1. Practice content
1 computer network model
OSI model and the TCP / IP Model Comparison FIG.
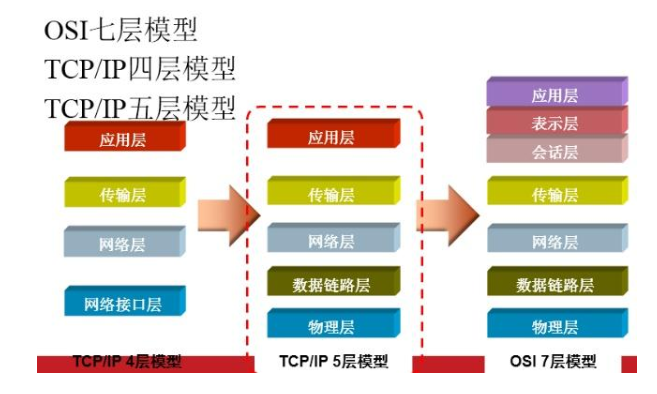
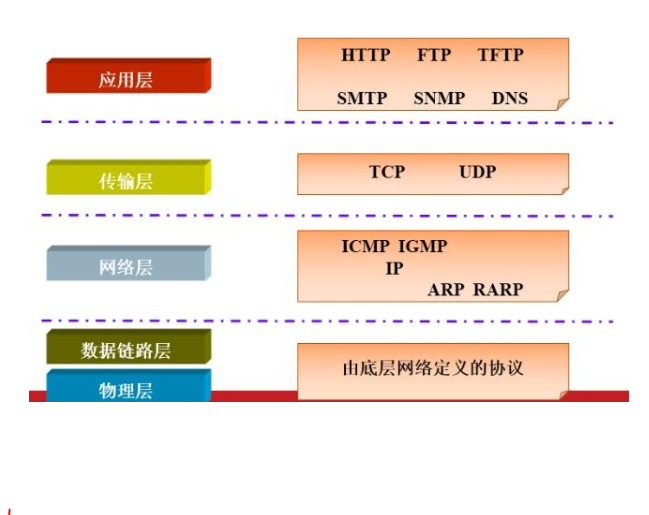
Composition TCP / IP protocol suite
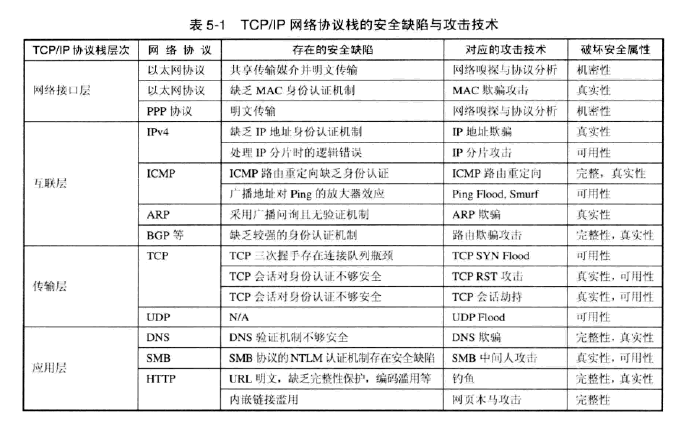
TCP / IP network protocol security flaws and total technology
2 network layer protocol ARP and ARP attack
ARP (Address Resolution Protocol, ARP) is located in a network layer TCP / IP protocol stack, responsible for parsing an IP address corresponding to the MAC address.
ARP protocol there is a lot of loopholes and shortcomings, caused great risks to computer networks.
1. First ARP protocol is broadcast sends an ARP request, as long as the host is the same network segment can receive, which for the attacker an opportunity to exploit, an attacker could send a large number of ARP request packet, blocking normal broadband network, so that the limited resources of the local area network are occupied by useless broadcast information, resulting in network congestion.
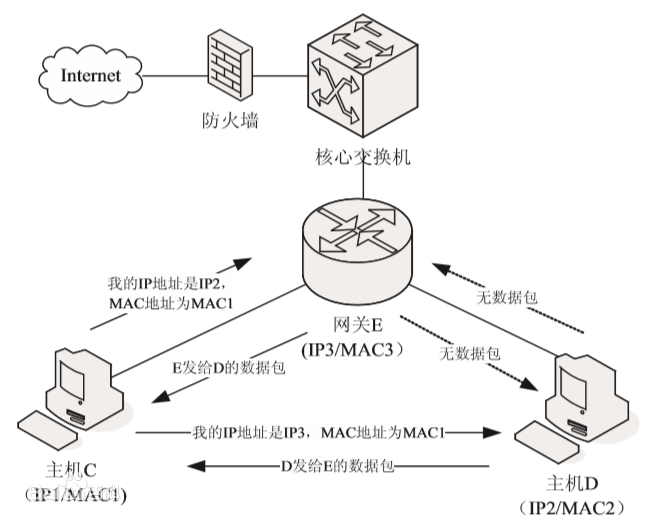
2. Second, ARP protocol is not secure authentication mechanism, because the hosts in the LAN is based on trust, so long as the host receives the ARP response packet, it will be cached in the ARP table, which provides the possibility for ARP spoofing. An attacker could send the wrong IP address mapping between MAC addresses.
ARP spoofing gateway theory of
ICMP redirection techniques are used to remind the host to change their routing host so that a routing path optimization ICMP packets. The concept is to understand the essence of the original host route is not the best route, and its default gateway to remind the host optimize their host routing and the message sent.
Typical topology best describes the ICMP redirect meaning is as follows:
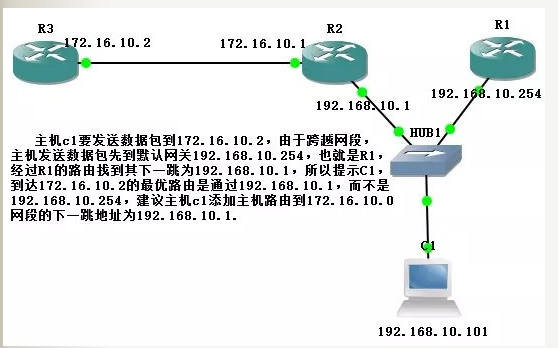
Based Routing ICMP redirect attack the principle of
redirection information ICMP routers provide real-time routing information to the host when a host receives ICMP redirect message, it will be based on this information to update their routing tables. Due to the lack of legitimacy of the examination necessary if a hacker wants to attack the host to modify its routing table, the hacker will send ICMP redirect messages to the host attack, let the host as required by hackers to modify the routing table.
Transport Layer 3 attacks
RST attack against this kind of attack can only tcp, udp for invalid. RST: (Reset the connection) is used to reset for some cause connection errors occur, and is also used to reject illegal data request. If you receive a RST bit time, usually some error has occurred.
RST attack schematic

Three-way handshake protocol
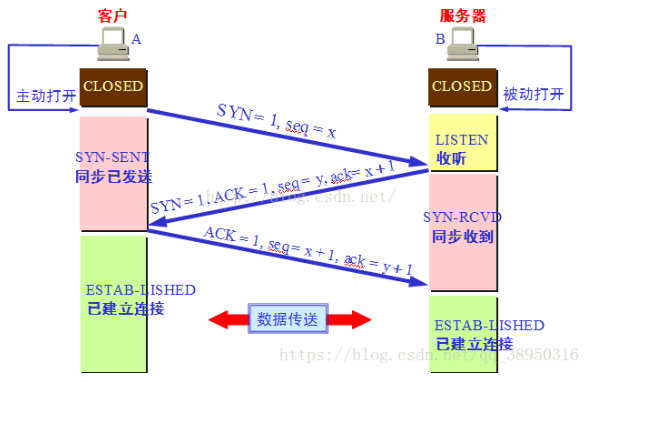
first handshake: a connection is established, the client sends syn packets (syn = x) to the server, and enters the SYN_SENT state, waiting for the server to confirm; the SYN: synchronization sequence number (Synchronize Sequence Numbers).
Second handshake: server receives syn packets, must confirm the customer SYN (ack = x + 1) , while themselves sends a SYN packet (syn = y), i.e., SYN + ACK packet, then the server enters a state SYN_RECV;
third handshake: the client receives the SYN + ACK packet to the server, the server sends an acknowledgment packet ACK (ack = y + 1) , this packet is sent, the client and server into the ESTABLISHED (TCP connection succeeds) state, complete the three handshake.
2. practice
Network attack and defense in the experimental environment (to SEED_VM as attack aircraft, Linux Metaspioitable / Windows Metasploitable as target drones) to complete TCP / IP protocol stack attack experimental points of the agreement, including the ARP cache spoofing attacks, ICMP redirect attacks, SYN Flood attacks, TCP RST attack and TCP session hijacking attacks (bonus).
The experiment SEED_VM as attack aircraft, Linux Metaspioitable as a target drone
attack aircraft SEED's IP is 192.168.92.4
host A Linux Metaspioitable drone IP is 192.168.92.125
host B Windows drone ip address is 192.168.92.124
3. The problems and solutions encountered in the study
- Question 1: XXXXXX
- Problem 1 Solution: XXXXXX
- Question 2: XXXXXX
- Problem 2 Solution: XXXXXX - ...
4. practice summary
xxx xxx