Secure Shell protocol, referred to as SSH, an encrypted network protocol used to secure connections between client and host, and support a variety of authentication mechanisms, the most practical authentication is password-based authentication mechanism and based on the well key authentication two kinds. How to set up Linux systems SSH key-based authentication, and how to avoid tight connection to the tutorial host.
Step one: Check the existing SSH key pair
First check mainly in order not to overwrite an existing key. Is Run the following command to see that there can use these keys and skip the second step, or back up the old key and generate a new key. If you see No such file or directory or no matches found means no SSH keys, you can proceed to the next step and generate a new key.
ls -al ~/.ssh/id_*.pub
The second step: to generate a new SSH key pair
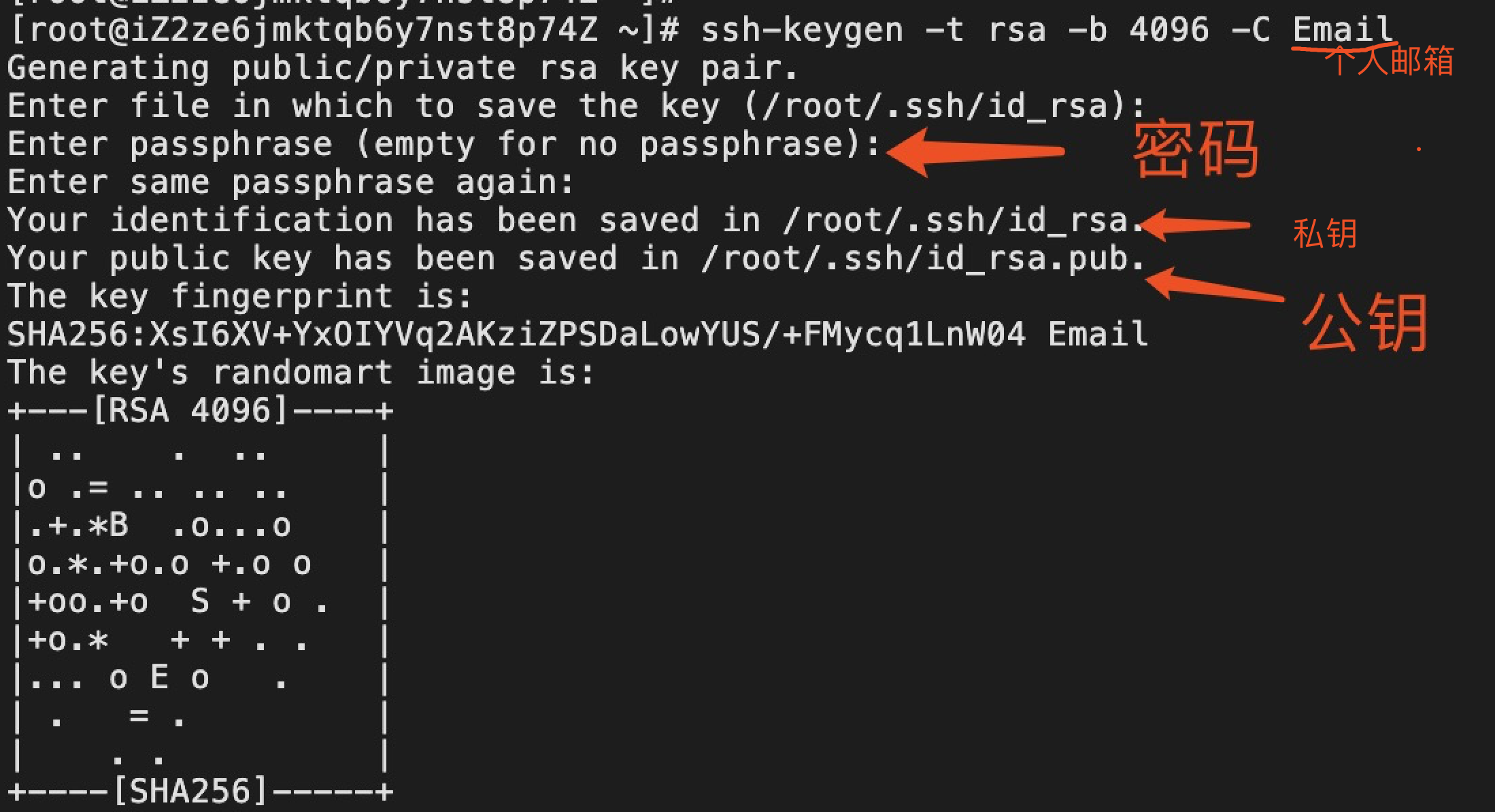
The following command will generate a new 4096 SSH key pair and e-mail address as a comment:
ssh-keygen -b 4096 -C [email protected]
ssh-keygen common parameters:
-t: Specifies the type of key generated, the default SSH2d RSA -f: specify the file name key generation, the default id_rsa (id_rsa private, public id_rsa.pub) -b: specify the key length (bits), RSA minimum requirement 768, the default is 2048; the DSA key must be 1024 (1862 standard specifies the FIPS) -C: add annotations; -P: providing the old password blank indicates no password (-P '') -N : new password, blank indicates no password (-N '') -R & lt hostname: from known_hosta (the first connection to the home directory .ssh directory will produce the file key) to delete all files belonging to the hostname density key -e: openssh read private or public key file; -i: reading unencrypted ssh-v2 compatible private / public key file, and then displays openssh compatible private / public key on the standard output device ; the -l: show the public key fingerprint data files; -q: quiet mode;
Press Enter to accept the default file location and file name:
Enter file in which to save the key(/home/yourusername/.ssh/id_rsa):
Next, ssh-keygen tool will be asked to enter a security password (if you do not use a password phrase, press Enter :), if you choose to use a passphrase that you will get extra security. In most cases, developers and system administrators use SSH without using a password, because they are useful for fully automated processes.
The third step: examining .ssh目录the authorized_keys文件presence or absence, presence skip Step
If not, create one, and then append the contents of id_rsa.pub to authorized_keys end of the file.
.ssh CD Touch authorized_keys -> ssh If this file exists in this step is omitted cat id_rsa.pub >> authorized_keys -> is added to the contents of id_rsa.pub authorized_keys
Step Four: detection, the need to modify the configuration of ssh (negligible)
[root@centos-004 .ssh]#vim /etc/ssh/sshd_config RSAAuthentication yes PubkeyAuthentication yes # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2 # but this is overridden so installations will only check .ssh/authorized_keys AuthorizedKeysFile .ssh/authorized_keys
Here it is important, before you configure the key login is successful, do not be too confident PasswordAuthentication will set no, otherwise you can not key login, and then prohibiting password, on the tragedy. After key registration set successfully, PasswordAuthentication can be set to no, disable the logon password, relatively safe.
Step five: copy the public key
After generating the SSH key pair for the realization there is no password to log in to the host, you need to copy the public key to the host to be managed. The easiest way to copy the public key to the host is named using the command ssh-copy-id. Local host terminal type:
ssh-copy-id remote_username@server_ip_address
You will be prompted remote_username password:
remote_username@server_ip_address's password:
After the user is authenticated, the public key attached to a remote user authorized_keys file , and closes the connection. If for some reason, the local host ssh-copy-id without this utility, you can use the following command to copy the public key:
cat ~/.ssh/id_rsa.pub | ssh remote_username@server_ip_address "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys"
Step Six: Login using SSH keys
After completing the above steps, you can log in to the remote host without being prompted for a password, the password test:
ssh remote_username@server_ip_address
https://blog.csdn.net/qq_27870421/article/details/94594492
http://baijiahao.baidu.com/s?id=1648175338751747914&wfr=spider&for=pc