[CrackMe] 160 CrackMe 04
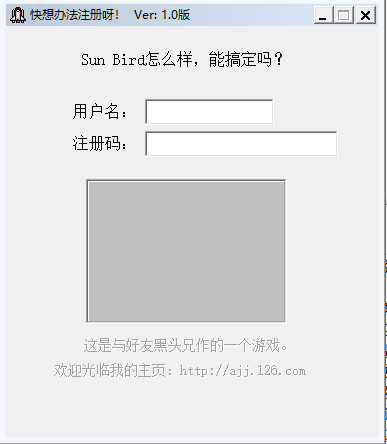
1. The following interface, enter the user name and password and click OK.
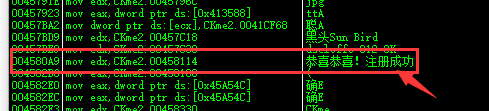
2. First use OD to search the string, and the following strings are found.
3. Key position, successful blasting method
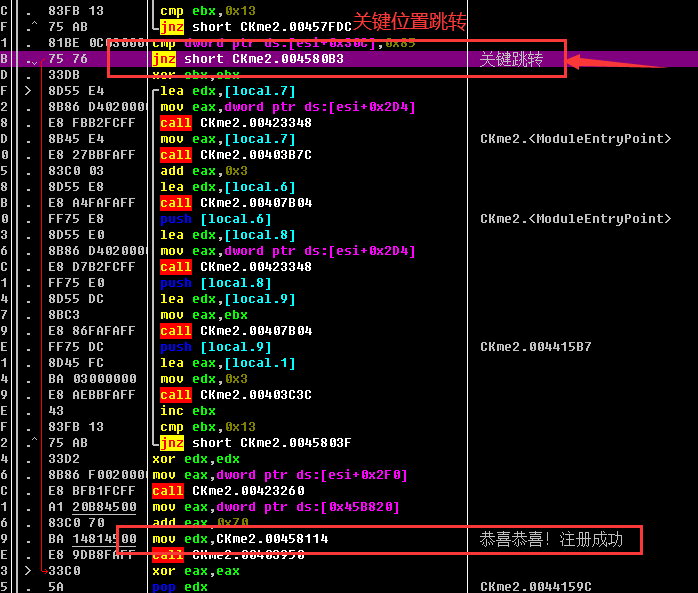
The blasting method was successfully cracked, and the following figure appeared.

4. Analyze key locations
Check that the memory is obviously 0, but there are some available memory below
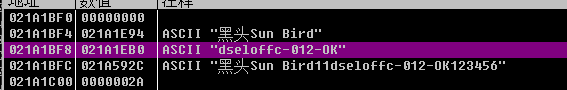
Corresponding account and password

The last line of code, Blackhead Sun Bird11dseloffc-012-OK123456 is very similar to the user name, which is obviously composed of the four attributes Blackhead Sun Bird 11 dseloffc-012-OK 123456.
We guessed it was a registration code, guessed a wave, and found success.
5. Set memory breakpoint analysis
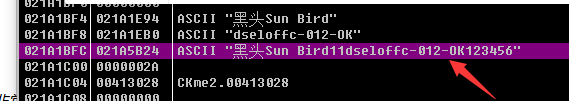
1) We will now check the memory write to it, check when to write, and write a breakpoint in the memory, and find that this is a system library, N multi-function write
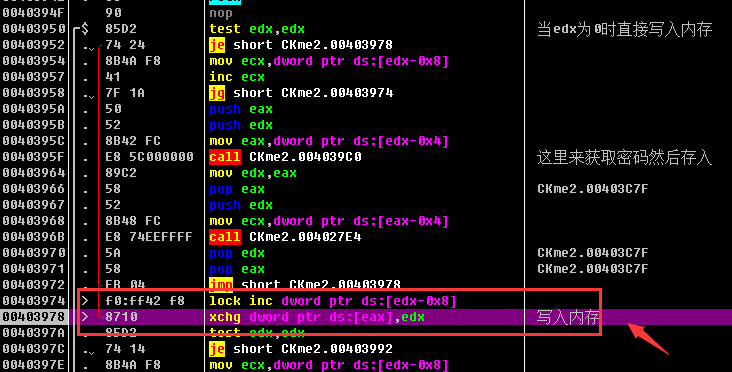
2) Keep following, follow CM.exe airspace, as follows:
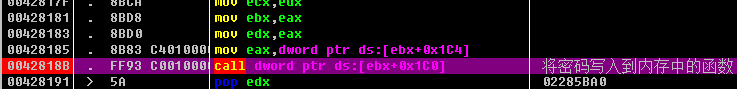
3) Re-enter again and find that its ebx points to a structure as a pointer, where the offset is fixed, as long as access to this memory must use this offset.

After clearing, come to reanalyze the algorithm, the algorithm is very clear:
There are four sets of data, one is the character string obtained by the length of the user name +5, and the rest are implemented by splicing as shown in the figure.
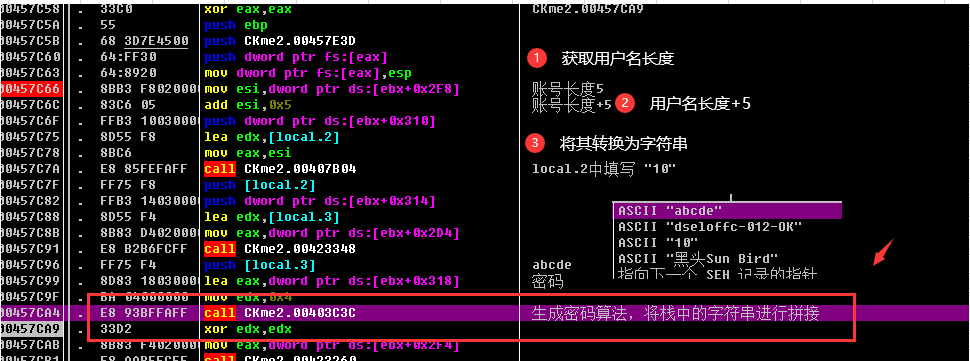
6. Registration machine preparation
It is relatively easy to write a registration machine, no difficulty
#include <stdio.h> #include <iostream> #include <sstream> #include <windows.h> using namespace std; int main() { string userName; stringstream ss; cin >> userName; ss << string("黑头Sun Bird") << userName.length() + 5 << string("dseloffc-012-OK") << userName; string password = ss.str(); cout << password; }