Redis basic data types
- Preface
- Why do you need a NoSQL database
- What is Redis
- Introduction to Redis Basic Knowledge
- Redis data type
- to sum up
Preface
In daily development, we generally choose relational databases to store data, such as MySQL, Oracle, etc., but in business scenarios with large concurrency, relational databases often become system bottlenecks and cannot fully meet our needs, so The non-relational database, the NoSQL database, was born.
The most common interpretation of NoSQL database is "non-relational", and some people explain it as "Not Only SQL". Non-relational databases do not guarantee transactions, that is, they do not have ACID features. This is also the biggest difference between non-relational databases and relational databases. The Redis we are about to introduce is a type of NoSQL database.
PS: This series of articles is based on Redis5.0.5 version .
Why do you need a NoSQL database
Compared with traditional relational databases, NoSQL databases have the following advantages:
- 1. There is no relationship between the data, which is very easy to expand
- 2. Support for reading and writing of massive data, higher performance under high concurrency
- 3. Support distributed storage, and easy to expand and shrink
At the same time, there are many types of NoSQL databases. According to different data storage types, there are mainly the following common NoSQL databases:
- 1. Key-value storage. Such as: Redis and MemcaheDB
- 2. Document storage. Such as: MongoDB
- 3. Column storage. Such as: HBase
- 4. Graph storage. Such as: Neo4j
- 5. Object storage
- 6. Other types are no longer listed
What is Redis
Redis full name: REmote DIctionary Service, that is, remote dictionary service. Redis is an open source (in compliance with the BSD protocol), network-supported, memory-based and persistent log-based, Key-Value database.
Redis has the following characteristics:
- 1. Support rich data types. Such as strings (strings), hashes (hashes), lists (lists), sets (sets), sorted sets (sorted sets) and range queries, bitmaps, etc.
- 2. Rich functions. Provides persistence mechanism, expiration strategy, subscription/release and other functions
- 3. High performance, high availability and cluster support
- 4. Provides APIs in multiple languages
Introduction to Redis Basic Knowledge
Redis uses key and value storage, and the maximum length of key and value is limited to 512M.
Redis has 16 databases by default. This can be modified in the configuration file redis.conf:
databases 16
These 16 databases are named with numbers 0-15 and do not support the modification of names, and the data between the databases is not isolated . For example, if we switch to any database, execute the command flushhall to clear the data of all databases, so It is not recommended to isolate different business system data through a database, but we can set it to different databases for different modules in the same business system.
Commonly used database operation commands
- Switch database. After switching the database, the current database number will be displayed. The default number 0 database does not display the number.
select 数据库编号

As you can see from the figure below, we set the value in database 0, so we can't get the value in other databases:

- Clear the current database
flushdb
- Clear all databases
flushall
Redis data type
There are 9 data types supported in Redis up to version 5.0.5. They are:
- 1, Binary-safe strings (binary safe strings)
- 2, Lists (list)
- 3. Sets
- 4. Sorted sets (ordered set)
- 5. Hashes
- 6、Bit arrays (or simply bitmaps)(位图)
- 7、HyperLogLogs
- 8、 geospatial
- 9、Streams
Although 9 types are listed here, the first 5 are the most commonly used.
In Redis, different types of commands are provided for each data type. Let us introduce them in turn.
1.Binary-safe strings (binary safe strings)
The string type is the most widely used type, and the key value in Redis can only be stored as a string, while the value can support 9 data types.
Strings in Redis can store three data types:
- String
- Integer
- Floating point
So our string type operation commands also include auto-increment commands, let’s take a look at the common operation commands of string type
Common commands
Here are several commonly used operating commands:
- Set value (only a single key and value can be set)
set key value
- Set value (multiple key and value)
mset key1 value1 key2 value2
- Take a single value
get key
- Take multiple values
get key1 key2

- View all the keys of the current database (use this operation with caution, if there are too many key values, it may directly crash)
keys *
- View the total number of current database keys (return an integer)
dbsize
- Check whether the key exists in the current database (returned is an integer: 0-no1-yes)
exists key
- Rename key
rename oldKey newKey

- Delete key (multiple separated by spaces, the return is the number of successfully deleted keys)
del key

- View key type
type key

- Increment by 1 (if value is not an integer, an error will be reported)
incr key
- Increment the specified size (if value is not an integer, an error will be reported)
incrby key 需要自增的数字

- Set the value, if the key already exists, the setting fails
setnx key value # 设置单个key
mset key1 value1 key2 value2 # 设置多个key

PS: setnx and mset are atomic operations. They must all be set successfully to return true. There are also parameters to set the expiration time. Generally, distributed locks are implemented based on this command with expiration time.
- Set key with expiration time
set key value EX|PX 18 # EX表示秒,PX表示毫秒
The following example is set to automatically expire after 5 seconds

- Set the expiration time individually. However, in order to ensure atomicity, we always use the above set command with time directly.
expire key
Application scenario
The application scenarios of the string type are very rich. Normal hot data can be cached using the string type. The following scenarios can be mainly applied:
- 1. Hotspot data and its object cache
- 2. Distributed Session Sharing
- 3. Distributed lock (using setnx command)
- 4. Redis is deployed independently and can be used as a globally unique ID
- 5. Using its atomic increment command, it can be used as a counter or current limit, etc.
2.Lists
The elements inside the List in Redis are also strings, and we can add the specified element to the specified position in the list. Operation commands for list data types generally start with a lowercase letter l.
Common commands
Look at some commonly used operating commands:
- Insert one or more values into the head of the list key, create a key if the key does not exist
lpush key value1 value2
- Insert value into the head of the list key, and do nothing if the key does not exist
lpushx key value1 value2
- Remove and return the head element of the key value
lpop key
- Insert one or more values into the end of the list key, create a key if the key does not exist
rpush key value1 value2
- Insert one or more values into the end of the list key, and do nothing if the key does not exist
rpushx key value
- Remove and return the last element of the key value
rpop key
- Returns the length of the key list
llen key
- Returns the element whose index is index in the key list. The head starts at 0 and the tail starts at -1
lindex key index
- Returns the elements between the subscripts start (inclusive) and stop (inclusive) in the key list
lrange key start stop
- Set the value to the specified index position in the key list. If the key does not exist or the index is out of range, an error will be reported
lset key index value
- Intercept the elements between [start,end] in the list and replace the original list to save
ltrim key start end

3.Sets
The collection in Redis is an unordered collection of String type, and the elements in the collection are unique and cannot be repeated.
Common commands
Set set operation commands generally start with s. Here are some commonly used commands:
- Add one or more element members to the set key, and return the number of successful additions, if the element already exists, it will be ignored
sadd key member1 member2
- Determine whether the element member exists in the set key
sismember key member
- Remove the elements in the set key, the non-existent elements will be ignored
srem key member1 member2
- Move the element member from the set source to dest, if member does not exist, do nothing
smove source dest member
- Return all elements in the collection key
smembers key

4.Sorted Sets (ordered set)
The difference between an ordered set and a set in Redis is that each element in an ordered set is associated with a double-type score, and then the scores are arranged in ascending order.
Common commands
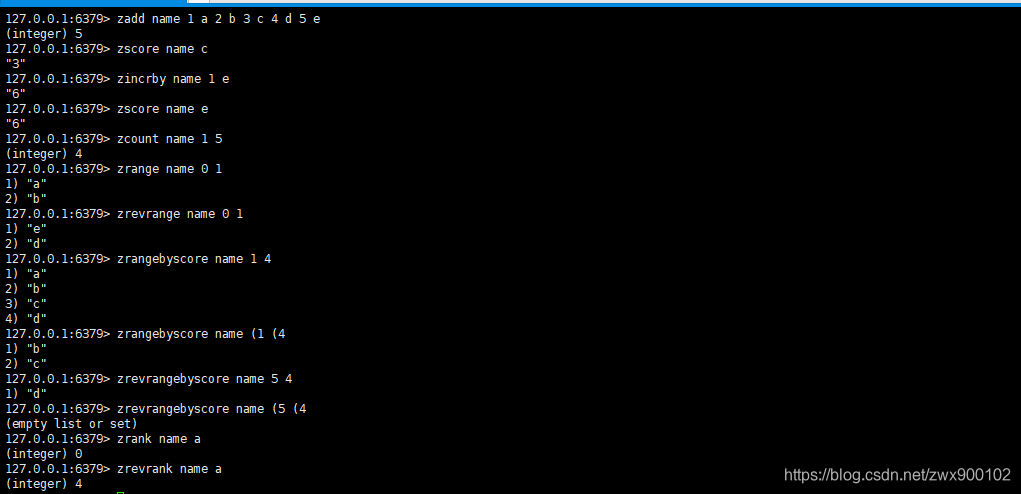
The operation commands of Sorted Sets generally start with z. Here are some commonly used commands:
- Add one or more elements member and its score to the ordered set key
zadd key score1 member1 score2 member2
- Returns the score of the member member in the ordered set key
zscore key member
- Add num to the member in the ordered set key, num can be negative
zincrby key num member
- Returns the number of members whose score value is between min (inclusive) and max (inclusive) in the ordered set key
zcount key min max
- Return all members between start (inclusive) and end (inclusive) after the score in the ordered set key is arranged from small to large
zrange key start stop
- Return all members between start (inclusive) and end (inclusive) after the score in the ordered set key is arranged from large to small
zrevrange key start stop
- Returns all the elements of the score from min to max in the ordered set, sorted by score from small to large. Note that the default is the closed interval, but you can add (or [to control the opening and closing interval in front of max and min
zrangebyscore key min max
- Returns all the elements of the score from max to min in the ordered set, sorted by score from largest to smallest. Note that the default is the closed interval, but you can add (or [to control the opening and closing interval
zrevrangebyscore key max min
- Returns the ranking of the elements in the member in the ordered set (from small to large), and the returned result is calculated from 0
zrank key member
- Returns the ranking of the elements in the member in the ordered set (from large to small), and the returned result is calculated from 0
zrevrank key member
- Returns the number of members between min and max in the ordered set. Note that the min and max in this command must be preceded by (or [to control the opening and closing interval , the special values-and + represent negative infinity and positive infinity, respectively
zlexcount key min max
5.Hashes
What is stored in the hash table is a key and value mapping table. Commands for operating hash data types generally start with h.
Common commands
Here are some examples of commonly used commands:
- Set the value of the field field in the hash table key to value
hset key field value #设置单个field
hmset key field1 value1 field2 value2 #设置多个field
- Set the value of the field field in the hash table key to value, if the field already exists, do nothing
hsetnx key field value
- Get the value corresponding to the field field in the hash table key
hget key field
- Get the value corresponding to multiple fields in the hash table key
hmget key field1 field2
- Delete one or more fields in the hash table key
hdel key field1 field2
- Returns the number of fields in the hash table key
hlen key
- Add the increment increment to the value of the field field in the hash table key. The increment can be a negative number. If the field is not a number, an error will be reported
hincrby key field increment
- Add incremental increment to the value of the field field in the hash table key. The increment can be a negative number. If the field is not a float type, an error will be reported
hincrbyfloat key field increment
- Add the increment increment to the value of the field field in the hash table key. The increment can be a negative number. If the field is not a number, an error will be reported
hincrby key field increment
- Get all fields in the hash table key
hkeys key
- Get the values of all fields in the hash table
hvals key

Application scenario
The hash type is actually very similar to the string type, so basically everything a string can do, hash can do, and in some scenarios, it will be more efficient to use hash classification storage.
6.Bit arrays (or simply bitmaps)位图
Bitmap bitmap is to set 0 or 1 through the smallest unit bit, which indicates the value or state corresponding to an element, and its value can only be 0 or 1, indicating yes or no. So this is generally used to count whether it is logged in, whether it is saved or not, etc.
For example, the storage data format is generally: 100110000111, where 0 and 1 are the bit value, and the bit value of the specified position (offset) can be set when setting.
PS: The underlying storage data structure of the bitmap is also a string object.
Common commands
The bitmap data type mainly provides the following commands:
- For the string value stored in the key, set or clear the bit value on the specified offset offset. The offset parameter must be greater than or equal to 0 and less than 2^32 (bit mapping is limited to 512 MB).
setbit key offset value
- Get the bit value at the specified offset offset
getbit key offset
- Calculate the number of bits set to 1 in a given string, start and end can be omitted to count all, 0 means the first digit, -1 means the last digit
bitcount key [start] [end]
- Returns the position of the first binary bit in the bitmap, start and end can be omitted, 0 means the first bit, -1 means the last bit
bitpos key bit [start] [end]

Application scenario
This is generally used in all-or-nothing scenarios, such as whether to log in, whether to keep the user, whether to collect goods, whether to like, etc.
7.HyperLogLogs
HyperLogLog is a newly added data structure used for cardinal statistics algorithms in Redis 2.8.9. The advantage is that when the number or volume of input elements is very large, the space required to calculate the base is always fixed and small. This data structure is generally used to count information such as UV.
HyperLogLog itself is an algorithm, which comes from the paper "HyperLogLog the analysis of a near-optimal cardinality estimation algorithm", if you are interested in this algorithm, you can go to know.
In Redis, each HyperLogLog key only needs 12KB of memory to calculate the base of close to 2^64 different elements, but it may also have an error rate of 0.81%.
PS: The underlying storage data structure of HyperLogLogs is also a string object.
Common commands
This data type mainly provides the following three commands:
- Add any number of elements to the key in the specified HyperLogLog
pfadd key element1 element2
- Get the cardinality of one or more keys
pfcount key1 key2
- Combine multiple sourcekeys into one destkey, the cardinality of the combined destkey is close to the union of all sourcekeys before the merge
pfmerge destkey sourcekey1 sourcekey2

From the above, we can see that there is no command to take out after it is stored, so this is generally used for statistics and needs to be able to accept errors.
For example, in the above example, if u1 u2 u3 u4 is the user id, then I don’t need to judge, as long as the user visits the webpage once, I will save it once, and the last value retrieved through pfcount is the value after deduplication (that is, the above Said base) , although there is a certain error, but statistical data such as uv is acceptable.
Application scenario
This is generally used in data statistics that can accept error scenarios, such as UV statistics and other scenarios
8.geospatial (geographical location)
Geospatial is a new type of geospatial index data with radius query added in Redis version 3.2. Generally used to store and calculate the distance between two places.
PS: The underlying storage data structure of HyperLogLogs is also an ordered collection of objects.
Common commands
Here are some commonly used commands:
- Add the given space element (latitude, longitude, name) to the specified key. The effective longitude is between -180 degrees and 180 degrees, and the effective latitude is between -85.05112878 degrees and 85.05112878 degrees.
geoadd key longitude latitude member
- Return the position (longitude and latitude) of all elements at the given position from the key.
geopos key member1 member2
- Returns the distance between two given locations. The default unit is meter (m), which can be specified by unit. The unit supports the following types: meters (m), kilometers (km), miles (mi), feet (ft).
geodist key member1 member2 [unit]
- With the given longitude and latitude as the center, return all the location elements whose distance from the center does not exceed the given maximum distance among the location elements contained in the key.
georadius key longitude latitude radius m|km|ft|mi [WITHCOORD] [WITHDIST] [WITHHASH] [ASC|DESC] [COUNT count]
- With the given element as the center, return all the position elements whose distance from the center does not exceed the given maximum distance among the position elements contained in the key.
georadiusbymember key member radius m|km|ft|mi [WITHCOORD] [WITHDIST] [WITHHASH] [ASC|DESC] [COUNT count]
The last two commands are basically the same, one is to specify the latitude and longitude, and the other is to automatically read the latitude and longitude of an element. The main parameters are as follows (the unit will not be repeated):
- WITHDIST: While returning the position element, the distance between the position element and the center is also returned. The unit of distance is consistent with the range unit given by the user.
- WITHCOORD: Return the longitude and latitude of the location element together.
- WITHHASH: In the form of a 52-bit signed integer, returns the ordered set score of the position element after the original geohash code. This option is mainly used for low-level applications or debugging, and has little effect in practice.
- ASC: According to the position of the center, the position element is returned from near to far.
- DESC: According to the position of the center, the position element is returned from far to near.
- COUNT: Specify the number of returns. It has little impact on computing performance, but if there are many areas returned, using count can save bandwidth
Application scenario
This application scenario is obvious, and it is only needed for scenarios that need to calculate geographic location.
9.Streams
Streams is a data type introduced by Redis5.0. The durable message queue that supports multicast is used to implement the publish and subscribe function. The design of Streams draws on Kafka. Stream is the most complex data type in Redis. We will not introduce it here. When we introduce the distribution/subscription function later, we will introduce this data type and its powerful and complex operation API separately.
to sum up
This article mainly introduces 9 basic data types in Redis and their commonly used operation commands and application scenarios for analysis. The data types in Redis are very rich. Although the string type is sufficient in most cases, in some specific scenarios Using specific types will be more efficient and elegant.
In the next article, we will introduce the underlying data structure of data types in Redis.
Please pay attention to me and learn and progress with the lone wolf .