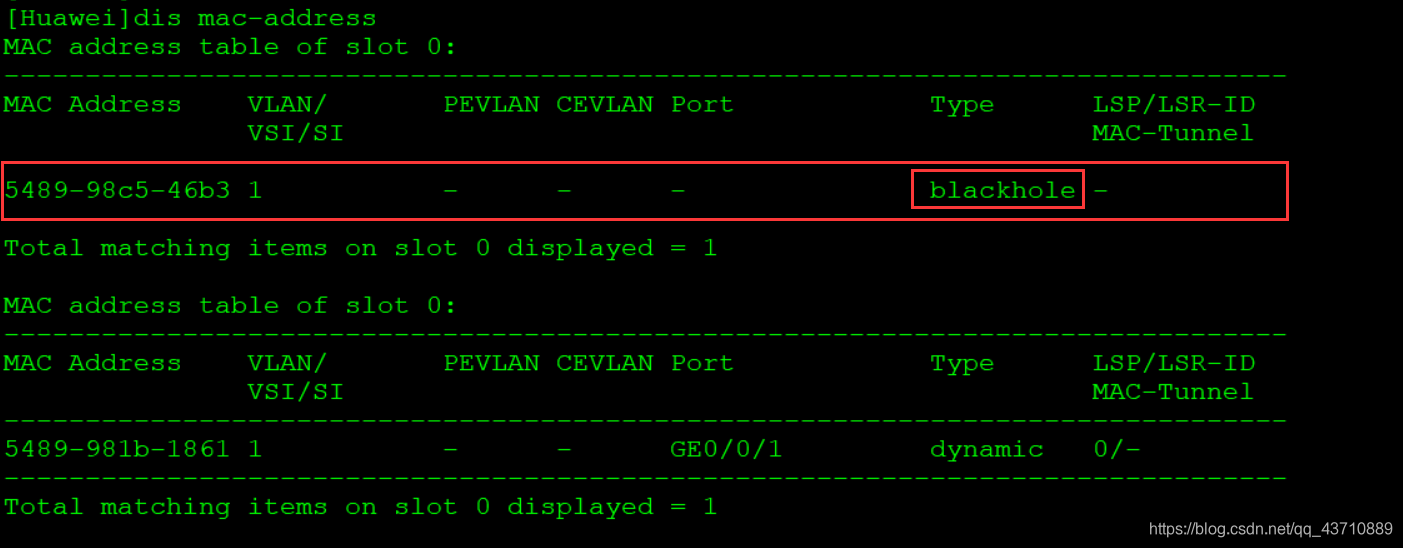
(3) Black hole entry (blockhole)
- It is manually configured by the user and delivered to each interface board. The entries cannot be aged.
- After the black hole MAC address is configured, the packet whose source or destination MAC address is that MAC will be discarded.
Through this operation, illegal users can be filtered
- Configuration
[Huawei]mac-address blackhole 5489-98c5-46b3 vlan 1
一定要敲vlan,否则无效;没有配置vlan,默认使用vlan 1 转发
2. Port security
Port security: By converting the dynamic MAC address learned by the interface into a secure MAC address (including secure dynamic MAC, secure static MAC and sticky MAC), it prevents illegal users from communicating with the switch through this interface, thereby enhancing the security of the device.
Secure MAC address classification
Secure dynamic MAC address
- MAC address converted when port security is enabled but the Sticky MAC function is not enabled
- When the device restarts, the entries will be lost and need to be re-learned; it will not be aged by default, only after the aging time is configured
Secure static MAC address
- The static MAC address manually configured when port security is enabled.
- Will not be aged, no entries will not be lost after restart
Sticky MAC address
- The MAC address converted to after port security is enabled and the Sticky MAC function is also enabled.
- Will not be aged, no entries will not be lost after restart
从学习方式看,动态和sticky都是通过接口接收数据帧动态学习到,静态是通过手工配置
从mac地址失效上看,静态和sticky的表项不会在设备重启后失效,动态在设备重启会丢失表项
Port security protection action
| action | Explanation |
|---|---|
| restrict | Discard the packets whose source MAC address does not exist and report an alarm (default behavior) |
| protect | Discard packets whose source MAC address does not exist |
| shutdown | The interface status is set to error-down, and an alarm is reported |
Configuration
Configure secure MAC function
interface GigabitEthernet0/0/1 //进入接口
port-security enable //使能端口安全
port-security protect-action shutdown //保护动作为shutdown
port-security aging-time 10 //配置老化时间

Configure Sticky MAC function
interface GigabitEthernet0/0/2
port-security enable
port-security mac-address sticky \\使能接口Sticky MAC功能
Port security frequently used scenarios
- Used in access layer devices, port security can be configured to prevent counterfeit users from attacking other ports.
- Used in the convergence layer equipment, the number of access users can be controlled by configuring port security.
接入层使用时注意:
如果接入用户变动比较频繁,可以通过端口安全把动态MAC地址转换为安全动态MAC地址。这样可以在用户变动时,及时清除绑定的MAC地址表项。
如果接入用户变动较少,可以通过端口安全把动态MAC地址转换为Sticky MAC地址。这样在保存配置重启后,绑定的MAC地址表项不会丢失。
MAC address offset
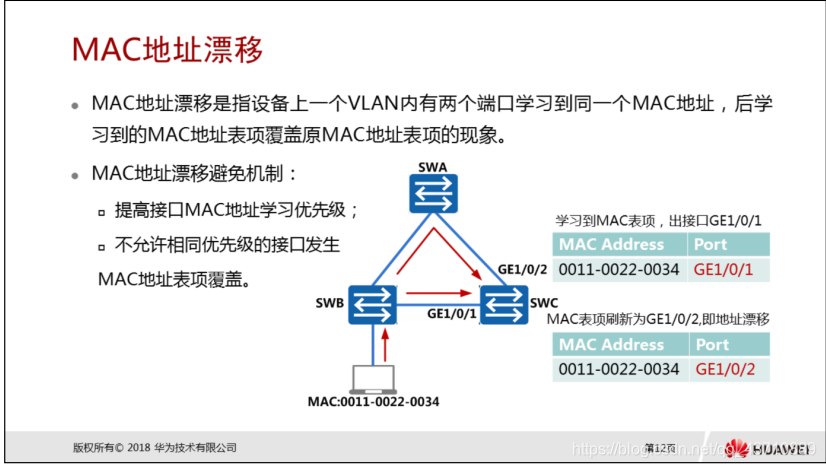
Definition: MAC address drift means that two ports in a VLAN on the device learn the same MAC address, and the MAC address table entries learned later overwrite the original MAC address table entries.
When both ports are sending messages, the MAC address table of the switch will frequently fluctuate and the outgoing interface corresponding to the MAC address will be modified. After multiple modifications, the switch will detect the MAC address drift
Scene
- Loop
- Switch between VRRP master and backup gateways
- Attacker access
- Bind a single MAC address with dual network cards
How to avoid
- Increase the priority of interface MAC address learning. When different interfaces learn the same MAC address table entry, the MAC address table entry learned by the high-priority interface can overwrite the MAC address table entry learned by the low-priority interface to prevent MAC addresses from drifting between interfaces.
- MAC address table entry overwriting is not allowed for interfaces with the same priority. When the priority of the port connected to the forged network device is the same as that of the secure network device, the MAC address entries of the forged network device learned later will not overwrite the previous correct entries. However, if the network device is powered off, it will still learn the MAC address of the forged network device. When the network device is powered on again, it will not be able to learn the correct MAC address.
solution:
1. Increase the priority of interface MAC address learning (the default is 0), the larger the priority, the lower priority cannot overwrite the higher priority
[Huawei-GigabitEthernet0/0/2]mac-learning priority 3
##配置接口学习MAC地址的优先级,缺省情况下,接口学习MAC地址的优先级为0,数值越大优先级越高
2. It is not allowed to overwrite the MAC address table entries on the interfaces of the same priority
undo mac-learning priority 3 allow-flapping
##配置不允许相同优先级的接口发生MAC地址漂移
3. IPSG: Match check of IP packet and MAC address based on binding table
[Huawei-vlan1]ip source check user-bind enable
4. STP and other Layer 2 destructive protocols
5. Configure MAC-spoofing-defend function
Since the behavior of the user side cannot be controlled, it may happen that the user side sends a packet forging the MAC address of the network side server , causing other users to be unable to access the network side server. After using this command to configure the network side interface as a trusted interface, the MAC address learned by this interface will not be learned on other interfaces, which can prevent the user side from sending packets from the MAC address of the network side server. If you need to configure the interface as a trusted interface, you need to enable the global MAC-spoofing-defend function first.
MAC address drift detection
Based on global detection (detecting whether all MAC addresses on the device have drifted)
It is enabled by default, and the default security level is middle: After 10 migrations of the MAC address, the system considers the MAC address to drift
MAC address flap processing action: trigger interface error-down or exit VLAN operation (the processing action is not enabled by default)
Configuration:
##接口视图下
mac-address flapping trigger quit-vlan //发生漂移该接口退出当前VLAN 变更为vlan 1
mac-address flapping trigger error-down //生漂移将接口down
##全局视图下
mac-address flapping detection \\配置全局MAC地址漂移检测功能
error-down auto-recovery cause mac-address-flapping interval 50 //接口发生漂移被down后恢复的时间
mac-address flapping quit-vlan recover-time 20 //退出vlan恢复时间,默认为10S
mac-address flapping aging-time 60 //配置MAC地址漂移表项的老化时间,默认为300S
VLAN-based detection (only detect whether the MAC address of the configured VLAN drifts)
MAC address flap processing action: trigger interface error-down or send an alarm
Configuration
##VLAN视图下,两种配置方式
loop-detect eth-loop alarm-only
###一旦交换机检测到该VLAN内发生了MAC地址漂移,交换机仅仅产生相应的告警信息(不会阻塞发生MAC地址漂移的接口)
loop-detect eth-loop block-mac block-time 10 retry-times 2
###如果检测到漂移则将接口堵塞,接口将被阻塞10s,10s之后接口会被放开并重新进行检测,此时该接口可以正常收发数据;如果20s内没有再检测到MAC地址漂移,则接口的阻塞将被彻底解除;但是如果20s内再次检测到MAC地址漂移,则再次将该接口阻塞,最大重复次数为2次(用retry-times关键字指定),如果交换机依然能检测到该接口发生MAC地址漂移,则永久阻塞该接口。
Special scene configuration
Turn off MAC address flapping detection for a specific VLAN
mac-address flapping detection exclude vlan X
- VRRP scenario.
- Server deploys NIC binding in load sharing mode on these two NICs, that is, bundles Eth1 and Eth2 into a logical interface, and loads outgoing traffic on the two physical interfaces, Eth1 and Eth2.