20,199,131 2019-2020-2 "network attack and defense practice 'Week 6 jobs
1. Practice content
1.1 Security Model
- Static security model: the network risk analysis, develop appropriate security policies, and to take security precautions as technology, mainly for fixed, static environment of threats and vulnerabilities.
- PDR security model: time-based closed-loop control theory models dynamically adapt to network security, network security in the classical inequality P> D + R (protection, detection, response) is essentially based, and proposed security quantifiable and calculable views .
- P2DR security model: PDR-based security model proposed, an increase of Policy Analysis formulate security policies, and as a core, all the protection, detection, response are based on the security policy implementation.
1.2 network security technology and systems
- Firewall technology and products
- Definitions : refers to the firewall between different network security domains placed, safety components or devices to access network traffic or behavior enforces access control, to protect specific network security domain from unauthorized access and damage security objectives.
- Function :
traffic to and from the network control checks.
Prevent vulnerable or insecure protocols and services.
To prevent the leakage of internal information network.
Network access and access to monitor the audit.
Strengthen the network security policy and integrate with other security defenses. - Deficiencies :
congenital : Unable to include prevention, spread spread via network attacks and illegal outreach of security threats from computer viruses within the network.
Technological bottlenecks: Unable to prevent penetration attacks for open services, including security vulnerabilities, a Trojan horse or botnet communications network penetration attacks against the client program and covert channels. - Technology :
packet filtering : to extend the routing function basis, through the examination of the network layer and the transport layer header information, according to the security policy rule set of user defined, determining whether to forward the data packet (simple, limited safety function).
Packet filter based on the detected state of the art: also known as dynamic packet filtering. In addition to using a static security policy rule matching security, also connected to the network context probe packets to determine whether to allow communication. This technology compared to traditional packet filtering technology more secure, the legitimacy of the data has been more effective protection (have an impact on network performance).
Agent Technology : allows clients to non-direct connection through a proxy and network services, also known as "Network Agent." The main client connection with the proxy server, proxy server and then connect with the target server. Techniques include application proxy agent (work in the application layer), circuit-level proxy (work in the transport layer) and NAT proxy (work in the network layer), and the like.
Deployment Method :
packet filtering router: a router with packet filtering firewall function.
Dual-homed bastion host: application proxy gateway as a dual-homed bastion host.
Screened Host: the bastion host and packet filtering binding.
Screened subnet: increasing the second track packet filtering router on the basis of the host screen.
1.3 iptable
- iptables Commands
iptables: administration tool for IPv4 / IPv6 packet filtering and NAT
1) Introduction: Linux kernel version 2.4 introduces a new packet processing engine Netfilter, as well as a command-line tool to manage it iptables. iptables is used to establish, maintain and checklists Linux kernel IPv4 packet filtering rules.
2) structure level: iptables - Table table - catena alberghiera chain (built-in or custom) - Rule (target certain clauses, etc.).
iptables packets on the network rules applied to "chain" orderly. Chain constitutes a set of tables, for processing a particular type of traffic.
The default table iptables filter (filter). It contains three default chains: FORWARD, INPUT and OUTPUT, each packet processing core to go through a chain 3 a. FORWARD chain in the rule for a network interface received, but also all the packets forwarded to another network interface. INPUT and OUTPUT chain rules are for the purpose of local host, or traffic from the local host.
Nat chain rule table contains controls the NAT (Network Address Translation). In addition, mangle, raw and security table, not detailed here.
Each rule constitutes a chain has a "target (target)" clause, which determines how to handle packages that match. Once a packet matches a rule, it will determine the outcome, no other rules to check it. Although the internal iptables defines a number of target, but still you can specify the other strand as a target rules. Filter rules table can be used with a target clause ACCEPT (packet may continue), DROP (silently discard the packet) and REJECT (discard the packet and return an ICMP error message) and the like.
-
iptable command arguments detailed:
Check status: iptables -Liptables parameter options:
-t <TABLE>: Specify the table to be manipulated;
-A: add an entry to the rule in the chain;
-D: delete the entry from the rule in the chain;
-i: inserting an entry to the rule in the chain;
-R: entry replacement rules chain;
-L: display rule entries already in the chain;
-F: clear rule entries already chain;
-Z: Empty rule in the chain calculator packet and byte counters;
-N: Create a new user-defined rules chain;
-P: The default target is defined rule in the chain;
-h: displays help information;
-p: Packet Type Specifies the protocol to match;
-s: Specifies the packets that match the source address ip;
-j <target>: Specifies the target to jump;
-i <Network Interface>: Specifies the packet enters the network interface of the machine;
-o <Network Interface>: Specifies the data packets leaving the network interface used by the machine.
2. practice
Practice One: Firewall Configuration
Practice Task: iptables configuration on the platform Linux, complete the following functions and tests
-
Filtering ICMP packets, so that the host does not accept ping packets.
-
Allow only specific IP addresses to access a host of network services, and other IP addresses can not access.
-
Experimental environment
kali (the accessing party IP: 192.168.200.8), Metasploitable2-Linux ( need to configure the firewall host IP: 192.168.200.10), SEEDUbuntu9-Aug -2010 ( access square 192.168.200.3) -
Experiments specific steps
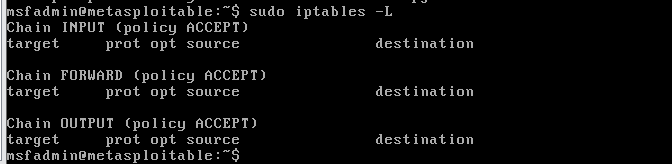
using the command: iptables -L, list all the rules in the rule chain view, is the default rule
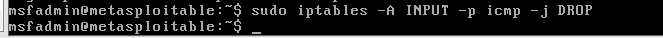
Use the command: iptables -A INPUT -p icmp -j DROP, rules for filtering ICMP packets, -A: adding the specified chain end (the append) a new rule ;-P: packet protocol specified to match the type of ; -j: Specifies the jump target (including DROP, ACEEPT, etc.);
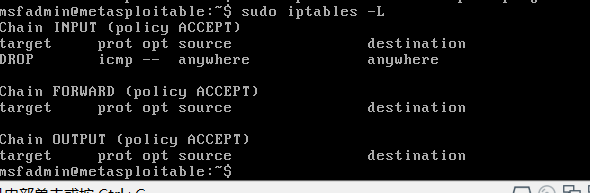
View all the rules listed in rule in the chain, has been added successfully found
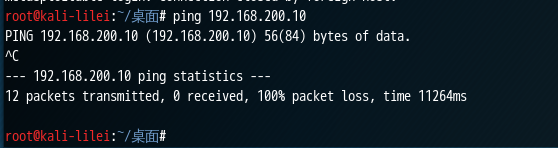
kali Ping longitudinal Metasploitable2-Linux configuration rule shown in FIG comparison:

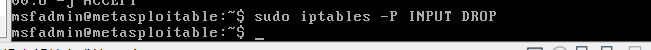
Use the command: sudo iptables -P INPUT DROP, traffic flow is closed all the ports of the local host of the machine
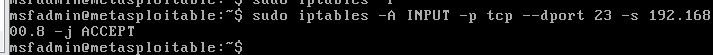
Use the command: sudo iptables -A INPUT -p tcp --dport 23 -s 192.168.200.8 -j ACCEPT, configure the rule to allow the host 192.168.200.8 IP can access native telnet
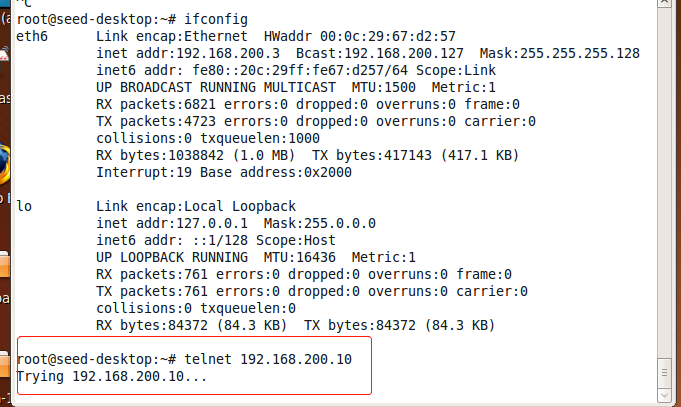
Were used kali and SEEDUbuntu9-Aug-2010 telnet login Metasploitable2-Linux, as shown, kali access to other hosts (including SEEDUbuntu9-Aug-2010) inaccessible

3. The problems and solutions encountered in the study
- Question 1: iptables command error
- Problem 1 Solution: iptables command parameters strictly case-sensitive
4. practice summary
xxx xxx