Foreword
This work belongs courses: https://edu.cnblogs.com/campus/besti/19attackdefense
where this requirement in the job: https://edu.cnblogs.com/campus/besti/19attackdefense/homework/10449
me in this the aim of the course is: learning network attack and defense technology-related knowledge, acquire the relevant skills.
In particular aspects of the job which helped me to achieve goals: learning environment to build network attack and defense.
1. knowledge carding and summary
Network security research
Network attack techniques
- The definition of cyber attacks: a hazard to network security target behavior
- Basic features: the use of certain network attack tools on the target system access to attack
- Network attack process: information gathering, network stealth port scans and vulnerability, attack, set up the back door and eraser
- Network defense technology
- Passive defense to active defense development
- Message encryption, access control, firewall, intrusion prevention, malware prevention, security audit
- Information Encryption: the core technology of network security and transport security foundation
- Access control: authentication, certification stand-alone environment, network environment, authentication, access control technology
- Dependence of malicious code (viruses independence malicious code (Trojan horses, backdoors, Rootkits) does not have the ability to replicate the dependence of malicious code (Trojan horses, logic bombs, back door), does not have the ability to replicate, self-replicating: the malicious code prevention ), the independence of the self-replicating malicious code has the ability (worms, malicious script)
- Passive defense to active defense development
2. The offense and defense environment to build detailed process
Topology Figure 2.1, offensive and defensive environment
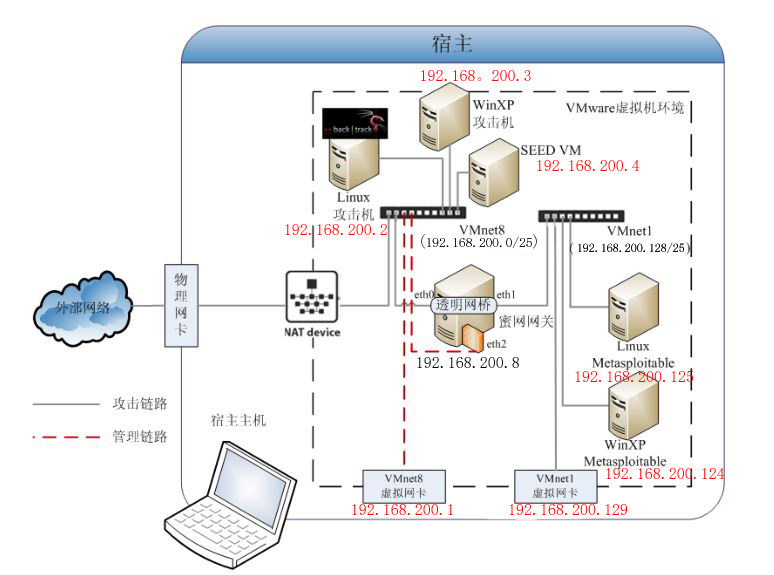
2.2, VM network settings

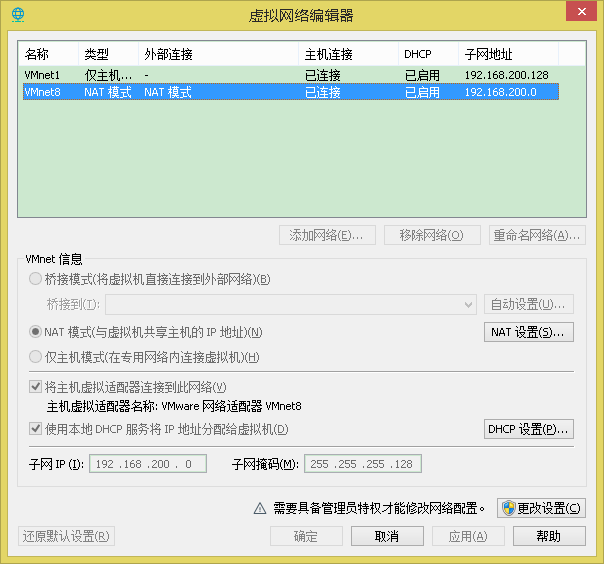
2.3 virtual machine configuration
2.3.1 Linux installation kali attack aircraft
Direct vmware virtual scan, a load .vmx , the network adapter is provided kali custom (VMnet8 (NAT))
Power set, kali default user name kaliand password kali, suthen ifconfigcheck the IP address.
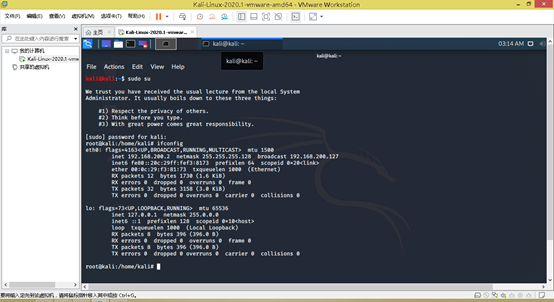
Remember the IP address, my side is 192.168.200.2 .
2.3.2 Windows Installation attack aircraft VM_WinXPattacker
Set the network adapter to NAT
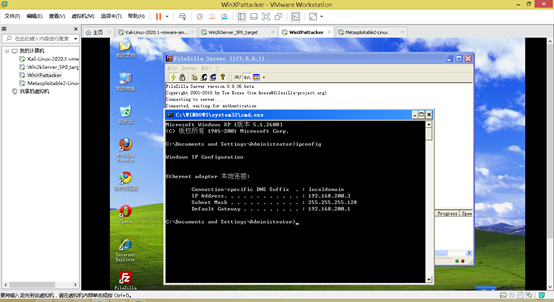
ipconfigFound a note of the address, I was 192.168.200.3
Installation 2.3.3 SeedUbuntu
Use vmware New Virtual Machine -> Custom Installation -> ..-> later installation of the system -> Linux -> ...-> Use an existing virtual disk .vmdk.
Once the network adapter to select the custom (VMnet8 (NAT))
Seed for the default account seed, password dees, su passwordseedubuntu
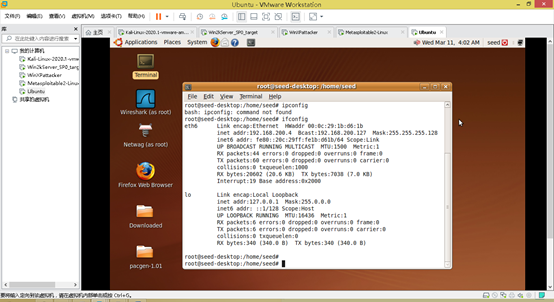
Use ifconfigto view and note the IP address.
2.3.4 Windows installation drone VM_Win2kServer
3.1 loaded with the .vmx , the network adapter is set to host-only model
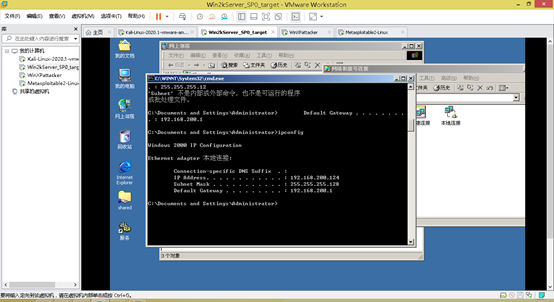
Boot setting TCP / IPv4, use the IP address 192.168.200.124, address mask 255.255.255.128, default gateway 192.169.200.1, preferred DNS server 1.0.0.1.
2.3.5 Linux drone metasploitable-linux-2.0.0
3.1 with the introduction .vmx , network adapters for only the host mode
Power, as the drone account msfadmin, password msfadmin, sudo supassword msfadmin. carried out
vim /etc/rc.local
#i键进入编辑模式,在exit0上面输入
ifconfig eth0 192.168.200.125 netmask 255.255.255.128
route add default gw 192.168.200.1
#ESC返回,:wq回车 保存并退出
reboot #重启After rebooting ifconfigView
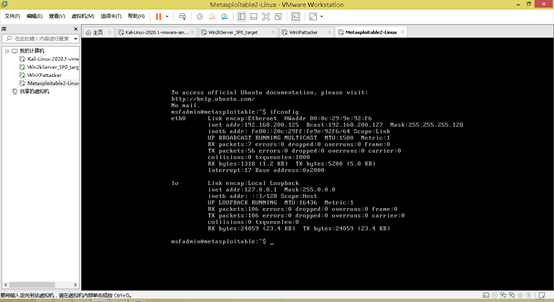
Address is 192.168.200.125
2.3.6 Honeynet roo-1.4 Installation
- a. vmware New Virtual Machine
- b. Hardware Compatibility Workstation 6.5-7.x
- c. Install the operating system later
- d. The client operating system Linux , versions of CentOS 5 and earlier
- e behind the default
After completion of the CD / DVD loading .iso image, adding two network adapters, 1,3 is the NAT , 2 of only the host mode
Power, for the account roo, password honey, su -passwordhoney
Enter Honeyall the Configuration , for the first time required to initialize selected default
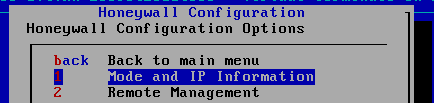
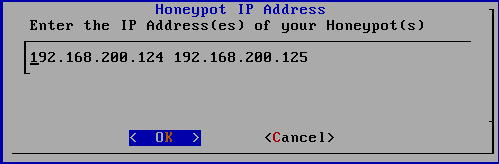
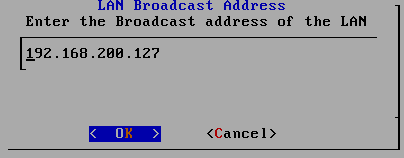
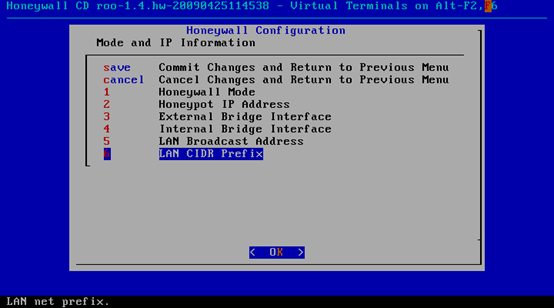

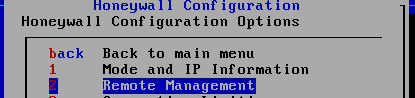

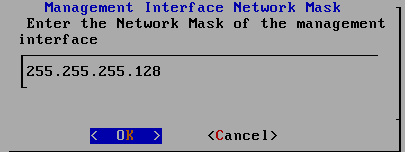

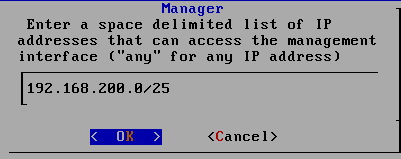
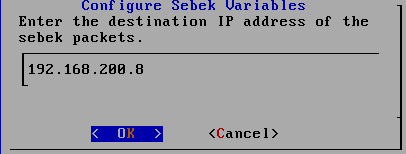
2.3.7 back VM_WinXPattacker
Browser opens https://192.168.200.8, for the first time account roo, passwordhoney
After resetting the password as follows
Configuration
2.4 Test
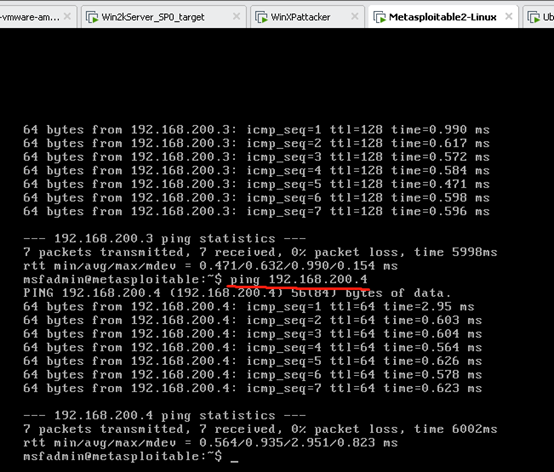
Switch to ping any arbitrary drone attack aircraft, attack aircraft of any arbitrary drone ping
ping times windows_target
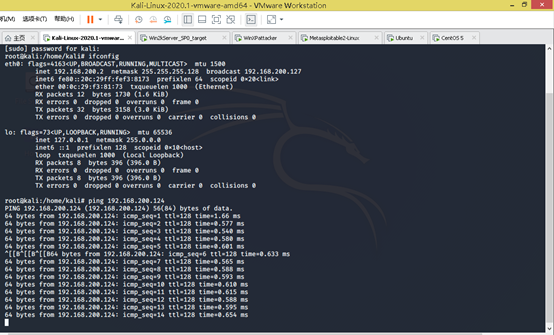
winXPattacker ping windows_target
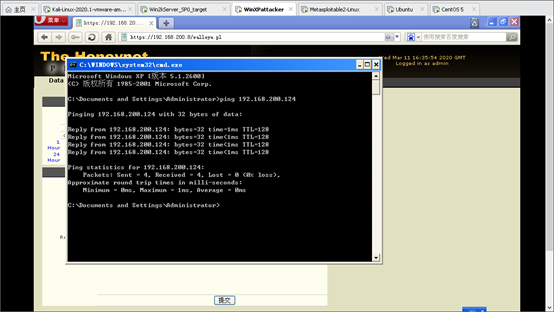
seed ping windows_target
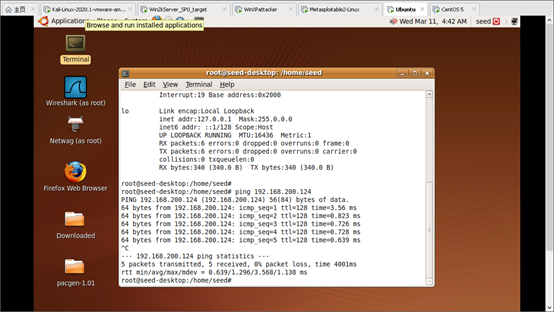
seed ping metasploitable-linux-2.0.0

kali ping metasploitable-linux-2.0.0
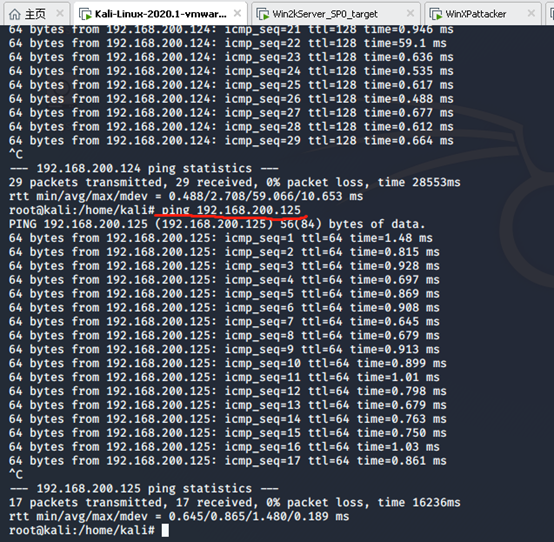
winXPattacker ping metasploitable-linux-2.0.0
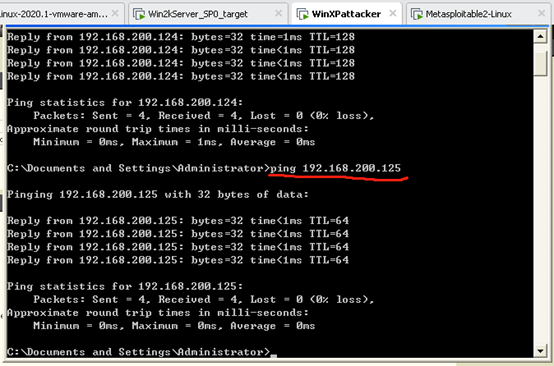
win2kServer ping times
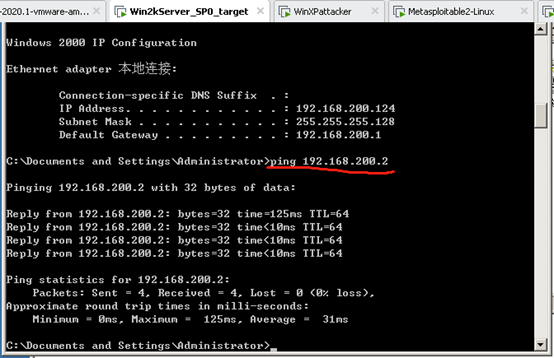
win2kServer ping winXPattacker
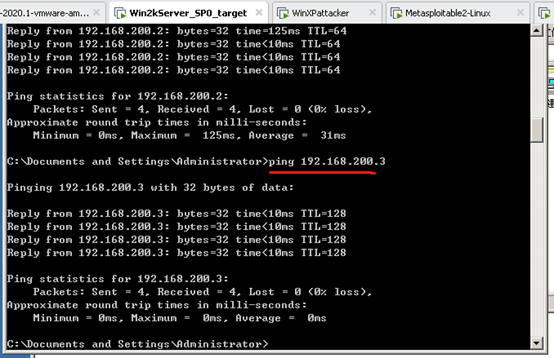
win2kServer ping seed
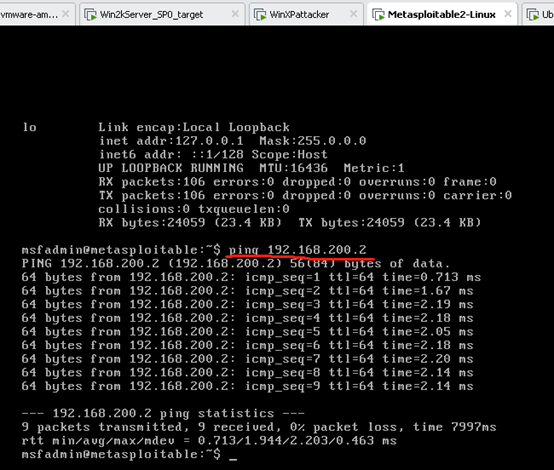
metasploitable-linux-2.0.0 ping kali
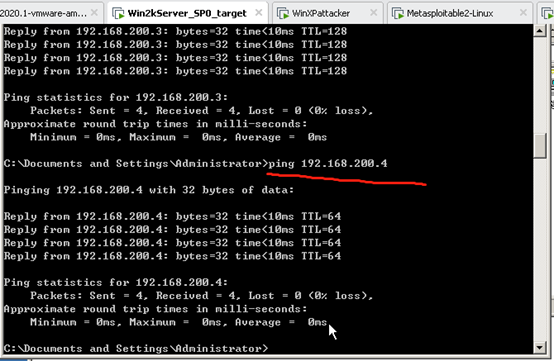
metasploitable-linux-2.0.0 ping winXPattacker

metasploitable-linux-2.0.0 ping seed
3. The problems and solutions encountered in the study
Question 1: falied to install USB inf file
Problem 1 Solution: Turn Services VMware Authorization Service
Question 2: Can not automatically install drivers VMCI
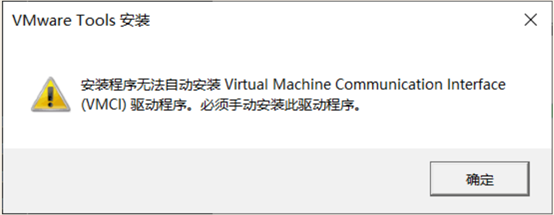
Problem 2 Solution: The issue can not automatically install the driver appears VMCI installation of VMware Tools in a virtual machine
- Question 3: After installing vmware no virtual NIC
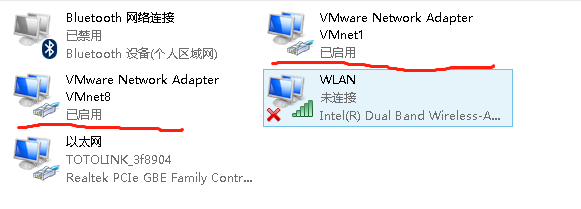
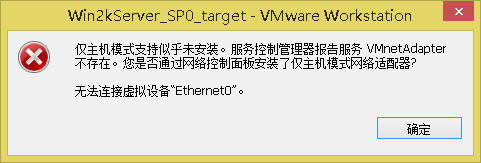
Question 3 Solution: VMware after installation, no virtual network card
The main reason is because the problem of 1,2 uninstall vmware presence of residual, heavy equipment will produce an error, my own official website to download the latest version vmware workstation pro 15, 14 and 3 with a solution actually has no effect, and later to a friend cracked version 15 was resolved. vmware15.7z , extraction code dxee.
VMware after installation, no virtual network card required to remove all the files containing vmware, when I practiced with vmware words found some documents in the eclipse-jee contained in a computer, I thought nothing no control, and perhaps this is what I have the reason is not necessarily heavy equipment failure.
4. Learning sentiment, thinking
Previously installed vmware, may not be uninstalled when the clean uninstall, various error when reloading, tried a variety of approaches did not bear fruit, only to find the patience, a bold attempt to achieve the goal.
Reference material
- Based on the third generation honeypot gateway ROO, simply set up the network environment ***
- Questions about the virtual machine to install VMware Tools can not be installed automatically appear in VMCI driver
- VMware after installation, no virtual network card
- 20,199,102 2019-2020- 2 "network attack and defense practice," the second week of work