Today, the public account message function is opened! | Housewarming benefits at the end of the article
SNAT policy overview
SNAT full name: Source Network Address Translation source address translation
SNAT is an address translation operation of Linux firewall, a type of packet control in the iptables command;
SNAT function: modify the source IP address of the data packet according to the specified conditions.
With the gradual reduction of IP address resources, it is difficult for companies to apply for public IP addresses, or can only admit the cost of one or a few public IP addresses, so most companies will face the problem of hosts in the LAN accessing the Internet. demand. Using a small enterprise network and applying the SNAT strategy in the gateway can solve the problem of shared Internet access in the LAN.
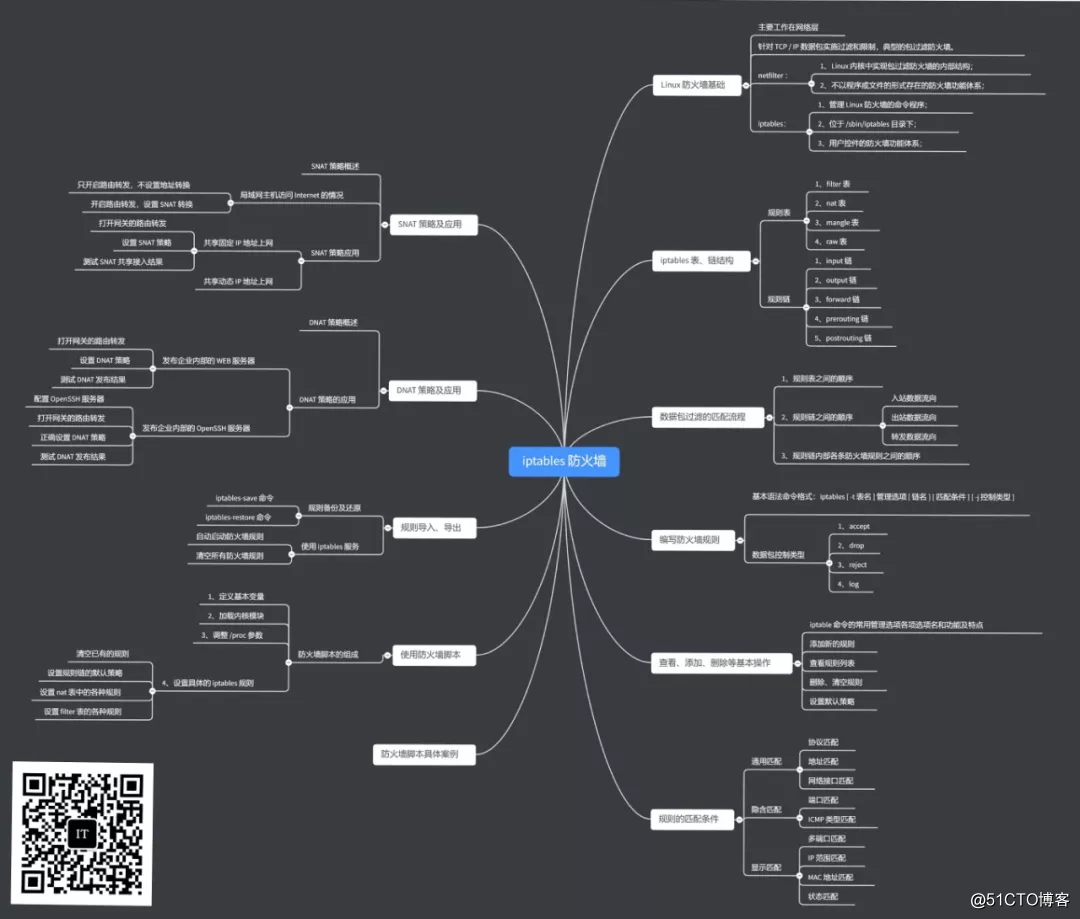
The Linux gateway server needs to connect to the Internet and the LAN through two network cards eth1 and eth2 respectively to analyze the situation of the LAN hosts accessing the Internet.
Each host in the local area network correctly set the IP address/subnet mask/default gateway address
Eth1: 192.168.3.111/24 Gw: 192.168.3.1
Eth2: 192.168.1.7/24 (connect to the internal network card without configuring the gateway)
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:f9:55:5b brd ff:ff:ff:ff:ff:ff
inet 192.168.1.7/24 brd 192.168.1.255 scope global eth2
inet6 2409:8a00:30f8:4d70:20c:29ff:fef9:555b/64 scope global dynamic
valid_lft 259010sec preferred_lft 172610sec
inet6 fe80::20c:29ff:fef9:555b/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:f9:55:65 brd ff:ff:ff:ff:ff:ff
inet 192.168.3.111/24 brd 192.168.3.255 scope global eth1
inet6 fe80::20c:29ff:fef9:5565/64 scope link
valid_lft forever preferred_lft forever
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.3.0 0.0.0.0 255.255.255.0 U 1 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 1 0 0 eth2
0.0.0.0 192.168.1.1 0.0.0.0 UG 0 0 0 eth2Turn off the firewall and selinux
# service iptables stop
iptables:将链设置为政策 ACCEPT:filter [确定]
iptables:清除防火墙规则: [确定]
iptables:正在卸载模块: [确定]
# setenforce 0
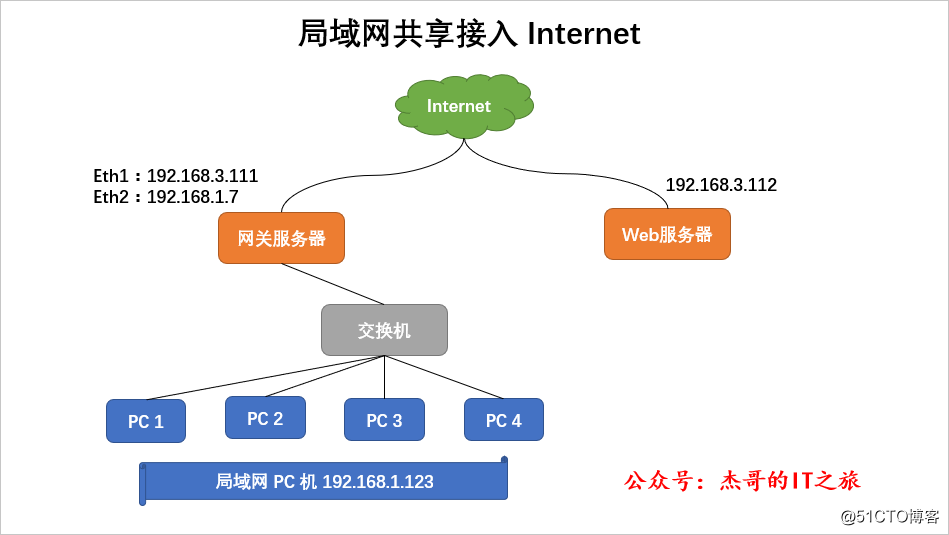
Only enable routing and forwarding, and without address translation,
the Linux server acting as a gateway must enable routing and forwarding to connect to multiple networks.
When the address translation strategy is not used, the source IP of data packets that access the Internet from the LAN PC 192.168.1.123 is forwarded by the gateway is so low that it remains unchanged. When the host in the Internet receives such a request packet, the response packet will not be Return correctly, causing the access to fail. (The private network address cannot be routed normally in the Internet)
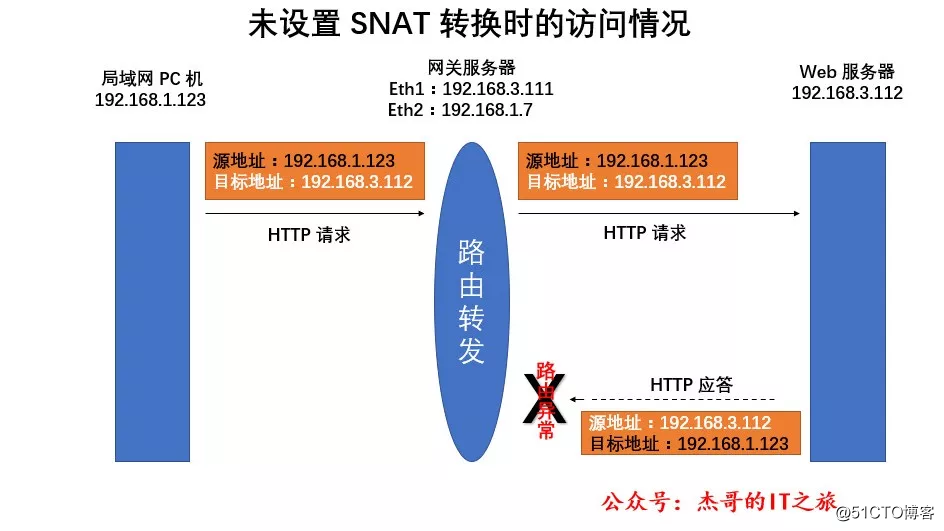
Turn on routing and forwarding and set SNAT conversion.
If the SNAT policy is correctly applied in the gateway server, the data packet forwarding situation is different.
When the data packet of the LAN PC accessing the Internet arrives at the gateway server, the routing is selected first. If it is found that the data packet needs to be forwarded from the external network interface eth1, the source IP address 192.168.1.123 is changed to the gateway's external network interface address 192.168 3.111, and then sent to the target host 192.168.3.112.
Submit the data access request from the public network IP address of the gateway server, and the target host can correctly return the response data packet, so that the LAN PC can share the same public network IP address to access the Internet.
In the process of address translation by SNAT, the gateway server will correctly return the response data packet to the source host in the LAN according to the previously established SNAT mapping. As long as the first packet of the connection is processed by SNAT, the connection and other packets corresponding to the data stream will be automatically processed by SNAT. The server in the Internet does not actually know the IP address of the PC in the LAN, and the conversion between them is completely completed by the gateway host, which can play the role of intranet protection.
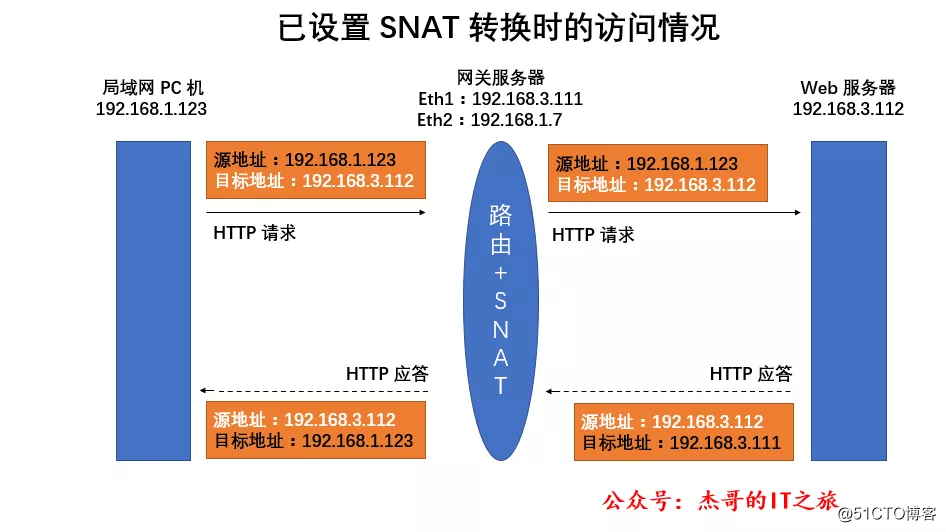
SNAT strategy application
SNAT strategy application: It is to provide access strategy for the LAN sharing Internet access. The cut-in time for processing data packets is after routing selection. It is to modify the source IP address of the data packet sent out of the LAN to the external network interface IP of the gateway server address.
The SNAT strategy is used in the postrouting chain of the nat table.
When writing a SNAT policy, you need to use the iptables command combined with the --to-source IP address option to specify the modified source IP address.
Sharing a fixed IP address to access the Internet. The
Linux gateway server connects to the Internet and LAN through two network cards eth1 and eth2 respectively.
The default gateway setting of all LAN PCs is: 192.168.1.7, and the DNS server has been set up.
PCs on the 192.168.3.0/24 network segment are required to be able to access the Internet normally through sharing.
Turning on the gateway's routing forwarding
IP forwarding is the key to realize the routing function, corresponding to the ip_forward setting in the /proc file system.
When the value is 1, it means on, and when it is 0, it means off.
Use the Linux host as the gateway device, you can modify the sysctl.conf configuration file, and the routing and forwarding function must be permanently enabled.
# vi /etc/sysctl.conf
7 net.ipv4.ip_forward = 1 # 将第 7 行的配置由原来的 0 改为 1
# sysctl -p # 读取修改后的配置
During the test, routing and forwarding can be temporarily turned on.
# echo 1 > /proc/sys/net/ipv4/ip_forward
# sysctl -w net.ipv4.ip_forward=1
net.ipv4.ip_forward = 1
Set the SNAT strategy correctly.
Adopt the SNAT strategy for the data packets of the LAN PC accessing the Internet, change the source address to the gateway's public IP address, set up firewall rules, keep the SNAT strategy effective for a long time, and write the relevant commands into the rc.local configuration File, easy to set automatically after booting.
# iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth1 -j SNAT--to-source 192.168.3.111Test the SNAT policy sharing access results.
Use a PC in the local area network to access websites on the Internet normally.
The accessed website server will think that the gateway host 192.168.3.111 is accessing to obtain web logs, and it is not known whether it is the PC address 192.168.3.123 of the actual corporate intranet that is accessing.
Start a Windows device, configure the IP address according to the actual situation, and test the connectivity;
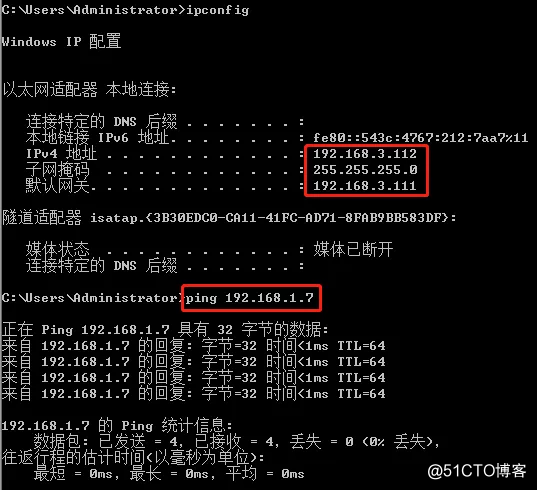
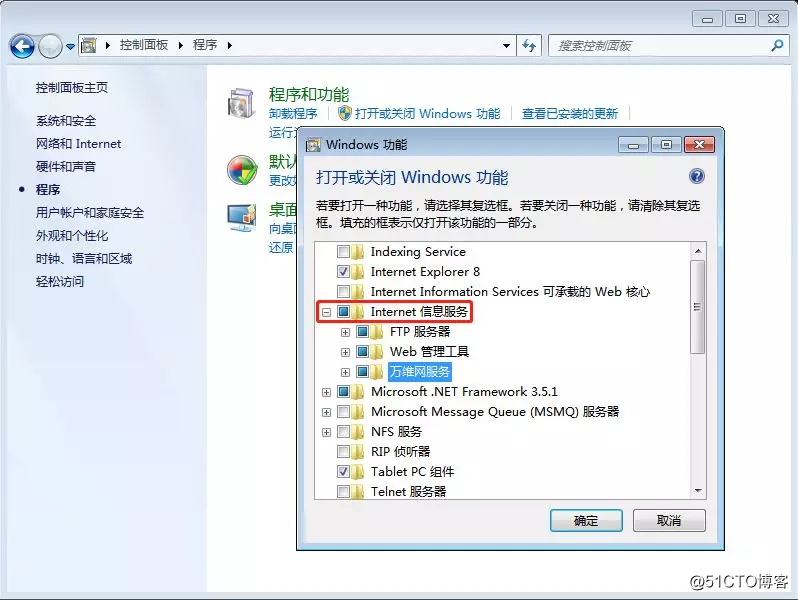
Install the IIS service on the Windows operating system and select the Internet Information Service option;
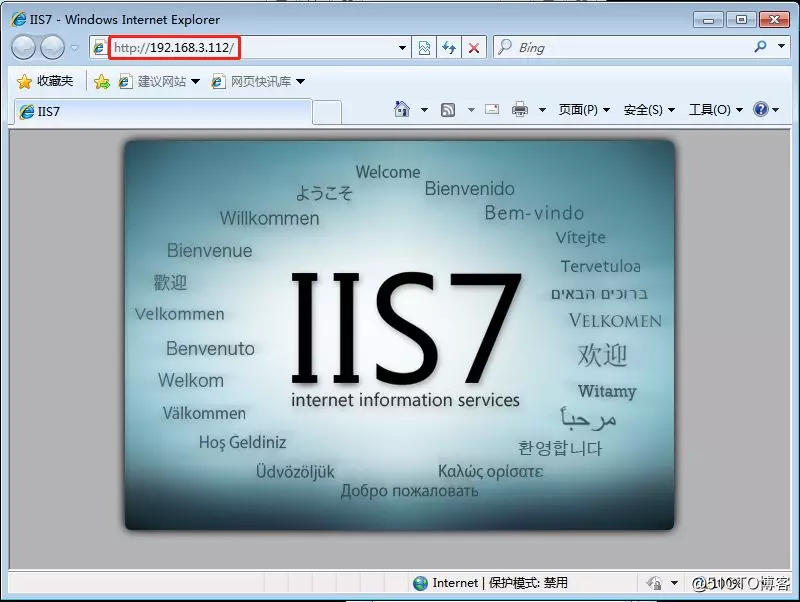
After installation, open the browser and enter the IP address of the machine to access;
Share dynamic IP address to surf the Internet
iptables provides a data packet control type called masquerade, which can be used to modify the source IP address of the data packet, and can automatically obtain the IP address of the external network interface, without using --to-source to specify a fixed IP address .
To use the MASQUERADE masquerading strategy, simply remove the --to-source IP address in the SNAT strategy, and then use -j MASQUERADE to specify the packet control type.
ADSL broadband link, usually the connection name is: ppp0, ppp1, etc.;
# iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o ppp0 -j MASQUERADE
If the gateway uses a fixed public IP address, it is better to choose the SNAT strategy instead of the masquerade strategy to reduce unnecessary system overhead.
DNAT strategy and application
The full name of DNAT: Destination Network Address Translation (Destination Network Address Translation)
DNAT is another address translation operation of Linux firewall, which is a type of packet control in iptables commands;
Function: Modify the destination IP address and destination port of the data packet according to the specified conditions.
DNAT strategy overview
DNAT: used to modify the target IP address and target port, used in the PREROUTING chain and OUTPUT chain of the nat table.
Similar to SNAT, SNAT is used to modify the source IP address and is used in the POTROUTING chain of the nat table.
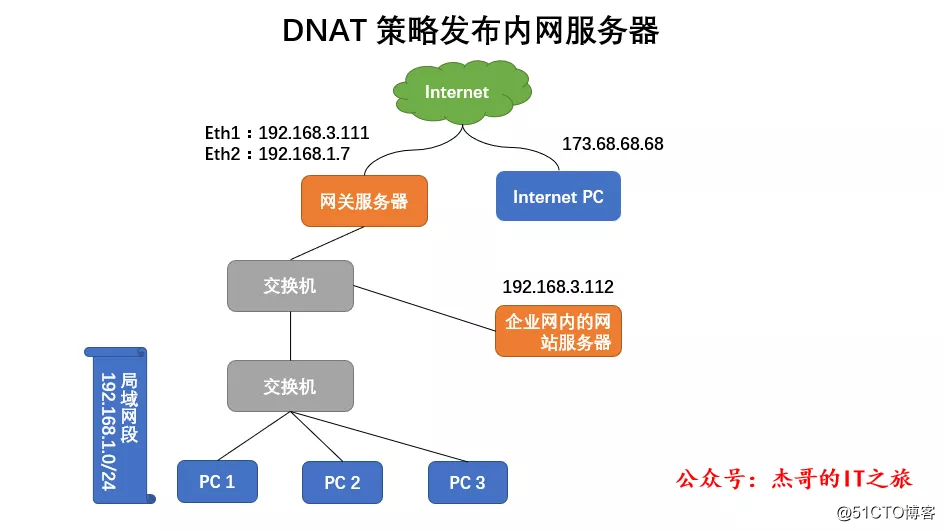
In the Internet environment, the registered website domain name must correspond to a legal public IP address, and the Internet PC will not be able to access the company's intranet server unless the DNAT policy is correctly set in the gateway server.
When the HTTP request submitted by the Internet PC reaches the enterprise's gateway server, the gateway server first judges the destination address and destination port of the data packet, and finds that the data packet needs to access port 80 of the machine, then the destination IP address is changed to a website on the intranet The server IP address is then sent to the internal web server.
The gateway server will modify the source IP address of the returned HTTP response packet according to the DNAT mapping established before, and then return it to the Internet PC.
The Internet PC does not actually know the LAN address of the corporate website server. The intermediate conversion is done by the gateway host. Through the set DNAT strategy, the internal server of the enterprise can provide services to the Internet.
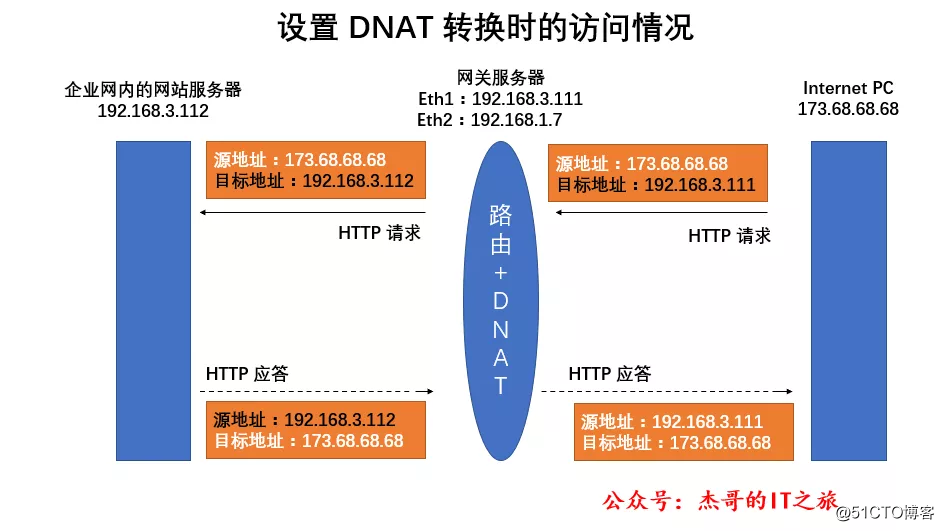
DNAT strategy application
DNAT application: is to publish the internal server of the enterprise on the Internet, and the cut-in time for processing data packets is performed before routing. Modify the destination address of the data packet accessing the IP address of the gateway's external network interface to the IP address of the internal server that actually provides the service.
When using the iptables command to set the DNAT policy, you need to combine the --to-destination IP address option to specify the IP address of the internal server.
The company publishing the internal web server of the
enterprise needs to register the domain name of the website, and the IP address is 192.168.3.111
The company’s web server is located in the local area network with an IP address of 192.168.3.112
It is required to be able to view the company’s website content from the Internet by accessing the website domain name
Open gateway routing and forwarding
# vi /etc/sysctl.conf
7 net.ipv4.ip_forward = 1 # 将第 7 行的配置由原来的 0 改为 1
# sysctl -p # 读取修改后的配置Set the DNAT strategy correctly
for any host in the Internet to access the data packet of the gateway 80 port, and modify the target address to the IP address of the website server located in the intranet.
# iptables -t nat -A PREROUTING -i eth2 -d 192.168.1.7 -p tcp --dport 80 -j DNAT --to-destination 192.168.3.112
# iptables -t nat -L -n -v
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- eth2 * 0.0.0.0/0 192.168.1.7 tcp dpt:80 to:192.168.3.112
Chain POSTROUTING (policy ACCEPT 1 packets, 136 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1 packets, 136 bytes)
pkts bytes target prot opt in out source destination
Test DNAT publishing results
are correctly set in the website server 192.168.3.112, start the web service, test the web page, you can customize the home page file, and then access the website through the client in the Internet, without DNS resolution, you can also directly access.
Publish the internal OpenSSH server
DNAT strategy: used to modify the destination IP address of the data packet, but the destination port number can also be modified when needed.
Configure the OpenSSH service
to enable the OpenSSH service in the gateway and website server, using ports 2345 and 22 respectively.
The gateway's sshd service faces the Internet directly, so the default port is not used.
Open gateway routing and forwarding
# vi /etc/sysctl.conf
7 net.ipv4.ip_forward = 1 # 将第 7 行的配置由原来的 0 改为 1
# sysctl -p # 读取修改后的配置Set the DNAT strategy correctly
. The sshd service of the gateway directly faces the Internet without address translation, but the website server is located in the intranet and needs to be published through the DNAT strategy.
The gateway sets up firewall rules, modifies the data packets that access the external network's IP address 2346 port, and modifies the destination address and port to facilitate forwarding to the web server.
# iptables -t nat -A PREROUTING -i eth2 -d 192.168.1.7 -p tcp --dport 2346 -j DNAT --to-destination 192.168.3.112:22To test the DNAT release results,
use ssh -p 2345/2346 username@eth2 IP address to log in to the gateway server