This series of related blog, reference geeks time - Something about network protocol
Fun Talking about Network Protocol-Lecture 24 | Cloud in the Internet: The cost of owning land is high, and it is more flexible to buy an apartment
As we mentioned earlier, there are a large number of large machines stacked in the data center, connected by a network. Once the number of machines is very large, people find that maintaining such a large number of machines is quite troublesome, and there are many inflexible places.
- Purchasing is not flexible: if a customer needs a computer, it needs to purchase, put on the shelf, plug in the network cable, and install the operating system by itself. The cycle is very long. Once the purchase is used, it will be N years, and the product cannot be returned. Even if the business is not done, the machine remains in the data center.
- Operation and maintenance are not flexible: Once you need to expand the CPU, memory, and hard disk, you need to go to the computer room to get it manually, which is very troublesome.
- Inflexible specifications: Purchased machines tend to move hundreds of gigabytes of memory, and each application may only require 4 cores and 8G, so many applications are mixed on it, and various port conflicts are likely to affect each other.
- Reuse is not flexible: a machine, once one user does not use it, to another user, you need to reinstall the operating system. Because the original operating system may leave a lot of data, it is very troublesome.
From physical machine to virtual machine
In order to solve these problems, people invented something called a virtual machine, and based on it produced a cloud computing technology.
In fact, you can use the virtual machine on your personal computer. If you have no idea about virtual machines, you can download a desktop virtualization software and try it yourself. It allows you to flexibly specify the number of CPUs, memory size, hard disk size, you can have multiple network cards, and then create one or more virtual computers in a laptop. When not in use, there will be no deletion at all.
In the data center, there is a similar open source technology qemu-kvm , which allows you to take out a small machine in a huge physical machine. This set of software can solve the above problems: one point can be created, one point can be destroyed. As big as you want, every time you create a new system.
We often compare the physical machine to building a house with our own land, while the virtual machine is equivalent to buying an apartment. It is more flexible and can be bought and sold at any time . So why can this software do these things?
It uses software to simulate hardware . Just now, qemu-kvm used in the data center. From the name, emu means Emulator (emulator), which mainly simulates CPU, memory, network, and hard disk, making the virtual machine feel that it is using an independent device, but when it is actually used, of course, it is still a physical device.
For example, multiple virtual machines use physical CPUs in turn, and memory is also mapped using virtual memory, which is ultimately mapped onto physical memory. The hard disk creates an N-G file on a large file system and serves as the hard disk of the virtual machine.
Simple analogy, virtualization software is like a "cheater", "cheat" the applications in the virtual machine, so that they feel exclusive resources, in fact, they have nothing, all from the physical machine.
The principle of virtual network card
How does the network "cheat" the application? How to connect the network of virtual machine and the network of physical machine?
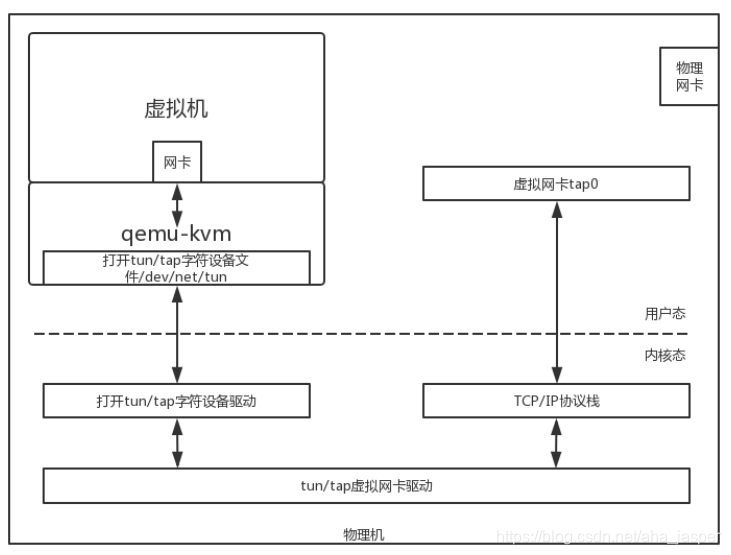
First, the virtual machine must have a network card. For qemu-kvm, this is achieved through a TUN / TAP technology on Linux .
A virtual machine is a piece of software running on a physical machine. This software can open a Char Dev (character device file) called TUN / TAP just like other applications . After opening the character device file, you can see a virtual TAP network card on the physical machine .
As a "cheater", the virtualization software will virtualize a network card in the virtual machine to let the applications in the virtual machine feel that they really have a network card. So all network packets are sent here.
Of course, the network package will go to the virtualization software . It will be converted into network packet file stream, write a character device , like writing a file the same. The TUN / TAP character device driver in the kernel will receive the written file stream and give it to the virtual network card driver of TUN / TAP . This driver converts the file stream into a network packet again, and hands it to the TCP / IP protocol stack. It is finally sent from the virtual TAP network card and becomes a standard network packet .
In this way, after changing hands, the data was finally sent from the virtual machine to the outside of the virtual machine.
Virtual network card connected to the cloud
We just have a virtual TAP network card. The next step is to see how this card is connected to the huge data center network.
Before connecting, let's take a look at what points need to be paid attention to in the cloud computing network.
- Sharing : Although each virtual machine will have one or more virtual NICs, there may be only a limited number of NICs on the physical machine. How do so many virtual network cards share the same outlet?
- Isolation : There are two aspects. One is security isolation . Two virtual machines may belong to two users. How to ensure that one user's data is not eavesdropped by another user? One is traffic isolation , two virtual machines, if there is a crazy film will not cause the other one can not go online?
- Interworking : There are two aspects. One is if two virtual machines on the same machine belong to the same user, how do the two communicate with each other? The other is if two virtual machines on different physical machines belong to the same user, how do these two communicate with each other?
- Flexible : Virtual machines are different from physics. They are often created and deleted, and drift from one machine to another. Some are interoperable and others are not. The flexibility is much better than the physical network and needs to be flexibly configured.
Sharing and interoperability issues
We will solve these problems one by one.
First of all, there are multiple virtual machines and multiple virtual NICs on a physical machine. How can these virtual NICs be connected together for mutual access and can access the external network?
How should virtual machines be connected?
Remember what we did in the university dormitory? You can imagine that your physical machine is your dormitory and the virtual machine is your personal computer. How should these computers be connected? ** Of course you should buy a switch.
On the physical machine, there should be a virtual switch. On Linux, there is a command called brctl , which can create a virtual bridge brctl addbr br0 . After the creation, connect the virtual network cards of the two virtual machines to the virtual bridge brctl addif br0 tap0, so that the two virtual machines are configured with the same subnet segment, and the two virtual machines can communicate with each other .
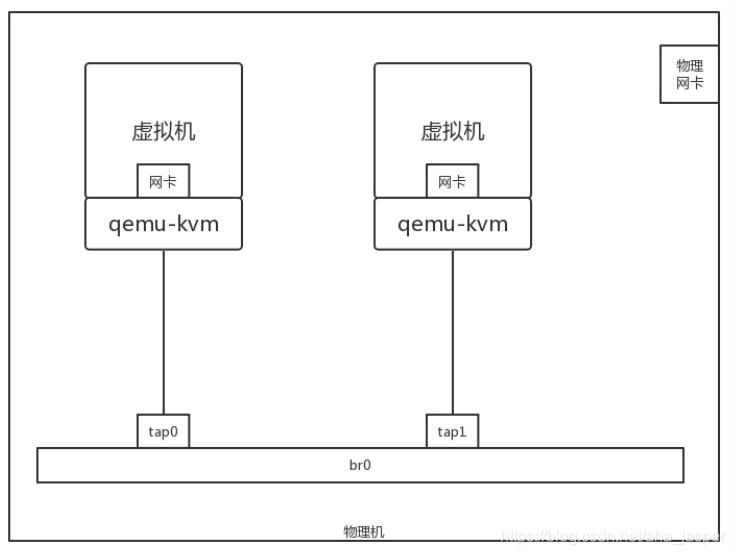
How do virtual machines connect to the Internet?
How do
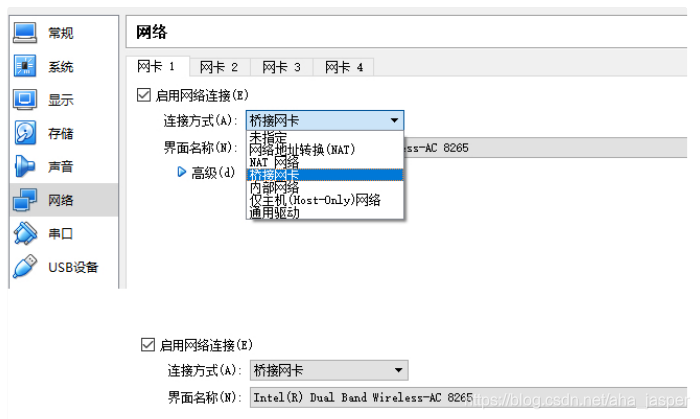
these virtual machines connect to the Internet? On the desktop virtualization software, we can see the following options. Here, the host-only network corresponds to the fact that the above two virtual machines are connected to a br0 virtual bridge , and regardless of the scenario of accessing the outside, as long as the virtual machines can access each other .
If you want to access the outside, there are often two ways.
bridging
One way is called bridging . If you choose to bridge the network on the desktop virtualization software, the following structure will be formed on your laptop.
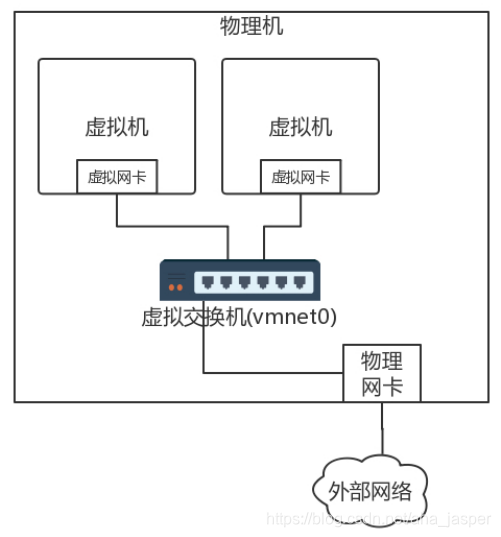
Each virtual machine will have a virtual network card. On your laptop, you will find a few more network cards, which are actually virtual switches. This virtual switch connects the virtual machines together. In the bridge mode, the physical network card is also connected to this virtual switch, and the physical network card is selected on the desktop virtualization software under " Interface Name ".
If you use a bridged network, when you log in to the virtual machine and look at the IPW, you will find that the address of your virtual machine is on the same network segment as that of your laptop and your colleague ’s computer. Why is this? This is actually equivalent to putting the physical machine and the virtual machine on the same network bridge. It is equivalent to having three machines on the network bridge, all of which are on the same network segment. I'll understand the picture as follows.
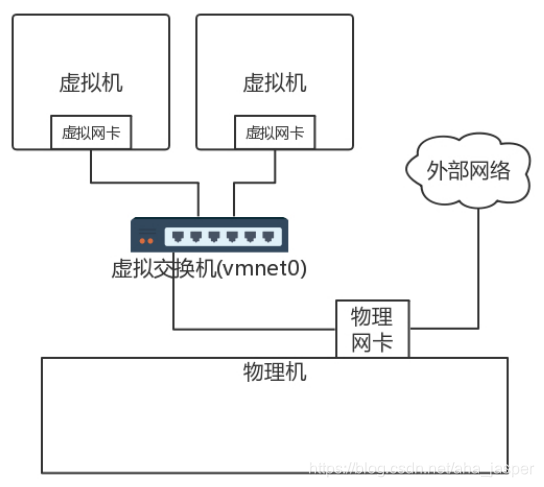
In the data center, the similar technology is adopted, but it is all Linux. A bridge br0 is created on each machine, the virtual machine's network card is connected to br0, and the physical network card is also connected to br0. All br0 Connected to the physical switch through the physical network card.
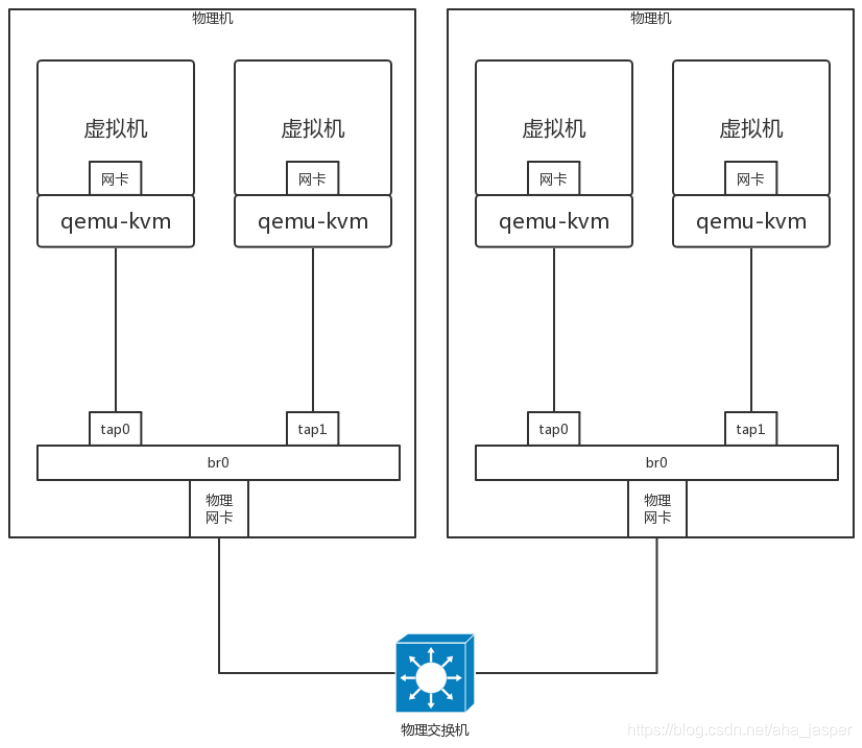
We also look at this topology from another angle. The same is to tie the network, the virtual opportunity and your physical network have the same network segment.
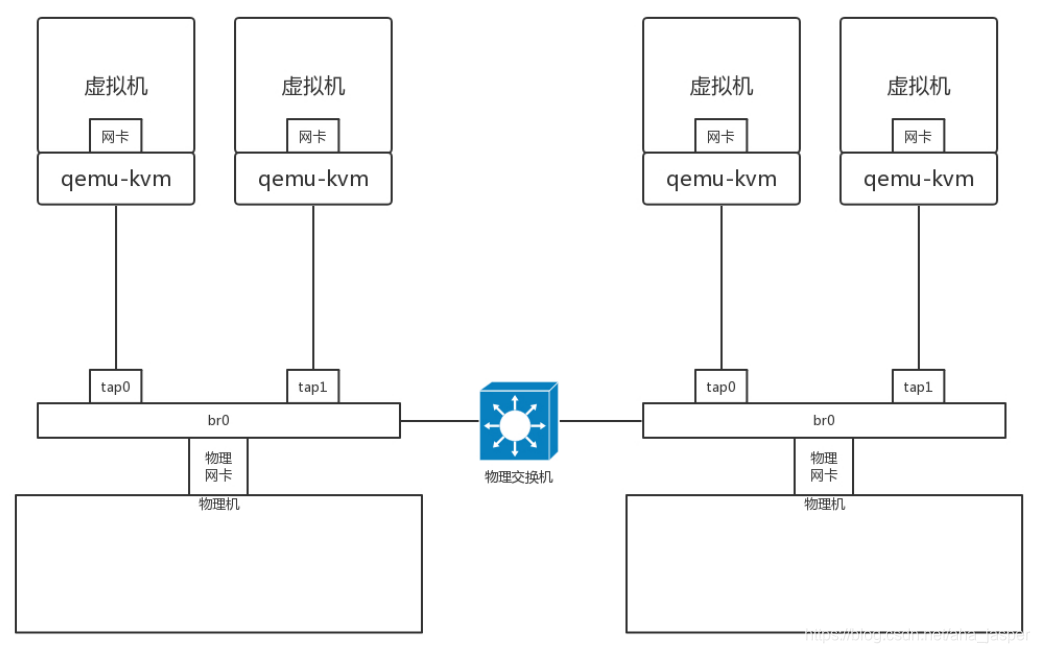
In this way, not only the interoperability problem of the same machine, but also the inter-physical machine interoperability problem is solved , because they are all in a Layer 2 network, and they can be accessed by the same network segment. But when the scale is large, there will be problems .
Do you remember? In a Layer 2 network, the biggest problem is broadcasting. There are already many physical machines in a data center. Broadcasting is already very serious and needs to be divided by VLAN. If a virtual machine is used, it is assumed that 10 virtual machines are created in a physical machine, all in a layer 2 network, and the broadcast will be very serious, so unless your desktop virtual machine or data center is very small, you can Use this relatively simple way.
NAT
Another way is called NAT. If you use NAT mode in desktop virtualization software, the following network structure will appear on your laptop.
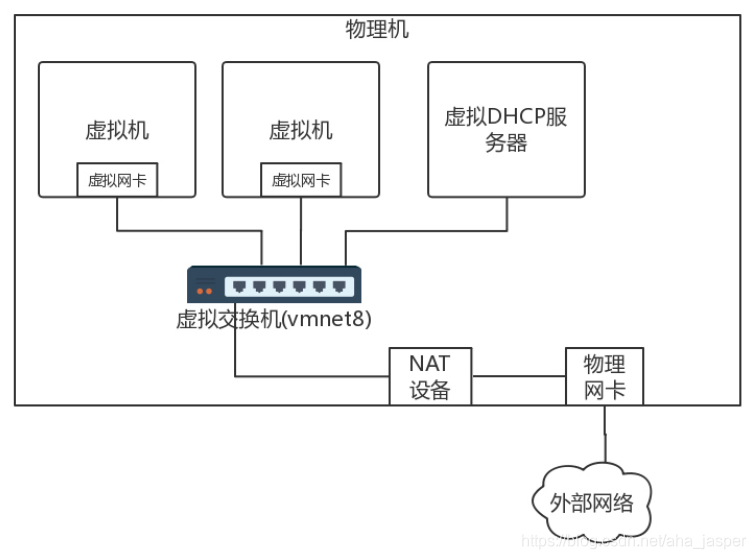
In this way, when you log in to the virtual machine and check the IP address, you will find that the network of the virtual machine is a virtual machine, and the network of a physical machine is a physical machine. The two are different. When a virtual machine wants to access a physical machine, it needs to NAT the address to the address of the physical machine.
In addition, it will also have a DHCP server built into your laptop to dynamically assign IP addresses to virtual machines on the laptop. Because the network of virtual machines is self-contained, IP management is required. Why is the bridge method not required? Because the bridge leveled the network, the IP address of the virtual machine should be assigned by the DHCP server of the physical network.
In the data center, a similar approach is used. This method is more like really moving the situation in your dormitory to a physical machine.
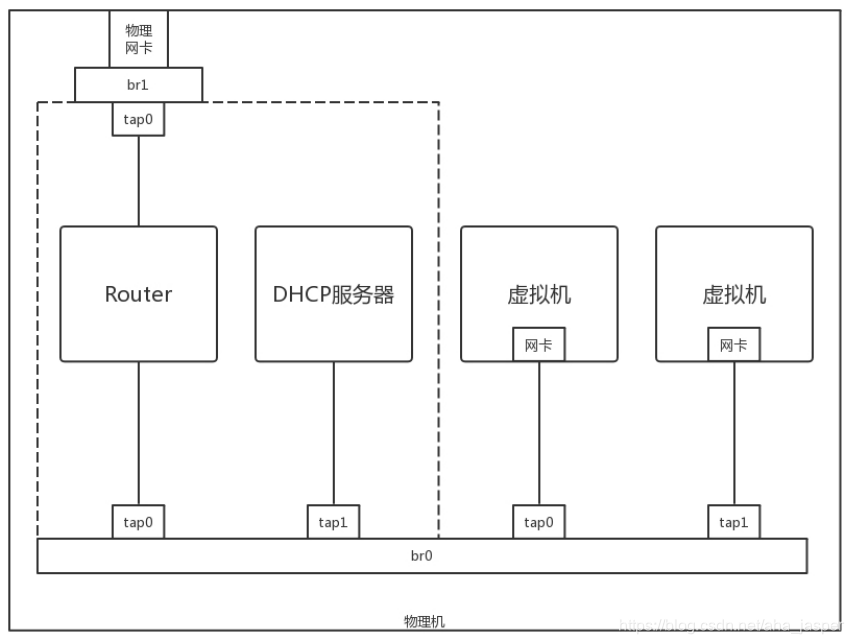
The virtual machine is your computer. The router and DHCP server are equivalent to a home router or bedroom computer. The physical network card is equivalent to the external network port of your dormitory for accessing the Internet. All computers are connected to a bridge br0 through the internal network port. To access the Internet, the virtual machine needs to be connected to the router through br0, and then the router will request the NAT to become the address of the physical network and forward it to the physical network.
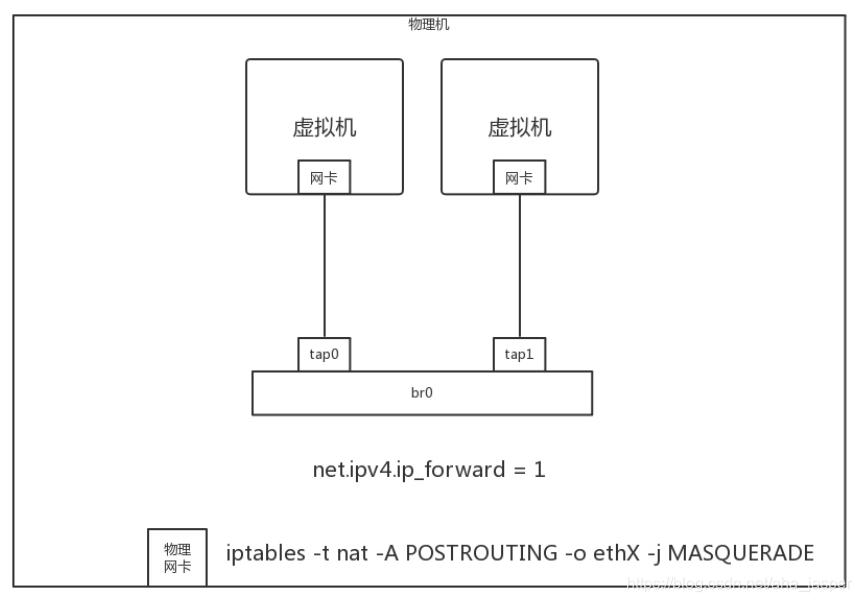
If you log on to the physical machine and make a simple configuration, you can simplify it. For example, the gateway address of the network where the virtual machine is located is directly configured on br0, without using a DHCP server, manually configure the IP address of each virtual machine, through the command iptables -t nat -A POSTROUTING -o ethX -j MASQUERADE, directly NAT on the physical network card ethX, all packets out of this network card NAT becomes the address of this network card. Through the setting net.ipv4.ip_forward = 1, the forwarding function of the physical machine is enabled, and the router is directly used instead of a separate router, so that the virtual machine can directly access the Internet.
Isolate the problem
Solve the problem of interoperability, the next step is the problem of isolation.
What if two virtual machines on a machine do not belong to the same user? Fortunately , the bridge created by brctl also supports VLAN function, you can set the tag of two virtual machines, so that on this virtual bridge, the two virtual machines are not interoperable .
But how do you interwork across physical machines and achieve VLAN isolation?
Since the tag on the bridge created by brctl cannot work outside the bridge, we need to find other ways.
There is a command vconfig , you can create a virtual network card eth0 with VLAN-based physical network cards , all away from this virtual network adapter package, all with the VLAN, if so, interoperability across physical machines and isolation can be achieved by this card.
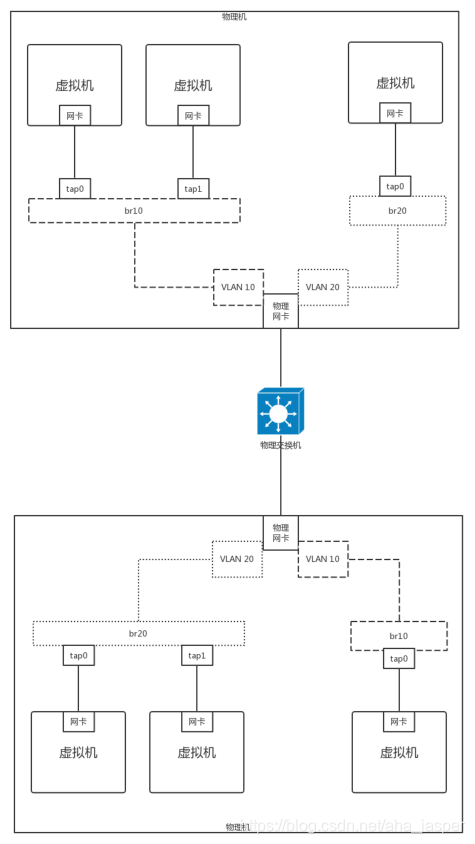
First assign different VLANs to each user, for example, there is one user VLAN 10 and one user VLAN 20. On a physical machine, based on the physical NIC, use vconfig to create a NIC with VLAN for each user. Different users use different virtual bridges, and virtual network cards with VLANs are also connected to the virtual bridges.
Can this guarantee the isolation of the two users? Different users cannot communicate with each other due to the bridge failure. Once the bridge is out, the packets will not be forwarded to another bridge due to different VLANs. In addition, the physical machine comes with a VLAN ID.
As long as the physical switch also supports VLANs, the VLAN ID is still there when it arrives at another physical machine, it will only forward packets to the same VLAN NIC and bridge, so across physical machines, different VLANs will not communicate with each other .
The bridge function created using brctl is simple, and VLAN-based virtual network cards can also achieve simple isolation. But this is not enough to meet large-scale cloud platforms, one is VLAN isolation, the number is too small . As we learned earlier, there are only 4096 VLAN IDs, which is obviously not enough. Another point is that this configuration is not flexible enough . Who can communicate with each other, and who cannot communicate with each other, traffic isolation has not been achieved , and there is a lot of room for improvement.
summary
Well, this section is here, let us summarize:
- The key technology of cloud computing is virtualization. Here we focus on the fact that the virtual network card connects the virtual machine inside and outside by opening the TUN / TAP character device
- The network in the cloud focuses on four aspects, sharing, isolation, interworking, and flexibility. Among them, there are two common methods for sharing and interworking, namely bridging and NAT, and isolation can be done through VLAN.
Next, leave you two thinking questions.
- For the sake of intuition, we will use the desktop virtualization system as an example in this section. In the data center, there is a well-known open source software OpenStack, which network connection mode in this section corresponds to which models in OpenStack?
- At the end of this section, we also mentioned that the network configuration methods mentioned in this section are less flexible. Do you know any more flexible methods?
