-
table of Contents
-
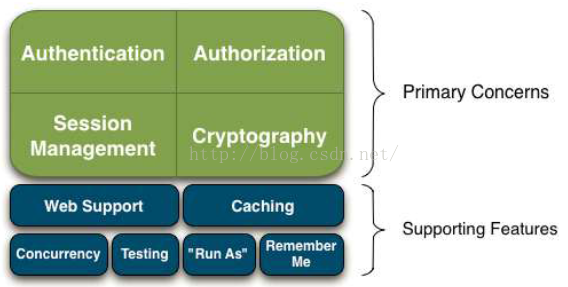
Composition: four major components, functional support
-
Shiro verification process
-
Configuration and examples
The four core functions of Shiro are also called "the four cornerstones of the Shiro application":
1. Authentication: Sometimes also referred to as "login" (authentication)
This is an act to prove that the user is who they say they are.
2.Authorization: The process of access control, that is, the absolute "who" accesses "what", that is, authorization.
3. Session Management: Session management:
manage user-specific sessions, even in non-Web or EJB applications, will be explained in detail later.
4. Cryptography: Keep data safe by using encryption algorithms.
1. Web Support: Shiro's web-supported API can easily help protect web applications.
2. Caching: Caching is the first-tier citizen in Apache Shiro to ensure safe and fast operation.
3. Concurrency: Apache Shiro uses its concurrency features to support multi-threaded applications.
4.Testing: The existence of testing support to help you write unit tests and integration tests, and ensure that you can be as safe as expected.
5. "Run As": a function that allows the user to assume the identity of another user (if allowed), sometimes useful in managing scripts.
6. "Remember Me": Remember the user's identity in the session, so they only need to log in when forced.
The first step is to get the subject of verification. The definition of this subject refers to:
Subject is a security term , which basically means
"the specific security view of the currently executing user". It is not called "User" because the word "User" is usually associated with humans. In the security world, the term "Subject" can be expressed as a human being, and it can be a third-party process, a cron job, a daemon account, or something similar. It simply means "this thing is currently interacting with the software" . For most intents and purposes, you can think of Subject as Shiro's "User" concept
/*获取验证的主体*/
Subject subject = SecurityUtils.getSubject();
/*获取Session*/
Session session = subject.getSession();
if(!subject.isAuthenticated()){ //验证通过
UsernamePasswordToken usernamePasswordToken = new UsernamePasswordToken("username","password");
/*设置记住账号*/
usernamePasswordToken.setRememberMe(true);
/*登录方法*/
subject.login(usernamePasswordToken);
}
/*退出登录*/
subject.logout();
Note: Session is a specific instance in Shiro, which is equivalent to HttpSession in the web environment; it can be used in the non-Web environment, and the scope of use is not limited to the web layer like HttpSession.
subject.login (usernamePasswordToken); The above exceptions may be thrown. These exceptions should be caught and processed at the same time.
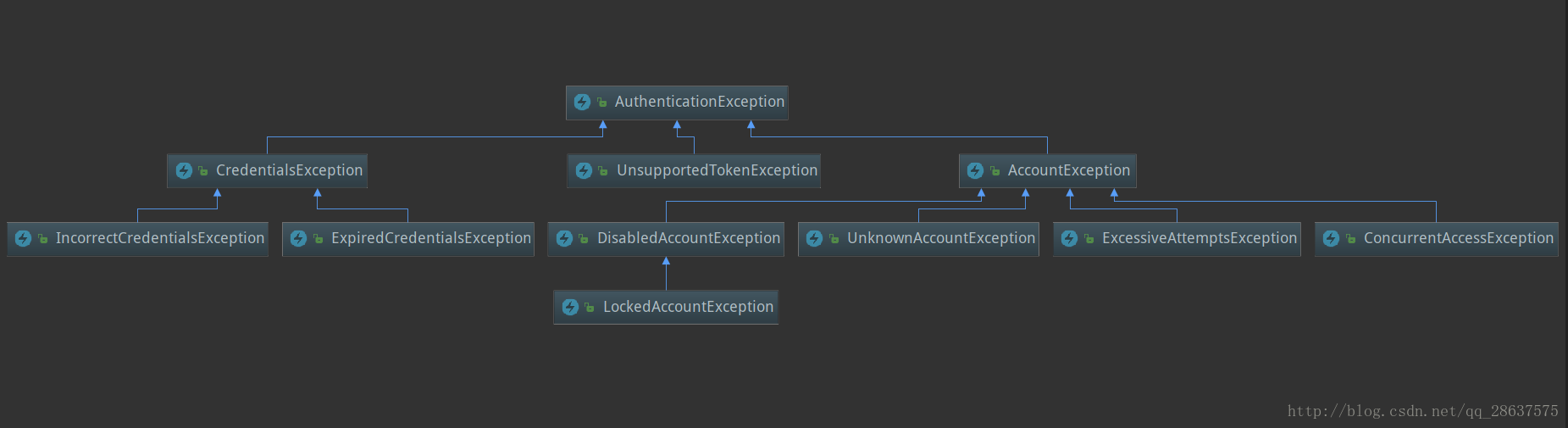
Common exceptions:
AuthenticationException contains the following subclasses:
- CredentitalsException Credential exception
IncorrentCredentialsException incorrect credentials
ExpiredCredentialsException Expired credentials
- AccountException
ConcurrentAccessException Concurrent access exception (thrown when multiple users log in at the same time)
UnknownAccountException Unknown account
ExcessiveAttemptsException The number of authentications exceeds the limit
DisabledAccountException Disabled account
LockedAccountException Account is locked
UnsupportedTokenException Unsupported token used
Handy Hint
's safest approach is to give ordinary login failure messages to users , because of course you don't want to help attackers who try to break into your system.
1.UnknownAccountException unknown account
Prompt message: The account does not exist, or the account password is inconsistent
2. IncorrentCredentialsException password error
3. LockedAccountException account is locked
Recently, I am working on a Spring boot blog system. The permission control uses the Shiro framework. The functions behind are improved, and my github will be released. I hope to give readers some help.
For advanced applications, see the next edition: