20,199,318 2019-2020-2 "network attack and defense practice," the sixth week of work
1. knowledge carding and summary
1.1 firewall functions
- Check the control network traffic in and out of the network
- Prevent vulnerable or insecure services and protocols
- Preventing the internal network information outsourcing
- Network access and access to monitor the audit
- Firewalls can strengthen the network security policy and integrate with other security defense mechanisms
Less than 1.2 firewall
- From the internal network security threats
- Cyber attacks by illegal outreach
- Computer viruses spread
security threats due to technical bottlenecks still unable to effectively guard against: - Open service penetration attacks against security vulnerabilities
- Penetration attacks against network client program
- Trojan horses, or bots for network communication based on covert channels
1.3 Firewall deployment methods:
- Packet filtering router
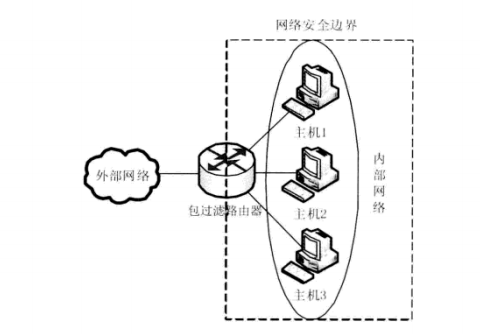
- Dual-homed bastion host
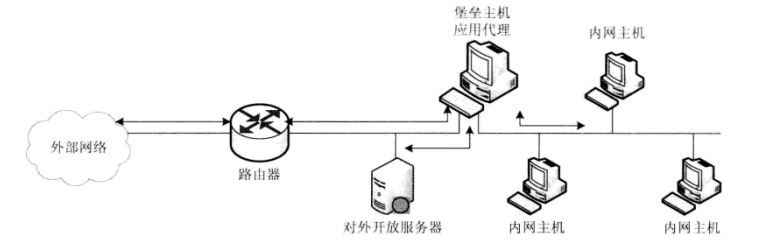
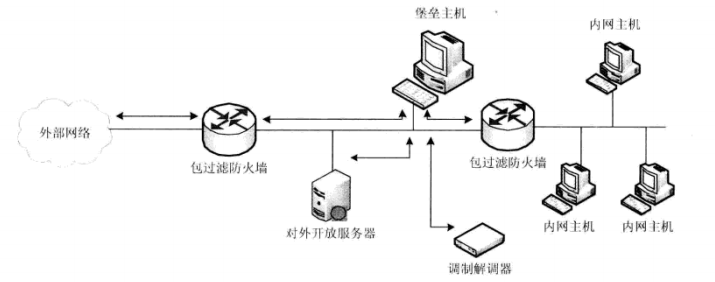
- Screened Host

- Screened subnet
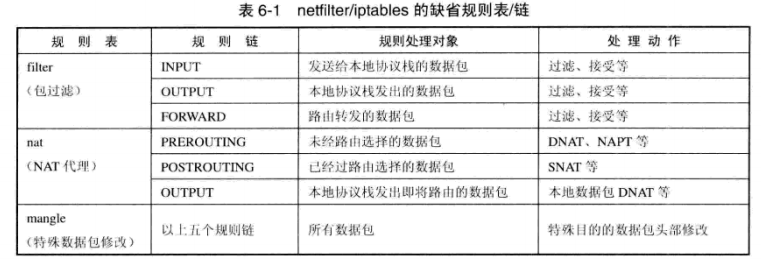
1.4 Linux open source firewalls: netfilter / iptables
-
working principle
在netfilter/iptables防火墙系统中,netfilter组件位于Linux的内核空间中,实现了静态包过滤和状态报文检査(即动态包过滤)基本防火墙功能,此外也支持一个灵活可扩展的框架,支持NAT网络地址转换等其他额外功能,并提供了多层API接曰以支持第三方扩展,netfilter具备构建防火墙、NAT共享上网、利用NAT构建透明代理,以及构建QoS或策略路由器等安全功能。Iptables则是工作在Linux用户空间中的防火墙配置工具,通过命令行方式允许用户为netfilter配置各种防火墙过滤和管理规则。
- Iptables provides users with a command-line interface to configure netfilter rules, the command syntax is:
$ iptables [-t table] command [match] [target]
where the rule is in the specified configuration -t table, the default table including filter, nat, mangle, raw and so on. command part is the most important part of the iptables command, it tells iptables command what to do, for example, insert rules to add the rule to the end, or delete rules chain. The following are the most commonly used commands.
• -A or an append: This command rule to the end of the chain.
Example:$ iptebles -A INPUT-s 205.168.0.1 -j ACCEPT
The example command to be appended to the end of a rule INPUTS determining the packet from the source address 205.168.0.1 can be accepted into the local protocol stack.
• -D or -delete: by specifying a rule to match the specified rules with -D or position number in the chain of the command to delete the rule from the chain.
• -P or --policy: This command sets the default target chain operations, namely policies for all packets in the chain does not match any of the rules will be forced to use the policy for this chain.
Example:$ iptables -P INPUT DROP
The default target command chain operation is designated as INPUT DROP This means that all discarded INPUT chain do not match any rule packets.
• -N or --new-chainj create a new chain of command specified name.
• -F or -flush, if you specify the name of the chain, the chain of command to delete all the rules, if the chain name is specified, the command deletes all rules in all chains. This parameter is used to quickly remove.
Example:$ iptables -F FORWARD
• -L or a list: Lists all rules specified chain.
Example:$ iptobles -L FORWARD
MatchRule matching the condition part, specify the packet matches the rule should have the characteristics, the matching condition is divided into two categories: general and specific protocol matching matching, the matching condition for the generic matches with any packet protocol may be used Bian, as will. Into the network interface / outgoing network interface, -s / -d source and destination addresses, -p protocol type, -m network connection status, match the matching condition a particular protocol certain upper layer protocol specific fields, such as "--sport / --dport of TCP / UDP port mapping setting conditions and the like, in a plurality of matching conditions is to use "and" relationship, i.e. simultaneously satisfy the triggered only certain operating behavior.
Targetportion of the target satisfy the matching operation after the specified condition, that is with processing operation .netfilter / iptables packets that match the rule executed in addition to allowing user-defined target, there are many common target operation option defined by default.
- netfilter / iptables NAT mechanisms of
(1) IP masquerading
demand netfilter NAT mechanism is the most commonly used IP masquerading. Private IP packets in the network segment, such as a shared Internet access through a scene external IP address is bound to the firewall, this mechanism can be used, so that the internal network
packet sent by the host network source IP masquerading, using a firewall external IP address, just like emitted from outside the firewall IP address. Specific configuration rules:
#iptables -t nat -A POSTROUTING -i ethl -o ethO -j MASQUERADE
(2) SNAT mechanism
SNAT "jSNAT" described by certain operating options, with «-to-sourcew described to convert the IP address, or IP address and a range of ports (only one for TCP and UDP). E.g:
# iptables -t nat -A POSTROUTING -o ethO -j SNAT —to 1.2.3.4
Source IP address of the network connection that rule will be emitted by the routes modified to 1.2.3.4.
# iptables -t nat -A POSTROUTING -o ethO -j SNAT -to 1.2.3.4-1.2.3.6
Source IP address of the network connection of this rule will be issued by a modify routing IP 1.2.3.4 to 1.2.3.6 IP segment.
# iptables -t nat -A POSTROUTING -p Cep -o ethO -j SNAT —to 1.2.3.4:1-1023
TCP source IP address of this network by a routing rule sends modify 1.2.34 connected, and the source port is set within a range of 1~1023.
(. 3) DNAT mechanism
DNAT PREROUTING chain created for the application for the present machine (including routing. Packet filters) to change the destination address are ignored, that reaches the real destination address. Need to use the "-i" option. Destination NAT with "-jDNAT" represented by "-to-destination" option described IP address, port, or a range of IP addresses. E.g:
Translates the destination address of 5.6.7.8.
# iptables -t nat -A PREROUTING -i ethl -j DNAT —to 5.6.7.8
Translates the destination IP address of any one of 5.6.7.8-5.6.7.10.
# iptables -t nat -A PREROUTING -i ethl -j DNAT —to 5.6.7.8-5.6.7.10
The destination address and port translation Web network traffic to 5.6.7.8:8080.
# iptables -t nat -A PREROUTING -p tcp --dport 80 -i ethl -j DNAT --to 5.6.7.8:8080
1.2.3.4 to the local packet sent to redirect local loopback.
# iptables -t nat -A OUTPUT -d 1.2.3.4 -j DNAT —to 127.0.0.1
It is a special case of the target DNAT port forwarding mechanism, 8080. To the network traffic to the external network IP 1.2.3.4 forwarded to the internal network IP192.168.1.1 port 80, and with the following rules preclude:
# iptables -A PREROUTING -t nat -p tcp -d 1.2.3.4 —dport 8080 -j DNAT —to 192.168.1.1:80
Hands-
practice Task: configure iptables on Linux operating system platform, or a personal firewall on the Windows operating system platform, complete the following functions and tested:
(1) filter ICMP packets, so that the host does not receive Ping packet;
(2) allow only specific IP addresses (such as LAN Linux attack aircraft 192.168.200.6), access to a host of network services (such as FTP, HTTP, SMB), while the other IP address (such as Windows attack aircraft 192.168.200.2) can not access .
A: (1) in Linux (ip: 192.168.200.6). Configure the personal firewall filtering ICMP packets, so that the host does not accept ping packet, as follows:
first use of windows host linux ping the host computer connected to:
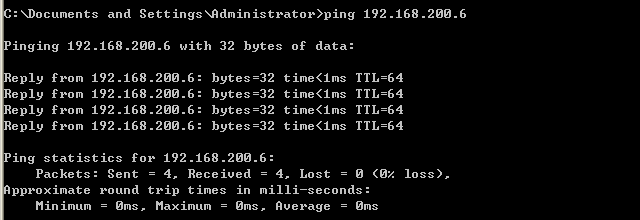
Linux is then performed on the host iptables -A INPUT -p icmp -j DROPcommands, adding the INPUT chain it is produced, ping icmp packets missing rule, this time to the host, ping linux ping fails:

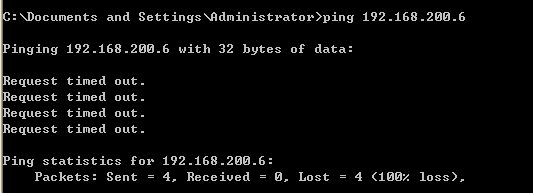
Just remove the filter rules:
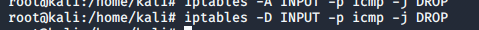
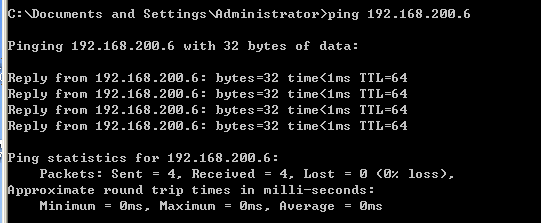
Try to ping linux host again:
(2) connecting the target machine via telnet 192.168.200.125 command, the source address of 192.168.200.6 and ip 192.168.200.2:

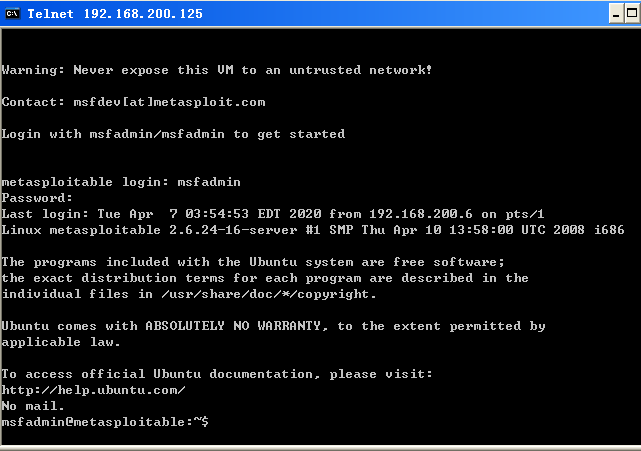
Then iptables -A INPUT -p icmp -j DROPthe rule is satisfied datagram is discarded, at this time telnet connection fails:



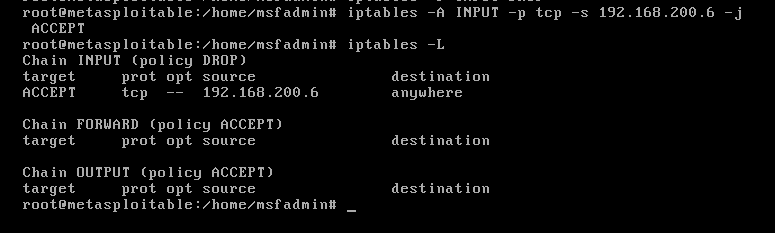
Then command iptables -A INPUT -p tcp -s 192.168.200.6 -jopen source IP192.168.200.6 tcp services to the target machine ACCEPT, can be used iptables -Lto view the rules
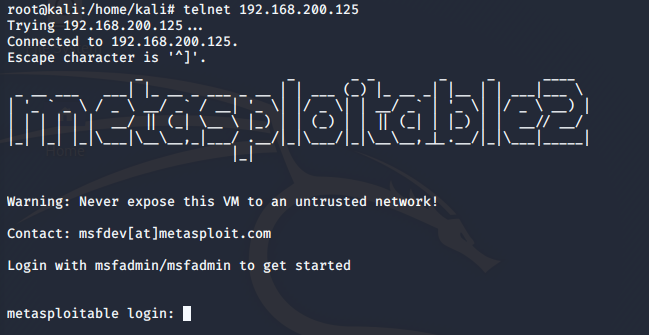
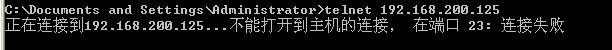
192.168.200.6 can telnet target IP, and 192.168.200.10 connection fails:
1.5 Snort features and basic infrastructure
Snort basic structure shown in FIG software, it consists of four basic components:
(1) packet sniffer / decoder (Sniffer);
(2) pre-processor / plug (Preprocessor);
(. 3) detects the engine / widget (Detection Engine);
(. 4) the output module / plug (output modules);
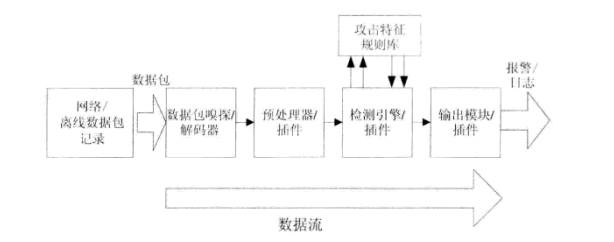
Snort four major components and processes described below.
- Packet sniffer / decoder. First, the packet capture libpcap off from the card or record, then the packet is decoded packet structure filled into the link layer protocol, for decoding, such as the TCP / UDP protocol layer to the high level.
- Preprocessor / plug-ins. Then the packet is sent to a variety of preprocessing plug-in, checking the data packet and prior to detection of the engine operation. Preprocessing plug-in checks whether each packet should be noted that an alarm or something modified.
- Detection Engine / plug-ins. Then, the packet is sent to the detection engine detects engine first matched string defined by the features of the various rules file for rapid detection of the pattern matching information for each packet, and then provides additional detection of various packet detecting plug Features. Rules for each keyword options corresponding to the detected engine plug-ins can provide different detection function.
- Output module / plug. Alarm / log information generated before the various components, according to a user configuration, call the appropriate output plug is transmitted and recorded.
Hands: Snort
Task: Use the given Snort pcap file (decoding Network Scanning in Chapter 4 in either a pcap file) intrusion detection, and detect attacks will be explained.
Used on BT4 Linux or Wndows Attacker attack aircraft attack aircraft Snort, given pcap file intrusion detection, access to the alarm log.
Performed snort -r /home/kali/listen.pcap -c /etc/snort/snort.conf -K ascii
-K asciimainly in order to specify the encoding output log file is ASCII (default binary)
can be seen from the results, most of the TCP packet, a small portion of the ARP packet:

There alarm data 10, the log records are:

Statistical data stream:

Vim can be generated in the read default log directory / var / log / snort alert in a file, the recording information 10 of the intrusion detection alarm data:

2. practical assignments
Analysis of virtual network firewall and IDS attack and defense environment honeypot network gateway / IPS configuration rules, and analytical reports on how honeypot network gateway is the use of firewalls and intrusion detection technology to complete its attack data capture and control requirements.
Detailed analysis of configuration rules file and startup items including:
-
Firewall (netfilter + IPTables): / etc / init.d / rc.firewall
-
Intrusion detection system (Snort): / etc / init.d / hflow-snort and /etc/snort/snort.conf
-
Intrusion Prevention System (Snort_inline): / etc / init.d / hflow-snort_inline and /etc/snort_inline/snort_inline.conf
analyze the content: -
Above script is how to achieve Honeywall data capture and data control mechanisms?
-
IPTables get a list of the actual rules, actual implementation parameters and Snort.inline of Snort.
-
After Honeywall boot, firewall, NIDS, NIPS is how to start?
-
Bonus: Snort rules Honeywall is how to automatically upgrade?
A:
How to (1) above script is Honeywall for data capture and data control mechanisms? -
First, the relationship between the firewall and intrusion detection technologies. iptables is responsible for data accept, reject and drop, snort major role in early warning, can not stop. So is the use snort to monitor, there are violations of the rules on the issue of early warning information to tell iptables, iptables to block the connection and thus in violation of the rules.
-
Data acquisition and control data
typically includes two control data, a firewall is to control the data, there is a limitation on the IPS abnormal data.
View firewallvim /etc/init.d/rc.firewallfile: .

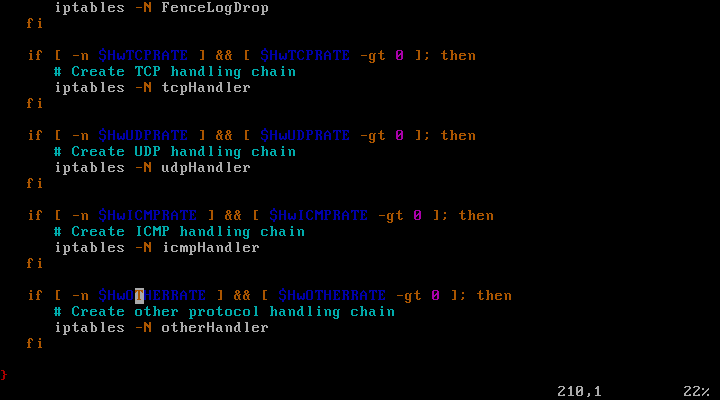
Firewall file rc.firewall in create_chains () is used to create chains, which respectively function to create a blacklist and white list, the list of protection and protection log deletion, -N's intention to create a new chain based on user-specified name, which is blacklisted block certain users enter the network address and the host white list is considered that the user can add a trusted set of network users and the network address, protection list is a list of files, delete IPS protection is a log sheet for recording / delete rebound from fence packets.
About data capture, whether or iptables Snort, are able to capture the network connection information recorded in the form of logs, comprising a source IP / port, destination IP / port, and protocol for connection.
(2) to obtain the actual list of rules IPTables, Snort and practical implementation of Snort.inline parameters.
-
By instructions
iptables -t filter -Lto view the list of rules, -t is specified rules table, -L representing the list. To page through the shift key + Fn key + arrow keys. You can see some of the rules such as OUTPUT, INPUT, FORWARD it has been closed.
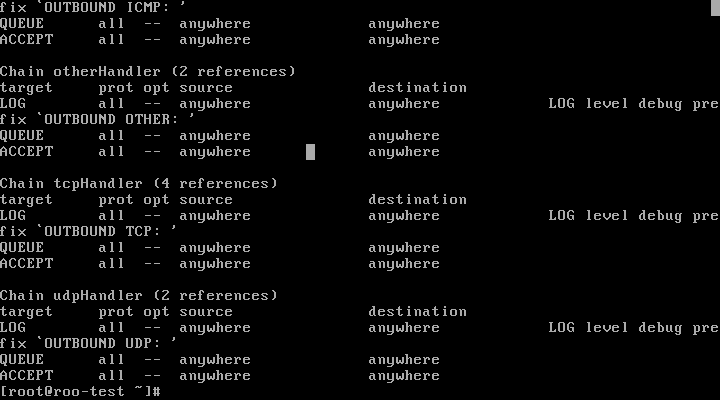
-
snort actual execution parameters
execution commandvim /etc/init.d/snortd, snortd is snort startup script file, snort.conf rules set specific warning, such as analysis of the figure below, default snort.conf rule, the default monitor network card is eth0, the default path to store logs / var / log / snort like.



-
snort_inline actual execution parameters
execution commandvim /etc/init.d/hw-snort_inlineto open snort_inline script
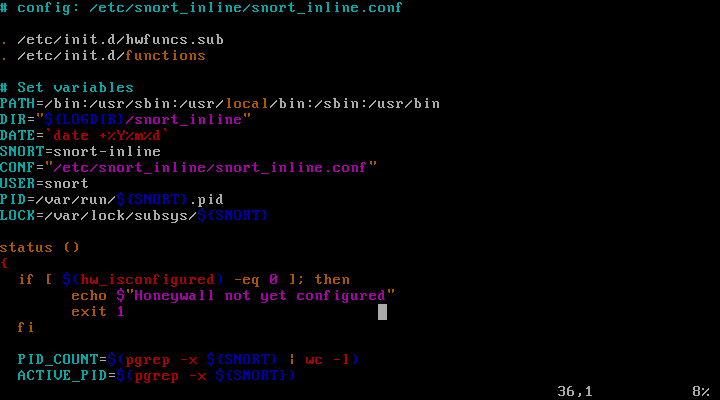
As well as some of the Run command. Wherein -Q is, i.e. QUEUE mode, is for the protection rules snort_inline QUEUE pass through iptables.

After (3) Honeywall boot, firewall, NIDS, NIPS is how to start?
- Firewall, NIDS, NIPS start
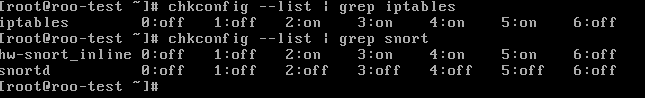
by commandchkconfig --list | grep [服务]to query the current service is not open.
chkconfig command is used to check various services, system settings. 0-6 if all off, will not start automatically.
You can see the firewall and NIPS (snort_inline) is to follow the system startup and boot automatically configure just the script file. NIDS does not start automatically.
(4) Bonus: Snort rules Honeywall is how to automatically upgrade?
- How Snort rules to automatically upgrade
command in the / etc directoryvim honeywall.confopen honeywall configuration file, which you can see some of this, as we configured IP address, subnet mask, and so on.
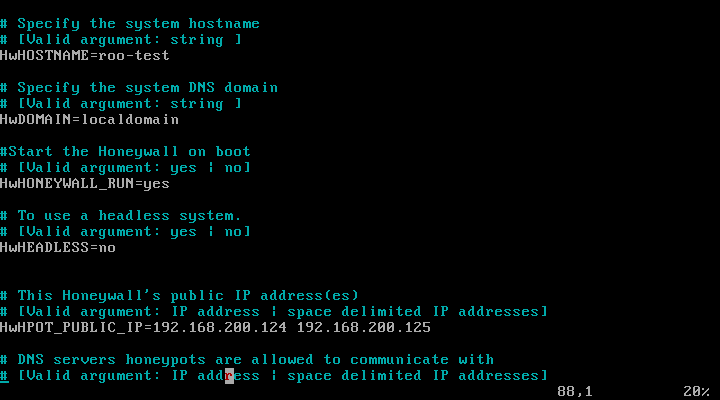
Snort rule can see, the default is not automatically updated. You can also see Oinkmaster word, which is automatically updated software.

Oinkmaster.conf open the file in the current directory, you can see the update file

3. encountered problems
- One problem: the use of two tools snort and iptables and also less skilled
- A solution to the problem: refer to some online tutorials.
4. Learning sentiment, thinking
The main practice learning network security technology. Practice, the process is quite smooth, and did not encounter any major problems, but using iptables and snort tool to be strengthened.